
In-Depth Analysis of ZKML Applications and Prospects in Web3
TechFlow Selected TechFlow Selected

In-Depth Analysis of ZKML Applications and Prospects in Web3
This article will delve into the development and challenges of ZKML technology through the two cases of Worldcoin and Vanna, promoting its widespread application and prosperity in the blockchain field.

With the rapid advancement of blockchain technology, data privacy and security have become central issues. Zero-knowledge machine learning (ZKML), an emerging technology that effectively combines the security of zero-knowledge proofs (ZKP) with the intelligence of machine learning (ML), is bringing unprecedented opportunities to the Web3 world.
Currently, ZKML applications in the blockchain field are extensive, primarily including the following aspects:
-
Hardware acceleration: Due to the computational complexity of ZK proofs, projects such as Cysic and Ulvetanna utilize hardware acceleration to improve on-chain computation efficiency.
-
On-chain data processing: Projects like Axiom and Herodotus focus on converting on-chain data into formats suitable for ML training, ensuring ML output results can be easily accessed from the chain.
-
Computation circuitization: To enable ML computations to be processed by blockchain-based ZK systems, projects such as Modulus Labs and Jason Morton transform ML computation patterns into circuit forms.
-
ZK proof of results: To address trust issues in ML models, projects like RISC Zero and Axiom use ZK-SNARKs-based proofs to verify model authenticity.
ZKML is currently developing rapidly and can support the construction of decentralized identity (DID) in Web3. Previously, identity management methods such as private keys and mnemonic phrases led to poor user experience in Web3. True DID construction could leverage ZKML to enable biometric identification for Web3 entities, while ZKML ensures the privacy and security of users' biometric information. Worldcoin is applying ZKML to implement zero-knowledge DID verification based on iris scanning.
This article will explore the development and challenges of ZKML technology through two case studies—Worldcoin and Vanna—and promote its broader application and prosperity within the blockchain domain.
1. Worldcoin Case Study: Application of ZKML in Identity Verification and Privacy Protection
-
DApp Integration with Worldcoin
Worldcoin ID can be used for identity authentication. Worldcoin provides an IDKit SDK to authenticate using the World App, with the specific process as follows:
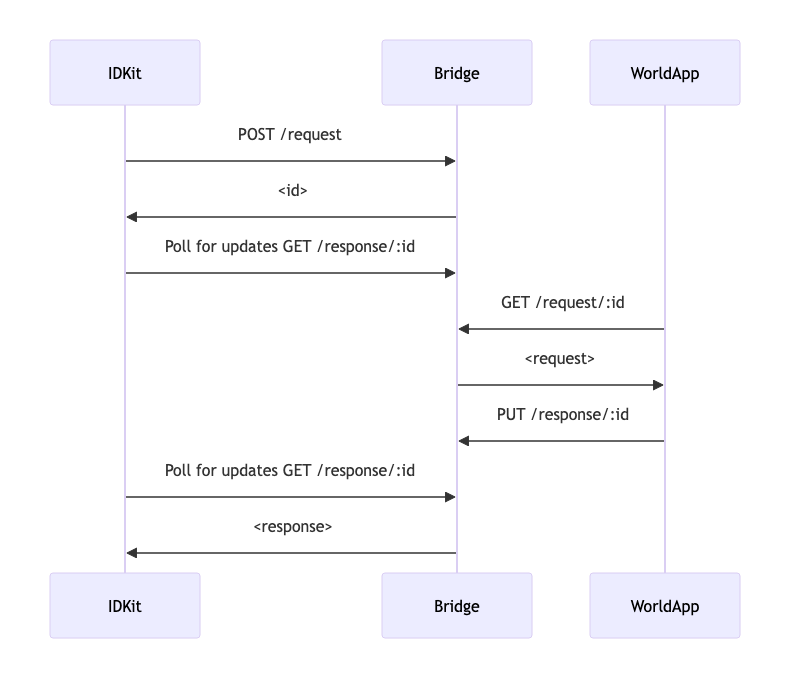
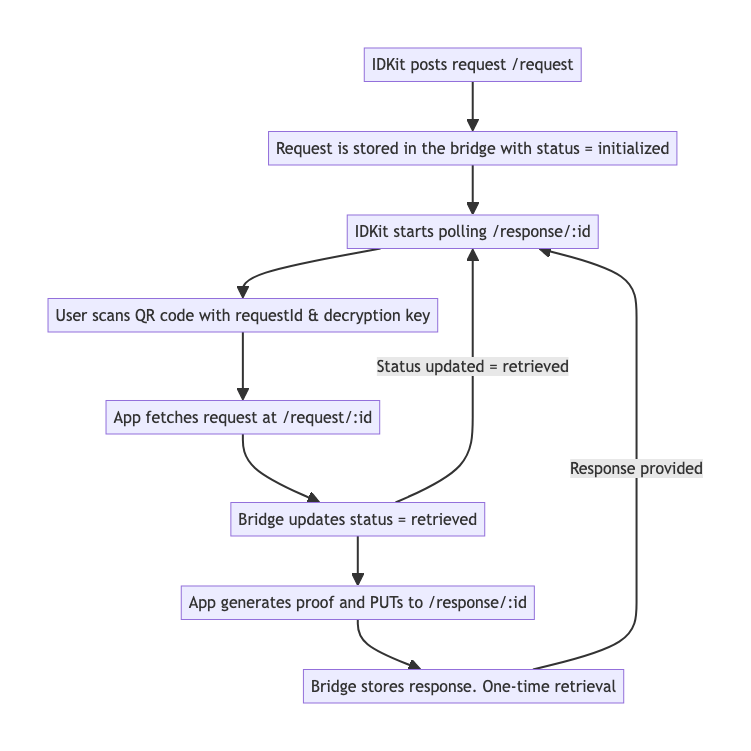
