The Key to Connecting All Chains: Cross-Chain Interoperability Protocol
TechFlow Selected TechFlow Selected

The Key to Connecting All Chains: Cross-Chain Interoperability Protocol
A fully on-chain interoperability protocol is a new paradigm extended from cross-chain technology.
Author: YBB Capital Researcher Zeke
Preface
Since its inception, blockchain has been marked by constant disputes—evolving from the original vision of an "electronic payment system" to concepts like "world computer," "high-speed parallel chains," and "application-specific chains for gaming/finance." Divergent values and technical disagreements have given rise to hundreds of public blockchains. Due to their inherent decentralization, blockchains are relatively closed and isolated systems that cannot perceive or interact with the outside world, leaving individual chains as disconnected islands unable to interoperate. Today’s dominant narrative in public blockchains is moving toward a multi-layered modular architecture, including not only Layer 2 execution layers but also data availability (DA) layers, settlement layers, and even execution layers atop other execution layers. Fragmented liquidity and disjointed user experiences will continue to worsen, while traditional cross-chain bridge solutions remain fraught with risks.
From the perspective of an average user, transferring assets across chains via bridges is already cumbersome and time-consuming. On top of that, users may face issues such as incompatible assets, hacker attacks, soaring gas fees, and insufficient liquidity on the target chain. The lack of interoperability between chains not only hinders widespread blockchain adoption but also makes different public chains resemble hostile tribes or nations. Base-layer blockchains continue to debate trade-offs around the "trilemma," while different layers argue over whose solution is superior. As multi-chain and multi-layer development intensifies, traditional cross-chain bridges can no longer meet industry needs. Web3's demand for omnichain connectivity is now more urgent than ever. So, how far has omnichain interoperability progressed? And how far are we from reaching the next billion users?
What Is Omnichain Interoperability?
In traditional internet environments, we rarely experience fragmented user experiences. For example, in payment scenarios, platforms like Alipay or WeChat Pay allow seamless transactions across nearly all websites. However, in the Web3 world, natural barriers exist between public blockchains. In simple terms, omnichain interoperability protocols act as hammers breaking down these walls—enabling seamless transfer of assets and information across multiple blockchains through cross-chain communication solutions. Their ultimate goal is to achieve a seamless experience comparable to Web2, progressing toward chain-agnostic or even intent-centric models.
Achieving omnichain interoperability involves overcoming several key challenges, including communication between heterogeneous smart contract platforms and non-wrapped methods for cross-chain asset transfers. To address these issues, projects like LayerZero and Wormhole have proposed innovative solutions, which we will analyze later. But first, it's important to understand the differences between omnichain protocols and traditional cross-chain bridges, the existing challenges in cross-chain technology, and current approaches.
How Omnichain Changes Things
Unlike traditional third-party bridges where users must lock assets on the source chain, pay gas, and wait to receive wrapped tokens on the destination chain, omnichain interoperability represents a new paradigm built upon cross-chain technology. It functions as a communication hub transmitting everything—including assets—across chains. This enables true interoperation between chains. Take Sushi, which integrates Stargate’s routing system: users can seamlessly swap assets between source and destination chains directly within Sushi, greatly optimizing the cross-chain experience. Future use cases could include seamless interactions between decentralized applications (DApps) running on different blockchains.
The Trilemma and Three Types of Verification
The blockchain world is full of trade-offs, much like the famous scalability trilemma. Cross-chain solutions face a similar interoperability trilemma: due to technical and security constraints, protocols can only optimize two out of three key attributes:
1. Trustlessness: No reliance on centralized trust entities; provides security at the same level as the underlying blockchain. Users do not need to trust intermediaries or third parties to ensure secure and correct transaction execution;
2. Extensibility: The protocol can easily integrate with any blockchain platform regardless of specific technical architectures or rules, supporting broad ecosystem compatibility beyond just a few select networks;
3. Generalizability: The ability to handle any type of cross-domain data or asset transfer—not limited to specific transaction types or assets. This means blockchains can exchange various forms of information and value, including cryptocurrency, smart contract calls, and arbitrary data.
