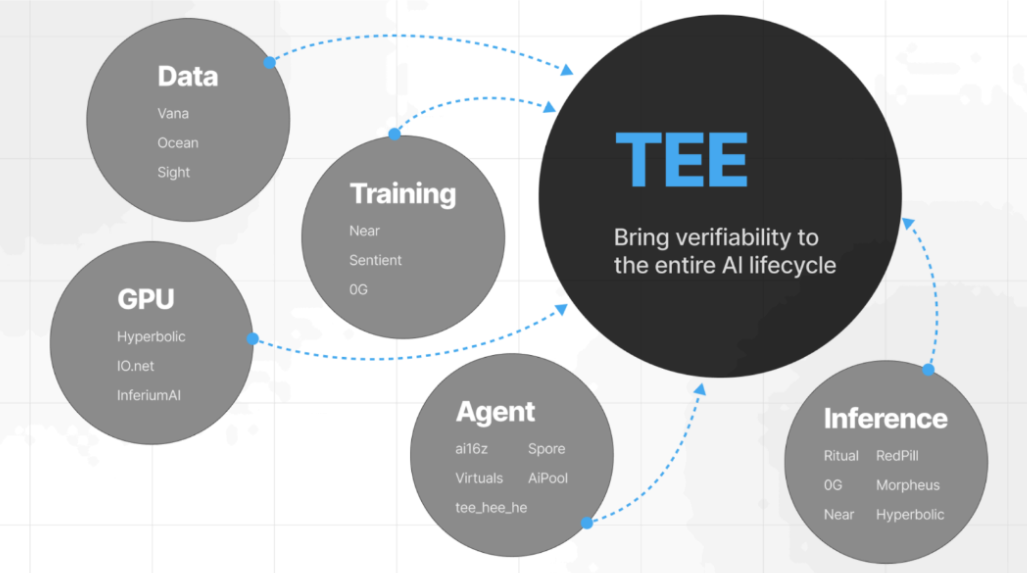
Huobi Growth Academy | TEE (Trusted Execution Environment) In-Depth Research Report: The Revolution of Privacy Computing, the Ultimate Puzzle for Web3
TechFlow Selected TechFlow Selected

Huobi Growth Academy | TEE (Trusted Execution Environment) In-Depth Research Report: The Revolution of Privacy Computing, the Ultimate Puzzle for Web3
TEE is building a more secure and efficient crypto world.
In the Web3 era, TEE (Trusted Execution Environment) is becoming a key cornerstone of data security and privacy computing.
From MEV protection to AI computation, from decentralized finance to DePIN ecosystems, TEE is building a more secure and efficient crypto world.
This report will guide you through this cutting-edge technology, revealing how it reshapes the future of Web3.
Chapter 1: The Rise of TEE — Why Is It the Core Puzzle Piece of the Web3 Era?
1.1 What Is TEE?
A Trusted Execution Environment (TEE) is a hardware-based secure execution environment that ensures data cannot be tampered with, stolen, or leaked during computation. In modern computing systems, TEE creates an isolated region separate from the operating system (OS) and applications, providing enhanced security for sensitive data and computations.
Core Features of TEE
Isolation: TEE runs in a protected area of the CPU, isolated from the operating system, other applications, and external attackers. Even if hackers compromise the main OS, data and code inside the TEE remain secure.
Integrity: TEE ensures that code and data are not altered during execution.
Through remote attestation, TEE can prove to external parties that it is running trusted code.
Confidentiality: Data within the TEE cannot be accessed externally—even device manufacturers or cloud providers cannot read it. Using sealed storage mechanisms, sensitive data remains secure even after device power loss.
1.2 Why Does Web3 Need TEE?
In the Web3 ecosystem, privacy computing, secure execution, and censorship resistance are core requirements, and TEE precisely provides these critical capabilities. Current blockchains and decentralized applications (DApps) face the following issues:
1.2.1 Privacy Issues on Blockchain
Traditional blockchains (e.g., Bitcoin, Ethereum) are fully transparent—anyone can view all transactions and smart contract data. This leads to the following problems:
User privacy leakage: In scenarios such as DeFi trading, NFT purchases, and social apps, users' fund flows and identities may be tracked.
