CoinFund: Fat protocols are not an investment thesis
TechFlow Selected TechFlow Selected

CoinFund: Fat protocols are not an investment thesis
Under the current market conditions, given the same amount of capital, would you prefer to invest in foundational protocols such as public blockchains, or in higher-level application-layer protocols that are closer to end users?
Written by: jake
Translated by: chinadefi
In the current market, given the same capital, would you rather invest in foundational protocols like public blockchains, or in higher-level application-layer protocols that are closer to end users? This article offers insight into that question. The types of protocols leading each bull cycle have consistently evolved, and this analysis is worth considering.
Additionally, before diving in, here’s a quick primer on "fat protocols": a fat protocol is one that incorporates more functionality—thus appearing “fat.” The image below better illustrates the widely discussed distinction in blockchain between fat protocols and thin internet protocols like TCP/IP:
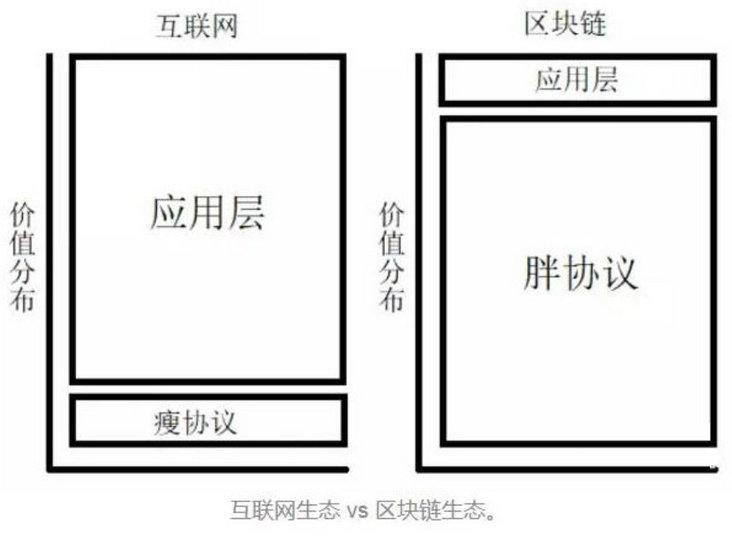
Seeking Investment Criteria Within the Functional Stack
In “Fat Protocols,” my colleague Brooklynite Joel Monegro offered a profound comparison between 1990s internet protocols and 2010s blockchain protocols. He explained that early internet protocols delivered immense value but were “thin,” meaning monetization historically occurred at the “fat” application layer built atop them. In contrast, decentralized blockchain protocols, supported by scarce digital assets, are now “fat”—monetized at the network level via cryptoeconomics or tokens—while the application layer remains comparatively “thin.” Decentralized applications can still monetize, but primarily through interoperability with the underlying data layer.
This view of blockchain networks is a significant observation that has deeply influenced how blockchain investments are structured, as discussed in CoinFund’s writings on blockchain investing. Specifically, it helped traditional investors and Bitcoin startups realize over a market cycle that participating in private equity of centralized firms is typically a suboptimal way to invest in decentralized networks—but that was last summer. This summer, we have crypto funds, venture capital funds allocating capital to tokens, hedge fund investments in SAFTs, grant-based smart contract options, crypto asset options, token-based contract protocols, and other technologies that together offer a toolkit for growing value networks. As investors spend time understanding and experimenting with the complexity of blockchain’s new asset classes, issuance mechanisms, and lifecycle dynamics, they can make informed decisions about optimal investment structuring.
Characterizing value networks as fat protocols helps emphasize the need for these new investment approaches and outlines a solution: investing in the cryptoeconomics of networks. However, the idea of fat protocols as an investment criterion is easily misunderstood. Today, we see investors applying rigid filters for “protocol tokens” when evaluating opportunities. We all wish TCP/IP had been a “fat” protocol so we could’ve invested in it back in 1992. But I believe this investment strategy embraced by crypto investors misapplies Joel’s concept of value networks.
There exists an investment thesis based on the fat protocol idea, summarized as follows:
If you invest in an application token, you face a 95% startup failure rate—or higher! If you invest in a protocol token, you gain diversification across all applications built on that protocol. It’s better to diversify across protocols than across applications, because protocols are more broadly applicable and capture value from everything built on top of them. Foundational protocols will accrue more value than others (ah, if only TCP/IP had been a fat protocol!). Therefore, invest in protocol tokens, not application tokens.
I believe, on its own, this thesis is highly imprecise and subjective—and thus suboptimal as an investment criterion. I also believe that a significant portion of the value generated within decentralized networks will never flow exclusively to the foundational protocol layer. Instead, we should strive to more precisely understand the interactions and value flows across layers of the functional software stack.
