Preliminary Security Assessment of Web3 Desktop Wallets
TechFlow Selected TechFlow Selected

Preliminary Security Assessment of Web3 Desktop Wallets
This report presents the details and findings of the technical analysis, aiming to enhance security awareness among all Web3 participants.
Author: CertiK
Desktop wallets play a critical role in the Web3.0 ecosystem, providing users with reliable solutions for securely managing digital assets within decentralized networks. According to a report by Cointelegraph [1], analysts from the Bitfinex exchange observed that as of December 1, 2023, the global number of cryptocurrency holders had significantly increased—from 432 million at the beginning of the year to 575 million. Desktop wallets hold a substantial share in this expanding market.
As the Web3.0 industry rapidly evolves, the importance of desktop wallets in safeguarding user assets has become increasingly evident. However, after conducting an in-depth technical analysis of multiple desktop wallets, the CertiK security team identified several potential security vulnerabilities that could expose users to higher risks during usage. This report presents the detailed findings and conclusions of this technical analysis, aiming to raise security awareness among all members of the Web3.0 community. We hope this report will remind users to remain highly vigilant when using desktop wallets and take proactive steps to protect their digital assets.
Security Risks from the Supply Chain
Desktop wallets are essential tools for Web3.0 users to manage and protect their digital assets. However, under the threat of supply chain attacks [2], their security is often overlooked. A supply chain attack occurs when cybercriminals target third-party vendors, service providers, or other links in the supply chain upon which an organization depends. To prevent such security incidents, it is recommended that users verify the hash value of installation packages—even those downloaded directly from official websites—because only packages verified through this method can be considered secure software. However, not all users possess the technical capability to perform such verification. When using certain desktop wallets, this lack of security awareness may increase users' vulnerability to attacks.