Enterprise data leakage: Enterprises want to leverage blockchain technology, but sensitive data (e.g., trade secrets, medical records) cannot be stored on public chains.
TEE Solution: By combining TEE with smart contracts, developers can build private computation contracts where only authorized users can access results while original data remains hidden. Secret Network (a privacy smart contract platform based on TEE) has already implemented this model, allowing developers to create DApps that protect user privacy.
1.2.2 MEV (Miner Extractable Value) Problem
MEV refers to profits miners or block producers extract by exploiting transaction transparency when ordering transactions. For example: Front-running: Miners or bots submit transactions before users’ transactions to gain profit. Sandwich attacks: Attackers insert their own trades before and after a user’s trade to manipulate prices for profit.
TEE Solution: With TEE, transactions can be ordered in a private environment, ensuring miners cannot see transaction details in advance.
Flashbots is exploring a TEE + fair sequencing solution to reduce MEV's impact on DeFi.
1.2.3 Web3 Computing Performance Bottlenecks
Public chain computing capacity is limited; on-chain computation is expensive and inefficient. For example: High Ethereum gas fees make running complex smart contracts extremely costly. Blockchains cannot efficiently support AI computation, image processing, or complex financial modeling tasks.
TEE Solution: TEE can serve as a core component of decentralized computing networks, enabling smart contracts to offload computational tasks to trusted environments and return verifiable results.
Representative project: iExec (provides a decentralized cloud computing platform based on TEE).
1.2.4 Trust Issues in DePIN (Decentralized Physical Infrastructure Networks)
DePIN is a new trend in the Web3 space, including examples like: Helium (decentralized 5G network), Filecoin (decentralized storage), Render Network (decentralized rendering).
DePIN relies on trustless computation and verification mechanisms. TEE can ensure the trustworthiness of data and computational tasks. For instance: Data-processing devices can execute tasks within TEE to guarantee unaltered results. Combined with remote attestation, TEE can provide trustworthy computation results to blockchains, solving fraud issues in DePIN ecosystems.
1.3 Comparison Between TEE and Other Privacy Computing Technologies (ZKP, MPC, FHE)
Currently, privacy computing technologies in the Web3 domain include:
TEE (Trusted Execution Environment)
Advantages: Efficient, low latency, suitable for high-throughput computing tasks such as MEV protection and AI computation.
Disadvantages: Relies on specific hardware, vulnerable to security flaws (e.g., SGX attacks).
ZKP (Zero-Knowledge Proofs)
Advantages: Mathematically proves data correctness without requiring third-party trust.
Disadvantages: High computational overhead, unsuitable for large-scale computation.
MPC (Multi-Party Computation)
Advantages: Does not rely on single trusted hardware, suitable for decentralized governance and private payments.
Disadvantages: Lower computational performance, limited scalability.
FHE (Fully Homomorphic Encryption)
Advantages: Enables direct computation on encrypted data, ideal for extreme privacy needs.
Disadvantages: Extremely high computational cost, currently difficult to commercialize.
Chapter 2: Inside TEE Technology — Deep Dive into the Core Architecture of Trusted Computing
Trusted Execution Environment (TEE) is a hardware-based secure computing technology designed to provide an isolated execution environment that safeguards data confidentiality, integrity, and verifiability. With rapid advancements in blockchain, artificial intelligence, and cloud computing, TEE has become a crucial part of Web3 security architecture. This chapter explores the core technical principles, mainstream implementations, and applications of TEE in data security.
2.1 Basic Principles of TEE
2.1.1 How TEE Works
With hardware support, TEE creates a protected, isolated region within the CPU, ensuring code and data cannot be accessed or tampered with externally. It typically consists of the following key components:
Secure Memory: TEE uses dedicated encrypted memory areas inside the CPU (Enclave or Secure World), which external programs cannot access or modify.
