Analyzing the hacking methods and questions behind the recent $1.5 billion theft from Bybit
TechFlow Selected TechFlow Selected

Analyzing the hacking methods and questions behind the recent $1.5 billion theft from Bybit
Hacker groups, especially state-sponsored hackers such as Lazarus Group, are continuously upgrading their attack methods.
Author: SlowMist Security Team
Background
On the evening of February 21, 2025, Beijing time, according to on-chain investigator ZachXBT, Bybit experienced a massive outflow of funds. This incident led to the theft of over $1.46 billion, making it the largest cryptocurrency theft in recent years in terms of financial loss.
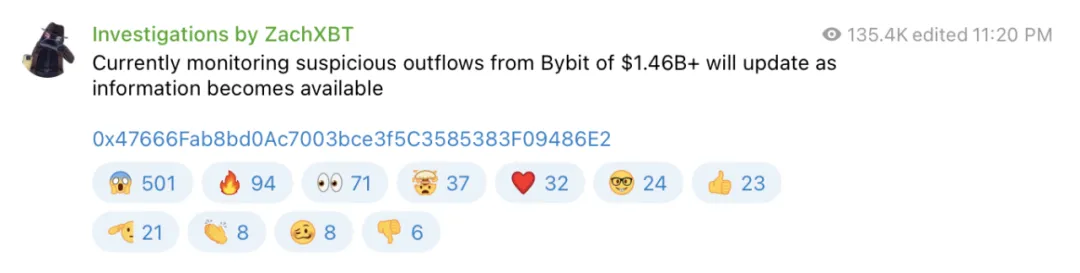
On-Chain Tracking Analysis
Immediately after the incident, the SlowMist security team issued a security alert and began tracking and analyzing the stolen assets:
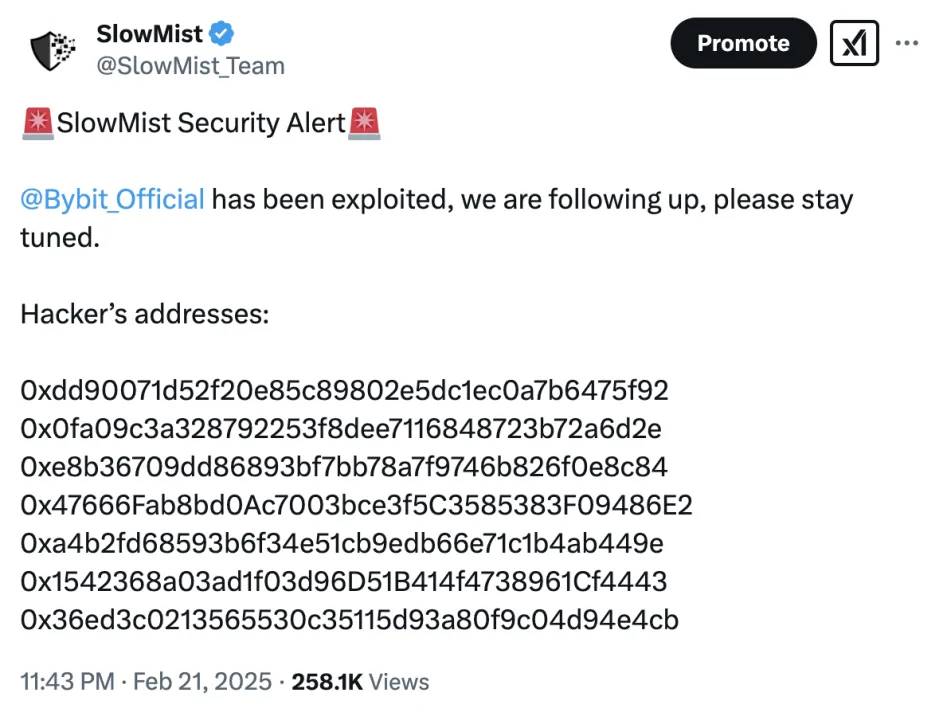
According to SlowMist's analysis, the stolen assets primarily include:
· 401,347 ETH (worth approximately $1.068 billion)
· 8,000 mETH (worth approximately $26 million)
· 90,375.5479 stETH (worth approximately $260 million)
· 15,000 cmETH (worth approximately $43 million)
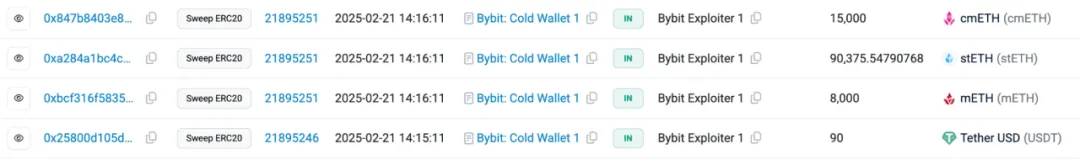
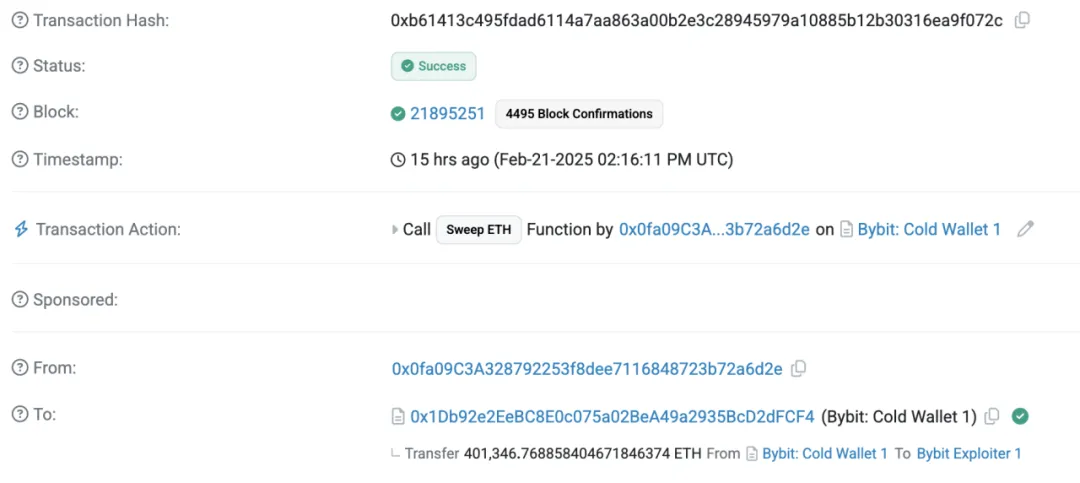
We used MistTrack, an on-chain tracking and anti-money laundering tool, to analyze the initial hacker address
0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2
and obtained the following information:
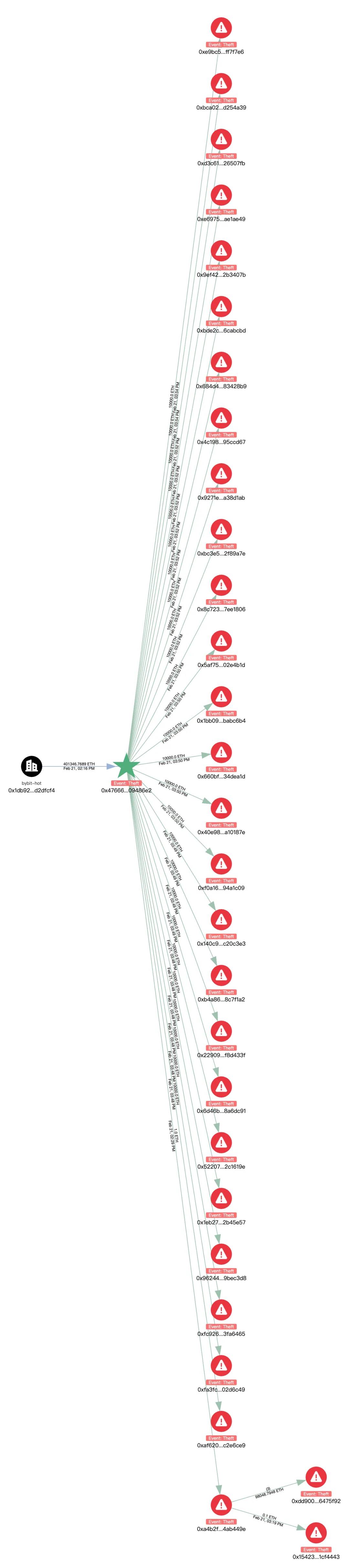
The ETH was dispersed; the initial hacker address transferred 400,000 ETH in chunks of 1,000 ETH to 40 different addresses, with further transfers ongoing.