After this process, the user's biometric information serves as a login credential, ultimately generating a proof for identity verification within the Worldcoin App.
Application of ZKML in Worldcoin
-
Application of ML in Worldcoin
By running the IrisCode model locally on self-hosted biometric data (user devices), it verifies whether the user has created a valid and unique WorldID locally, and calls the _addMember(uint256 groupId, uint256 identityCommitment) function on the WorldID Semaphore identity group with a valid identity commitment, making the protocol publicly permissionless.
-
Application of ZK in Worldcoin
Registration Process
During Worldcoin’s registration process, users generate a WorldID via iris scanning and call the _addMember function on the Semaphore identity group with a valid identity commitment, enabling public permissionless access to the protocol.
Signup Sequencer: The registration sequencer orders batches of data (identities) submitted to Ethereum smart contracts.
Semaphore MTB: SMTB is a service for batch-processing Merkle tree updates. It accepts individual Merkle tree updates and merges them into a single update, which is useful for reducing the number of transactions submitted to the blockchain. SNARKs are generated to ensure correctness of the batch Merkle tree updates.
Tx Sitter: Signs transactions and sends them to the blockchain.
Proof inputs include the external nullifier (a public 32-byte value that scopes the uniqueness of verifications) and the secret identity nullifier. These two values compute the nullifier hash, used for user identity identification.
Login Process
During login, the user-submitted identity nullifier is converted into a proof—a process similar to zk-rollups. After submitting the identity nullifier, multiple Merkle state updates are aggregated and published onto the blockchain.
Summary
Worldcoin’s technical implementation involves multiple layers, including local execution of the IrisCode model, generation of external nullifiers, batch processing via Semaphore MTB, and transaction handling by Tx Sitter. Since the IrisCode model runs locally on the user device—converting iris scans into a World ID—this step is not executed by external nodes, thereby protecting user privacy. The integration of these technologies enables Worldcoin to achieve efficient and secure identity verification while preserving user privacy.
The Worldcoin case demonstrates the potential and effectiveness of ZKML technology in practical applications. By combining zero-knowledge proofs and machine learning, Worldcoin enhances both the security of identity verification and the strength of user privacy protection.
This case provides valuable reference and inspiration for other blockchain projects.