Isolated Execution: Code running inside TEE operates independently of the main OS; even if the OS is compromised, TEE maintains data security.
Sealed Storage: Data can be encrypted and stored in non-secure environments, accessible only by the TEE.
Remote Attestation: Allows remote users to verify whether the TEE is running trusted code, ensuring computation results have not been tampered with.
2.1.2 TEE Security Model
The TEE security model relies on a minimal trusted computing base (TCB), meaning:
Only the TEE itself is trusted—not the main OS, drivers, or other external components.
Encryption and hardware protections prevent software and physical attacks.
2.2 Comparing Three Mainstream TEE Technologies: Intel SGX, AMD SEV, ARM TrustZone
Currently, leading TEE solutions are primarily provided by three major chipmakers: Intel, AMD, and ARM.
2.2.1 Intel SGX (Software Guard Extensions)
An Intel-developed TEE technology first introduced in Skylake and later CPUs. Provides a secure computing environment via Enclaves, applicable to cloud computing, blockchain privacy contracts, etc.
Key Features: Memory isolation based on Enclaves—applications can create protected enclaves to store sensitive code and data.
Hardware-level memory encryption: Data inside the Enclave is always encrypted outside the CPU, making dumped memory unreadable.
Remote attestation: Enables remote verification that the Enclave is running untampered code.
Limits: Limited Enclave memory (initially only 128MB, expandable to over 1GB). Vulnerable to side-channel attacks (e.g., L1TF, Plundervolt, SGAxe). Complex development environment (requires SGX SDK for specialized app development).
2.2.2 AMD SEV (Secure Encrypted Virtualization)
AMD’s TEE technology, mainly used for secure computing in virtualized environments. Ideal for cloud computing, offering VM-level encryption protection.
Key Features
Full memory encryption: Uses internal CPU keys to encrypt entire VM memory.
Multi-VM isolation: Each VM has its own key, preventing cross-access between VMs on the same physical machine.
SEV-SNP (latest version) supports remote attestation to verify VM code integrity.
Limits: Only applicable in virtualized environments, not suitable for non-VM applications. Higher performance overhead due to encryption/decryption costs.
2.2.3 ARM TrustZone
ARM’s TEE solution, widely used in mobile devices, IoT devices, and hardware wallets for smart contracts.
Provides Secure World (secure environment) and Normal World (regular environment) through CPU-level partitioning.
Key Features
Lightweight architecture: Does not depend on complex virtualization, suitable for low-power devices.
System-wide TEE support: Enables secure applications such as encrypted storage, DRM, and financial payments.
Hardware-based isolation, differing from SGX’s Enclave mechanism.
Limits: Lower security level than SGX and SEV, since Secure World depends on manufacturer implementation. Development constraints—some functions are restricted to device vendors, limiting third-party developer access to full TEE APIs.
2.3 RISC-V Keystone: The Open-Source Hope for TEE’s Future
2.3.1 Why Do We Need Open-Source TEE?
Intel SGX and AMD SEV are proprietary technologies, constrained by vendors. RISC-V, as an open-source instruction set architecture (ISA), allows developers to create customized TEE solutions, avoiding closed-hardware security risks.
2.3.2 Key Features of Keystone TEE
Built on RISC-V architecture, fully open source. Supports flexible security policies—developers can define their own TEE mechanisms. Suitable for decentralized computing and Web3 ecosystems, integrable with blockchain for trusted computation.
2.3.3 Future of Keystone
Potentially a key infrastructure for Web3 computing security, reducing reliance on Intel or AMD. Community-driven efforts aim to strengthen security mechanisms and reduce side-channel attack risks.
2.4 How Does TEE Ensure Data Security? From Sealed Storage to Remote Authentication
2.4.1 Sealed Storage
TEE allows applications to store encrypted data externally, decryptable only within the TEE. Examples: Private key storage, medical data protection, confidential AI training data.
2.4.2 Remote Attestation
Remote servers can verify whether the code running in the TEE is trustworthy, preventing malicious tampering. In Web3, this can validate that a smart contract executed in a trusted environment.
