Author: Jordi Alexander
Translation: TechFlow Friends
Chapter One: The Ultimate Answer to Life, the Universe, and Everything
I hear you want to learn how to navigate the uncharted waters of the Ponzi universe!
Since you've traveled so many light-years to get here, let me cut straight to the chase:
The ultimate answer to the question you seek is (-4,+2).
This game theory notation represents the outcome of an interaction—(X,Y) means Player 1 ends up with X, and Player 2 with Y.
The truth is, in a Ponzi scheme, if one player wins, the other loses even more.

Simply put, for every two Lamborghinis a Ponzi scheme earns, it extracts even more tickets from those who walk away empty-handed.
The game of pooling resources is as old as human history, and over centuries has evolved to become increasingly efficient at tapping into our fundamental human needs.
Humans crave success, desire belonging to a community, and long to be part of something greater than themselves.
As we enter the Web3.0 era, everything around us is becoming financialized and tokenized, making these mechanisms only more complex and stranger.

Complexity is the con artist’s favorite weapon. The more time and expertise required to understand a game, the easier it is to fool people into believing they can win.
So buckle up, because we’re about to take a high-speed tour through the Ponzi universe, exploring its “Three Fundamental Laws.”
Chapter Two: The Three Fundamental Laws of the Ponzi Universe
In thermodynamics, an "isolated system" describes one completely separated from its environment.
We introduce the concept of an “isolated investment system”:
Funds entering a protocol purely with the expectation of generating monetary returns.
To illustrate this vividly, imagine a poker table with eight players.
If four are professional players working there, while the other four play socially and for fun, then the table is an open system.
But if all eight are professionals solely focused on profit, then the table becomes economically isolated.
The First Law of Ponzi Economics:
The amount of capital in an isolated system can be moved around, but it cannot grow beyond what was initially invested.
An economically isolated system cannot create money—it can only redistribute the money that was put in. Thus, while winners may emerge, their gains come entirely at the expense of other participants.
Zero-sum games can have cooperative elements—players may team up against others, turning into a kind of Hunger Games—but ultimately they remain adversarial, devolving into player-versus-player warfare, anonymous versus anonymous.

When hidden costs are factored in, it's not just zero-sum—it becomes negative-sum.
The Second Law of Ponzi Economics:
The entropy loss within an isolated system increases over time.
Transaction fees; arbitrage bots and sandwich attacks lurking everywhere, siphoning value; high mining costs; potential code vulnerabilities.
Just operating the system incurs ever-rising costs...
...and this doesn't even account for whether founders left backdoors to redirect funds to themselves.
Over time, as costs accumulate, less and less capital remains available for players to win. In the poker analogy, if they keep playing long enough, the house rake grows so large that eventually all the money on the table gets taken by the casino.

As losses mount within the system, we arrive at the final law.
The Third Law of Ponzi Economics:
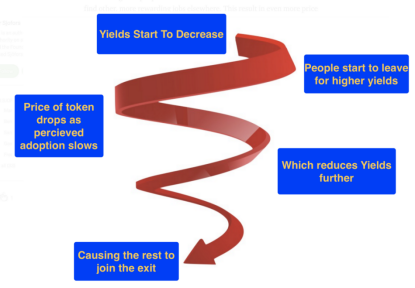
As the amount of money in the system begins to shrink, activity in the system declines toward zero.
Without sufficient fresh inflows, once the rocket fuel runs out, a death spiral begins. People lose hope of future wealth, rumors spread, and both community engagement and mindshare spiral downward.

This death spiral might take months or years to unfold, but eventually, as a Ponzi scheme grows larger, it requires exponentially increasing capital just to keep going.
Once a Ponzi reaches billions in scale, it depends on massive new entrants just to offset organic system losses—a gravitational pull that becomes impossible to overcome.