2. Vanna Network and ZKML: Intelligent Inference and Validation in Blockchain
Overview of the Vanna Network
The Vanna network is an innovative blockchain platform focused on providing efficient zero-knowledge proof generation and validation services. It combines the transparency and immutability of blockchains with the privacy-preserving properties of zero-knowledge proofs, offering users a secure and reliable data processing environment.
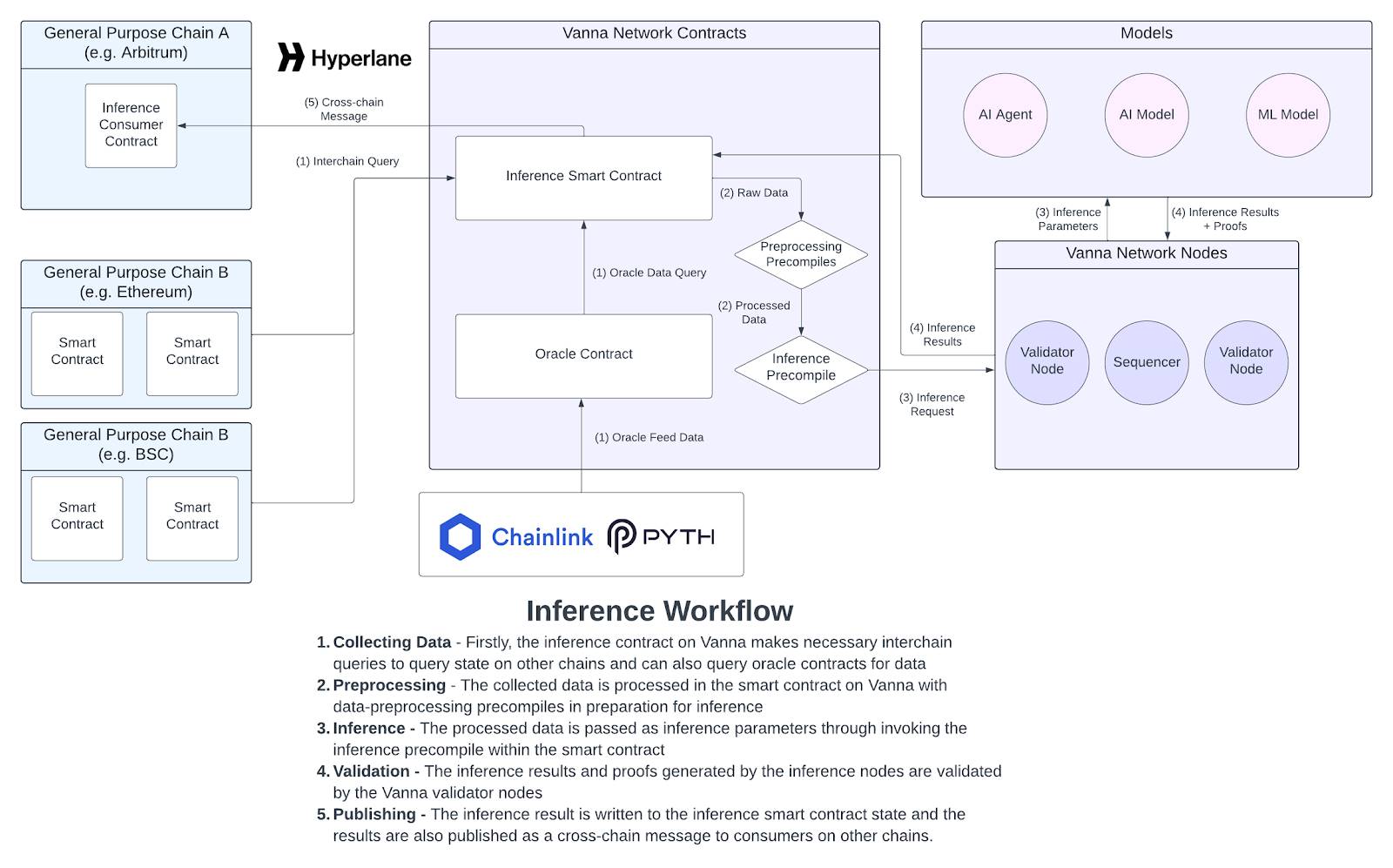
Vanna Network Features
-
Querying Data: Access Oracle feed data or on-chain states by performing cross-chain queries on smart contracts.