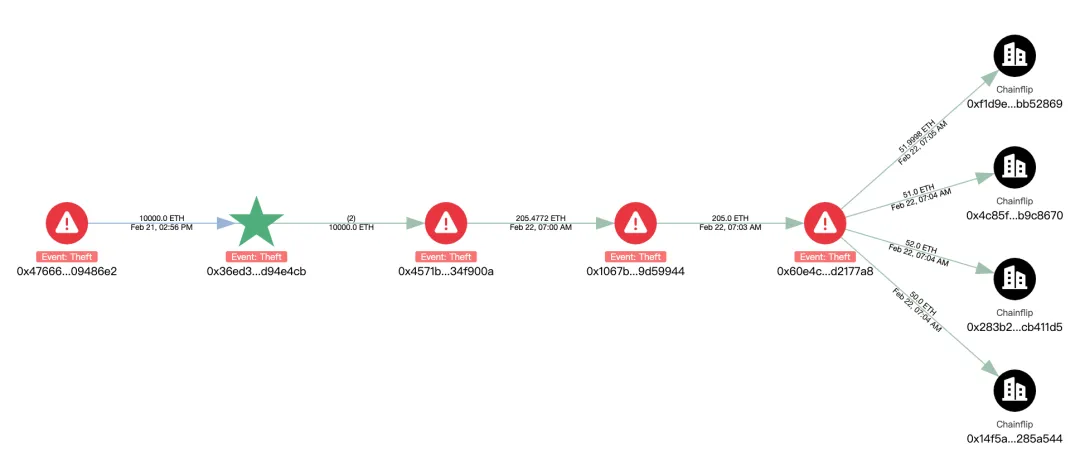
Among them, 205 ETH were swapped into BTC via Chainflip and cross-chained to the address:
bc1qlu4a33zjspefa3tnq566xszcr0fvwz05ewhqfq
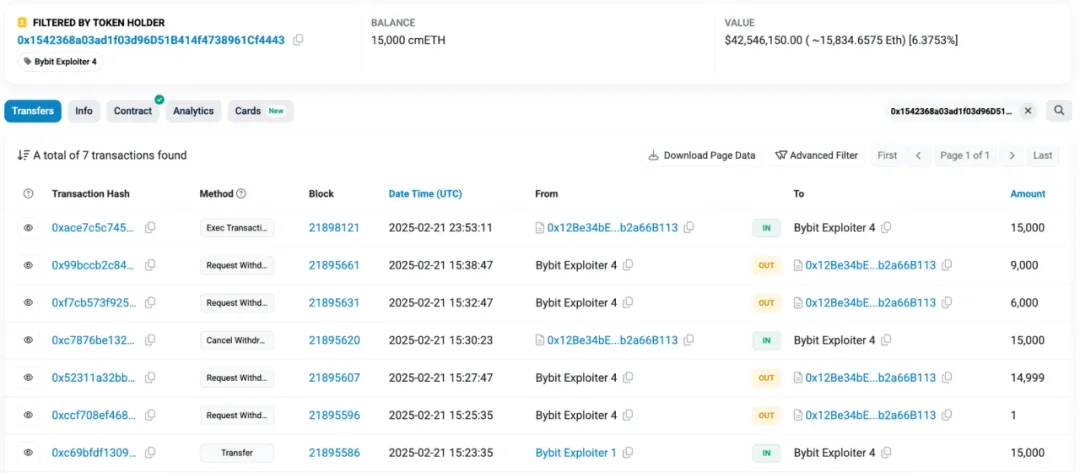
cmETH flow: 15,000 cmETH were transferred to the address:
0x1542368a03ad1f03d96D51B414f4738961Cf4443
Notably, mETH Protocol posted on X stating that in response to the Bybit security incident, the team promptly paused cmETH withdrawals, preventing unauthorized withdrawals. mETH Protocol successfully recovered 15,000 cmETH from the hacker address.
