Can evidence obtained from cryptocurrency exchanges in cryptocurrency-related cases be used directly?
TechFlow Selected TechFlow Selected

Can evidence obtained from cryptocurrency exchanges in cryptocurrency-related cases be used directly?
This article analyzes the compliance of obtaining evidence from virtual currency exchanges and elaborates on the principles of evidence collection.
Author: Attorney Liu Zhengyao
Introduction
As virtual currencies become increasingly known, their use in criminal activities such as money laundering, fraud, operating gambling sites, and illegal business operations is growing. Due to a series of regulatory policies issued by mainland China in 2017 and 2021 targeting virtual currencies, domestic cryptocurrency exchanges have been comprehensively banned. Currently, popular cryptocurrency exchanges used by Chinese users (such as Binance, OKX, Bybit, Bitget, HTX, etc.) all operate overseas.
This presents a challenge for public security investigative agencies within China: while the criminal acts may occur domestically or victims reside in China, critical transaction data, exchange KYC (identity verification) information, and login logs are stored on servers located abroad. Can "electronic data" obtained by law enforcement agencies via email or online policing systems from overseas exchanges be used as evidence in court?
The author will analyze this practical issue from the perspective of a defense lawyer, based on China's Criminal Procedure Law and relevant judicial interpretations.
I. Current Practice: How Do Law Enforcement Agencies Obtain Evidence from Overseas Exchanges?
Before discussing whether such evidence can be used, it's essential to understand how electronic evidence in cases is obtained. At present, there are three main ways for public security organs in mainland China to obtain data from overseas exchanges, each with different legal validity:
(1) International Criminal Judicial Assistance
