Will CEX be the end of cross-chain bridges?
TechFlow Selected TechFlow Selected

Will CEX be the end of cross-chain bridges?
If we face attacks and either need a capital bailout or have to rely on the goodwill of hackers, what are we doing here?
Author: Marco Manoppo
Compiled by: TechFlow intern
Moving crypto assets across blockchain networks is difficult. But as the cryptocurrency and blockchain industry matures, the Web3 world will undoubtedly become multi-chain, with various blockchains optimized for specific needs and use cases. However, this also increases the risks faced by asset owners when transferring assets between different networks. Last year alone, over $1 billion was exploited from various crypto bridges—and just days ago, we witnessed around $200 million stolen from a cross-chain bridge called Nomad.
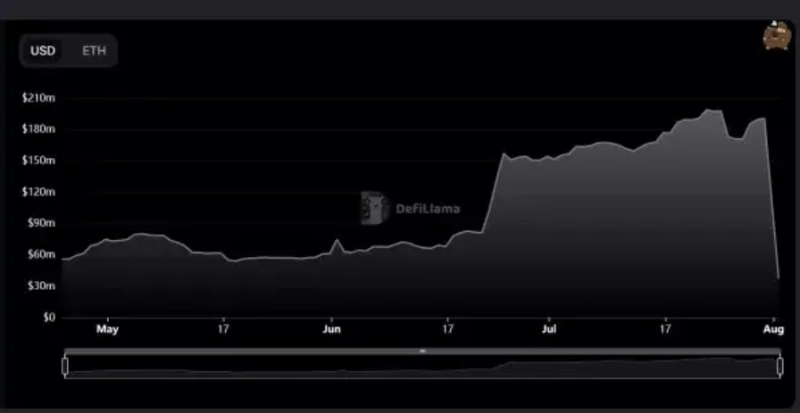
What made this incident unique was that it didn’t require deep technical expertise—leading to widespread participation from all kinds of individuals. Almost anyone familiar with how blockchain transactions work could join the attack simply by copying and pasting the original attacker’s transaction data.
At this point, nearly every existing cross-chain bridge has been exploited in one way or another. Some have survived; others will never truly recover their former glory. I’m not a network expert—I’m merely describing how cross-chain bridges work, their importance, their flaws, and offering my thoughts on how they might evolve as crypto assets mature.
How Do Cross-Chain Bridges Work?
Literally speaking, just as the term suggests, cross-chain bridges "connect" cryptocurrency assets across multiple blockchain networks. This trend arguably began in early 2020, driven by the growth of multiple Layer 1 ecosystems competing for market share, inviting users into their ecosystems to try out their offerings.
These bridges typically work by locking tokens in a smart contract and issuing equivalent tokens on another chain, while ensuring users can always redeem their bridged tokens back to native assets on a 1:1 basis. Let’s look at a concrete example.
Wrapped Bitcoin (WBTC) is one of the most popular bridged assets, operating under a centralized and custodial model. Users deposit BTC on the Bitcoin blockchain and receive WBTC—an ERC-20 token—on Ethereum. BitGo acts as the custodian of WBTC, requiring users to go through KYC procedures via BitGo to redeem WBTC back to BTC. Additionally, a group of partners holds multi-signature keys for all deposited and minted BTC. In this case, users can verify on-chain data to confirm whether the backing is truly 1:1.
Types of Cross-Chain Bridges
In general, cross-chain bridges can be categorized into trusted and trustless bridges.
The former relies on centralized entities to operate, as illustrated by the WBTC example above. Users must trust the security of these centralized custodians to ensure sufficient liquidity is available to redeem bridged assets for native tokens. The risks here include rogue behavior by the central entity or incompetent security management.
The latter relies on smart contracts. Users must trust the security of the underlying blockchain and the code written into those smart contracts to enable bridge functionality. In this case, the risks involve poorly written code, hackers, or previously overlooked attack vectors.
Additionally, there are trustless bridges incorporating AMMs, which essentially create a more seamless cross-chain swap experience. Compared to traditional bridging models, this approach is generally far more efficient. However, it remains a trustless model carrying the inherent smart contract risks mentioned above.