Alice Doesn’t Know How to End a Protocol
When discussing protocols in the context of blockchain investing, we’re often imprecise. A protocol is simply a set of rules, behaviors, and formats that define communication standards between two or more nodes on a network. This definition is so broad that we can consider many decentralized applications or platforms themselves as protocols.
By technical intuition alone, it's clear that each layer of functionality simultaneously acts as a protocol to the layer above it and as an application to the layer below. TCP/IP is an application of a complex hardware networking stack, while serving as a protocol for data transmission between computers. HTTP is a protocol for structured web data, and an application of TCP/IP. Within the stack, dApps like Augur are applications of both the Ethereum protocol and data storage protocols like IPFS. After all, Twitter functions as a microblogging protocol with thousands of applications built on its API—including Twitter’s own app. Finally, James Childs-Maidment’s stateless smart contracts are an application of Ethereum, which serves Leeroy’s centralized UX app. In short, you can draw protocol-application boundaries at any level of abstraction along the functional stack.
Being literally defined as a “protocol” does not determine whether it is “fat.” Fat protocols refer to value and information networks—open networks that maintain compact data ownership and can be monetized via cryptoeconomics. Therefore, what matters is understanding how value flows across layers of the functional stack and how each layer captures that value.
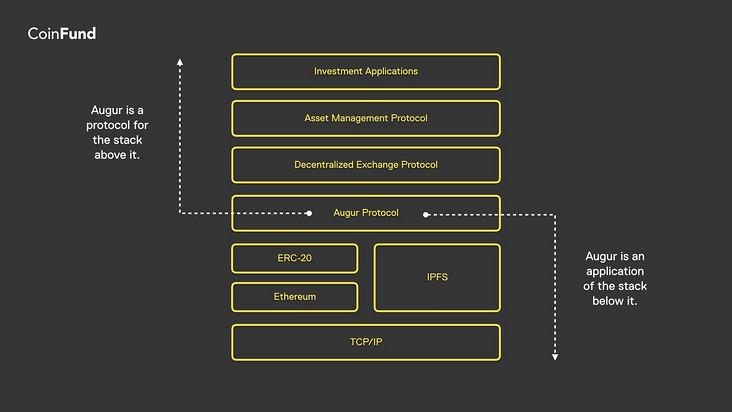
The protocol-application boundary is an abstract divider between two parts of the functional stack.
If “protocol” is to serve as a filter for better investment decisions, presumably due to desirable traits like greater diversification and upside potential, then we must be able to explain how such protocols acquire, accumulate, and transfer value. Specifically, we should be able to articulate why one protocol-application boundary offers better investment characteristics than another.
Good Luck Investing in TCP/IP
Intuitively, I believe lower layers in the protocol stack are more widely applicable and thus offer greater diversification—but this is often incorrect. In reality, for an investment aiming to enhance diversification, being “closer to TCP/IP” is a questionable criterion. For a protocol to diversify the layers above it, it must first achieve sufficient market share to serve those layers.
The blockchain era differs from the TCP/IP era. TCP/IP had essentially one real competitor, and its adoption required coordination among governments, corporations, and standards bodies worldwide. Today’s decentralized protocols are developed by small, agile, open-source teams, resulting in increasing numbers of competing protocols with overlapping functionalities. Clearly, rampant speculation around token supply disincentivizes interoperability: everyone wants to build their own protocol to capture more value. Consider the number of decentralized protocols addressing the same concepts—stablecoins, lending, trading, social media. Betting on the “wrong” protocol may mean investing in an isolated stack.
Unlike 1970s network protocols, which were “technically distinct enough to prevent intercommunication,” every decentralized protocol built on the same platform (like Ethereum) can interoperate. (For those that don’t, interoperability platforms like Cosmos or Polkadot exist—though these sit higher up in the stack, not lower.) Even traditional cronyism and aggressive investor-driven “ecosystem” building—where investors push portfolio companies to integrate—won’t work reliably. In a diversified protocol environment, many investors may end up sharing in the gains from multiple protocols.
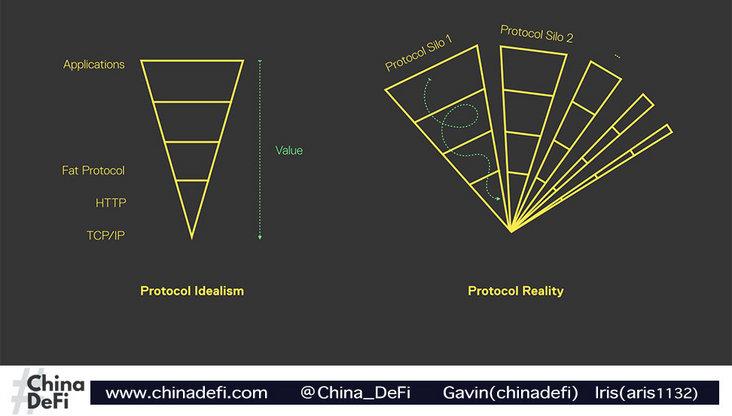
In practice, the protocol stack is fragmented into dependent silos, competing for data and exhibiting complex value flows.
