Diving into Dark Pools: Privacy Research on Transparent Blockchains
TechFlow Selected TechFlow Selected

Diving into Dark Pools: Privacy Research on Transparent Blockchains
By introducing privacy-enhancing technologies such as zero-knowledge proofs, dark pools aim to provide high security while protecting transaction privacy.
Author: Muhammad Yusuf, Delphi Digital
Translated by: Wu Shuo Blockchain
Editor's note: This article provides a detailed overview of various types of dark pools, covering their operational mechanisms, privacy architectures, order matching, liquidity sources, MEV resistance, censorship resistance, and more. By incorporating privacy-enhancing technologies such as zero-knowledge proofs, dark pools aim to protect transaction privacy while maintaining high security. Additionally, the article touches on regulatory compliance, trade visibility, and explores different business models within dark pools.
Before diving into the inner workings of blockchain-based dark pools, let’s first understand their origins—how they emerged, why they persist, and how transformative they have been.
Dark Pools in the 1960s
In 1969, when computers still occupied one or two entire rooms and traders shouted orders on trading floors, institutional investors needed a better way to buy and sell stocks without triggering market reactions. Jerome Pustilnik founded Instinet, pioneering electronic trading on Wall Street. Institutional investors could place orders, and Instinet would match and execute them. For platforms like Instinet to function effectively, a large volume of both buy and sell orders was required. What attracted institutions? Confidentiality. Instinet allowed large firms to operate anonymously, hiding their identities and order details from other participants and the broader market. This prevented their trades from influencing prices and reduced the risk of front-running by other traders.
As of 2022, over 60 dark pools were registered with the SEC. Some are operated by exchanges such as the New York Stock Exchange (NYSE) and NASDAQ; others by broker-dealers like Morgan Stanley’s MS Pool and Goldman Sachs’ SigmaX; and some independently, such as Liquidnet and MatchNow.
The problem with operator-run dark pools is that operators may have greater incentives to act improperly rather than comply with regulations. The equation is simple: corrupt profits > cost of corruption. Operators can earn more through misconduct than they pay in fines. In 2018, the SEC fined Citigroup $12 million for misleading investors while operating a dark pool and leaking confidential order information to high-frequency traders, who then executed over $9 billion in trades against Citigroup’s clients and profited from it.
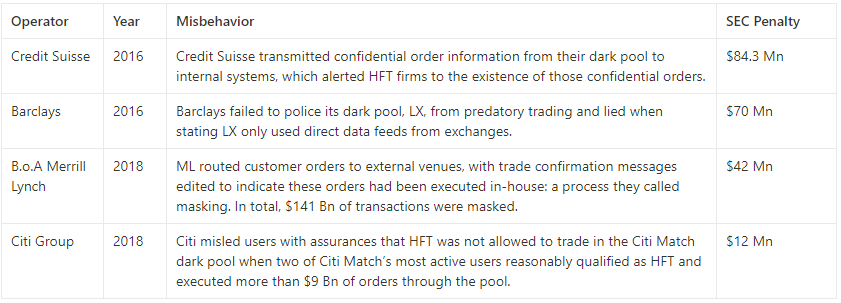
Users of traditional dark pools face risks of manipulation by operators. This is the heavy price they pay for participating in a broken trust system. Since 2011, dark pool operators have paid over $340 million in fines to settle allegations. Compared to the profits they might accumulate, this cost is relatively small. Blockchain-based dark pools aim to eliminate reliance on potentially malicious operators, but challenges remain.
Mixers, Pools, and Everything In Between
Blockchains were designed to be fully transparent. While transparency promotes accountability, it’s also a double-edged sword. If you receive your salary on-chain, anyone with your wallet address can see your past and future earnings.
DEXs and wallets are tracked by wallet-tracking platforms and copy-trading services, which even allow anonymous actors to front-run successful traders, complicating their strategies. Large orders also risk being frontrun by searchers in the public mempool.