-
Preprocessing: Use Vanna’s built-in precompilers to preprocess raw queried data in preparation for inference.
-
Inference Execution: Seamlessly and scalably run inference at any cryptographic security level suitable for your use case.
-
Inference Verification: All cryptographic proofs ensuring inference validity are verified by validator nodes on the Vanna network.
-
Publishing and Provenance: Inference results can be relayed via cross-chain messaging to contracts on any chain and published to a data availability layer.
Characteristics of the Vanna Network
-
Parallel Inference Pre-execution
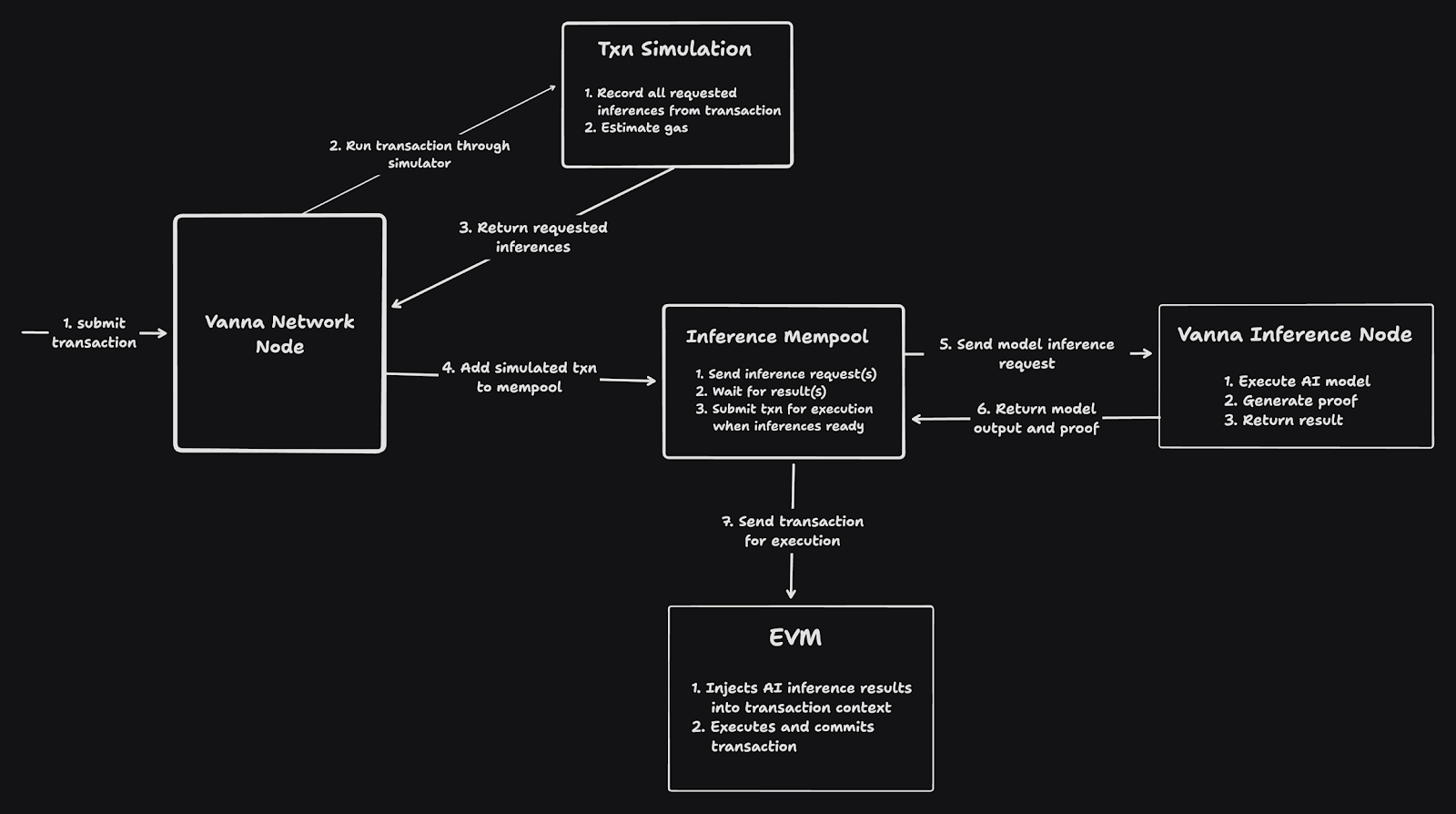
Divided into three stages:
Stage One: Simulation
Vanna runs each transaction through a simulator to determine which inference requests the transaction will issue. No actual execution occurs at this stage.