In particular, some desktop wallets may unintentionally incorporate modules or algorithms similar to backdoored software, leading antivirus programs to generate false positives. While official websites often provide reasonable explanations for these alerts, users who lack the ability to verify hashes may uncritically accept them, treating antivirus warnings as normal occurrences. This misplaced trust creates a potential opening for malware to disguise itself as legitimate wallet installers, thereby exposing users to greater risk.
As shown in the figure below, 65 antivirus engines on VirusTotal analyzed a common desktop wallet download file, and 19 of them flagged the sample as malicious.
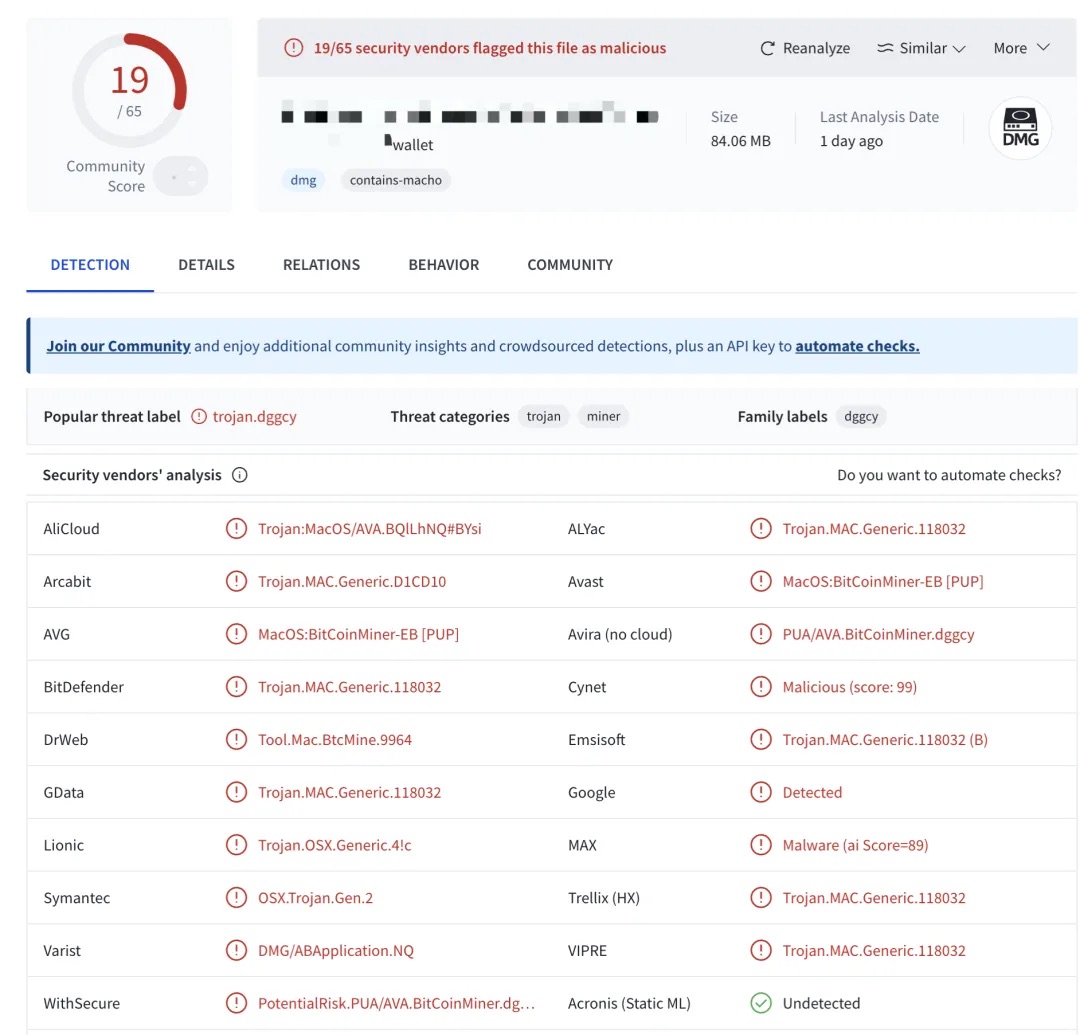
This analysis demonstrates that supply chain attacks are not merely theoretical threats. For users lacking technical means to verify software authenticity, there is a real risk of inadvertently downloading and installing malicious software. Even installers downloaded from official websites may trigger antivirus alerts, making it difficult for users to assess their safety and creating latent security hazards.
Security Risks in Local File Storage
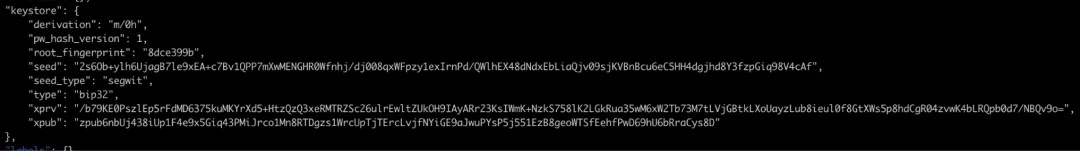
During our in-depth investigation, we found that certain desktop wallets allow users to store private keys in plaintext for specific operational purposes. This practice greatly increases the security risk to users’ digital assets, as plaintext private keys would be directly exposed to attackers if the user’s computer becomes infected with viruses or malware, jeopardizing the safety of their digital holdings.
Unencrypted local file:
Encrypted local file:
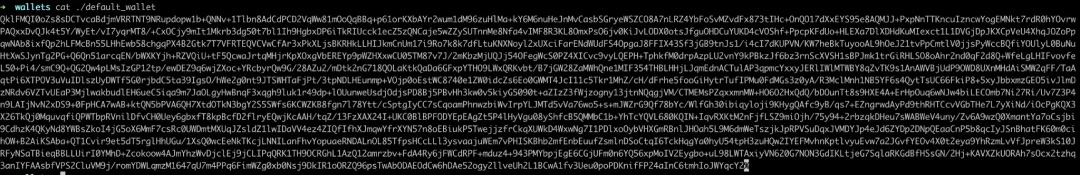
Even when users encrypt local files with a PIN code, the security of the key cannot be fully guaranteed against sophisticated malware. Whether running as standalone desktop applications or browser extension plugins, these wallets may become targets for malicious software. Yet users often place undue trust in desktop wallets due to their convenience and functionality, overlooking underlying security flaws. Compared to mobile apps, which benefit from strict permission controls and data isolation, desktop wallets appear relatively weak in protecting users’ private keys. Therefore, users must remain constantly aware of their operating environment’s security to avoid theft caused by improper storage or insecure configurations.