Early classifications of cross-chain bridges followed thinkers like Vitalik Buterin, who divided them into three categories: hash time-lock contracts, custodial validators (watchmen), and relay-based verification (light clients). Later, Arjun Bhuptani, founder of Connext, reclassified cross-chain solutions into three models based on trust assumptions: natively verified (trustless + extensible), externally verified (extensible + generalizable), and locally verified (trustless + generalizable). These verification methods differ in trust models and technical implementation, catering to varying security and interoperability requirements.
Natively Verified:
● Natively verified bridges rely on the consensus mechanisms of both the source and destination chains to directly validate transactions, eliminating the need for additional validation layers or intermediaries. For instance, some bridges implement smart contracts that create direct validation logic between two blockchains, allowing each chain to confirm transactions using its own consensus mechanism. This approach enhances security by leveraging the inherent security of participating chains. However, it can be technically complex and isn't supported by all blockchains.
Externally Verified:
● Externally verified bridges use third-party validators or validator clusters to verify transaction validity. These validators—such as independent nodes, consortium members, or other participants—operate independently of the source and destination chains. This model typically involves cross-chain message passing and validation logic executed by external entities rather than the chains themselves. While this allows greater flexibility and wider interoperability, it introduces additional trust assumptions and potential security risks. (Despite high centralization risks, external verification remains the most common cross-chain method due to its flexibility, efficiency, and low cost.)
Locally Verified:
● Locally verified refers to a model where the destination chain verifies the state of the source chain to confirm and execute transactions locally. This is typically achieved by running a light client of the source chain inside the destination chain's virtual machine, or vice versa. Local verification relies on either an honest minority assumption (at least one honest relayer in the committee) or a synchrony assumption (users must manually transmit transactions if the committee fails). This is the most trust-minimized form of cross-chain communication, though it comes with high costs, lower development flexibility, and works best between blockchains with similar state machines—such as Ethereum and its L2s, or Cosmos SDK-based chains.
Different Types of Solutions
As one of the most critical infrastructures in the Web3 world, designing cross-chain solutions remains a persistent challenge, leading to a wide variety of approaches. Currently, these can be categorized into five main types, each offering unique ways to facilitate asset exchange, transfer, and contract invocation.1
● Token Swaps: Allow users to trade an asset on one blockchain and receive an equivalent asset on another. Using technologies like atomic swaps and cross-chain automated market makers (AMMs), liquidity pools can be created across chains to enable asset exchanges;
● Asset Bridges: Involve locking or burning assets on the source chain and minting corresponding assets on the destination chain. Based on how assets are handled, this can be further divided into three subtypes:
○ Lock/Mint Model: Assets are locked on the source chain, and an equivalent "bridged asset" is minted on the destination chain. Reversing the process burns the bridged asset to unlock the original;
○ Burn/Mint Model: Assets are burned on the source chain and reminted in equal quantity on the destination chain;
○ Lock/Unlock Model: Assets are locked on the source chain and unlocked from a liquidity pool on the destination chain. These bridges often incentivize liquidity providers through revenue-sharing mechanisms;
● Native Payments: Enable applications on the source chain to trigger payments using native assets on the destination chain, or initiate cross-chain payments based on data from one chain. Often used for settlements triggered by blockchain data or external events;
● Smart Contract Interoperability: Allows smart contracts on the source chain to invoke functions on destination chain contracts based on local data, enabling complex cross-chain applications such as asset swaps and bridging operations;
● Programmable Bridges: An advanced interoperability solution combining asset bridging with message transmission. When assets move from source to destination, they can immediately trigger contract executions on the destination chain, enabling functionalities like staking, swapping, or depositing assets into smart contracts.