Stage Two: Inference Mempool
Transactions and their inference requests are added to an inference mempool, which forwards the requests to Vanna inference nodes. Inference and proof generation occur here.
Stage Three: EVM Execution
Inference results are injected into the EVM so that transactions can directly read them, just like any other variable. Then the transaction is executed and committed to the blockchain.
-
Separation of Validation and Computation
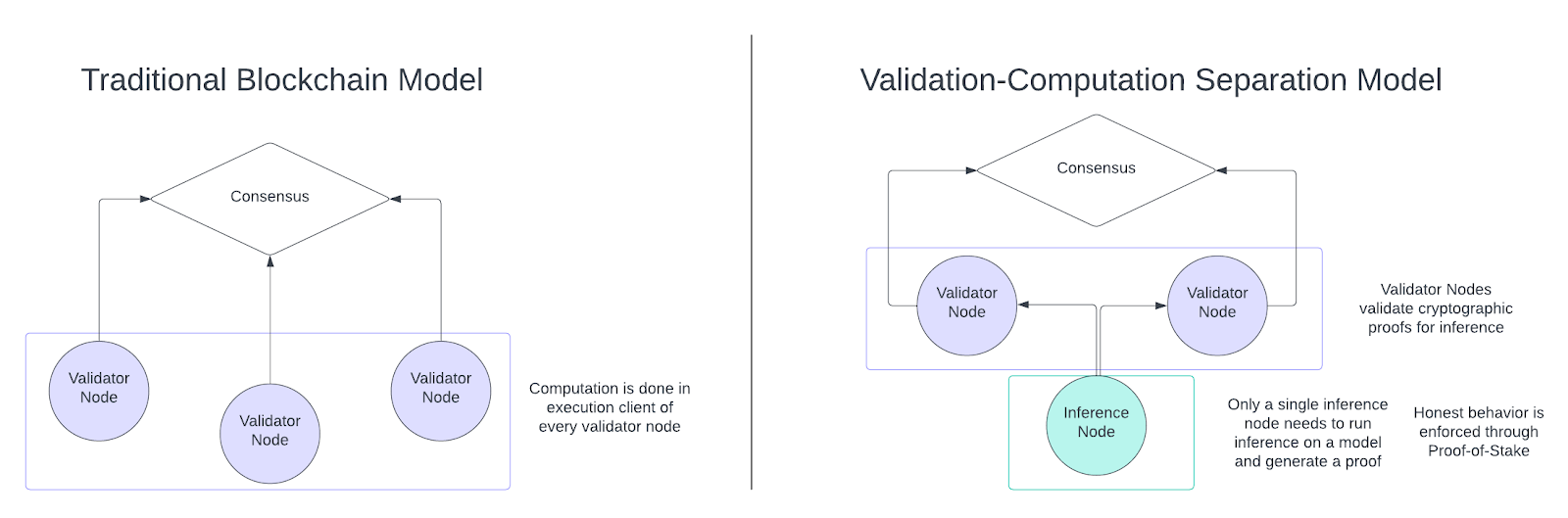
The Vanna Network employs two types of nodes—validation nodes and inference nodes—and separates network validation and inference computation across these node types.
Validation Nodes: Rollup nodes independently validate transactions and verify the state of the Vanna network. Rollup nodes on the Vanna network also participate in verifying cryptographic proofs generated by inference nodes.
Inference Nodes: Inference nodes do not validate transactions or blocks on the network; they solely focus on performing AI/ML inference and generating cryptographic proofs for those inferences.