Security of PIN Code Encryption Algorithms
Another high-risk issue is that many desktop wallets employ flawed file encryption methods, making it easier for attackers to access and decrypt users’ encrypted data. Specifically, these wallets do not bind file encryption to hardware-specific information of the device. This means that even if a file is encrypted, attackers can transfer it to another device and perform offline decryption, effectively bypassing inherent device-level security protections.
Further analysis revealed weaknesses in the anti-brute-force mechanisms used by some wallets when implementing PIN codes. Many wallets use cryptographic algorithms with far fewer hash iterations than industry standards. For example, OWASP [3] recommends 600,000 iterations for password protection; Apple sets 10,000,000 iterations for its backup keychain; 1Password and LastPass use 650,000 and 600,000 iterations respectively. In contrast, some desktop wallets set their hash iteration count as low as 5,000—significantly below these established security benchmarks. Under such conditions, attackers can easily crack users’ PIN codes using brute-force techniques, even complex passwords being vulnerable to compromise.
In addition, our audit found that some wallet software lacks sufficient defenses against advanced attacks. Malicious actors typically first steal users’ encrypted data and then leverage powerful computing resources to decrypt it in offline environments. Due to vulnerabilities in encryption algorithm choices made by certain desktop wallets, their encrypted data becomes more susceptible to cracking. This not only puts users’ digital assets at risk but also poses new challenges to the overall security of the Web3.0 ecosystem.
Relatively Secure Desktop Wallet Solutions
When using desktop wallets, we recommend opting for MPC (Multi-Party Computation) wallets or hardware wallets, as desktop systems (PCs) inherently suffer from various security vulnerabilities compared to mobile devices. Although desktop wallets offer simplicity and easy access, their constant internet connectivity exposes them to more severe threats from hackers and malware. Therefore, for users requiring higher security, choosing alternative wallet types is a prudent decision.
MPC wallets offer significant advantages in enhancing digital asset security and recovery capabilities. By leveraging Secure Multi-Party Computation technology, these wallets split private keys into multiple shards distributed across different participants or nodes. This design eliminates single points of failure, ensuring no single entity holds the complete private key. Thus, even if a user’s desktop system is compromised, attackers cannot steal assets using any individual key shard. Only when multiple parties combine their respective shards can a valid transaction signature be generated. As long as not all key shards are stolen simultaneously, users’ assets remain secure.
Beyond this, the distributed key management system of MPC wallets offers greater operational flexibility and lower transaction costs. It supports hidden signatures and off-chain accountability mechanisms, further strengthening privacy and security. In this way, MPC wallets ensure digital asset safety remains intact even if parts of the system are breached.
Another advantage of MPC wallets is their recovery functionality. If a user loses or damages their device, they can still recover their keys via third-party services. This process requires users to reconstruct the private key using pre-distributed key shards stored in separate locations. Additionally, some MPC wallets offer social recovery features, allowing emergency contacts to help regain wallet access under extreme circumstances.
Hardware wallets for desktops provide a physically isolated solution by storing private keys within dedicated hardware devices. All signing operations occur offline inside the hardware, meaning that even if the desktop system is compromised, attackers cannot access the stored private keys. This physical isolation greatly enhances asset security, as private keys never get exposed to the internet, reducing the risk of hacking and theft.
Today, most hardware wallets also include recovery functions to prevent asset loss due to device damage or loss. The recovery process usually involves creating backup seed phrases or key shards, which users can securely store in different locations. If the hardware device is lost or damaged, users can use these backups to regain access to their wallets and retrieve their assets.
Moreover, some hardware wallets integrate biometric authentication to enhance security. This means that even if unauthorized individuals obtain key shards, they cannot access the wallet without passing biometric verification. Biometric technologies may include fingerprint scanning, facial recognition, or voice recognition, adding an extra layer of protection for hardware wallets.
For instance, Zengo's MPC system enhances wallet security by distributing multiple private key shards across different devices. Recovery functionality within the MPC system is crucial, enabling users to regain access to their wallets in case of device loss or damage. To ensure asset security, private key shards are tightly bound to the account, meaning assets are only at risk of loss if both the shards and the account are lost simultaneously.
In addition, some hardware wallet manufacturers (such as Ledger) offer identity-based key recovery services. For example, Ledger’s "Ledger Recover [4]" service splits the wallet recovery phrase into three encrypted fragments distributed among three custodians. If a user loses their seed phrase, after identity verification, two fragments can be combined to regain access to locked funds. This service aims to provide additional safeguards against the risk of losing digital asset keys, though it raises concerns among some users due to the online storage of seed phrases linked to government-issued identification.
