
Beyond Audits, BlockSec Sets Sights on the Billion-Dollar Market for Monitoring and Blocking
TechFlow Selected TechFlow Selected

Beyond Audits, BlockSec Sets Sights on the Billion-Dollar Market for Monitoring and Blocking
In one year, blocked 13 attack incidents and preemptively secured $14,000,000 in assets—this exclusive expertise is now available to all project teams!
Since BlockSec's inception in 2021, the founding team predicted that blockchain security would absolutely go beyond smart contract audits.
If contract auditing is like a pre-launch security checkup, maximizing the probability of project safety, then monitoring and blocking act as a bodyguard during operations—serving as the last line of defense when facing unpredictable external attacks.
How early can an attack transaction be detected—and how much lead time can we gain for response?
How quickly can we trace the origin and logic of such an attack and find an effective countermeasure?
Can this capability be productized to serve more projects?
BlockSec has been exploring uncharted territory.
First Successes
Leveraging cutting-edge academic expertise and extensive practical experience, BlockSec developed a prototype of its attack-blocking product in early 2022. But could it truly intercept on-chain attacks as expected? The team was waiting for the right moment to prove its capabilities.
Soon after, in March of that year, the system detected an on-chain attack targeting @homecoinfinance. The team responded swiftly, helping the project recover losses—marking the first-ever monitoring and blocking event in Web3 history!
Although the targeted assets were relatively small, this was a major milestone for BlockSec in the Web3 security space.
Shortly afterward, BlockSec successfully intercepted over a dozen on-chain attacks against various projects, cumulatively preventing more than $14 million in asset losses—proving the reliability of the system. This includes recovering $3.8 million for Saddle Finance in April 2022, $2.4 million for Platypus in February 2023, and $5 million for Paraspace in March 2023.
In these successful cases, the team applied multiple attack-blocking techniques such as frontrunning, counter exploits, automatic contract analysis, and auto-generation. These technologies stem from the team’s decade-long expertise in software and system security.
For nearly a year, BlockSec quietly carried out this "white-hat vigilante" work—until the Paraspace incident in March this year finally brought them into the spotlight.
On March 17, just like any other day, BlockSec posted a message on Twitter (shown below) after completing the interception of the attack on Paraspace.
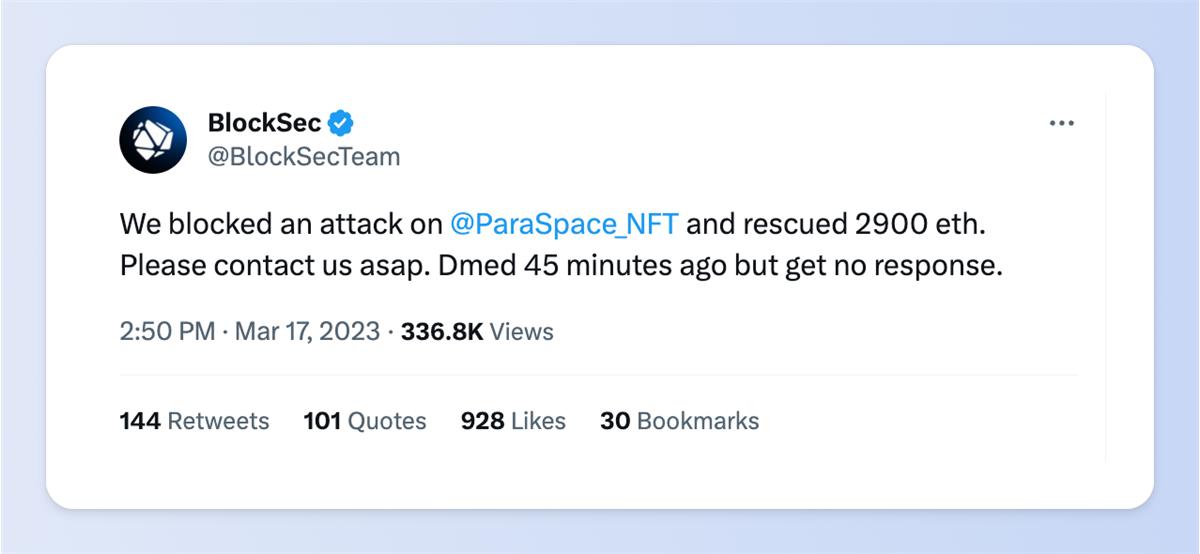
Soon, NFT whales who had staked on Paraspace flooded the comment section.