In the world of cryptocurrency, we’ve seen this evolution repeated countless times in DeFi protocol forks. They add nothing particularly useful beyond a new logo and chain, yet they enter a Ponzi cycle. Generous liquidity mining rewards gradually attract users to farm, increasing total value locked (TVL), building momentum.
But without inflows from an open system, they inevitably end in a death spiral. Next stop: Goblin Town:
Chapter Three: First-Principles Framework and FAQs
The basic structure of every game is the same:
1. Opening: People pool money together;
2. Middle: Mechanisms that chop and move money;
3. Endgame: Pooled funds are redistributed, determining winners and losers.
As we know, the middle stage is where psychological manipulation occurs. So skip this part and go directly to the final “endgame” phase.
Whether you're farming in some financial metaverse or dancing your way into the Web3.0 revolution, ask yourself:
“Who will be the benefactor providing returns to investors, and why would they have any rational incentive to do so?”

Legitimate projects have a clear answer to this question. They explain execution risks involved, giving potential investors transparent understanding to make informed decisions.
Meanwhile, modern-day Ponzi brothers have mastered the art of speaking in vague, circular logic. When confronted with this question, they retreat repeatedly into psychological mechanisms.
Below are common (and unimaginative) scripts used by pure scams and “social Ponzi schemes.”
Scam: We have a secret system using super AI machine learning trading/mining/Mumbo Jumbo to generate high yields. But don’t ask what it is—it’s proprietary secret alpha.
Social Ponzi: We’re like Bitcoin, but due to our superior design, we’ll replace the dollar as the “reserve currency,” while Bitcoin fails.
While these stories can make great marketing slogans, offering such alpha publicly—or expecting the whole world to live on “XYZ Shitcoin”—clearly sounds implausible. If you had a Ponzi detector, it would scream the loudest alarm right here.
FAQ #1: If it’s not black and white, how should we assess the degree of Ponzi-ness? Isn’t everything somewhat a Ponzi?
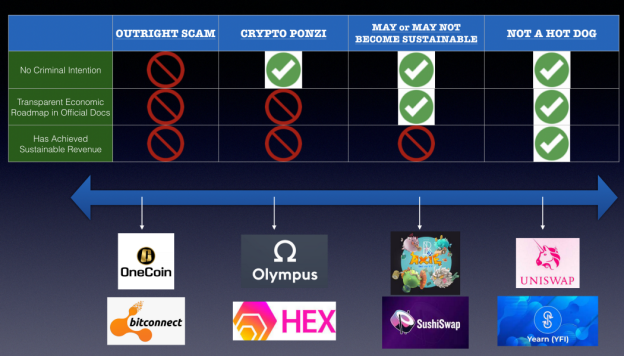
Indeed, there’s a sliding scale for Ponzi schemes, ranked from worst to best into four tiers:
Open Scam: Founders are knowingly recruiting victims;
Crypto Ponzi: Unrealistic, misleading plans presented as aiming for real utility;
Might Fake It Till Make It: Generating revenue, but heavily incentivized to build enough moat to eventually remove those incentives;
Not a Ponzi: Possesses moats and generates sustainable revenue.
FAQ #2: Where do memecoins like $DOGE fall on this spectrum?
Memecoins are also Ponzi schemes, but not malicious ones. Since everyone is generally joking, they can be seen as willing participants investing for entertainment value from the meme community. You could even interpret it further:
Haha, this is a funny meme. Others might enjoy it too—it could go viral! Plus, some of them might be wealthy whales who decide to spend resources creating real utility for the coin! That’s why our coin is called DOGE.
For example, $DOGE holders might bet that Elon will use his money to create value for holders in exchange for his daily LOLs.
FAQ #3: If the first law is true—that protocol mechanics themselves don’t create money—then how can they pay yields? Some claim they sustain 50,000% APY!
Crucially, you must understand that yields paid by protocols in their own tokens are misleading.
The protocol’s value remains constant: Y tokens × value per token V.
Imagine a rectangle with fixed area—you can increase length, but width decreases proportionally. Each token’s value is diluted at the same rate.
A 10% daily yield (3,660% annualized) causes each coin’s value to drop by 10% per day. The Smart(er) Coin game demonstrates this destructive effect.
Coins initially bought for six cents end up worth less than one-millionth of their original value—the value eroded by excessive yields.
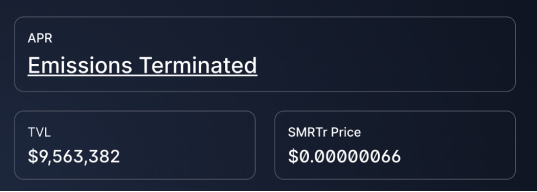
However, high APY enables Squid Game-style player-versus-player battles—those who sell first and exit at price V extract value from later users.