In sum, from a diversification standpoint, choosing the right base protocol isn’t much different from choosing the right startup or the right application. On the other hand, if we assume protocols can coexist and interoperate, perhaps we should instead invest in their interoperability—which resides higher up in the stack.
We Left Value in the Applications
Typically, a base protocol’s ability to capture value from higher application layers is highly context-dependent and involves complex relationships with underlying protocols. Simple examples illustrate this well.
Augur Delivers Usage, Not Value, to Ethereum
Augur is a three-party cryptoeconomic system involving market creators, reporters, and traders. Speculative increases in REP price affect traders little—they may never hold or even need REP to trade markets. Yet, Augur’s usage fundamentally drives REP valuation through a perpetual pricing mechanism. Meanwhile, Augur manifests on Ethereum in a very different way: paying transaction fees to the network for executing Augur’s logic. In practice, every transaction in the Augur app is a transaction on Ethereum.
If we draw a line between Ethereum and Augur, Ethereum is exposed to Augur’s usage—not its value. This is merely a projection of value flow from Augur to Ethereum. To truly capture the fundamental value of the Augur platform, one should hold REP.
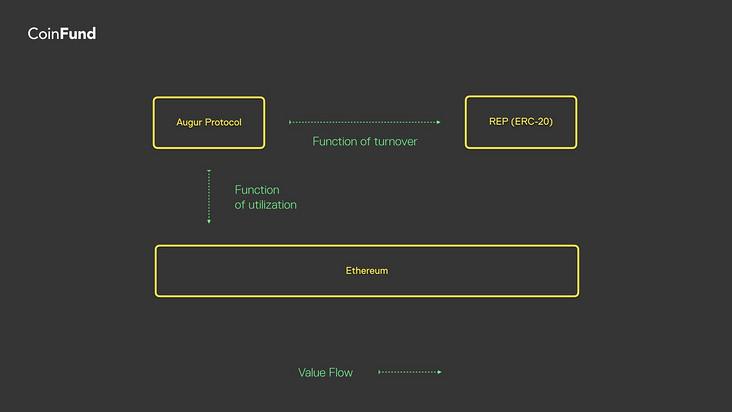
(1) Augur projects its usage onto Ethereum via transaction volume and network fees.
(2) The value of REP is a function of future discounted cash flows related to platform trading volume.
(3) Usage value and turnover value are largely independent and uncorrelated.
Leeroy Achieves Tokenization Through Direct Use
Similarly, holding ETH only gives exposure to Leeroy’s usage, not its value. Leeroy itself has no token, so it isn't a “fat” protocol. But that’s the point: to gain economic exposure to Leeroy’s operational throughput via a base protocol proxy, one would have to become an Ethereum miner. Conversely, Leeroy’s stateless smart contract architecture enables a more attractive monetization alternative within its centralized application layer—the so-called “filters” of Leeroy. If you're actually earning money on Leeroy as an influencer, that might be the most effective way to capture non-operational revenue from the platform.
Tokens Closer to Consumers Can Win in the Short Term
Ultimately, stepping back, 2017 marked blockchain technology spilling into broader tech markets. CoinFund was fortunate to collaborate with some of the first major tech companies pioneering cryptoeconomic business models—Kik Interactive and YouNow. Moreover, seasoned entrepreneurs already grasp the anticipated value of crypto assets and micropayments—a trend that continues. As more mainstream users enter cryptoeconomics, short- to medium-term growth hinges on the success of consumer-facing applications. Indeed, any on-chain blockchain protocol today is likely to lag behind due to scalability bottlenecks. Consumer apps built by experienced, well-resourced companies with internal tech teams will require mainstream-friendly experiences. This means value will flow into semi-centralized niches, off-chain solutions, and custodial experiences.
These perspectives suggest that for most investors, diversification must occur vertically across the protocol stack—not horizontally at its base layer. And if you're playing the base protocol game, perhaps it’s time to get more precise about value flows.
Conclusion
Investors who rigidly separate “application tokens” from “protocol tokens” are misguided. I say this: yes, value often flows down the functional stack, but it doesn’t necessarily pool at the base layer—it gets isolated, redirected, locked, diluted, or transformed along the way. Each value transfer between layers requires individual analysis, and not all transfers behave the same. Holding Ether may give investors more exposure to the usage of upper-layer assets, but not necessarily to their excess value. Holding tokens of applications that onboard millions of users into cryptoeconomic systems may be a far superior mid-term strategy for capturing blockchain’s growth curve. Each protocol-application boundary demands its own analysis. We have substantial work ahead to more precisely understand protocols and the relationships between layers in the functional stack.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News