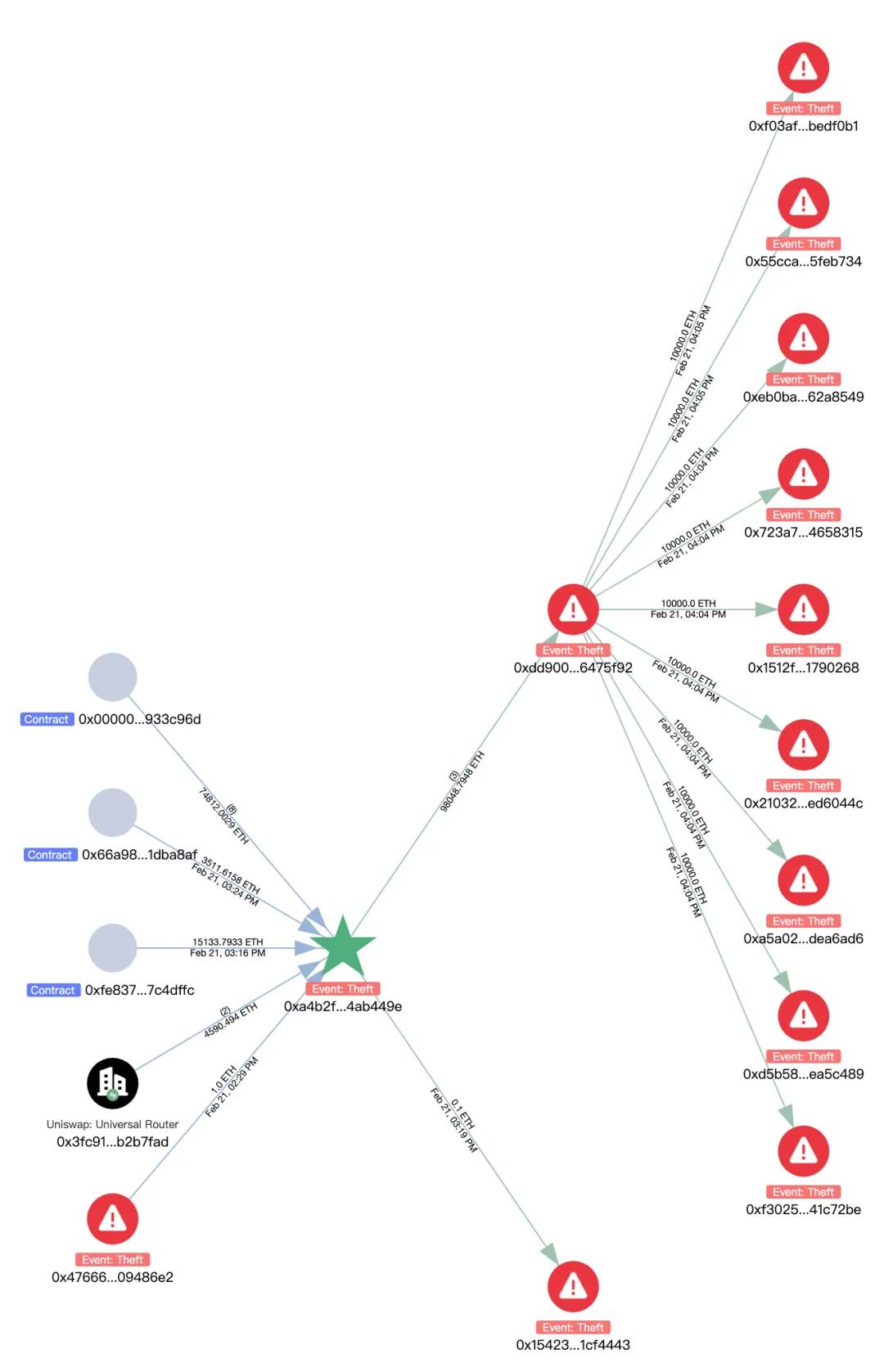
mETH and stETH transfers: 8,000 mETH and 90,375.5479 stETH were transferred to the address:
0xA4B2Fd68593B6F34E51cB9eDB66E71c1B4Ab449e
Then converted into 98,048 ETH via Uniswap and ParaSwap, and subsequently transferred to:
0xdd90071d52f20e85c89802e5dc1ec0a7b6475f92
The address 0xdd9 dispersed ETH in chunks of 1,000 ETH to 9 addresses and has not moved them further for now.
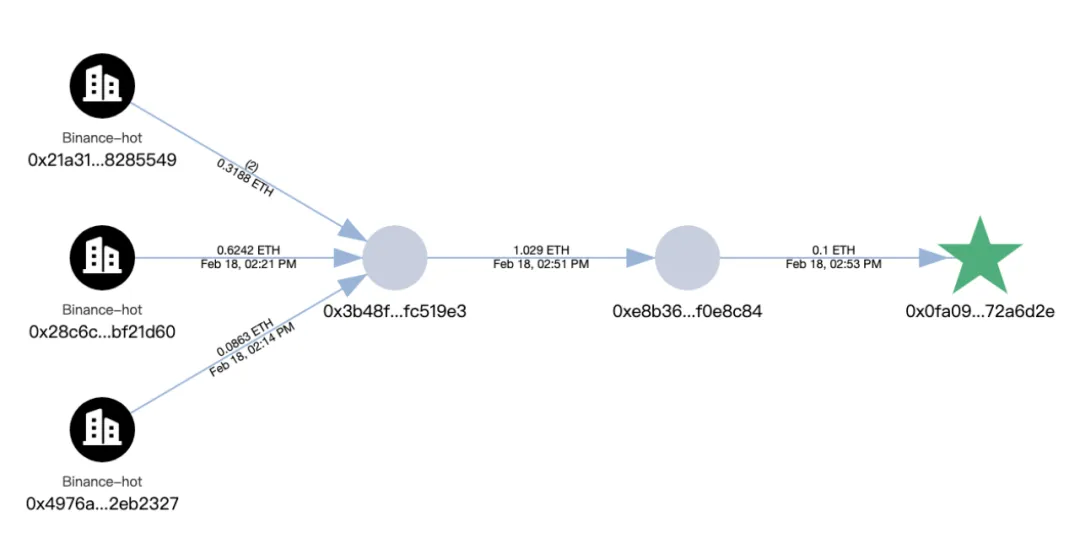
In addition, tracing the hacker’s initial attack address identified in the attack method analysis section:
0x0fa09C3A328792253f8dee7116848723b72a6d2e
revealed that the initial funds of this address came from Binance.
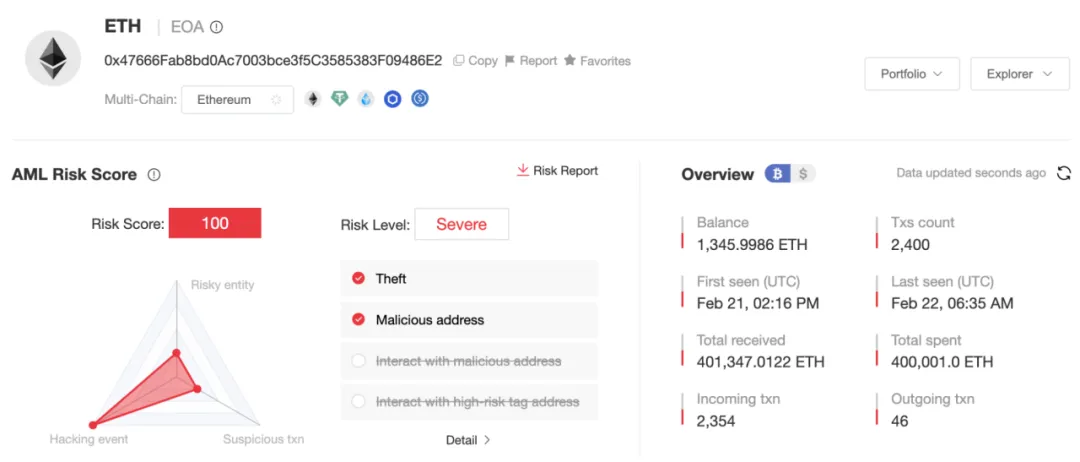
The current balance of the initial hacker address:
0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2
is 1,346 ETH, and we will continue monitoring the relevant addresses.