LayerZero

As the most well-known project in the omnichain interoperability space, LayerZero has attracted major crypto investors including a16z, Sequoia Capital, Coinbase Ventures, Binance Labs, and Multicoin Capital, raising a total of $315 million across three funding rounds. Beyond the project’s appeal, this highlights the strategic importance top-tier capital places on the omnichain sector. Yet despite its prominence, LayerZero has long been controversial, frequently criticized for centralization risks and ecosystem shortcomings. Setting aside the hype and bias, let’s examine whether LayerZero’s architecture holds real potential to unify chains.
Trustless Cross-Chain Communication: As previously noted, most mainstream bridge solutions rely purely on external verification, shifting trust off-chain and significantly reducing security (this is why many multisig bridges fail—hackers only need to target custodians). In contrast, LayerZero splits verification between two independent entities—the oracle and the relayer—minimizing the flaws of external validation. In theory, their independence creates a fully trustless and secure environment. However, attackers could still target either component, and collusion between oracle and relayer remains a risk. Thus, LayerZero’s claim of trustlessness in V1 contains logical vulnerabilities. The upcoming V2 version introduces a Decentralized Verifier Network (DVN) to improve validation, which we’ll discuss below.
LayerZero Endpoint: Endpoints are core components of the protocol. While V1’s oracle and relayer (and V2’s DVNs) focus on message validation and fraud prevention, endpoints are smart contracts enabling actual message exchange between native environments of two blockchains. Each endpoint on every participating chain consists of four modules: Communicator, Validator, Network, and Libraries. The first three enable core protocol functionality, while Libraries allow developers to extend features and add blockchain-specific custom functions. These libraries enable LayerZero to adapt to diverse blockchains with different architectures and VMs—for example, both EVM-compatible and non-EVM chains.
How It Works: The LayerZero communication system centers on endpoints, with the first three modules forming the foundation of cross-chain messaging. The process begins when an application on Chain A sends a message containing transaction details, destination chain ID, payload, and payment info to the Communicator. The Communicator packages this into a data packet and forwards it to the Validator. The Validator then collaborates with the Network module to begin transferring Chain A’s block header to Chain B, instructing the Relayer to pre-fetch transaction proofs. The Oracle retrieves the block header, and the Relayer fetches the proof, sending both to Chain B’s Network contract, which passes the block hash to the Validator. After verifying the packet and proof, the Validator forwards the message to Chain B’s Communicator, which delivers it to the target app—completing the cross-chain communication.
In LayerZero V2, the Oracle will be replaced by a Decentralized Verifier Network (DVN) to resolve concerns about off-chain centralization and insecurity. Simultaneously, the Relayer will be replaced by an Executor, whose role is limited to executing transactions without performing validation.
Modular and Scalable: Developers can use the Libraries module to extend LayerZero’s core functionality on any blockchain. These modules are part of the protocol’s smart contract suite and allow new, chain-specific features without modifying the core code. The protocol is highly scalable due to its lightweight message setup. Its simple user experience is another key advantage: cross-chain operations can be completed as a single transaction, avoiding the wrapping/unwrapping steps typical of traditional bridges. As a result, the experience resembles a simple token swap on the same chain.
LayerZero Scan: With LayerZero supporting nearly 50 public chains and L2s, tracking message activity is challenging. LayerZero Scan addresses this by serving as a cross-chain explorer, showing all protocol message exchanges across participating chains. Users can filter activities by source or destination chain, or explore transaction history per DApp using LayerZero.
OFT (Omnichain Fungible Token): The OFT standard enables developers to create tokens with native-level functionality across multiple chains. OFT works by burning tokens on one chain and minting copies on the destination. Originally limited to EVM-compatible chains, LayerZero expanded the standard in OFT v2 to support non-EVM platforms.
ONFT (Omnichain Non-Fungible Token): ONFT is the non-fungible counterpart to OFT. NFTs built on the ONFT standard can be natively transferred and stored across any chain supporting the standard.