Before delving deeper into dark pools, let’s distinguish mixers from dark pools. Mixers are a subset of dark pools. Tools like Tornado Cash mix tokens to break the link between wallets and assets, making fund trails difficult to trace. Dark pools go further—they not only sever wallet-asset links but also enable users to trade without revealing any information about counterparties.
Having explored the origins and motivations behind traditional dark pools and distinguished mixers from dark pools, let’s now examine blockchain-based dark pools that inject privacy into their architecture using account/balance models and Privacy Enhancing Technologies (PETs) such as zero-knowledge proofs, multi-party computation (MPC), and fully homomorphic encryption (FHE).

At the time of writing, dark pools like Portal Gate, Renegade, and Tristero are still under development. Meanwhile, privacy protocols such as Panther and Railgun are already operational, enabling private DeFi transactions—not just swaps, but also staking, providing liquidity, and lending.
Privacy Architecture
Balance Models
Blockchains are state machines. State consists of accounts and transactions. As accounts transact, each state transition appends a new set of updates to the chain, updating account balances accordingly. The account/balance model refers to how blockchains track and manage user balances. Blockchains like Ethereum, Solana, and Polygon use an account model, while Bitcoin, Zcash, and Monero use a UTXO (Unspent Transaction Output) model. These models differ in how they manage and represent blockchain state.
The account model, similar to bank accounts, displays current state as a set of addresses and their balances. When you make a payment, you send the exact amount—no leftover balance remains, and no new balance is created. The UTXO model, however, is more complex. When you pay, your entire balance is transferred, burning the existing UTXO. The remaining portion becomes a new UTXO. The UTXO model represents the current state as a graph of spent and unspent transaction outputs.
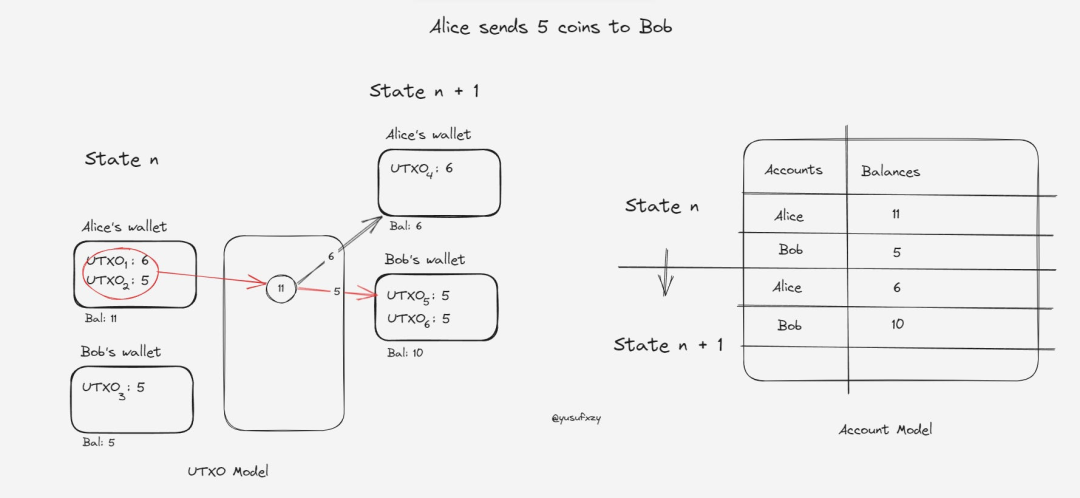
To illustrate, consider this scenario:
Alice has two UTXOs in her wallet—one with 6 coins and another with 5 coins. Bob has one UTXO with 5 coins. When Alice sends 5 coins to Bob, she combines both UTXOs into a single transaction, making it hard for observers to determine which UTXO funded the transfer or where the change went. This privacy-preserving mechanism obscures fund flows and protects participant anonymity.