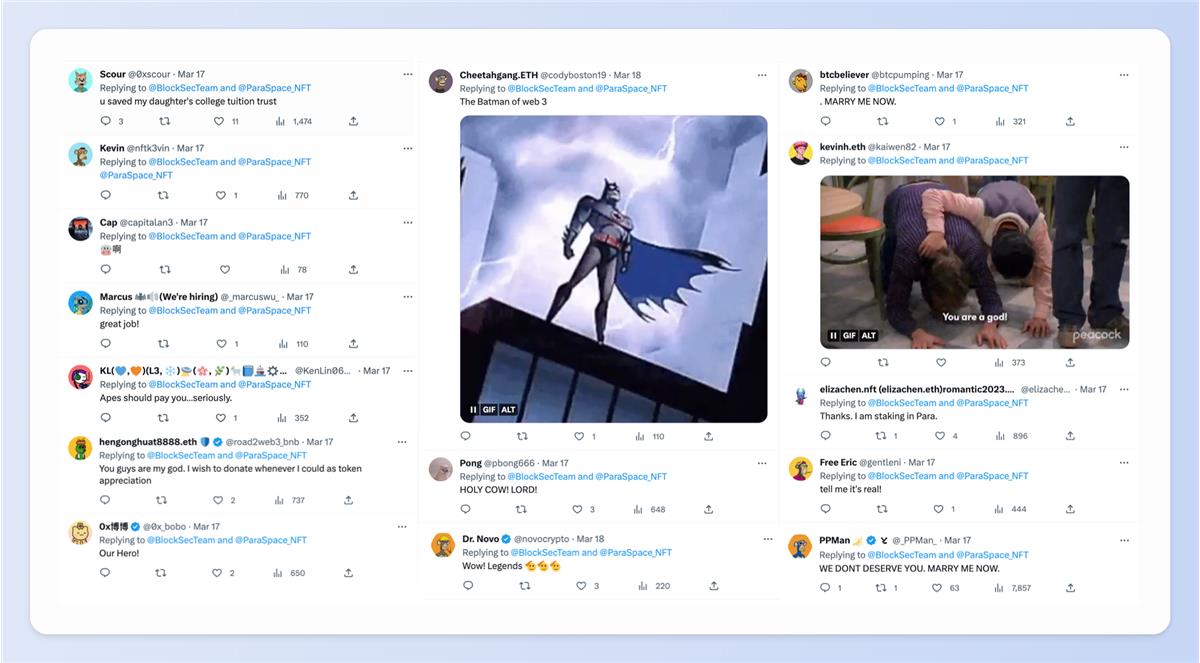
Some hidden Paraspace users anxiously sent private messages asking about the situation. Meanwhile, the hacker’s public “begging” behavior on-chain was widely shared by KOLs and media outlets.