FAQ #4: But what if no one sells and prices rise? Doesn’t that increase market cap?
True—but this is precisely why market cap isn’t a good metric for manipulated or tightly held tokens. With low liquidity, prices can easily be artificially propped up, especially when supply is pumped, at least temporarily.
Here’s the zero-sum version (generously assuming no entropy):
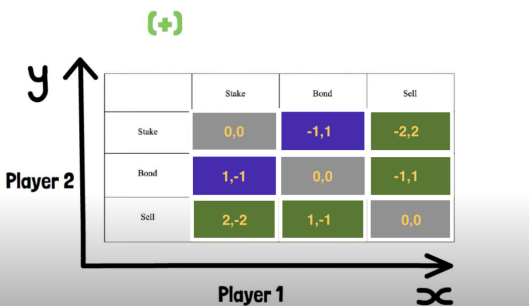
Yet this remains a game where selling dominates—any equilibrium other than (sell, sell) won’t be stable over time.
The only way two non-selling users can achieve a (3,3) outcome is by bringing in a bigger fool as a third player.
(3,3) is fake.
(3,3,-6) might be real—but shouldn’t be celebrated.
Chapter Four: Possibility of Redemption

If we define utility broadly enough, protocols can exit isolated investment systems and introduce real utility in multiple ways.
Some paths are more questionable, but if a Ponzi scheme decides to abandon its criminal roots and go legit, here are possible exit routes.
Gambling & Entertainment: The popularity of physical and online casinos proves there's a large market of people willing to trade monetary EV for entertaining speculation. If PvP dynamics stay fresh and fun, they can become sustainable projects.
Community & Memes: Create a sense of belonging that people are ultimately willing to pay for. Entertaining content further enhances this. NFTs may represent the best design in this space.

Charity / Donations: If people believe the project benefits the world, they may engage in a “money → feel-good” transaction. This token model remains unproven so far, but might work under certain conditions.
Investment Vehicle: Pool funds from the Ponzi into a decentralized hedge fund/yield aggregator/venture fund. While the business model itself is proven, transitioning from a scam origin raises many unanswered questions and keeps people trapped inside.
Bundle Attention and Sell: Time and attention are the ultimate scarce resources. With thousands of protocols/products competing for user attention simultaneously, monetization becomes increasingly feasible.
After capturing enough users, a protocol can attempt to generate income from open systems by packaging them into sellable products.
New protocols offer liquidity mining rewards to early users to bootstrap activity—in such cases, rewards can be directly attributed to the protocol.
In Web2.0, if you don’t pay for the product, you are the product.
In Web3.0, if you don’t pay for your attention, someone else will capture it and get paid for it.
Original link:
https://medium.com/@game_theorizing/of-smoke-and-mirrors-part-1-117c1f92e186
TechFlow is a community-driven deep content platform dedicated to delivering valuable information and thoughtful perspectives.
Community:
WeChat Official Account: TechFlow
Telegram: https://t.me/TechFlowPost
Twitter: TechFlowPost
Join WeChat group by adding assistant WeChat: TechFlow01