Immediately after the incident, SlowMist speculated based on the attacker’s method of obtaining the Safe multisig and money laundering techniques that the attacker was a North Korean hacker:
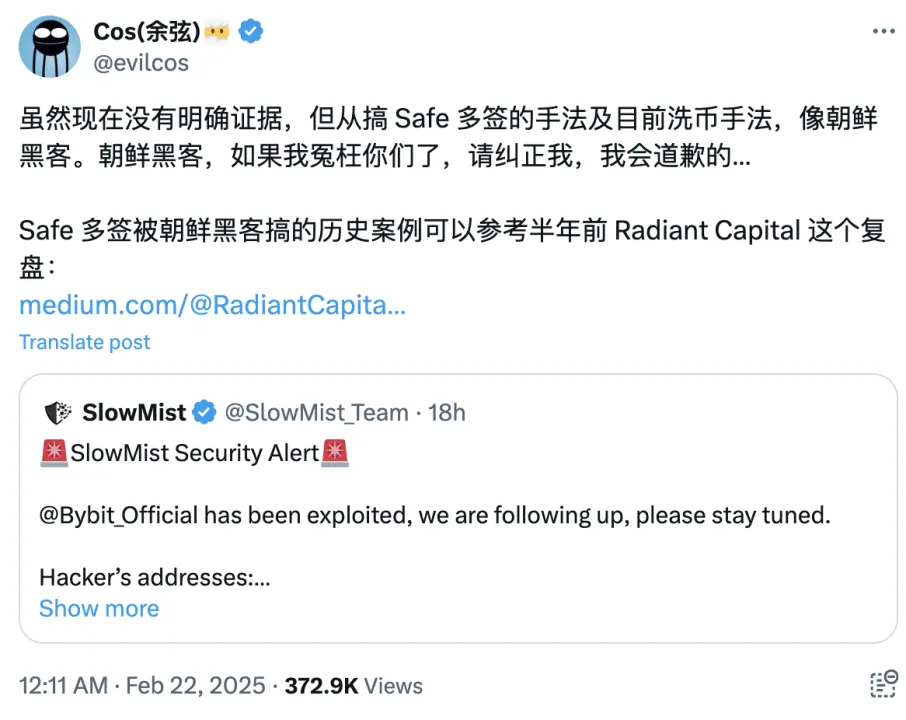
Possible social engineering attack methods:
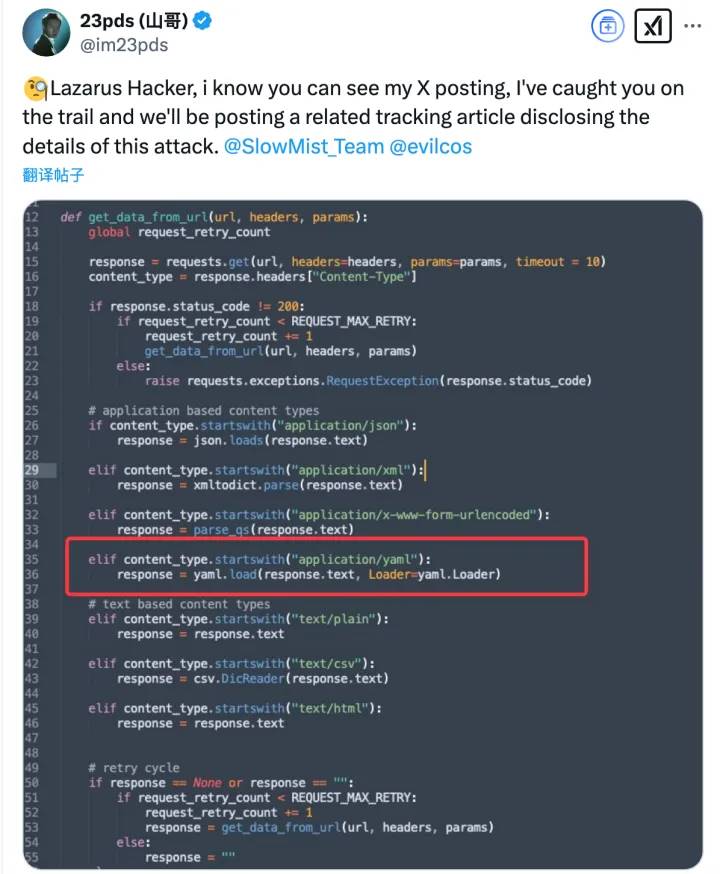
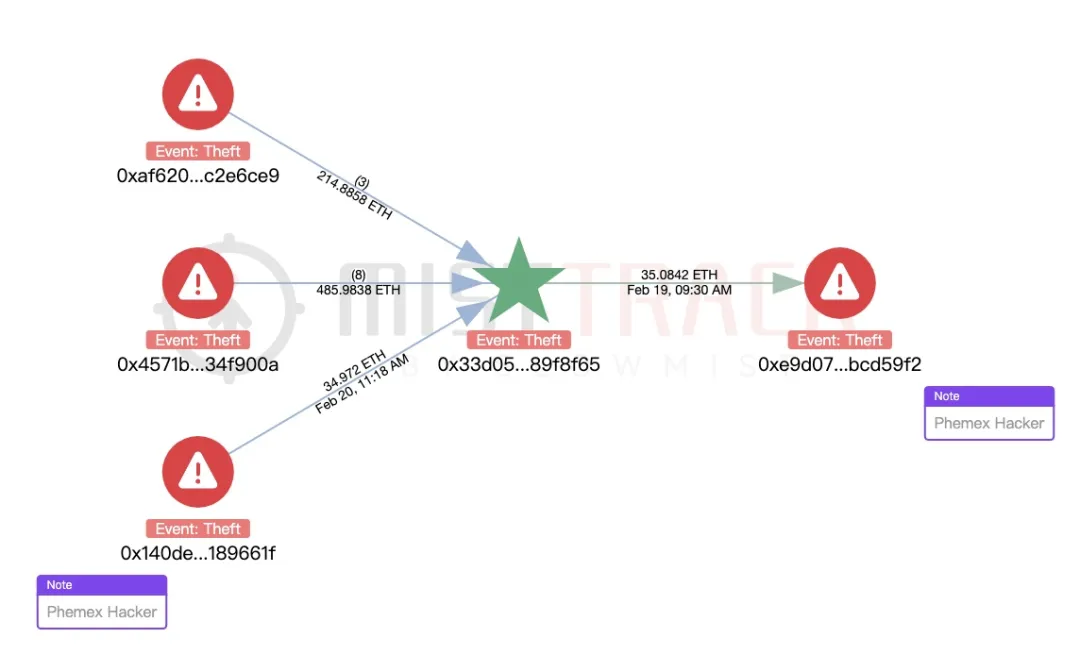
Using MistTrack analysis, links were also found between the hacker addresses in this incident and those associated with the BingX Hacker and Phemex Hacker:
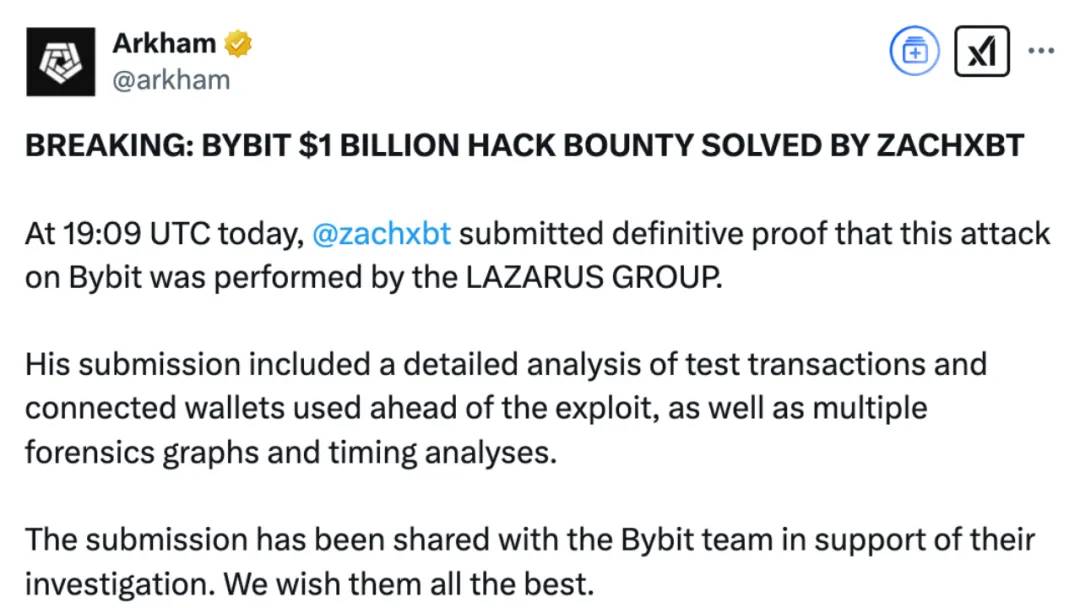
ZachXBT also confirmed the involvement of the North Korean hacking group Lazarus Group in this attack. The group has long engaged in transnational cyberattacks and cryptocurrency theft as one of its main activities. According to reports, evidence provided by ZachXBT—including test transactions, linked wallets, forensic charts, and timeline analysis—shows that the attackers repeatedly used technical methods typical of Lazarus Group. Meanwhile, Arkham stated that all related data has been shared with Bybit to assist the platform in further investigations.