-
Staking and Penalties
The Vanna network provides cryptoeconomic security through an application-layer staking contract. When inference nodes come online to help secure the network, they must deposit Vanna tokens as collateral in the staking contract. The staking contract enforces inference node behavior, with slashing conditions including but not limited to:
-
zkML – Generating invalid proofs that cannot be cryptographically verified
-
opML – Successful challenges against inferences generated by the node
-
zkFP – Successful challenges against the node’s inferences, or failure to generate a ZK-SNARK proving the inference
Summary
Through its unique design and features, the Vanna network demonstrates the application potential of ZKML in blockchain, particularly through parallel inference pre-execution, separation of validation and computation, and its staking and penalty mechanisms.
3. EZKL: The Developer's Sword for ZKML – Simplifying Zero-Knowledge Proof Generation and Verification
Overview of EZKL
EZKL takes high-level descriptions of programs and sets up zero-knowledge provers and verifiers. It focuses on PyTorch AI/ML models and other program representations in computational graphs. Once set up, the prover can prove statements such as:
-
“I ran this public neural network on some private data, and it produced this output.”
-
“I ran my private neural network on some public data and produced this output.”
-
“I correctly executed this public neural network on some public data, and it produced this output.”
EZKL Workflow
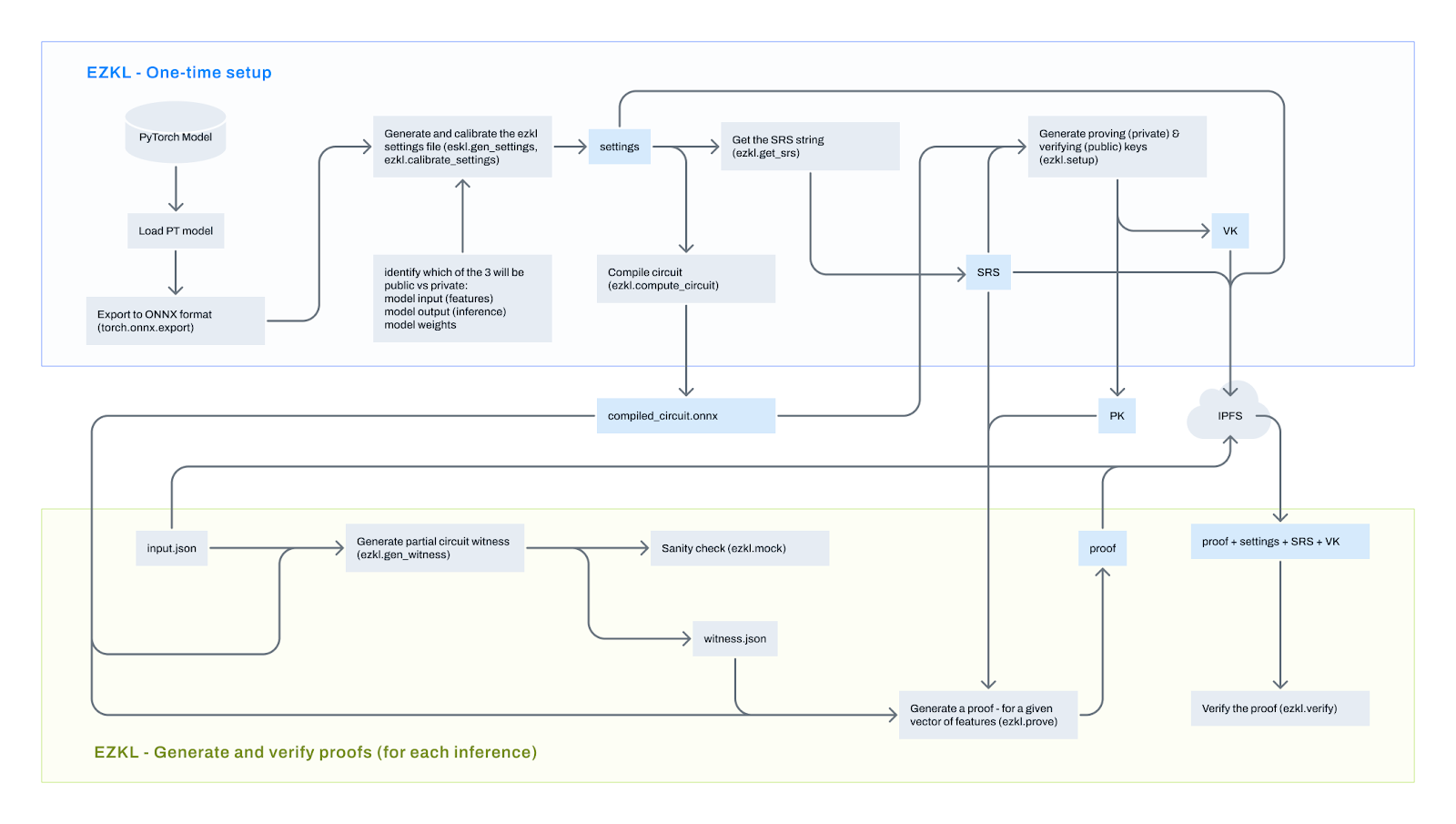
The EZKL workflow is illustrated below:
-
Define Neural Network Model: Define a simple neural network
-
Model Training: Generate input data and obtain output through the model
-
Model Export: Export the model in ONNX format
-
Generate Zero-Knowledge Proof Setup: Generate setup files
-
Compile Circuit: Compile the model to generate circuit files
-
Generate Zero-Knowledge Proof: Generate SRS, witness files, proving key, and verification key
-
Verify Zero-Knowledge Proof: Generate the zero-knowledge proof and verify it locally, or create Solidity code and ABI files for an EVM verifier, deploy the contract, and verify the proof on-chain
4. Challenges and Outlook for ZKML
As blockchain technology continues to evolve, zero-knowledge machine learning (ZKML) is gradually becoming a key force in enhancing application privacy and security. It not only heralds the emergence of innovative applications such as privacy-preserving smart contracts and enhanced security in decentralized finance (DeFi), but is also expected to become an indispensable component of blockchain technology, providing a solid technical foundation for building a more secure and privacy-focused digital world.