This is the most formal and internationally lawful method. It involves contacting the competent authorities of the country or region where the virtual currency exchange is registered or where its servers are located through China’s Ministry of Justice, based on bilateral criminal judicial assistance treaties. However, this method has significant drawbacks: the process is extremely cumbersome and typically takes six months to several years. For fast-moving crypto-related cases, even a one-day delay could result in the value of involved cryptocurrencies dropping to zero. This inefficiency makes it almost impossible to meet investigative needs, so it is rarely chosen in practice.
(2) Police Cooperation and “Green Channel”
Based on Interpol or other international police cooperation mechanisms, evidence collection from involved exchanges can be relatively faster.
In reality, however, what is more common is—domestic law enforcement directly utilizing the external "law enforcement cooperation mechanisms" established by cryptocurrency exchanges (e.g., Binance, OKX).
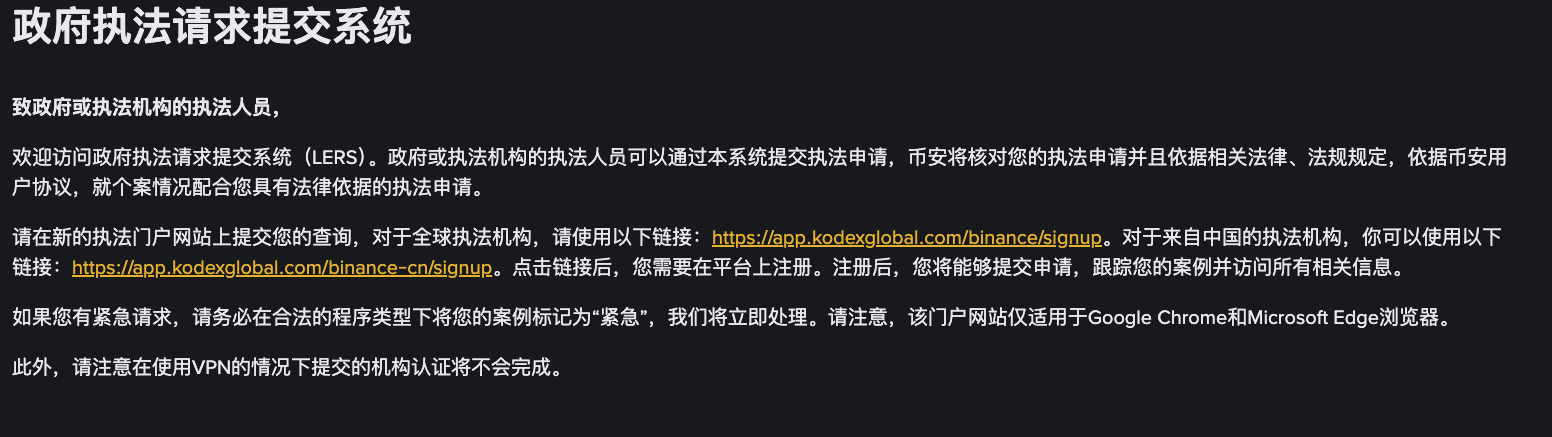
(The above image shows Binance's official website "Government Law Enforcement Request Submission System," source: Binance official site)
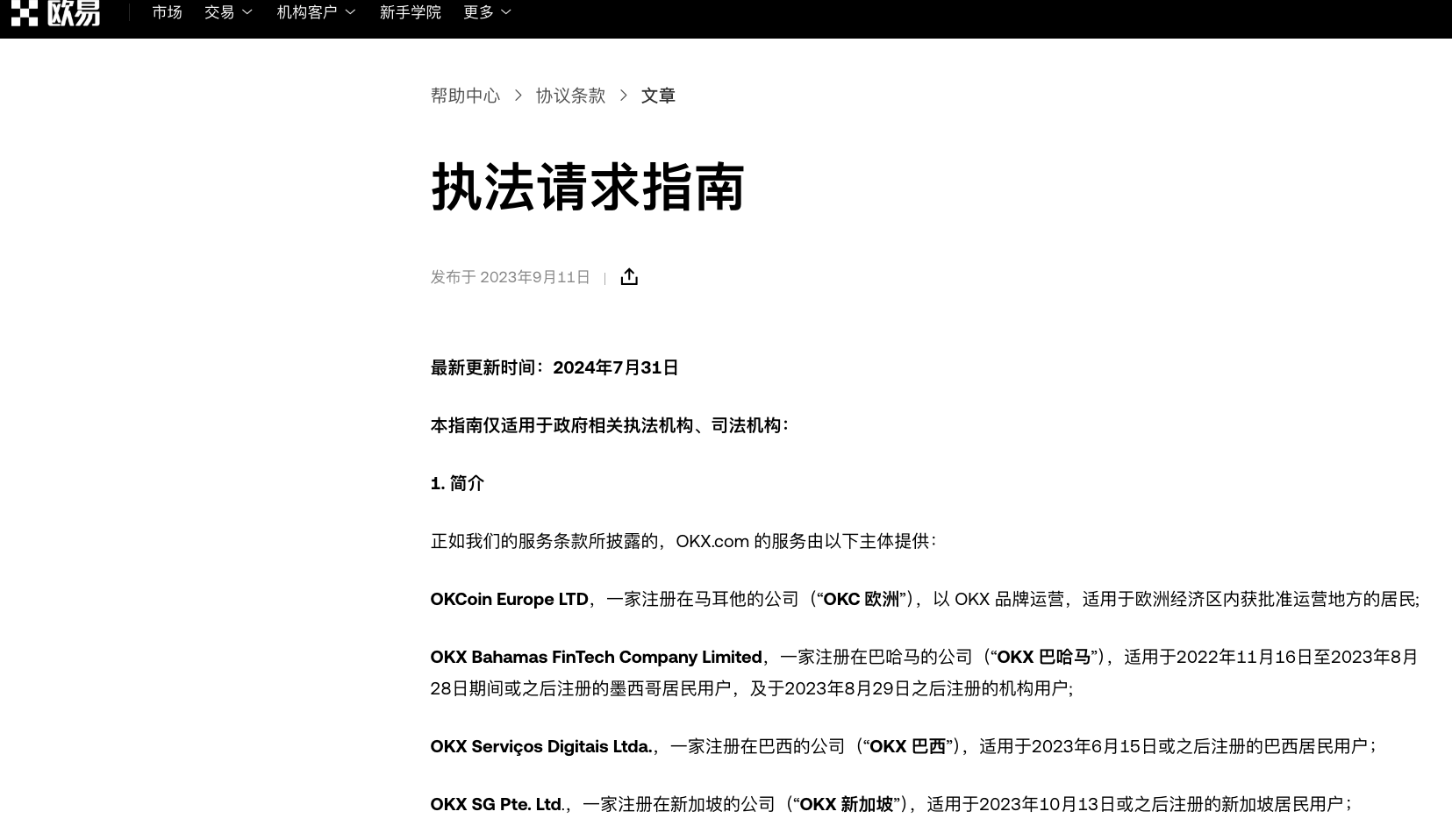
(The above image shows OKX's official website "Law Enforcement Request Guide," source: OKX official site)
In actual operation, investigating officers can authenticate their identity through Binance’s system (law firms or lawyers can also register), then send official letters requesting evidence (such as scanned copies of case-filing decisions or notices for evidence retrieval). After review by the exchange's compliance team, data is returned via email in Excel or PDF format. OKX receives such requests via email from judicial authorities. This is currently the primary method of evidence collection in most cryptocurrency-related cases in China.
