A Brief Analysis of Four Cross-chain Communication Models: Why Use Zero-Knowledge Proofs to Develop Cross-chain Protocols?
TechFlow Selected TechFlow Selected

A Brief Analysis of Four Cross-chain Communication Models: Why Use Zero-Knowledge Proofs to Develop Cross-chain Protocols?
Under the "one dominant, multiple strong" public chain landscape, users need a more secure, versatile, and user-friendly cross-chain communication protocol.
What Kind of Cross-Chain Services Do Users Need?
In recent years, various independent public blockchains and Ethereum Layer 2 solutions have emerged.
Due to differences in security, low costs, fast transactions, and developer and user communities, different chains each have their own advantages, making it common for users to switch between them.
Compared to Ethereum, transaction fees on Layer 2 and other standalone public chains are lower, and transaction speeds are faster. Therefore, users must use cross-chain bridges to reduce transaction costs or access higher-quality or unique applications on other chains.
If we compare a cross-chain bridge to an "armored truck," then regardless of whether someone tries to rob the truck or not, or what methods they use, the truck itself must have strong defensive capabilities and cannot have any security vulnerabilities. There must be no flaws in its design, manufacturing, transportation, sending, or receiving processes. Existing cross-chain bridge solutions either suffer from architectural design flaws, code vulnerabilities, or rely on certain trust assumptions in the sending, receiving, and relaying stages. All of these issues significantly undermine the security of cross-chain bridges.
As bridges built across public chains, cross-chain bridges undoubtedly play a crucial role in solving liquidity fragmentation among multiple blockchains and enabling asset transfers across chains.
However, user demand for cross-chain technology extends beyond simple asset transfers. Asset bridging is merely one DeFi application within the broader cross-chain protocol landscape. When two fundamentally different networks achieve interoperability through cross-chain protocols, this interoperability should not only enable token transfers across platforms but also support large file and data packet communication between chains.
In the Web3 multi-chain ecosystem, users simply want to seamlessly interact with all major public chains—both assets and data—through a single application.
During interactions, users do not wish to frequently switch wallets or networks.
Under the "one dominant, multiple strong" blockchain landscape, users need safer, more universal, and more user-friendly inter-chain communication protocols.
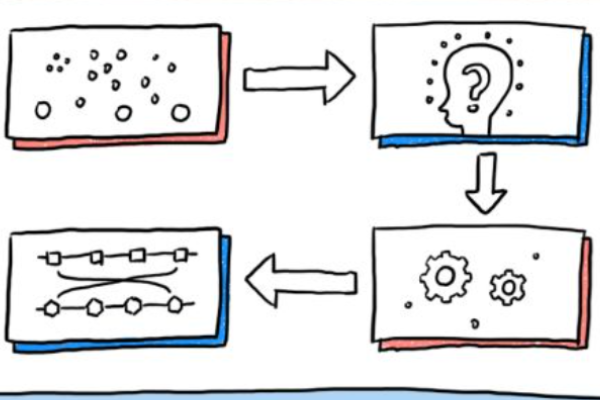
What Are the Cross-Chain Communication Models?
Native Verification Model
Native verification operates by running a light client within the virtual machines of both the source and destination chains, using a relayer for inter-chain communication. This model does not require operating a separate chain between public blockchains. If zero-knowledge proofs are used—as in Way Network—it can eliminate the trust assumptions required by LayerZero.

Figure 1: Native Verification Model
External Validation Model
External validation involves one or a group of validators who monitor specific addresses on the source chain. When a user sends an asset to a designated address on the source chain, the asset is temporarily locked.
Third-party validators verify this information and must reach consensus. Once consensus is achieved, the corresponding asset is minted on the target chain.
The drawback of this model is that it relies on "trust assumptions," making it vulnerable to asset theft due to "single point of failure" or "partial failure."
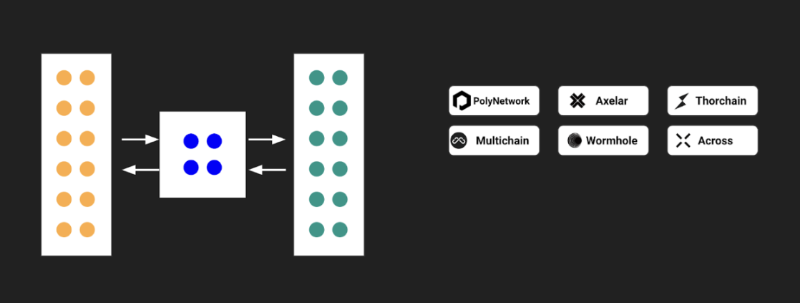
Figure 2: External Validation Model
Local Validation Model
Local validation is a peer-to-peer liquidity network where each node acts as a "router." These routers provide native assets from the target chain rather than derivative assets.
The limitation of this model is its lack of "generality"—it supports only asset transfers and cannot handle general-purpose information or data transmission between chains.