Attack Method Analysis
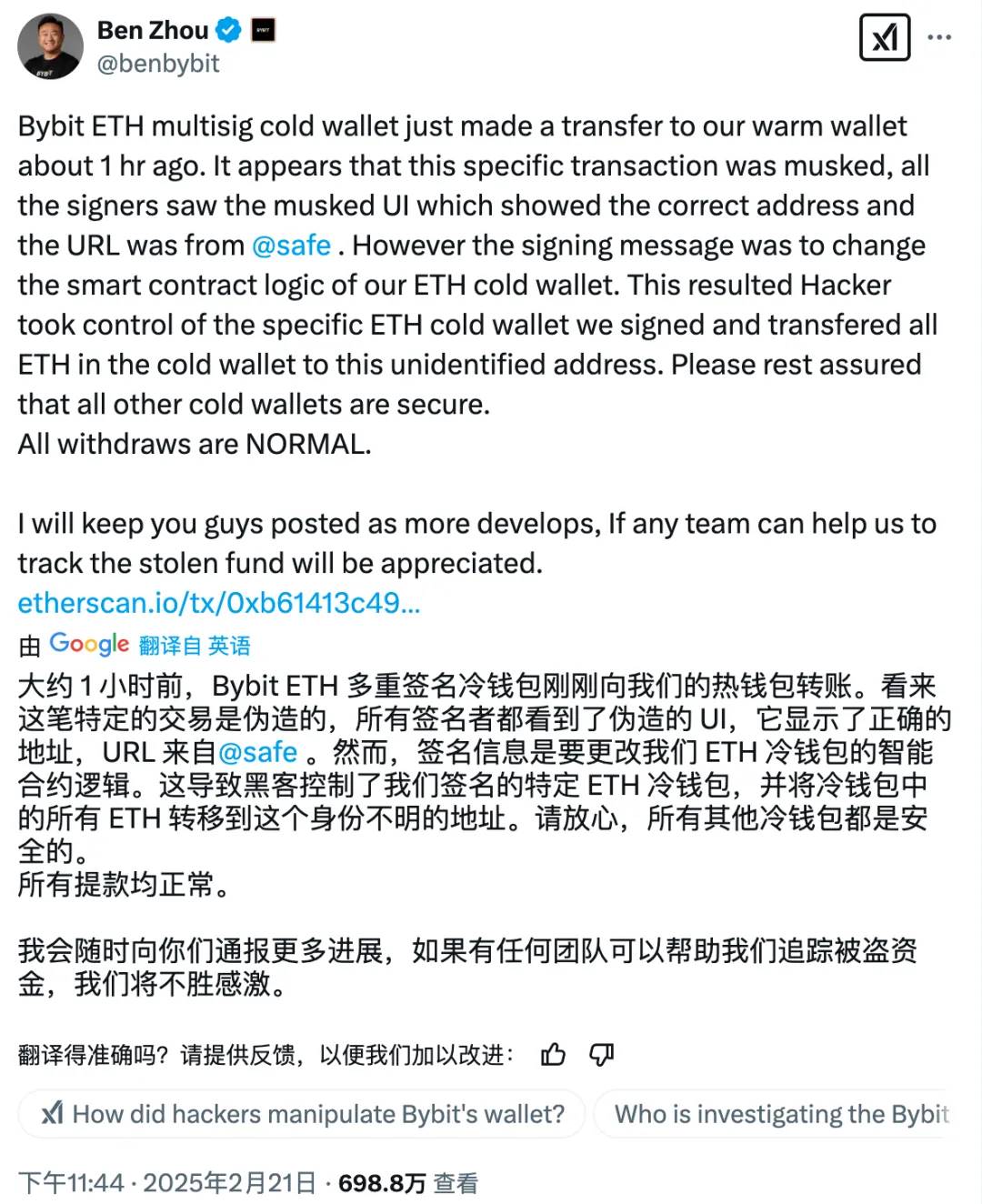
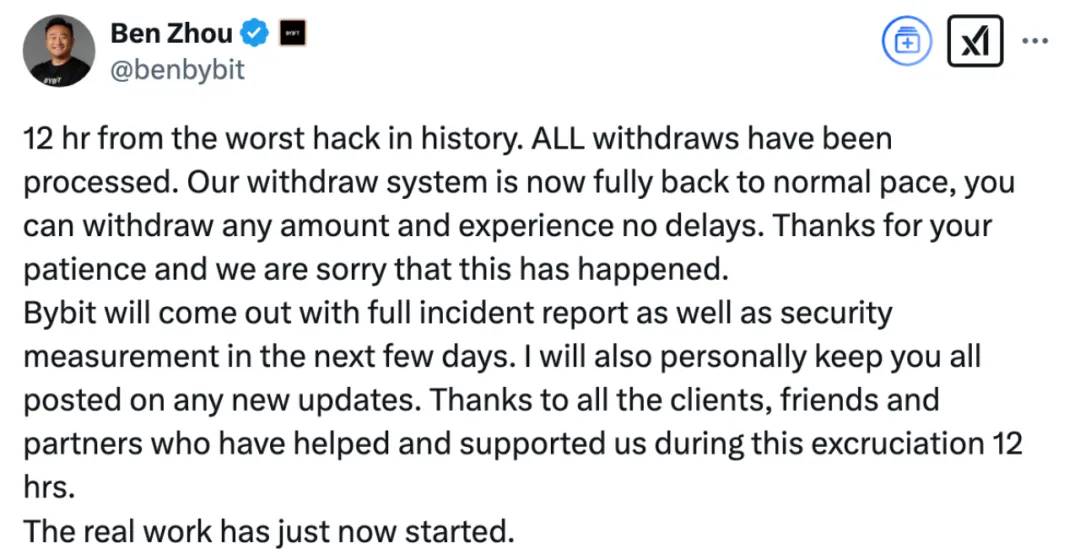
On the same night at 23:44, Bybit CEO Ben Zhou posted a statement on X explaining the technical details of the attack:
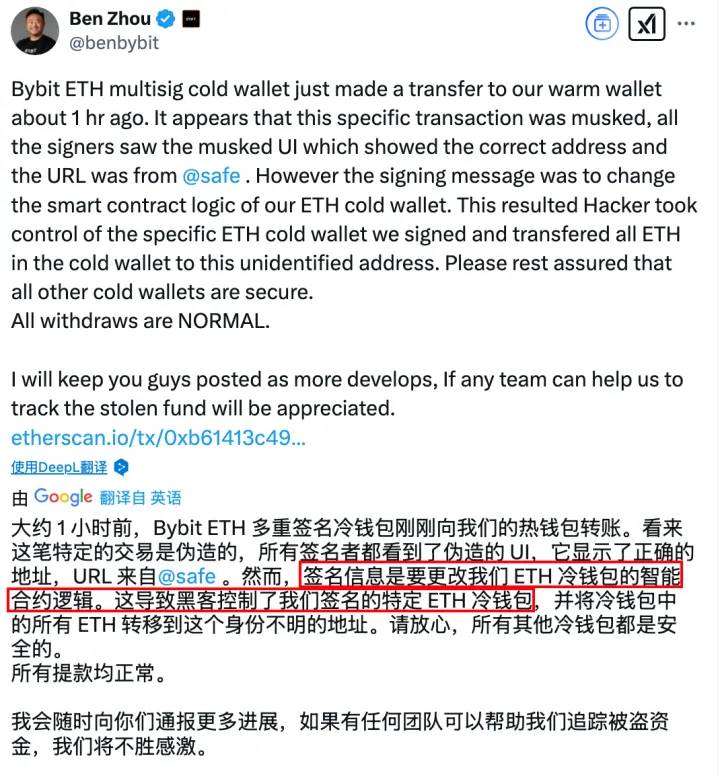
Through on-chain signature analysis, we discovered some traces:
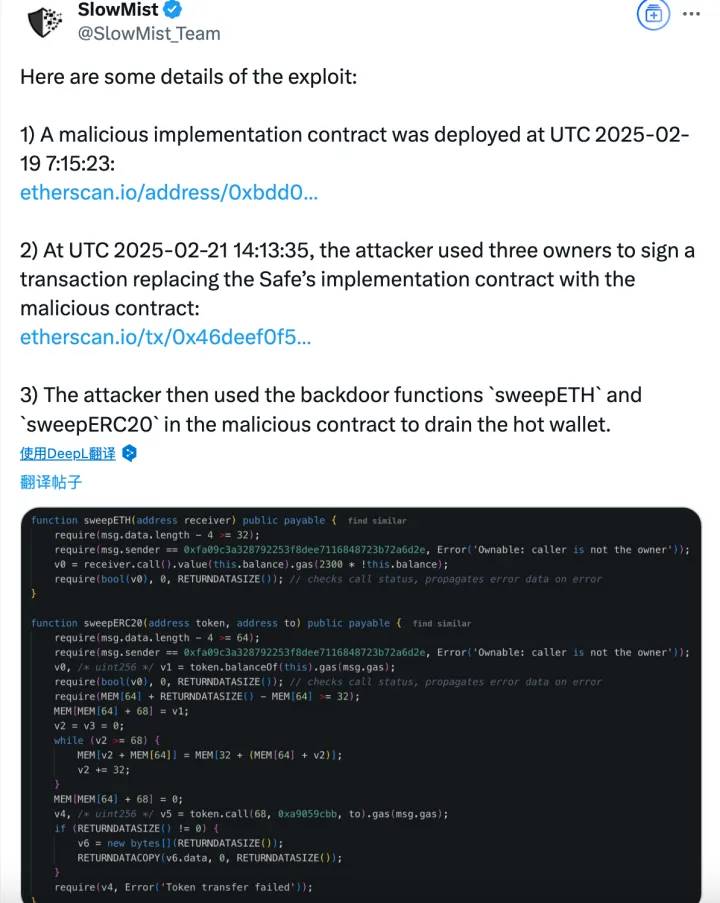
1. Attacker deployed a malicious contract: UTC 2025-02-19 07:15:23, deployed a malicious implementation contract:
0xbDd077f651EBe7f7b3cE16fe5F2b025BE2969516
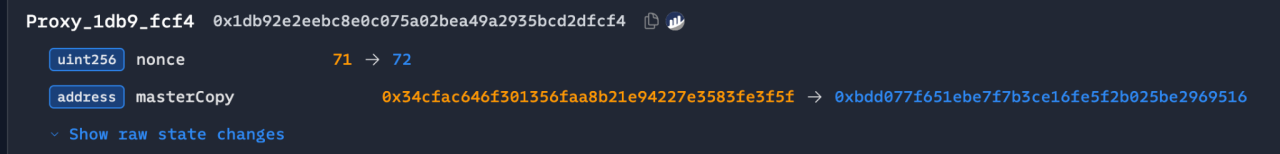
2. Tampered with Safe contract logic: UTC 2025-02-21 14:13:35, replaced the Safe contract with a malicious version through a transaction signed by three owners:
0x46deef0f52e3a983b67abf4714448a41dd7ffd6d32d32da69d62081c68ad7882
This leads to the identification of the initial attack address used by the hacker:
0x0fa09C3A328792253f8dee7116848723b72a6d2e.