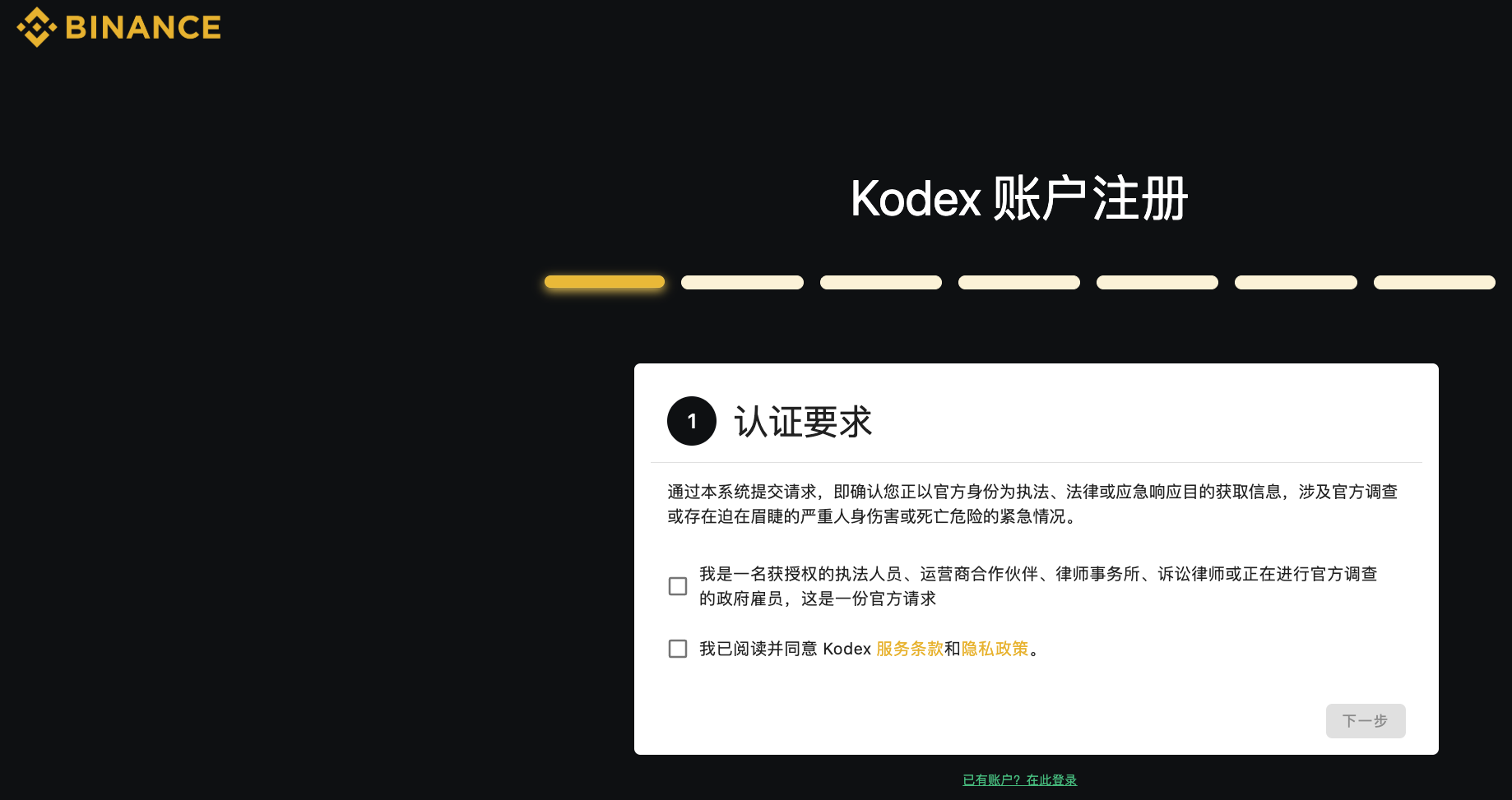
(The above image shows Binance's evidence request platform registration page, source: Binance official site)

(The above image shows OKX's evidence request method, source: OKX official site)
(3) Self-conducted Technical Extraction and “Remote Examination”
This is a relatively common method in judicial practice. When suspects are apprehended, investigators may use seized devices such as mobile phones or computers to log into their exchange accounts and directly view or export transaction records and deposit/withdrawal history. Data obtained this way is frequently used directly as prosecution evidence.