2.4.3 Side-Channel Attack Protection
Newer TEE designs use memory encryption, randomized data access, and other methods to reduce attack risks. Ongoing community and vendor efforts patch vulnerabilities such as Spectre, Meltdown, and Plundervolt.
Chapter 3: TEE Applications in the Crypto World — A Revolution from MEV to AI Computing
As a powerful hardware security technology, Trusted Execution Environment (TEE) is gradually becoming one of the most important computing infrastructures in the Web3 ecosystem. It not only addresses performance bottlenecks in decentralized computing but also plays a key role in MEV (Maximal Extractable Value), privacy computing, AI training, DeFi, and decentralized identity. TEE-powered Web3 computing is driving a transformation, bringing more efficient and secure solutions to the decentralized world.
3.1 Decentralized Computing: How Can TEE Solve Web3 Computing Bottlenecks?
Blockchains offer censorship resistance and high trust due to decentralization, but still face significant limitations in computing power and efficiency. Current decentralized computing platforms (e.g., Akash, Ankr) are leveraging TEE to address these issues, delivering high-performance, secure computing environments for the Web3 ecosystem.
3.1.1 Challenges in Web3 Computing
Limited computing power: Smart contracts on blockchains like Ethereum run slowly and cannot handle large-scale tasks such as AI training or high-frequency financial computation.
Data privacy issues: On-chain computation is transparent, unable to protect sensitive data like personal identifiers or trade secrets.
High computation costs: Running complex computations (e.g., ZK proof generation) on blockchains is prohibitively expensive, limiting application scalability.
3.1.2 Akash & Ankr: TEE-Powered Decentralized Computing
Akash Network
Akash offers a decentralized cloud computing marketplace where users can rent computing resources. TEE applications include:
Privacy computing: Through TEE, users can perform confidential computations in a decentralized environment without exposing code or data.
Trusted computing marketplace: Akash uses TEE to ensure rented computing resources are unaltered, enhancing task security.
Ankr Network
Ankr provides decentralized computing infrastructure, especially strong in Web3 cloud services and RPC. TEE applications in Ankr:
Secure remote computing: TEE ensures cloud-executed tasks run in trusted environments, preventing data leaks.
Censorship resistance: Combining TEE with decentralized architecture, Ankr delivers censorship-resistant computing resources, ideal for privacy-focused DApps.
3.1.3 Future Outlook
As demand for Web3 computing grows, TEE will become a standard component of decentralized computing networks, enhancing competitiveness in privacy, efficiency, and security.
3.2 Trustless MEV Transactions: Why Is TEE the Optimal Solution?
MEV (Maximal Extractable Value) is a core issue in blockchain transaction ordering, involving arbitrage, sandwich attacks, liquidations, and more. TEE offers a trustless MEV solution via trusted computation and encrypted transactions, reducing the likelihood of miner or validator misconduct.
3.2.1 Current State and Challenges of MEV
Front-running: Miners can preempt user transactions, enabling sandwich attacks.
Ordering centralization: Flashbots and other MEV solutions still rely on centralized sequencers.
Information leakage risk: Current MEV bidding systems may expose transaction data, affecting fairness.
3.2.2 TEE-Powered MEV Solutions
Flashbots & TEE: Flashbots is exploring TEE as a key technology for trustless transaction ordering (MEV Boost). Transactions can be encrypted and ordered within TEE, preventing miners or validators from altering order.
EigenLayer & TEE: EigenLayer uses TEE to ensure fairness in restaking mechanisms, preventing malicious MEV manipulation. Remote attestation verifies that MEV bidding systems are not tampered with.
3.2.3 Future Outlook
TEE can enable "trustless ordering" and "private transactions" in MEV, reducing miner manipulation and improving fairness, offering DeFi users a more equitable trading environment.