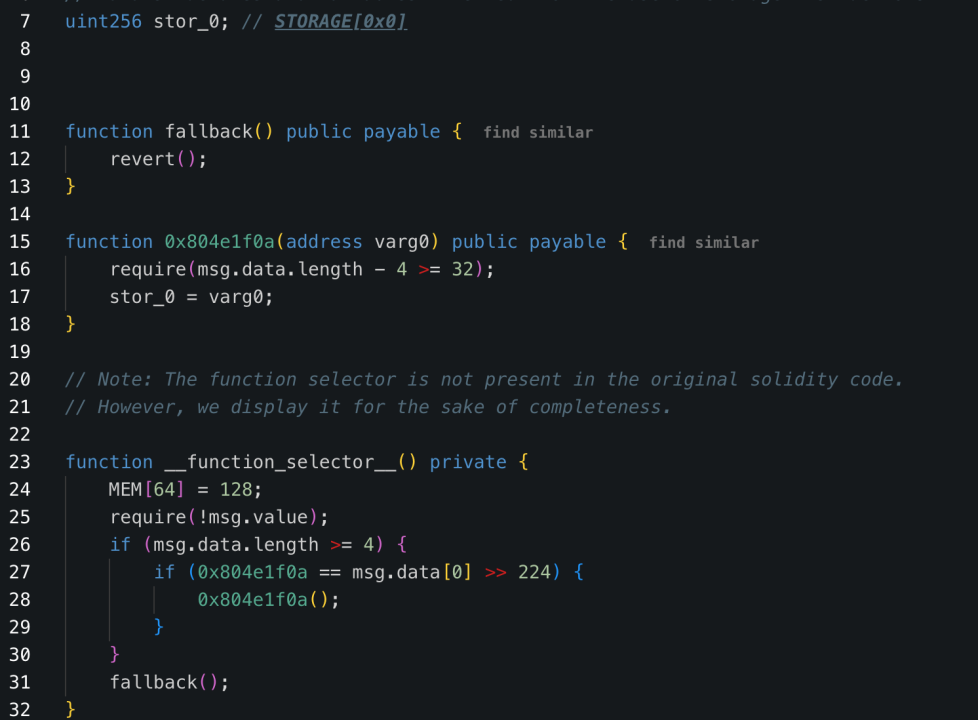
3. Embedded malicious logic: Used DELEGATECALL to write the malicious logic contract into STORAGE 0:
0x96221423681A6d52E184D440a8eFCEbB105C7242
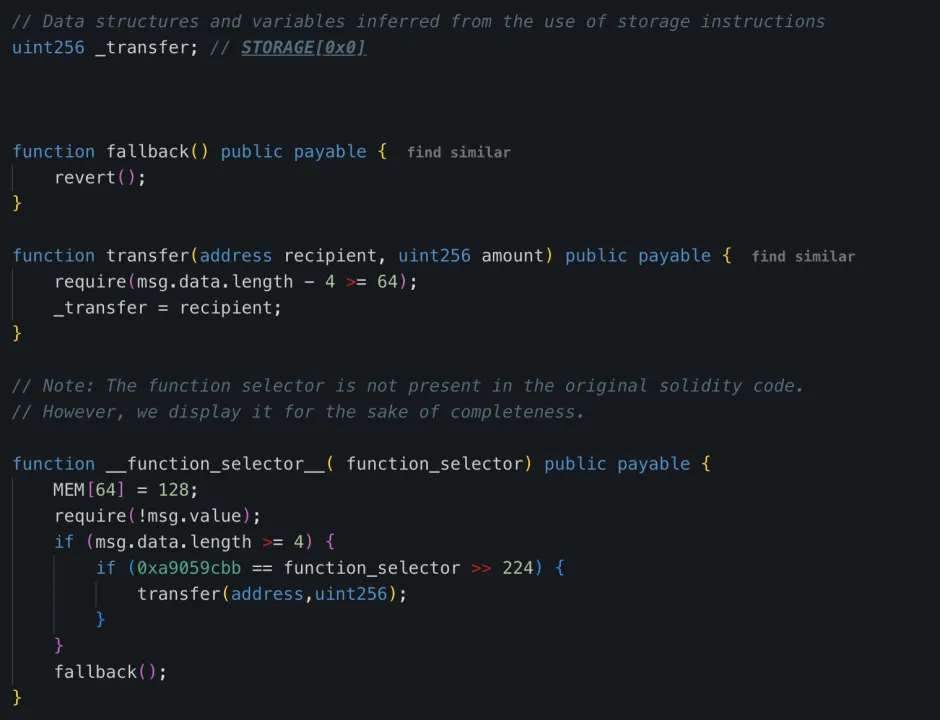
4. Called backdoor functions to transfer funds: The attacker used the sweepETH and sweepERC20 functions in the contract to transfer 400,000 ETH and stETH (totaling around $1.5 billion) from the cold wallet to unknown addresses.
In terms of attack methodology, the WazirX hack and Radiant Capital hack share similarities with this incident, as all three targeted Safe multisig wallets. In the WazirX hack, the attacker similarly pre-deployed a malicious implementation contract and, through transactions signed by three owners, used DELEGATECALL to write the malicious logic contract into STORAGE 0, replacing the Safe contract with the malicious implementation.
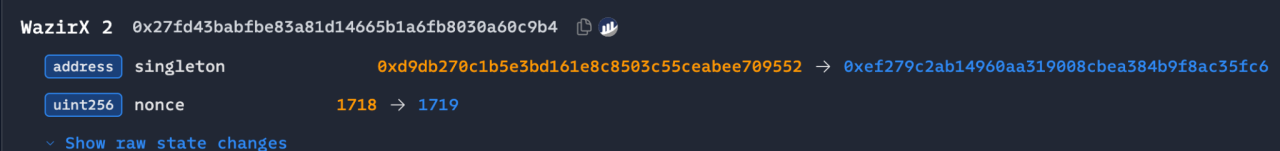
(https://etherscan.io/tx/0x48164d3adbab78c2cb9876f6e17f88e321097fcd14cadd57556866e4ef3e185d)
Regarding the Radiant Capital hack, official disclosures indicate the attacker used a sophisticated method to make signature verifiers see seemingly legitimate transactions on the frontend, which is similar to the information disclosed in Ben Zhou’s tweet.
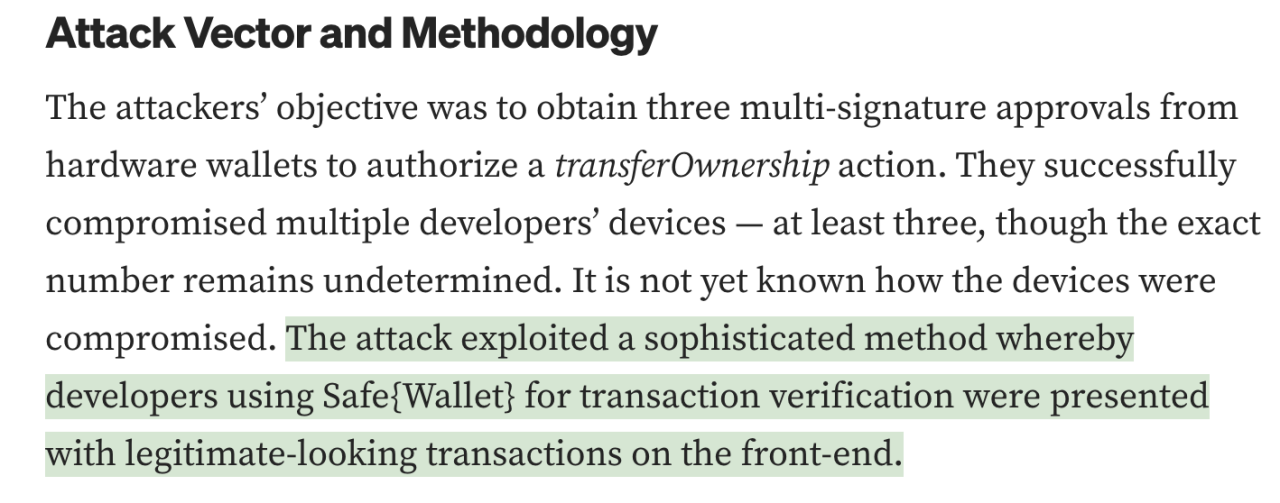
(https://medium.com/@RadiantCapital/radiant-post-mortem-fecd6cd38081)
Moreover, the permission-checking mechanisms in the malicious contracts involved in these three incidents are identical—each hardcodes an owner address within the contract to verify the caller. The error messages thrown during permission checks in the Bybit and WazirX hacks are also similar.