The newly generated UTXO has no known owner and requires advanced on-chain analysis to link it to an individual. In contrast, the account model encourages address reuse, making it easier to track a user’s history. UTXOs also make double-spending extremely difficult. Each UTXO generates a unique “nullifier.” When a UTXO is spent, its nullifier is consumed, preventing reuse.
Variants of the UTXO model are used in privacy-focused L1s and L2s. Aleo uses the Record model, a UTXO variant. Aztec and Polygon Miden combine UTXO and account models. Zcash’s UTXO model heavily inspired those used in dark pools. Some protocols modify it to support multiple assets and accounts. Protocols like Portal Gate, Penumbra, Railgun, and Renegade use a “note”-based mechanism, where each UTXO is a note. These notes contain asset, order, and value information—but are visible only to owners. Notes are stored in a Merkle tree tracking chain state, called the State Commitment Tree. Notes can result from internal transfers, settlements, or relay fees. Renegade uses embedded MPC to match UTXOs (orders) and update private states. Multiple notes can also be bundled into a single note.
In Panther Protocol, each asset or account is represented as a zAsset (private asset) or zNFT (private non-fungible token). The UTXO model operates via a Merkle tree called the “Bus,” batching up to 64 UTXOs per batch to optimize user cost efficiency. The “Bus Operator” manages processing, incentivized by rewards denominated in $ZKP. For single UTXO execution, Panther uses a “Taxi” Merkle tree. To support cross-chain UTXOs, there’s a “Ferry” Merkle tree.
Proof Systems
This is a core component of Privacy Enhancing Technologies (PETs). Zero-knowledge proofs (ZKPs) allow proving possession of correct information without revealing the information itself. In the context of dark pools, ZKPs can prove that a user has sufficient funds and permissions to place an order, enabling matching and settlement—all while keeping these details hidden from operators, other traders, and third parties.
Proof systems are cryptographic constructions designed to generate these proofs. They come in various forms, producing proofs of different sizes, requiring different timeframes, and consuming varying computational resources during generation and verification. Here, we’ll explore two key proof systems—Groth16 and UltraPlonk—both applied in the dark pools discussed.
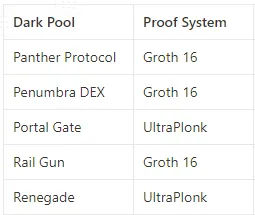
Panther, Penumbra, and Railgun use the Groth16 proof system. Groth16 is known for generating proofs of consistent size, making it preferable since proof size impacts transaction scale, gas costs, and throughput. Portal Gate and Renegade, on the other hand, use UltraPlonk.
Both Groth16 and UltraPlonk require a trusted setup—a process where a group of trusted parties collaboratively establish a common set of parameters. These parameters allow verifiers to validate proofs without trusting provers, and vice versa. Notably, a trusted setup implies trust assumptions about the involved parties. Secure multi-party computation (MPC) can prevent any single party from accessing the underlying setup structure. Groth16 relies on inputs from multiple parties for its trusted setup, whereas UltraPlonk requires only one party.
Inner Workings of Dark Pools
Now, let’s explore how dark pools operate internally—how they preserve privacy, provide liquidity, resist MEV extraction, withstand censorship, and handle compliance.
Wallet Setup
In most cases, users must create new dedicated wallets to interact with dark pools. Railgun partners with a third-party wallet provider called Railway Wallet, which allows creating an encrypted EOA to hold tokens/NFTs privately—without exposing amounts or types—and enables private calls to any public smart contract via the Relay Adapt mechanism.
In Renegade, a wallet is equivalent to a UTXO that holds private keys and signs transactions. You generate a new UTXO and submit a ZK proof proving it’s genuinely new and hasn’t been spent. Most actions—like deposits, order placement, and trades—invalidate the wallet, requiring creation of a new one to prevent double-spending. The user experience mirrors that of standard Ethereum wallets.
To use Penumbra, you create a new wallet as with other Cosmos chains, then fund it via IBC transfer.