The Bursting Bubble
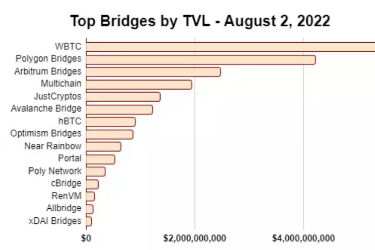
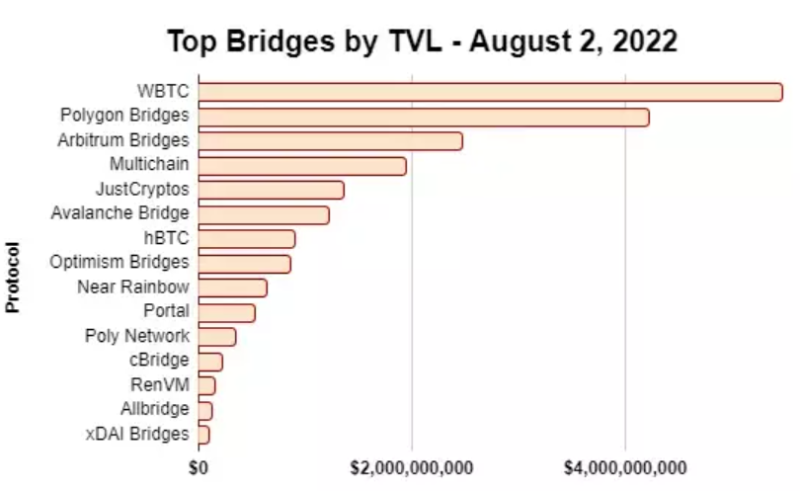
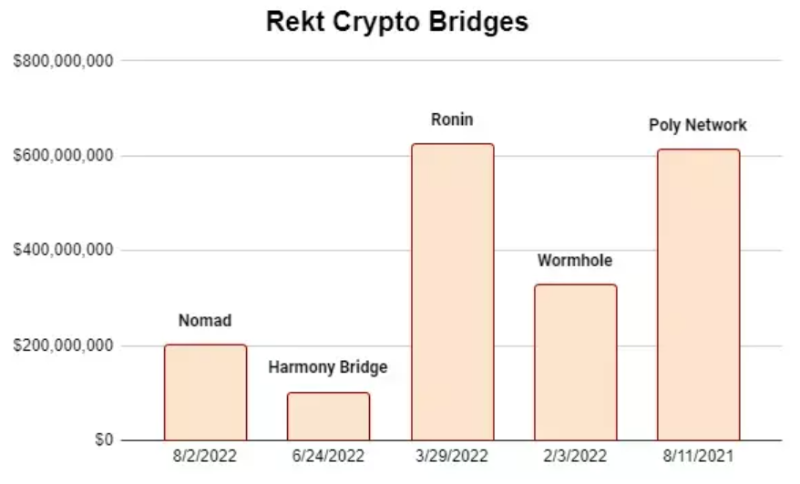
For hackers, crypto bridges are like flowers to bees. As the world becomes increasingly multi-chain and the total market capitalization of crypto assets grows (alongside rising DeFi TVL), attacks on these bridges yield ever-greater rewards. As of August 2, 2022, over $20 billion was locked across various bridges.
Would you believe that founders aged 20–30, backed by teams smaller than ten people, can defend against nation-state-level hackers? (Axie-Ronin, Harmony)
Schools of Thought
Vitalik once stated that the future would be multi-chain but not cross-chain. His basic argument is that decentralized applications living across different chains create complex interdependencies—so much so that a 51% attack on just one chain could trigger significant contagion effects, threatening the entire ecosystem’s economy.
Beyond security risks, token economics must also determine how to handle tokens across multiple chains. Supply-demand imbalances may arise, threatening the integrity of the original token economic framework and potentially impacting inflation rates due to cross-chain activity.
The Savior of Bridges
Ironically, the word “rescue” might be one of the most negatively charged terms mainstream media uses to describe Wall Street firms—those who messed up and needed government (or Warren Buffett) bailouts. Yet now, crypto is rapidly repeating TradFi’s mistakes:
-
Wormhole lost $320 million to hackers—bailed out by Jump Trading.
-
Ronin (Axie) lost $624 million—rescued by Binance, Animoca, a16z, Accel, Paradigm, Dialectic.
-
Harmony Bridge lost $100 million—the team inflated the price of ONE tokens to compensate victims (essentially, the community bailed out the project).
-
Poly Network suffered a $611 million hack—but fortunately, the hacker returned the funds.
Among these four cases, Poly Network had the best outcome, as the hacker eventually returned almost all stolen funds. But if our options when attacked are either needing financial rescues or relying on the goodwill of hackers, then what exactly are we doing here?
Wouldn't it be better to transfer assets via CEXs or trusted bridges instead?
These entities face greater regulation, maintain auditable reserves, have founders who can be legally held accountable, and (hopefully) offer better services.

Of course, you could argue that CEXs and trusted bridges can block your access at any time, especially under pressure from regulators. While this is absolutely true, trustless bridges may also be forced to do similar things—albeit on a smaller scale—such as blocking IP addresses or flagging transactions from blacklisted wallets. Ultimately, when crypto reaches 1 billion users, 99% of dApp consumers won’t actually care about how bridging works—they’ll just want the fastest, safest, and most trustworthy way to move their assets.
I think the game is basically over once USDC/USDT figure out a way to perform cross-chain swaps and get fiat off-ramps legalized in G-20 countries.
Some Thoughts
We aim to build a decentralized financial ecosystem, yet when vulnerabilities occur, we often rely on governments or large institutions to recover funds. If that’s the case, why not trust backed CEXs? Yes, they may be slower to adopt new chains, but if the end result is the same—and given increasing regulatory oversight likely makes them safer—doesn’t that defeat the original purpose?
I predict that "real" institutions managing trillions of dollars will favor CEXs and trusted bridges over trustless ones. Thus, while the trustless bridge market will still exist, its activity will primarily be driven by speculators chasing meme coins on the latest alt-L1s.
Current events, combined with Vitalik’s views on a multi-chain future, perhaps signal that we need to rethink the design, philosophy, and usage of these cross-chain bridges.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News