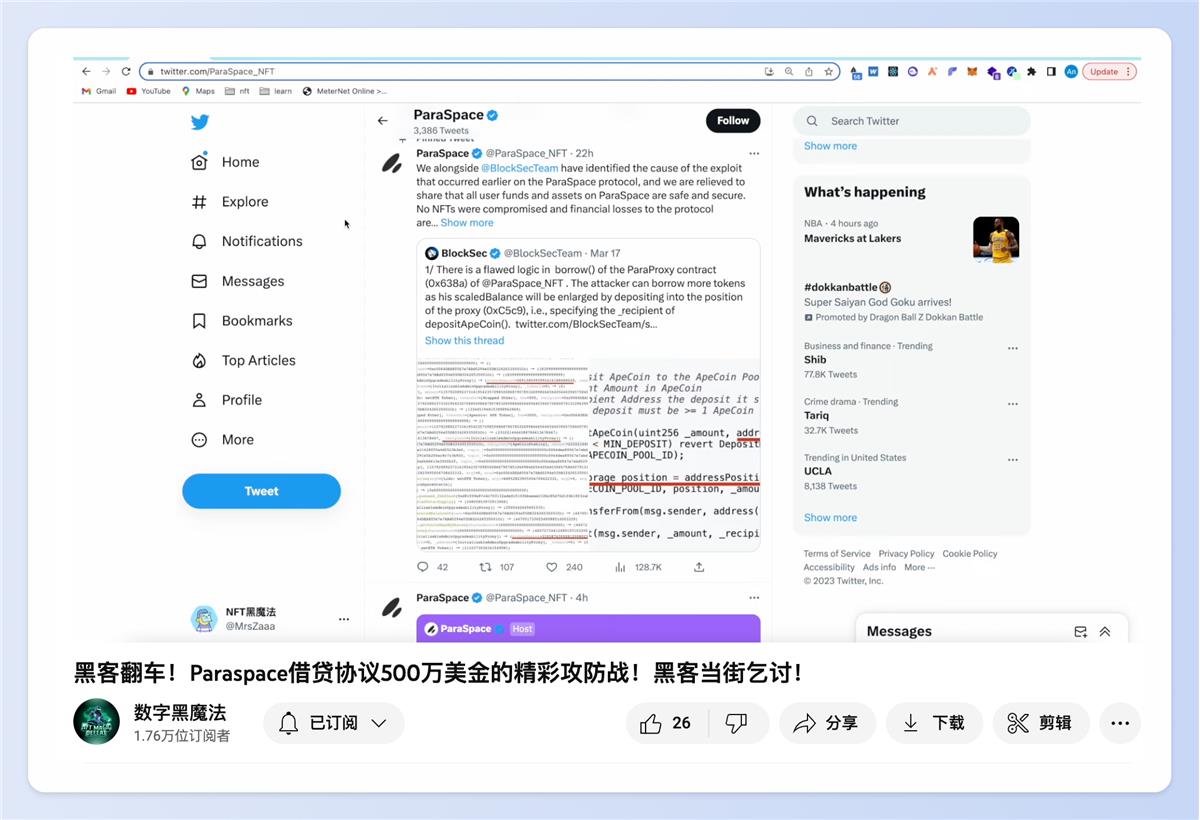
Suddenly, discussions about BlockSec skyrocketed across the industry, and BlockSec became instantly famous.
Incoming Inquiries
Faced with sudden fame, the team was quickly overwhelmed by a flood of inquiry emails. After seeing BlockSec’s “track record,” many projects expressed interest in purchasing its audit services.
At the same time, some projects requested monitoring services, asking whether this monitoring and blocking capability could be deployed specifically for their own use—ensuring peace of mind regardless of post-launch changes in TVL.
