What is a Merkle tree proof of reserves for CEXs, and what are its potential issues?
TechFlow Selected TechFlow Selected

What is a Merkle tree proof of reserves for CEXs, and what are its potential issues?
Hopefully, in the future, all exchanges can implement similar or even better 100% proof-of-reserves systems, providing a more open and transparent environment.
Following FTX's collapse due to insolvency caused by misappropriation of user funds, major cryptocurrency exchanges have publicly announced they will implement 100% proof-of-reserves using Merkle trees to demonstrate that their asset reserves are fully backed, not misused, and immune to similar failures.
So, what exactly is a Merkle tree proof of reserves, how does it prove 100% reserve backing, and what potential issues exist?
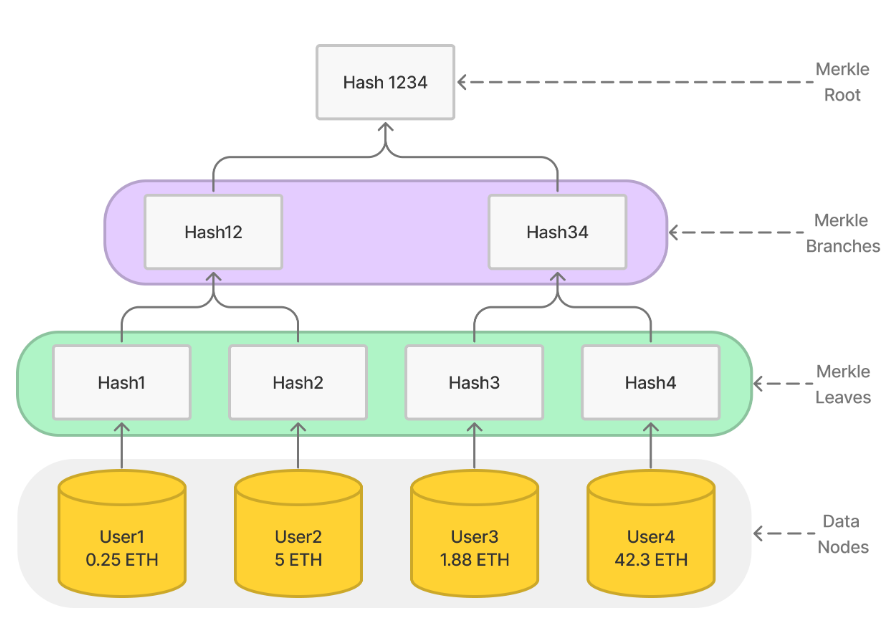
First, let’s understand what a Merkle Tree is. A Merkle Tree is a data structure. Suppose we have four pieces of data, each representing a user ID and balance. Hashing each piece individually forms the leaves of the Merkle tree. Then, combining two leaf hashes and hashing them together creates parent nodes. Repeating this process iteratively results in a complete Merkle tree, with the topmost node called the root. Due to the properties of cryptographic hash functions, any change to a single data node will alter the root hash.