For Panther and Portal Gate, KYC processes are established. Users can connect existing Ethereum wallets, but must verify their passport to gain credentials for protocol interaction. Business entities undergo KYB, sharing business details. Verification is conducted off-chain by registered compliance providers. Credentials expire periodically and must be renewed.
Order Discovery and Matching
Common DEXs like Uniswap and Curve use automated market makers (AMMs), matching orders against liquidity pools. This approach isn't ideal for privacy, as order details become publicly visible on-chain when matched against open pools—undesirable for large traders who don’t want to reveal their intent to the market. Some dark pools eventually match against liquidity pools or use external public contracts, employing relays as firewalls to separate traders from external liquidity sources while preserving privacy. Next, we’ll explore how dark pools source liquidity without compromising privacy.
Remember: traders have already deposited funds into dark pool wallets. Now, what happens when an order is submitted? Some dark pools use peer-to-peer order matching, others use pool-based methods, leveraging PETs like zero-knowledge proofs or multi-party computation, while their internal contracts interact with external public contracts. Peer-to-peer or cross-trader matching avoids slippage, unlike pool-based matching where pool prices may shift between order submission and execution. When traders' orders cross, execution occurs at their negotiated price.
In Renegade’s peer-to-peer model, when a trader submits an order, they select a relay to bid/match on their behalf and pay a fee. The trader generates a ZK proof called “VALID COMMITMENT,” proving ownership of their wallet and order. They then broadcast a “handshake” to match with another trader’s handshake. A handshake is an immutable list containing the VALID COMMITMENT ZK proof, hashed order details, nullifier, and key pair. When two handshakes match, they engage in multi-party computation. Renegade uses collaborative ZK-SNARKs to prove that the traders’ orders indeed match. This ensures order details remain hidden during matching. Once matched with all required proofs, a new wallet is created to hold exchanged tokens. It’s verified as genuinely new to prevent double-spending. The UX matches that of any Ethereum wallet.
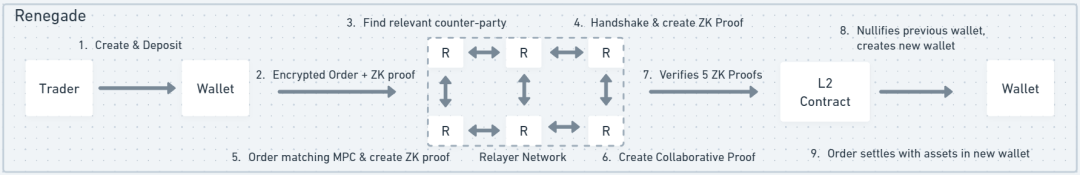
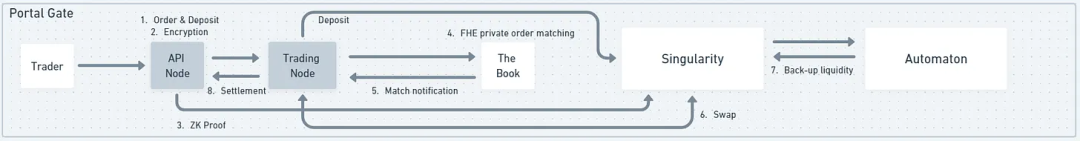
For Portal Gate, when a trader submits an order, an API node receives it, encrypts it, generates a ZK proof, and relays it to the Book. The Book is a set of off-chain nodes that collect orders and run matching algorithms in a Fully Homomorphic Encryption (FHE) environment—meaning encrypted orders can be matched without decryption. Upon successful match, only the aggregate result is revealed, not individual order details—preserving privacy.