In this incident, the Safe contract itself was not flawed—the issue lay outside the contract, where the frontend was tampered with to deceive users. This is not an isolated case. North Korean hackers used this method last year to attack several platforms, including WazirX ($230M lost, Safe multisig), Radiant Capital ($50M lost, Safe multisig), and DMM Bitcoin ($305M lost, Gonco multisig). This attack method is highly engineered and mature, requiring heightened vigilance.
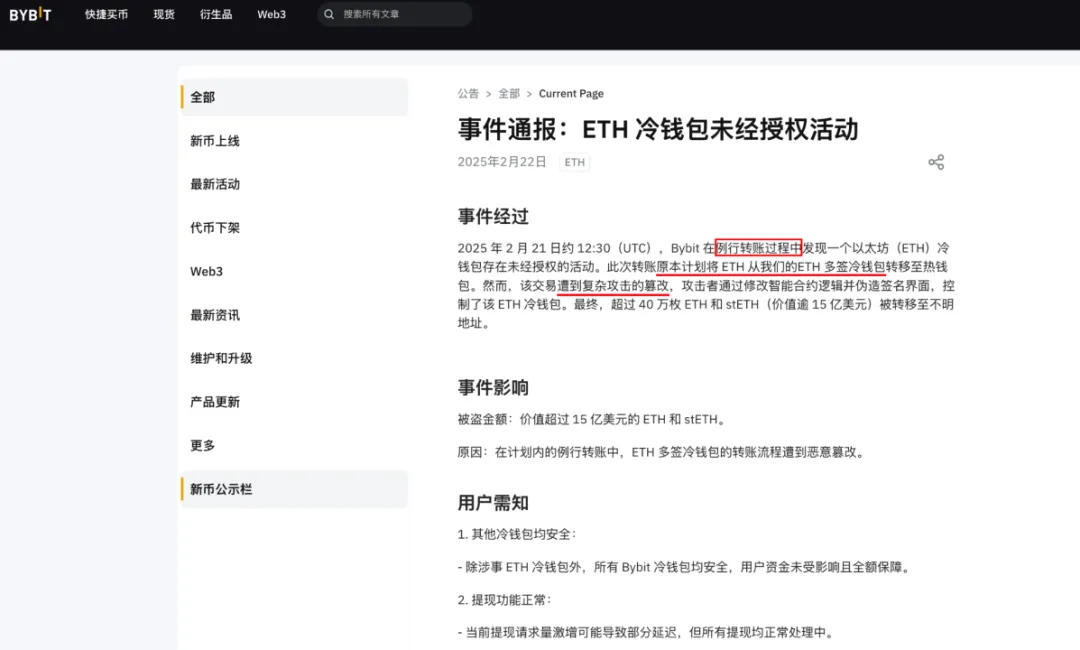
According to Bybit’s official announcement:
(https://announcements.bybit.com/zh-MY/article/incident-update---eth-cold-wallet-incident-blt292c0454d26e9140)
Combined with Ben Zhou’s tweets:
The following questions arise:
1. Routine ETH Transfer
Did the attacker gain prior access to internal financial operations at Bybit, learning the timing of ETH multisig cold wallet transfers?
Did they use the Safe system to trick signers into signing malicious transactions on a forged interface? Was the Safe frontend compromised and taken over?
2. Tampering with Safe Contract UI
Did signers see the correct addresses and URLs on the Safe interface while the actual transaction data being signed had already been altered?
The key question is: Who initiated the signature request first, and how secure was their device?
We await further official disclosure of investigation results to resolve these questions.
Market Impact
After the incident, Bybit quickly released an announcement, assuring that all customer assets are fully backed 1:1 and that the platform can absorb the losses. User withdrawals remain unaffected.
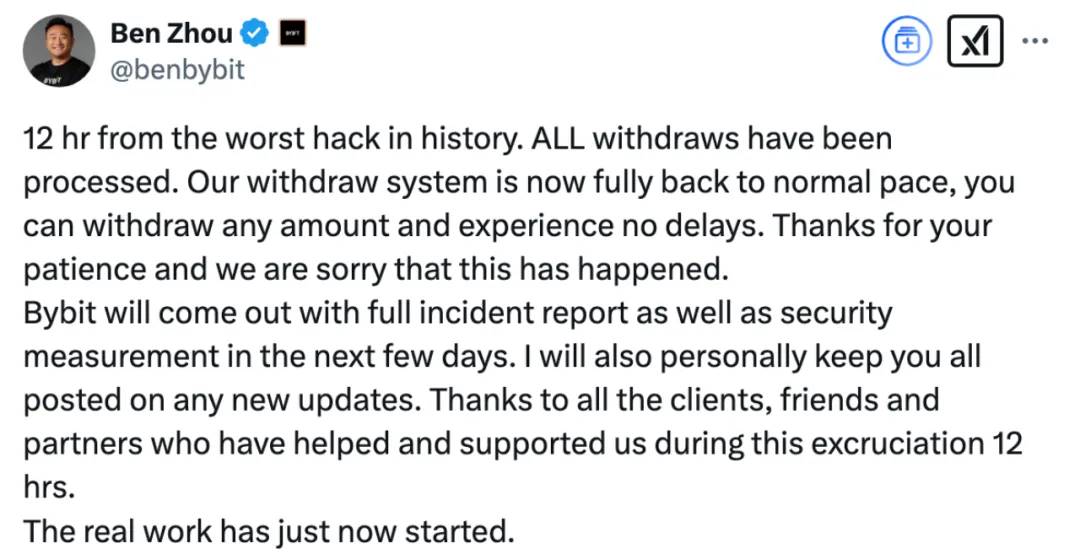
At 10:51 on February 22, 2025, Bybit CEO Ben Zhou posted on X stating that deposits and withdrawals have returned to normal:
Final Thoughts
This theft once again highlights the severe security challenges facing the cryptocurrency industry. As the crypto sector rapidly evolves, hacking groups—especially state-sponsored ones like Lazarus Group—are continuously upgrading their attack methods. This incident serves as a wake-up call for cryptocurrency exchanges, which must strengthen their security defenses and adopt more advanced protection mechanisms such as multi-factor authentication, encrypted wallet management, asset monitoring, and risk assessment to safeguard user funds. For individual users, enhancing security awareness is equally critical. It is recommended to prioritize safer storage options like hardware wallets and avoid keeping large amounts of funds on exchanges for extended periods. In this constantly evolving landscape, only through continuous technological upgrades can digital asset security be ensured, fostering healthy industry development.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News