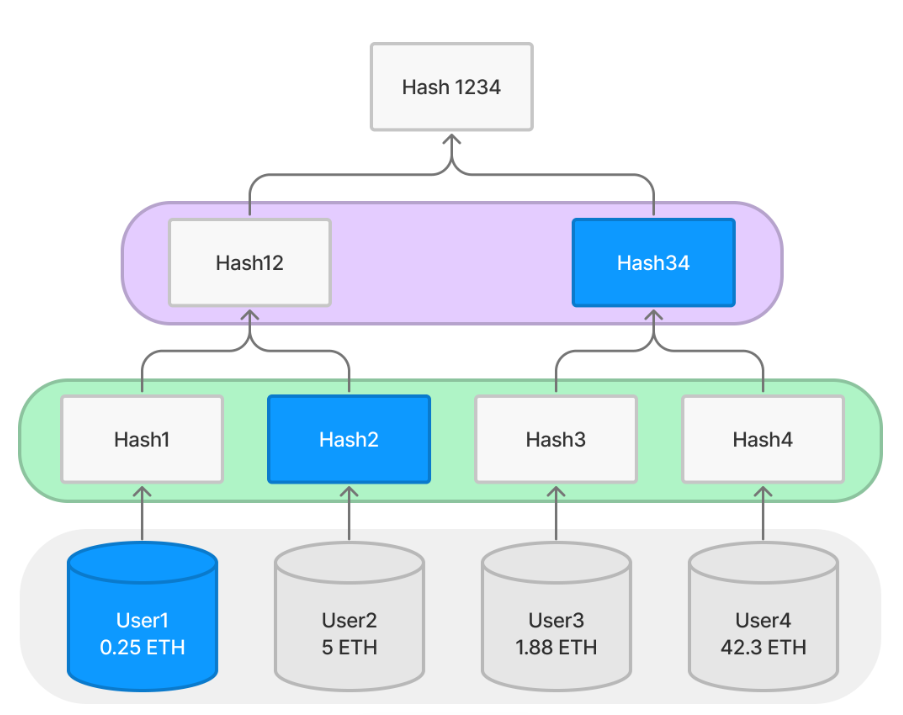
To prove that a specific user exists in the tree—for example, proving User1 and their balance—we only need to provide the values of the blue nodes shown in the diagram. With knowledge of their own user ID and balance, plus Hash2 and Hash34 (provided by the exchange), User1 can verify whether they are included under the root. Clearly, these nodes suffice to recompute the path up to the root; verification simply requires checking if the computed root matches the published one. We call [User1, Hash2, Hash34] the Merkle proof or authentication path for User1.
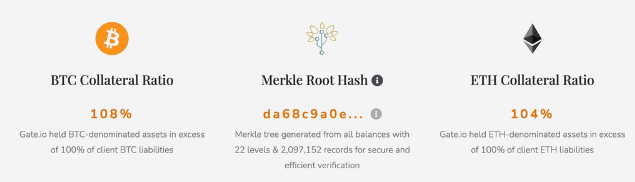
There are various ways to implement Merkle-based proof of reserves. Let's examine Gate.io's approach.
The implementation strategy is:
-
1. Publicly disclose the Merkle tree root.
-
2. Be able to prove to any user that their balance and UID exist within the tree.
-
3. Have a third-party auditing firm sum up all user balances recorded in the tree.
-
4. Have a third-party auditing firm sum up the total balances across all exchange wallet addresses.
Points 1 and 2 create a mathematical and social dynamic deterrent. Neither users nor auditors can independently confirm whether the disclosed Merkle root truly represents all of Gate.io’s users. However, since every user can verify their own presence in the tree (and naturally won’t check others’ data due to privacy concerns), if even one user provides evidence showing they are missing from the tree, it proves Gate.io falsified the data. In the absence of such reports, we assume the root is correct, allowing auditors to proceed with validating and summing balances in the tree.
Points 3 and 4 rely on trust in third parties. This may be criticized, but for centralized exchanges (CEXs), achieving trustless mechanisms is nearly impossible. Our focus should be on recognizing where vulnerabilities might arise.
Potential issues include:
-
Tree root update frequency. CEXs process thousands of transactions per second, making it impractical to update the Merkle root after every transaction. The displayed root is likely outdated, meaning the information available isn't current. Update frequency is a key parameter affecting the system’s reliability.
-
Frontend fraud risk. Users typically verify their inclusion via the exchange’s web interface, which could display fake results. Open-source third-party tools may be needed to mitigate this trust issue.
-
Credibility of third-party audits. Many companies in traditional finance that collapsed had undergone rigorous audits—audits alone do not guarantee safety.
-
Whistleblower feasibility. Even if a user discovers the root is fraudulent, would they recognize what action to take? Could they effectively prove and disseminate this fact?
While we’ve outlined several concerns, increasing transparency is overall a positive trend for CEX users.
We hope that in the future, all exchanges will adopt similar or even better 100% proof-of-reserves systems, fostering a more open and transparent environment.
RIP, FTX.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News