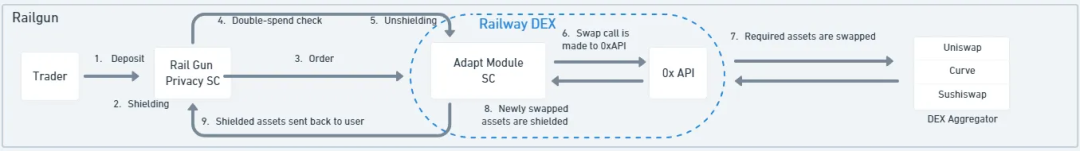
In Railgun, when a trader places a swap order, a smart contract called the “Adapt Module” performs several actions: it retrieves the private balance specified in the wallet and removes its privacy shield. The Adapt Module also verifies whether the order (UTXO) has already been invalidated/spent. Then, the 0x API aggregates liquidity across DEXs to find the best rate. After the swap, the Adapt Module re-shields the received assets into private balances, ensuring activity or addresses aren’t exposed. This workflow applies to other DeFi transaction types as well.
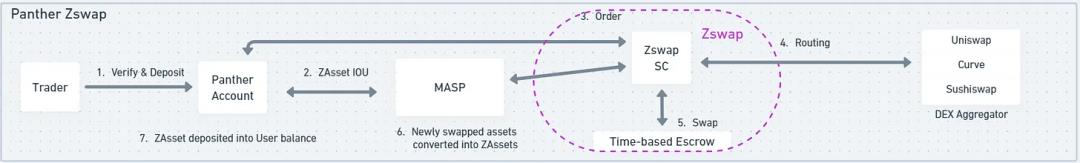
Panther Protocol works similarly, using a module called Zswap to connect Panther’s MASP (Multi-Asset Shielded Pool) with other DeFi protocols. Rather than a “pool,” MASP resembles a set of “append-only” Merkle trees, where each leaf is a commitment to a UTXO of assets deposited into MASP. When a trader creates an order, Zswap aggregates quotes from other DeFi protocols for selection. Once an order is placed, Zswap creates an encrypted time-based escrow contract to privately facilitate exchange between users without revealing details. After swapping, users receive IOUs of the tokens as ZAssets (or ZNFTs) from Panther’s MASP.
Penumbra’s swap module, also named Zswap, functions differently. When a trader creates an order, the private balance assets are burned, and the encrypted order value is sent to validators. A fee is required. The user receives a “swap” NFT to record the event. The NFT is composed of various parameters including traded assets, fees, input amount, and encryption keys. Validators aggregate multiple traders’ inputs into batches and execute them against centralized liquidity positions. Outputs are delivered proportionally to each trader. Individual data remains secret, but aggregated data is exposed when validators batch-execute against centralized liquidity.

Finding Liquidity
Dark pools like Renegade and Portal Gate operate by directly crossing buy and sell orders between users anonymously, but liquidity isn’t always sufficient. On regular DEXs, you’re almost guaranteed enough liquidity, but at the cost of privacy and price impact—anyone can see what you’re buying/selling, and guaranteed liquidity comes with a premium you must pay. In dark pools, order information stays hidden before and after trading.
Renegade follows this design, matching order flow directly with counter-flow without intermediaries. In low-liquidity scenarios, an “Indication of Interest” mechanism allows traders to disclose certain order details to relays matching orders. Details like price, size, asset, and order type can be proven efficiently via zero-knowledge proofs. If disclosed, other traders can view these pending orders, potentially leading to faster execution.
Panther Protocol is more than a dark pool—it enables a suite of privately executable DeFi activities. Users deposit funds into the Multi-Asset Shielded Pool, representing deposited assets as zkAssets (zkNFTs)—essentially IOU tokens, akin to stETH received when staking on Ethereum. Plugins called DeFi Adaptors privately connect MASP with existing DeFi protocols. Zswap and Ztrade are adaptors linking MASP with DEXs like Uniswap, Quickswap, and Curve.
Like Panther and Railgun, Penumbra supports multiple DeFi activities. When users open LP positions in Penumbra, they essentially create their own mini-AMMs. This results in thousands of concentrated liquidity positions, each set by users with their desired fee structures. While this may fragment liquidity, the Zswap / DEX engine synthesizes all individual positions into a single AMM, enabling routing across the entire liquidity landscape.