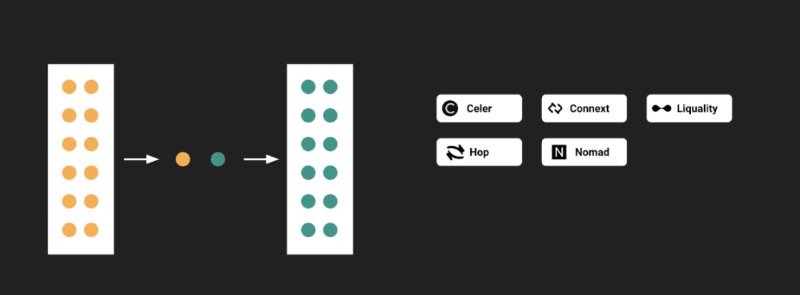
Figure 3: Local Validation Model
Upstream Chain Model
The upstream chain model requires dApps to deploy smart contracts on its chain so messages can be replicated and sent to other Layer 1 blockchains for state updates.
The main drawback lies at the business level: this chain competes rather than cooperates with all other Layer 1 chains, as each vies for dApps to deploy on their platform.
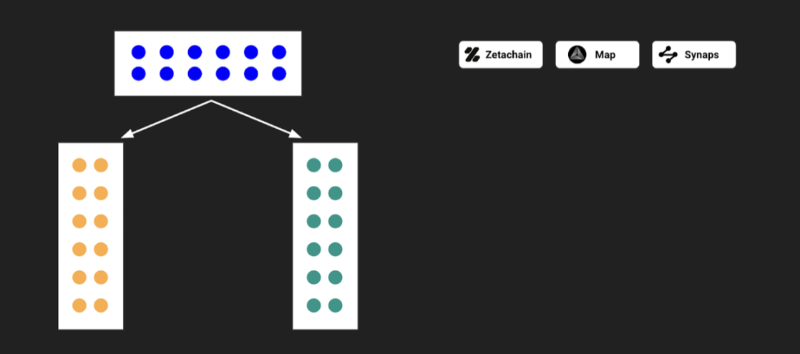
Figure 4: Upstream Chain Model
Why Is zkRelayer the Key to Unlocking Inter-Chain Communication?
An excellent inter-chain communication solution should possess the following advantages:
-
Trustless and secure;
-
Permissionless and decentralized;
-
General and universal;
-
Extensible;
-
Efficient and low cost.
Not all cross-chain solutions have these advantages, and the importance of each varies.
Users may tolerate slower cross-chain services, higher costs, or delayed support for various data formats in cross-chain transfers.
However, the first requirement—being trustless—is urgent and critical. Early external validation models attempted to solve cross-chain communication using another chain—an inherently cumbersome approach that struggles with communication challenges between EVM and non-EVM chains, or POW and POS chains.
Meanwhile, the intermediate chain itself becomes a centralized entity that is difficult to "prove its innocence"—meaning external validation offers neither Decentralized Security nor Trustless Security.
In contrast, LayerZero and Hyperlane in native verification emphasize the roles of Sender and Receiver clients while downplaying Relayer and Oracle components.
This introduces several issues:
-
First, users must trust that the Relayer and Oracle will not collude maliciously;
-
Second, users must trust that the protocol itself won't act maliciously at the Relayer stage.
In other words, none of the current solutions achieve true Trustless Security. Single points of failure and partial failures are like ticking time bombs embedded within inherently flawed cross-chain communication designs.
zkRelayer is a zero-knowledge proof-based cross-chain relay proposed by Way Network. Its key advantage is that users don’t need to trust any external third party or even the protocol itself. As long as the mathematical and cryptographic proof process is complete and correct, the system can be publicly accepted. Importantly, a fundamental shift occurs here: users trust "truth" rather than individuals or organizations. People and organizations can err or act maliciously, but truth cannot. Within the entire process—Chain A → Sender → zkRelayer → ZK Verifier → Receiver → Chain B—the zkRelayer surpasses the Sender and Receiver light clients to become the core component of the entire solution.
The core components of zkRelayer are the ZK Prover and Message Aggregator. Way Network’s ZK Prover uses Fox Tech's ZK-FOAKS zero-knowledge proof method, which is extremely fast and features both Recursive and Trustless properties. Its linear proving time and sub-linear verification time have reached theoretical limits. Applying ZK-FOAKS within the cross-chain relay ensures that communication is Trustless, Efficient, and Low Cost.
zkRelayer is the key that unlocks inter-chain communication. With zkRelayer, a new chapter in inter-chain communication begins.
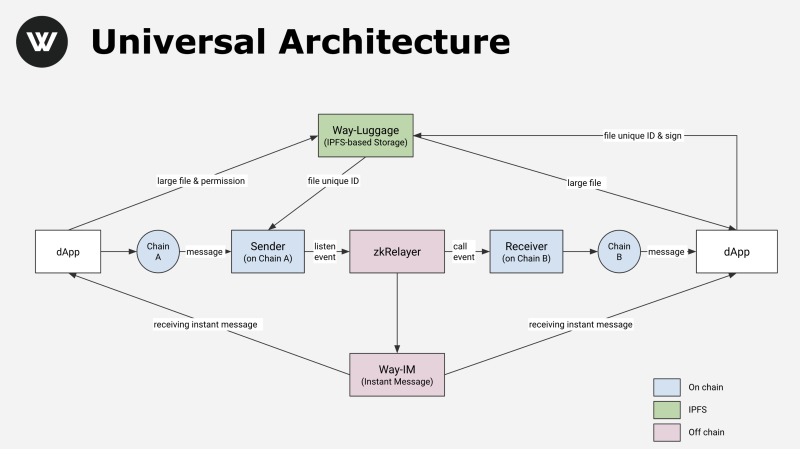
Figure 5: Way Network's Universal Inter-Chain Communication Architecture
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News