According to Article 33 of the 2019 Ministry of Public Security "Rules on Electronic Data Collection in Criminal Cases" (hereinafter referred to as the "2019 Rules"), this method falls under remote network examination and constitutes direct extraction of electronic data from domestically controlled devices, rather than direct evidence collection from foreign entities—raising certain procedural controversies (see below).
II. Core Controversy: The Legitimacy Dilemma of Evidence Obtained from Abroad
Currently, in our defense work, we mainly focus on challenging the legality and authenticity of evidence when prosecutors present Excel spreadsheets or PDF files sent directly from overseas cryptocurrency exchanges (via email) during trial.
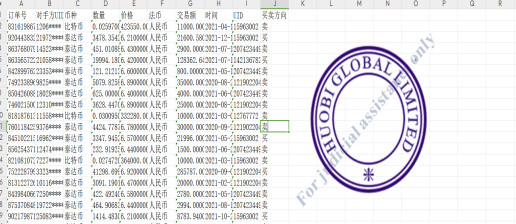
(The above image shows transaction records of an account retrieved by police from Huobi in a virtual currency case handled by our team)
(1) Legal Basis for Cross-border Evidence Collection
It is well known that exchanges like Binance, OKX, and Bybit are often registered or operated in jurisdictions such as the Cayman Islands, Seychelles, Dubai, Hong Kong, or Singapore. As previously mentioned, according to standard electronic evidence procedures in criminal cases, domestic Chinese investigative agencies cannot directly collect evidence abroad; strictly speaking, they should do so through international judicial assistance. However, in practice, very few agencies follow this route. Instead, most rely directly on the 2016 Supreme People's Court, Supreme People's Procuratorate, and Ministry of Public Security ("two highs and one ministry") "Provisions on Several Issues Concerning the Collection, Extraction, and Review of Electronic Data in Criminal Cases" (hereinafter referred to as the "2016 Provisions") and the 2019 Rules, which allow for "online extraction" or "remote examination" of electronic data stored overseas.
Thus, law enforcement agencies base their cross-border evidence gathering on judicial interpretations or internal regulations issued by the Ministry of Public Security. However, Article 25 of the "International Criminal Judicial Assistance Law" clearly states that overseas electronic data must be obtained through formal judicial assistance procedures. Nevertheless, those familiar with China's criminal defense landscape know that such disputes are usually treated at most as procedural flaws or minor controversies, rarely affecting the substantive outcome of a case.
(2) Data “Authenticity” and “Integrity” Cannot Be Self-verified
If domestic law enforcement uses the aforementioned "law enforcement cooperation mechanism," the data returned by cryptocurrency exchanges is typically just an ordinary Excel/PDF file without third-party notarization. Some lack digital signatures, and sometimes the sender is merely an individual employee’s personal email address.
As defense attorneys, we might raise questions such as: How can we prove the file transmitted via email hasn’t been altered? How can we confirm that a personal email truly represents the official exchange? How can we verify that no technical errors occurred during data generation? And so on.
In practice, because exchange employees are unlikely to testify in court, the authenticity and integrity of such evidence often cannot be substantiated.
(3) The Exchange's Own Legality Is Questionable Within Mainland China
According to the September 24, 2021 notice issued by ten national departments (including the "two highs and one ministry") titled "Notice on Further Preventing and Addressing Risks Associated with Virtual Currency Trading and Speculation," overseas cryptocurrency exchanges are prohibited from conducting any form of business activities within mainland China, and all such operations are deemed "illegal financial activities." Thus, from the regulatory standpoint within mainland China, these overseas exchanges themselves operate under an inherent "aura of illegality." Therefore, the legitimacy of evidence collected by domestic law enforcement from such foreign, allegedly illegal entities is highly questionable.