Portal Gate uses an anonymous AMM DEX called Automaton as backup for the Book—the order book run by relays to cross users’ trades. If the order book fails to execute due to insufficient liquidity, orders are routed to Automaton, where liquidity is bootstrapped like in any AMM.
Railgun’s Railway DEX uses 0xAPI created by 0x. This means Railway DEX routes orders to find the best execution price across the 0xAPI DEX aggregator. Once a route is found, the wallet generates proofs to use the trader’s balance for the swap and shields incoming tokens from 0xAPI back into the trader’s private balance.
Business Models
Traditional finance (TradFi) dark pools are largely seen as elite clubs accessible only to well-capitalized players. They pay membership fees to place anonymous orders and gain access to counterparty order flow. Trading fees are typically lower than on traditional exchanges. TradFi dark pools can also act as brokers, buying securities cheaply from sellers and reselling at higher prices to buyers.
Crypto dark pools move away from operator-centric designs, instead acting more as facilitators. They generate revenue through two main components: protocol fees on successfully matched orders, and a share of relay fees paid by traders to relayers for transaction processing. Relay operators may also claim part of the relay fee. Traders can choose to run their own relayer to enhance privacy and avoid relay fees.

Decentralized dark pools in crypto may face a “cold start” problem. Unlike DEXs that trade against liquidity pools, most dark pools rely on matching buy and sell orders directly between users. For such systems, having traders on both sides of the market is crucial. Note that TradFi dark pools are hosted by multibillion-dollar banks like Goldman Sachs and exchanges like NYSE, making it easier to attract order flow. Independent dark pools like Liquidnet estimated needing at least 100 buy-side firms to reach critical mass but initially onboarded only 38. Today, Liquidnet ranks among the top three global dark pools.

Centralized exchanges average ten times the trading volume of decentralized exchanges, attracting broader user bases, offering better UX and compliance, thus increasing supply to meet demand. OTC liquidity is relatively harder to obtain.
Most OTC trades in crypto occur via OTC desks, custodial smart contracts, or even Telegram groups—an alarming practice. Scams are common. Impersonation, message editing, and transaction tampering are easy on Telegram. Dark pools may not guarantee instant settlement for illiquid tokens or NFTs, but they offer higher security and privacy. OTC trades via dark pools also eliminate broker fees for OTC desk clients.
Trading volume is vital for dark pool effectiveness. It enables efficient order matching and protects trader anonymity. The more anonymous funds in the pool and the more orders in the book, the harder it is to link depositors and traders to their assets—simply because there are more potential depositors to confuse the linkage. When protecting assets, the type of token matters. Shielding common stablecoins like USDC or DAI offers higher anonymity than obscure meme tokens with few depositors.

MEV and Censorship Resistance
Most DEXs running on public blockchains allow MEV due to their transparent ledgers. Order details on DEXs like Uniswap or Curve are not confidential, allowing searchers and builders to reorder bundles and block transactions to extract MEV.
Privacy is important, but it’s subjective. Tornado Cash excelled at enabling anonymous on-chain financial activity. Being open-source and free to use, it was also exploited by criminals to launder stolen funds. North Korea’s Lazarus Group has stolen nearly $1 billion ($958 million). OFAC maintains a list of Specially Designated Nationals and Blocked Persons. Malicious individuals and entities like Lazarus—and even Tornado Cash’s smart contract addresses—have been added to the OFAC list for non-compliance. Non-compliant protocols risk having their transactions excluded from blocks—a serious censorship issue. And it’s not limited to block builders; validators and relayers can also choose to ignore transactions or blocks.