3.3 Privacy-Preserving Computing & DePIN Ecosystem: How Is Nillion Building the Next-Gen Privacy Network Powered by TEE?
Privacy computing is a major challenge in the Web3 ecosystem, especially in DePIN (Decentralized Physical Infrastructure Networks). TEE, through hardware-level encryption and isolated execution, provides strong privacy capabilities for projects like Nillion.
3.3.1 Nillion’s Privacy Computing Approach
Nillion is a blockchain-free decentralized privacy computing network combining TEE and MPC (multi-party computation) for data privacy:
Data sharding and processing: Encrypted computation via TEE prevents sensitive data leaks.
Private smart contracts: Nillion enables developers to build private DApps, with data visible only inside TEE.
3.3.2 TEE Applications in DePIN Ecosystems
Smart grids: Use TEE to protect user energy data privacy and prevent misuse.
Decentralized storage: Integrate with Filecoin to ensure stored data is processed within TEE, preventing unauthorized access.
3.3.3 Future Outlook
Projects like Nillion may become core infrastructure for Web3 privacy computing, with TEE playing an indispensable role.
3.4 Decentralized AI: How to Use TEE to Protect AI Training Data?
The convergence of AI and blockchain is a growing trend in Web3, but AI training faces data privacy and computation security challenges. TEE protects AI training data, prevents leaks, and enhances computation security.
3.4.1 Bittensor & TEE
Bittensor is a decentralized AI computing network using TEE to protect data privacy in AI training models.
Remote attestation ensures AI computing nodes are untampered, delivering trusted AI computation services.
3.4.2 Gensyn & TEE
Gensyn allows developers to run AI training tasks in decentralized environments, with TEE ensuring data confidentiality.
Combines zero-knowledge proofs (ZKP) with TEE to achieve verifiable trust in decentralized AI computation.
3.5 DeFi Privacy and Decentralized Identity: How Does Secret Network Use TEE to Protect Smart Contracts?
3.5.1 DeFi Privacy Issues
Traditional smart contracts are transparent, with all transaction data public—demand for private DeFi is huge.
Users want to protect transaction data such as balances and transaction history.
3.5.2 Secret Network & TEE
Private smart contracts: Secret Network uses TEE to protect smart contract execution, making transaction data visible only within TEE.
Decentralized Identity (DID): TEE can store user identity information, preventing leaks while supporting KYC compliance.
3.5.3 Future Outlook
TEE will play an increasingly important role in DeFi privacy and decentralized identity, providing stronger privacy protection for decentralized finance.
Chapter 4: Conclusion and Outlook — How Will TEE Reshape Web3?
As a pivotal technology in the crypto space, Trusted Execution Environment (TEE) has already demonstrated immense potential across various use cases. As the Web3 ecosystem continues to evolve, TEE’s role will grow even more critical—especially in decentralized infrastructure, privacy-preserving computing, and smart contracts. This chapter summarizes the current state of TEE technology, outlines its potential to drive Web3 innovation, and analyzes possible business models and token economics opportunities in the crypto industry.
4.1 How Can Trusted Computing Drive the Development of Decentralized Infrastructure?
4.1.1 The Necessity of Decentralized Computing
With the rise of decentralized technologies, traditional centralized computing architectures are increasingly inadequate for Web3 needs. Decentralized computing not only improves system security and fault tolerance but also enhances transparency and censorship resistance. However, decentralized systems face many challenges:
Trust issues: Unstable trust between nodes may lead to data tampering or untrustworthy computation results.
Privacy issues: Protecting user data privacy in decentralized environments remains a major challenge.
Performance issues: Decentralized computing may suffer from uneven resource distribution and low throughput.
4.1.2 TEE’s Role in Decentralized Infrastructure
TEE technology is key to solving these problems. By providing a protected, isolated computing environment, TEE supports decentralized computing systems in the following ways:
Trustless computation: Even without full mutual trust, TEE ensures computational integrity and data confidentiality.
Privacy protection: TEE enables encrypted computation without exposing data, safeguarding user privacy.
Enhanced performance: As hardware-based TEE solutions advance, computational throughput is expected to improve significantly.