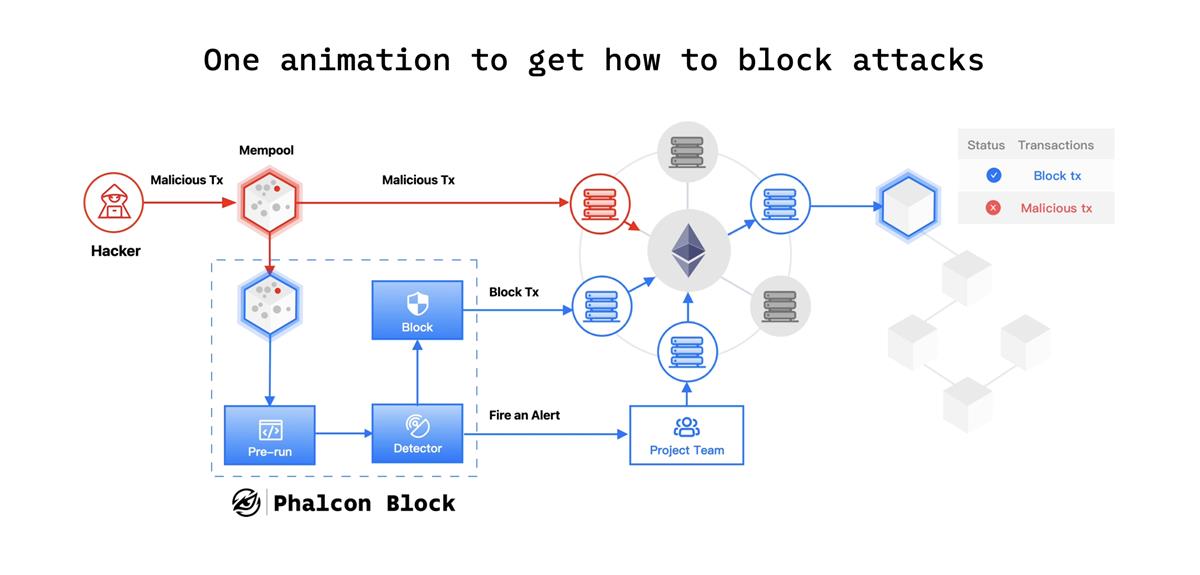
This aligned perfectly with the team’s next step—the “productization” of this capability, launching Phalcon Block.
Roadmap Decision
During product development, the team had multiple internal debates about “who should define the security rules.” Why not provide a technical framework like Forta and let projects define their own rules?
The team’s final answer was: Developers and security experts have fundamentally different ways of thinking.
Developers excel at forward thinking—ensuring that project functions operate as intended—while security experts specialize in reverse thinking—anticipating unexpected events. Precisely because of this, even exceptional developers can fall victim to security breaches. For example, Gavin Wood (former CTO of Ethereum and founder of Polkadot), despite his brilliance, suffered severe losses due to a hack on his Parity project.
Another issue lies in the composability risks inherent in DeFi—risks that developers often struggle to fully account for, especially those arising from interactions with other protocols. Historically, numerous such composability issues have occurred. For instance, Lendf.Me and imBTC functioned safely in isolation, but their combination created reentrancy vulnerabilities, leading to one of the most significant security incidents in early DeFi history.
Therefore, security rules should be defined by professional security firms, and BlockSec is uniquely positioned to provide top-tier intellectual support.
More broadly, what defines a reliable monitoring and blocking system?
-
Low false positive rate: If a system generates 100 alerts daily, all of which are false positives, users will soon stop using it—the information becomes meaningless due to excessive noise.
-
High coverage: Undetected attacks due to insufficient coverage could result in unacceptable losses.
-
Early detection: The system must detect attacks not only when malicious transactions are submitted, but ideally when attack contracts are first deployed.
-
Comprehensive blocking solutions: Systematically integrate multiple blocking strategies to counter evolving attack methods, enabling fast and automated generation of defensive transactions.
Advocacy in Paris
At the recently concluded EthCC side conference, DeFi Security Summit 2023, BlockSec co-founder and CEO Professor YaJin Zhou shared the team’s efforts and achievements in building monitoring and blocking systems.
On the first day, during the Monitoring Panel, Professor Zhou engaged in discussions with key global players in monitoring, including Forta, Hypernative, and Hexagate. When asked by the moderator, “Can you guarantee detection of all attacks?” he replied: “Detecting all attacks isn’t hard—the challenge lies in maintaining a low false positive rate. What BlockSec focuses on is balancing precision and recall effectively.”
Notably, BlockSec’s “lightweight” attack monitoring bot deployed on Forta has ranked #1 in accuracy for five consecutive months—a testament to BlockSec’s deep expertise and outstanding capabilities in this domain.