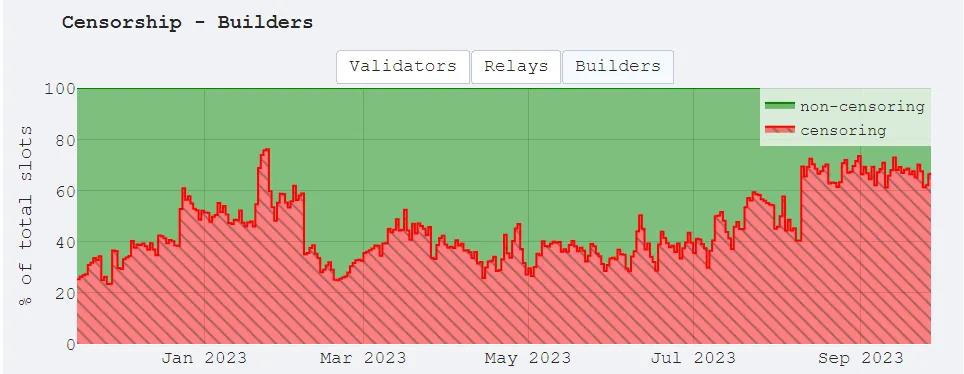
In dark pools, since each order generates ZKPs, order details remain mostly opaque to all third parties—including validators—eliminating the need to disclose matching or settlement details. This architecture resists MEV and censorship, at least as long as the transaction workflow remains within the dark pool’s encrypted environment. However, opportunities for MEV extraction may reappear when public contracts are invoked or shared sequencers are used.
Compliance
Whether operating within a protocol or as an individual user, the last thing you want is for your transaction to hang unprocessed, fail to be included in a block, jeopardizing your state transition, or inviting a visit from the SEC. For the founders and developers of Tornado Cash, these fears became reality—they were arrested on money laundering charges. In many countries, Tornado Cash frontends are illegal or disabled, and unsupported by some centralized exchanges. Yet, the Tornado Cash smart contracts themselves remain usable by technically skilled individuals.
To mitigate such risks, dark pools and other privacy-focused protocols have developed ways for users to opt into compliance voluntarily.
Renegade allows each trader to select a set of counterparties. Individual traders may want basic AML/sanctions checks on their counterparties, while institutions may require full KYB/KYC checks. This counterparty selection logic, using ZKPs for compliance checks, can be configured before MPC begins.
Portal Gate and Panther Protocol partner with compliance oracles, which in turn work with traditional compliance service providers to perform off-chain KYC/KYB verification of user accounts. Upon passing, users receive a ZK proof of compliance. This proof allows their wallets to interact with the dark pool protocol, though verification must be periodically renewed.
In Penumbra, users can use a “transaction view” to demonstrate compliance off-chain, selectively disclosing activities including fund sources. Similarly, Railgun users have “viewing keys,” allowing selective viewing of transactions and balances between block X and Y.
Railgun implements “Proof of Innocence,” developed by Chainway and discussed in the Privacy Pools 2.0 paper. Proof of Innocence helps prove your transactions are legitimate without revealing any details. A Merkle tree stores all prior UTXOs (transactions, balances). With this, you can prove a specific balance belongs to a transaction set. But to prove it does *not* belong, a Sparse Merkle Tree recording NULL values is used. Recursive SNARKs then verify the correctness of the proof chain from initial deposit to final withdrawal, serving as proof that the balance wasn’t part of a tainted set.
Lingering Thoughts
Dark pool users rely on public prices as benchmarks, but asset prices on public exchanges may not reflect volatility occurring within dark pools. Before 2014, price discovery between dark pools and public exchanges was one-way. FINRA and the SEC implemented a rule requiring post-settlement dark pool trade data to be published individually with a 2–4 week delay per security. It remains unclear whether similar disclosure standards will apply to crypto dark pools in the future to improve price discovery across all market participants.

Pure dark pools must accumulate order flow on both sides of the market to reach critical mass. We may see many OTC trades shift to dark pools, as they offer greater security, privacy, and cost efficiency compared to OTC desks and Telegram groups. However, in cases where private DEXs interact with public liquidity pools or external smart contracts, simulation of leaked information could expose certain trades and traders.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News