Wormhole

Like LayerZero, Wormhole is a leading omnichain interoperability protocol. It recently gained attention during its airdrop campaign. First launched in October 2020, Wormhole has evolved from a bidirectional token bridge in V1 to a platform enabling native cross-chain applications across multiple chains. Its most infamous incident occurred on February 3, 2022, when it suffered a hack resulting in the theft of $360 million worth of ETH. Remarkably, Wormhole replenished the funds within 24 hours (source unknown), and recently announced a $225 million funding round. What gives Wormhole such strong appeal among investors?
Precise Targeting: Unlike many EVM-focused protocols, Wormhole targets non-EVM ecosystems. It is the only major omnichain protocol supporting heterogeneous chains like Solana and Move-based platforms (APT, SUI). As these ecosystems recover and grow, Wormhole’s strategic positioning ensures its relevance and success.
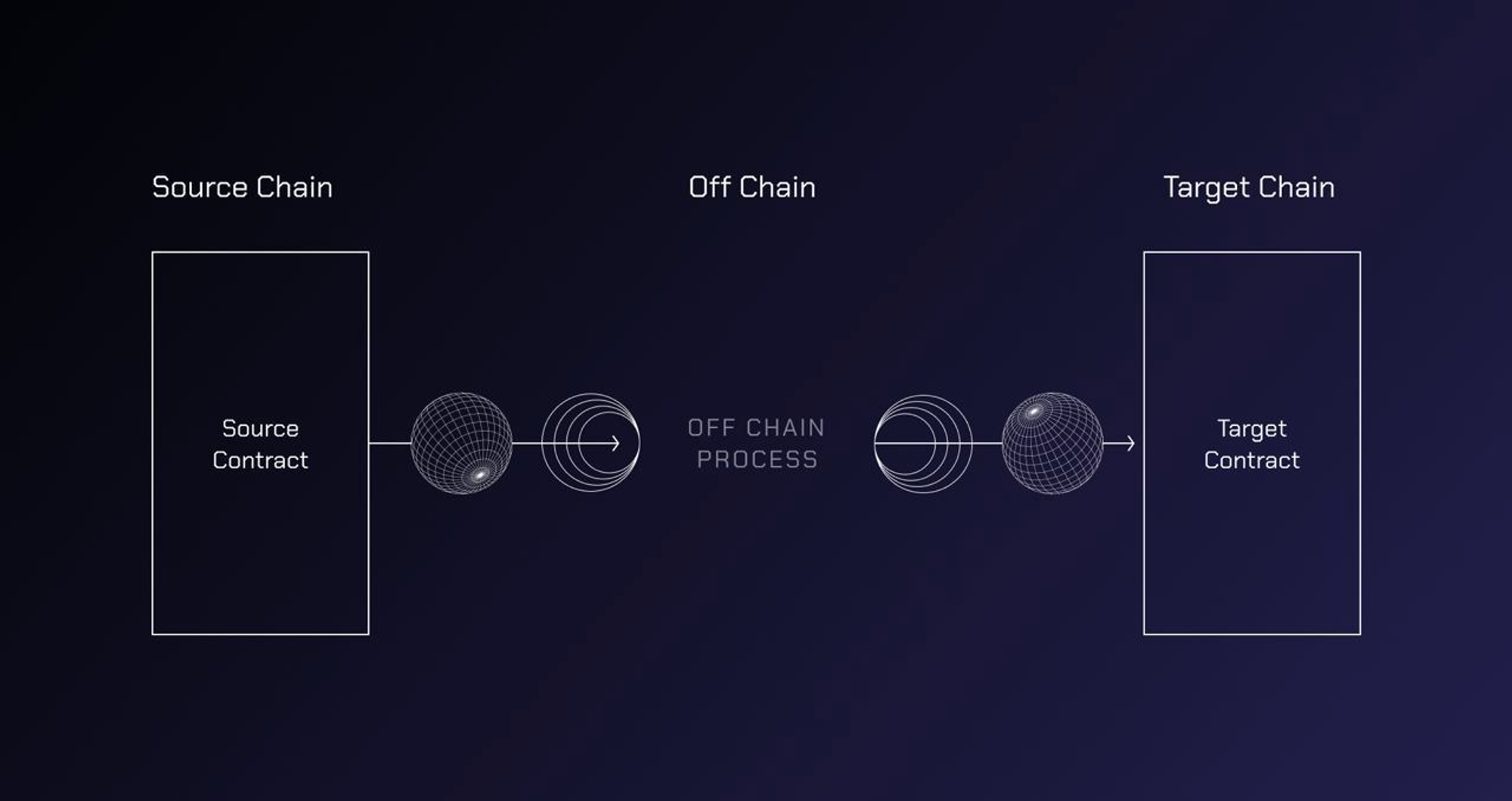
How It Works: At its core, Wormhole uses the Verifiable Action Approval (VAA) protocol and 19 Guardian nodes (selected from reputable industry institutions, though this centralization draws criticism). Cross-chain requests are converted into VAAs via Wormhole Core Contracts on each chain. The workflow is as follows:
1. Event Detection and Message Creation: A specific event on the source chain (e.g., asset transfer request) is captured and packaged into a message detailing the action;
2. Guardian Node Monitoring and Signing: The 19 Guardian nodes monitor for cross-chain events. Upon detection, they validate the event and sign it with their private keys (requires approval from at least two-thirds of nodes);
3. VAA Generation: Once enough signatures are collected, they are bundled into a VAA—an auditable, verifiable approval containing event details and node signatures;
4. VAA Transmission: The VAA is sent to the destination chain, where the Wormhole Core Contract verifies its authenticity by checking the guardian signatures and ensuring data integrity;
5. Execution: Once validated, the destination contract executes the requested operation—minting tokens, transferring assets, calling smart contracts, or custom actions—effectively mirroring the source chain’s event.
Security Modules: Wormhole is developing three internal security features—Regulatory, Accounting, and Emergency Shutdown—all built in public view for transparency. These await final development and adoption by guardians.2