On the second day, during his keynote speech, Professor Zhou explained how BlockSec’s proactive defense system, Phalcon Block, works, introduced the core technical principles behind attack interception, and walked the audience through several of BlockSec’s successful intervention cases.
These exclusive real-world success stories sparked enthusiastic discussion among attendees.
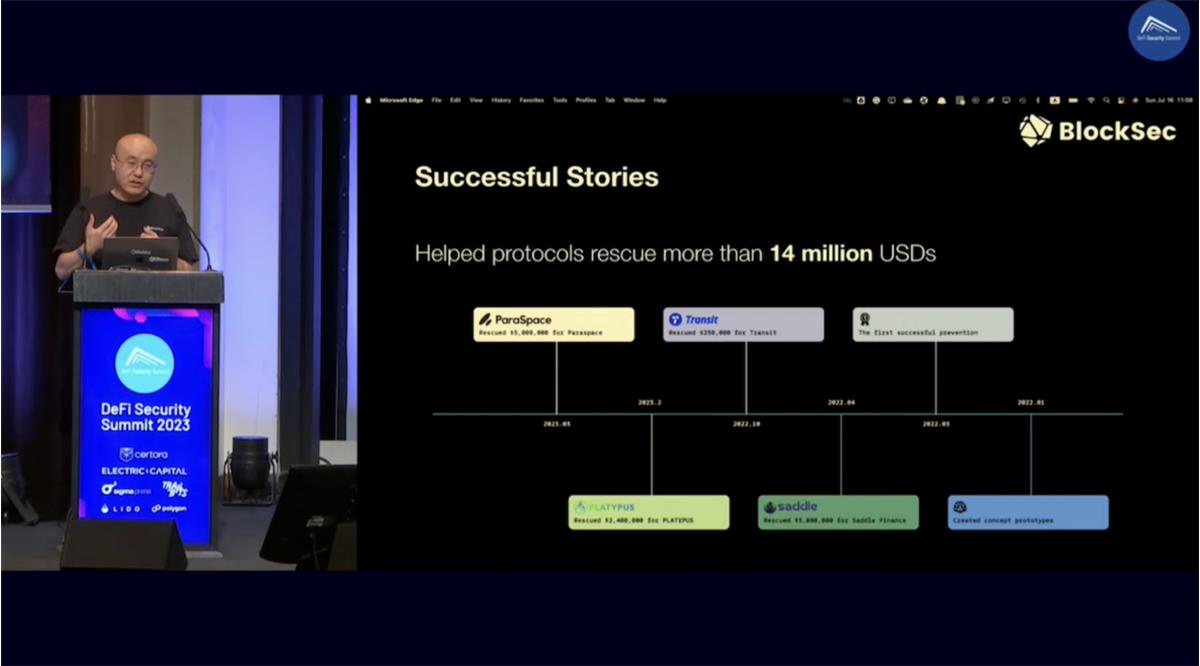
After two days of intense exchanges, we are more confident than ever that BlockSec’s monitoring and blocking solution, Phalcon Block, leads the industry in technology, methodology, and proven practical experience. We have the confidence and capability to build the final line of defense for project security.
Waitlist Now Open
From the Paraspace incident to now, BlockSec has focused on serving seed customers and refining the product, successfully onboarding well-known projects such as Compound and Filecoin.
Now, Phalcon Block officially opens its Waitlist. If your project is interested, here’s how to get started:
-
Submit your interest via the Waitlist: https://phalcon.xyz/block
-
We will contact you in order of sign-up to schedule a demo
-
If satisfied with the product and solution, subscribe online
-
Our technical team will assist with security rule configuration
-
Launch and run the monitoring and blocking system
Follow Phalcon’s official channels for the latest product updates:
Website: https://phalcon.xyz/
Twitter: https://twitter.com/Phalcon_xyz
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