Challenges
Despite its great potential, ZKML faces several challenges during implementation:
-
Technical Complexity: Implementing ZKML requires deep mathematical and cryptographic knowledge, increasing development and maintenance difficulty and demanding higher expertise from developers.
-
Performance Bottlenecks: The generation and verification of zero-knowledge proofs are computationally intensive, potentially affecting system response time and processing capacity. To address this, some projects like Lumoz offer a modular compute layer to enhance performance.
-
User Adoption: Despite strong privacy protection capabilities, users may remain hesitant due to unfamiliarity with ZKML’s complexity and security assurances.
-
Regulatory Challenges: The development of privacy-enhancing technologies requires regulators to update relevant laws to adapt to changes and challenges brought by new technologies.
Outlook
Despite existing challenges, the deep integration of ZKML and the future of blockchain remain promising:
-
Technological Advancement: As research deepens and technology matures, ZKML implementations will become more efficient and user-friendly.
-
User Education: Through education and outreach, understanding of ZKML’s complexity and security can be improved, increasing user adoption.
-
Regulatory Adaptation: Regulatory innovation and adaptation will provide legal and policy support for the development of ZKML technology.
-
Application Innovation: Ongoing advancements in ZKML will inspire more innovative applications, driving broader adoption of blockchain technology across diverse fields.
5. Conclusion
The development of ZKML technology marks a significant step forward in the blockchain domain, signaling the arrival of a new era of data privacy and security. Facing challenges such as technical complexity, performance bottlenecks, and regulatory hurdles, we should remain optimistic. With technological progress and growing user acceptance, ZKML will play an increasingly important role in the blockchain space, driving broader applications and innovations.
References
-
Intro to zero-knowledge proofs, Semaphore and their application in World ID
-
In-Depth Analysis of ZKML: Technical Principles, Applications, Advantages, and Challenges
-
Using Iris Scanning for Proof of Personhood: Is Worldcoin on the Right Path?
-
a16z Crypto Investor: Zero-Knowledge (ZK) Technology is Severely Undervalued
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