1. Regulatory: Implemented at the guardian/oracle layer, it allows guardians to monitor value flows on regulated chains within a time window. Each chain has a set cap; flows exceeding it are blocked;
2. Accounting: Maintained by guardians on a dedicated blockchain ("wormchain") acting as a cross-chain ledger. This enables independent validation of fund sufficiency before approving transfers;
3. Shutdown: Implemented on-chain, allowing guardians to collectively pause asset flows if a threat is detected. Current implementation uses on-chain function calls.
Fast Integration: Wormhole’s Connect product offers developers a simple bridging tool requiring only a few lines of code. For example, an NFT marketplace wanting to bridge NFTs from Ethereum to Solana can offer users a quick, in-app tool for seamless cross-chain movement.
Messaging: In a diverse blockchain landscape, messaging is essential. Wormhole’s Messaging product provides a decentralized solution for secure and easy exchange of information and value across chains. With simplified integration, it accelerates user and liquidity growth while maintaining high security and decentralization. For instance, a DeFi project on Ethereum can interact with one on Solana without complex intermediaries.
NTT Framework: The Native Token Transfer (NTT) framework enables native token and NFT transfers across blockchains while preserving intrinsic properties. NTT supports direct transfers without relying on liquidity pools, eliminating LP fees, slippage, and MEV risks. It also integrates with any token standard or governance system, allowing teams to retain full control, upgrade rights, and customization.
Conclusion
Although still in early stages, omnichain interoperability protocols currently face risks related to security and centralization, and their user experience still lags behind Web2 ecosystems. Nevertheless, compared to earlier cross-chain bridge technologies, today’s solutions represent significant progress. Looking ahead, omnichain interoperability is a grand narrative aiming to unify thousands of isolated chains. Especially in this era of modular architectures pursuing extreme speed and cost-efficiency, omnichain protocols serve as a pivotal link between past and future—one of the most crucial sectors we must closely watch.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News