III. Can Courts Use Such Evidence?
Despite the above flaws, in current judicial practice, instances where evidence obtained by police from overseas exchanges is excluded by courts are rare. In most cases, even if obvious defects exist, such evidence is still admitted after being "corrected." When reviewing such evidence, courts generally follow these logical standards:
(1) Distinguishing Between “Flawed Evidence” and “Illegal Evidence”
Courts tend to hold that obtaining evidence via email from overseas exchanges, although not fully compliant with strict judicial assistance procedures, does not constitute "illegal evidence" that would "seriously affect judicial fairness due to violation of statutory procedures." Instead, it is treated as "flawed evidence"—which can be remedied through correction or reasonable explanation, rather than outright exclusion.
(2) Corroboration by Other Evidence
More rigorous investigative agencies and procuratorial organs may take the following steps to strengthen electronic data obtained directly from overseas exchanges:
First, record audio and video throughout the entire process of sending and receiving emails. Additionally, perform hash verification (e.g., MD5 or SHA-256) on received email content to ensure data integrity;
Second, notarize the process or use third-party preservation. Have a notary office certify the full process of sending and receiving evidence-request emails, or employ blockchain-based evidence storage to prove that "the email indeed came from the exchange's official mailbox and was not modified by investigators."
Third, attach analytical reports. Hire domestic blockchain security companies to issue analysis reports. While they cannot verify internal exchange data (like KYC), they can verify on-chain data. The basic logic is: if the transaction hash values in the Excel sheet provided by the exchange match publicly available data on blockchain explorers, this indirectly supports the authenticity of the exchange's data.
Fourth, corroboration with other evidence in the case. Compare exchange data with the defendant’s confession, chat logs from seized phones, and locally cached data. If multiple sources align, courts usually admit the evidence.

IV. Defense Perspective: Effective Ways to Challenge the Evidence
For defendants and their defense counsel facing evidence submitted by law enforcement from overseas exchanges, there are effective strategies. Below are key points of challenge summarized by Attorney Liu based on practical experience:
(1) Scrutinizing the Authenticity of KYC (Account Ownership)
KYC data provided by exchanges (usually passport or ID card information) is typically static. Defense counsel should pay special attention to whether the KYC information linked to the accused account could have been acquired through purchased identities—that is, without additional supporting evidence, the registered account holder may not actually be the one operating it (similar to real-world cases involving the buying and selling of bank cards). Moreover, checking whether the IP addresses used to log into the exchange account align with the suspect’s life轨迹 can help verify whether the accused was genuinely using the account.
(2) Challenging Data Integrity
If the evidence consists only of printed screenshots of Excel sheets or other paper copies instead of original electronic files, it cannot be proven unique or tamper-proof. Furthermore, some prosecutors incorrectly treat printed transaction records or chat logs as documentary evidence—this is entirely wrong, and defense lawyers must firmly oppose it.
(3) Addressing the Specific Nature of Stablecoins Like USDT
Data obtained from Tether or decentralized wallets differs fundamentally from that of centralized exchanges (like Binance). On-chain data is public and accessible to anyone. If prosecutors only provide blockchain transfer diagrams without linking wallet addresses to real identities through exchange KYC data, the evidentiary chain remains broken.
V. Final Thoughts
To summarize: Can evidence obtained from overseas exchanges be used? Briefly: yes, but with conditions—and room for technical challenges. Specifically:
First, regarding admissibility. Chinese courts generally do not reject the evidentiary status of data from overseas exchanges. As long as law enforcement can demonstrate objective sourcing (e.g., through notarized email exchanges), such evidence is typically accepted.
Second, regarding probative value. A standalone Excel spreadsheet from an exchange carries weak evidentiary weight. A closed loop must be formed combining "on-chain data + internal exchange data + defendant device data + fund flow trails."
Third, practical trends. As major exchanges like Binance and OKX strengthen compliance, the format of their responses is becoming more standardized (now often including electronic seals), making it harder for defense teams to attack based on "formal authenticity."
A Suggestion:
For law enforcement: Ensure full documentation (audio/video recording or notarization) of the entire process from sending requests to receiving replies from overseas cryptocurrency exchanges. Consider engaging professional institutions to conduct blockchain traceability analysis to strengthen evidence.
For defendants and defense counsel: Focus on examining the originality of electronic data (whether original files were transferred), consistency (whether hash values match), and relevance (whether the possibility of someone else operating the account can be ruled out).
In the near future, the interplay between technology and law in cryptocurrency cases will continue. The use of overseas evidence will gradually shape new judicial standards through this ongoing contest.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News