TEE will become a core technological backbone for decentralized computing networks (e.g., Akash, Ankr), accelerating the maturity and adoption of decentralized infrastructure.
4.2 Potential Business Models and Token Economics Opportunities for TEE
4.2.1 Business Models Driven by TEE
As TEE technology gains traction, emerging business models and platforms are beginning to emerge. Key models include:
Decentralized computing markets: Platforms like Akash and Ankr operate decentralized computing markets where users rent computing resources, with TEE ensuring trust and privacy.
Privacy computing services: Companies offering TEE-based privacy computing services can serve industries like finance, healthcare, and insurance with encrypted data and secure computation, charging per task.
Distributed computing and storage: TEE secures data in decentralized storage and computing platforms, creating revenue opportunities via storage and computation fees.
Blockchain infrastructure providers: Offering specialized hardware or software tools enabling Web3 projects to run smart contracts and DApps within TEE environments.
4.2.2 Token Economics Opportunities for TEE
In the Web3 and crypto ecosystem, TEE can deeply integrate with tokenomics to unlock new value creation. Specific opportunities include:
Tokenized computing resources: Decentralized computing platforms can use tokens to exchange computing power—users and node operators participate in tasks, submit, and verify data using cryptocurrency, with all exchanges governed by smart contracts.
Token incentives for TEE services: Privacy computing services based on TEE can use tokens as incentives or payment methods to ensure smooth execution and validation of privacy tasks.
Decentralized identity and data exchange: TEE can support DID systems with technical backing for data privacy, while token-based incentives promote widespread adoption of decentralized identity and data sharing.
4.3 Key Directions for TEE in the Crypto Industry Over the Next Five Years
4.3.1 Deep Integration of TEE and Web3
In the next five years, TEE will play an even greater role in Web3, particularly in these key areas:
Decentralized Finance (DeFi): TEE will be widely adopted in DeFi protocols to protect transaction privacy, ensure trustworthy computation, and enhance smart contract security.
Privacy Computing: As global privacy regulations mature, privacy computing will become a core component of Web3. Integrating TEE with ZKP, FHE, and other technologies will deliver more robust privacy solutions.
Decentralized Artificial Intelligence (AI): TEE provides a secure environment for decentralized AI, supporting safe model training and inference, enabling intelligent decentralized applications.
Cross-chain computing: As blockchain ecosystems expand, TEE will facilitate trusted computation across chains, making cross-chain asset swaps and data processing more secure and efficient.
4.3.2 Hardware and Protocol Innovation in TEE
Ongoing TEE advancements will drive improvements in performance and security:
Hardware innovation: Next-gen hardware TEE solutions like RISC-V Keystone and Intel TDX (Trusted Domain Extensions) are expected to surpass current offerings in performance, security, and scalability.
Protocol innovation: Integration of TEE with MPC, ZKP, and other technologies will spawn new privacy-preserving and trustless protocols.
Decentralized hardware platforms: These will break away from single-vendor models, enabling more small nodes to join the trusted computing ecosystem, maximizing utilization of decentralized computing resources.
4.3.3 Regulatory Compliance and Privacy Evolution
With tightening global privacy regulations, innovation in TEE compliance will be a key direction over the next five years:
Multi-jurisdiction compliance: TEE technology will adapt to regional privacy laws (e.g., GDPR, CCPA, PIPL), ensuring decentralized computing meets global data protection standards.
Verifiable privacy computing: Combining TEE with ZKP will make privacy computations auditable, increasing regulator trust and facilitating compliance.
Chapter 5 Summary
TEE technology holds broad application potential in the Web3 ecosystem, capable of providing trustless computing environments and effectively protecting user privacy. As TEE continues to evolve, it will play an increasingly vital role in decentralized computing, privacy protection, and smart contracts, driving maturity and innovation in the Web3 ecosystem. Meanwhile, TEE will spawn new business models and token economics opportunities, creating additional value in the crypto industry. Over the next five years, with hardware innovation, protocol development, and regulatory adaptation, TEE will become an indispensable core technology in the crypto industry.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News