Multiparty Computation (MPC) in Secure Desktop Wallets
When comparing the security of MPC wallets and hardware wallets, each has subtle strengths and weaknesses.
Due to inherent limitations of hardware wallets—such as limited CPU performance, restricted network connectivity, and rudimentary user interfaces—it can be challenging to display detailed transaction information clearly. This makes it difficult for users to fully verify transaction details when deeper inspection is needed. In such cases, MPC wallets emerge as a comparatively better option. MPC wallets enable multiple parties to jointly compute and verify transaction data without exposing sensitive information, offering a more robust framework for confirming transaction intent and integrity. Unlike hardware wallets, MPC-based solutions [5] can leverage the computational power and network environment of mobile devices or other platforms, allowing tighter integration with backend systems and reducing risks associated with transaction validation.
Overall, desktop hardware wallets provide users with a secure and reliable method of asset protection through physical isolation and recovery functions. The integration of biometric technology further strengthens this protection, ensuring users’ assets remain safeguarded even under extreme conditions.
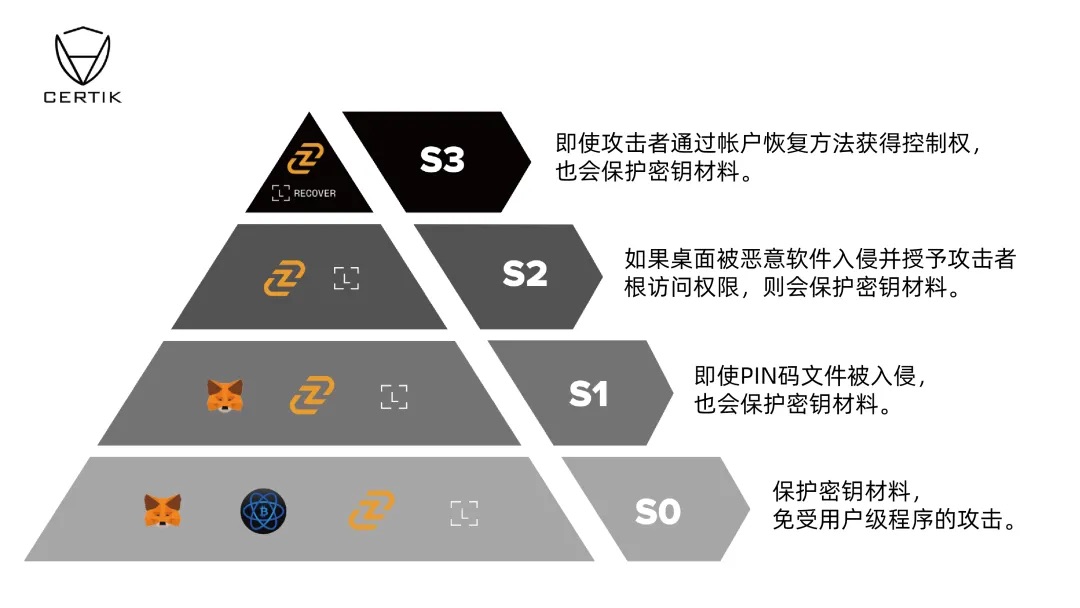
Comparison of Desktop Wallet Solutions
Based on the above risk and security analysis, we conducted a comparative evaluation of multiple desktop wallets. The following chart summarizes the security mechanisms of these wallets and their protective measures against identified risks. (S0 represents basic risk levels, with higher grades indicating increasingly complex risks.)
Conclusion
As vital tools for managing digital assets, desktop wallets face multiple security challenges: antivirus false positives, lack of sandbox protection, and inadequate encryption algorithms—all of which could lead to asset theft. These risks are especially dangerous for non-technical users, who may struggle to identify or respond appropriately. Therefore, wallet developers must strengthen security measures to ensure software integrity.
At the same time, users should enhance their risk awareness and adopt best practices for storing and managing digital assets. Through rigorous auditing and continuous improvement of desktop wallets, we can better protect users’ digital assets and promote the healthy development of the entire Web3.0 ecosystem.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News