
Drainer Attacks: The Evolving Phishing Threat You Need to Know
TechFlow Selected TechFlow Selected

Drainer Attacks: The Evolving Phishing Threat You Need to Know
Beware! Drainer phishing tactics have escalated again.
Author: BlockSec
Drainer: Upgraded Phishing Tactics Target Five Major Projects
Recently, an increasing number of hackers have been using the Drainer toolkit to conduct Web3 phishing attacks. They leverage phishing websites that automatically prompt users to connect their wallets, extract valuable token information, and generate malicious transactions. Initially, hackers directly spread these phishing sites on social media platforms. However, as Web3 users have become more vigilant, traditional methods have proven less effective. Hackers have therefore shifted tactics—exploiting the traffic and trust associated with popular platforms to widely distribute phishing links by compromising Discord servers, Twitter accounts, official websites, software supply chains, and email databases—causing significant losses for many users.
To better understand the strategies used by these hackers, we summarize several recent Drainer-related incidents in the table below:
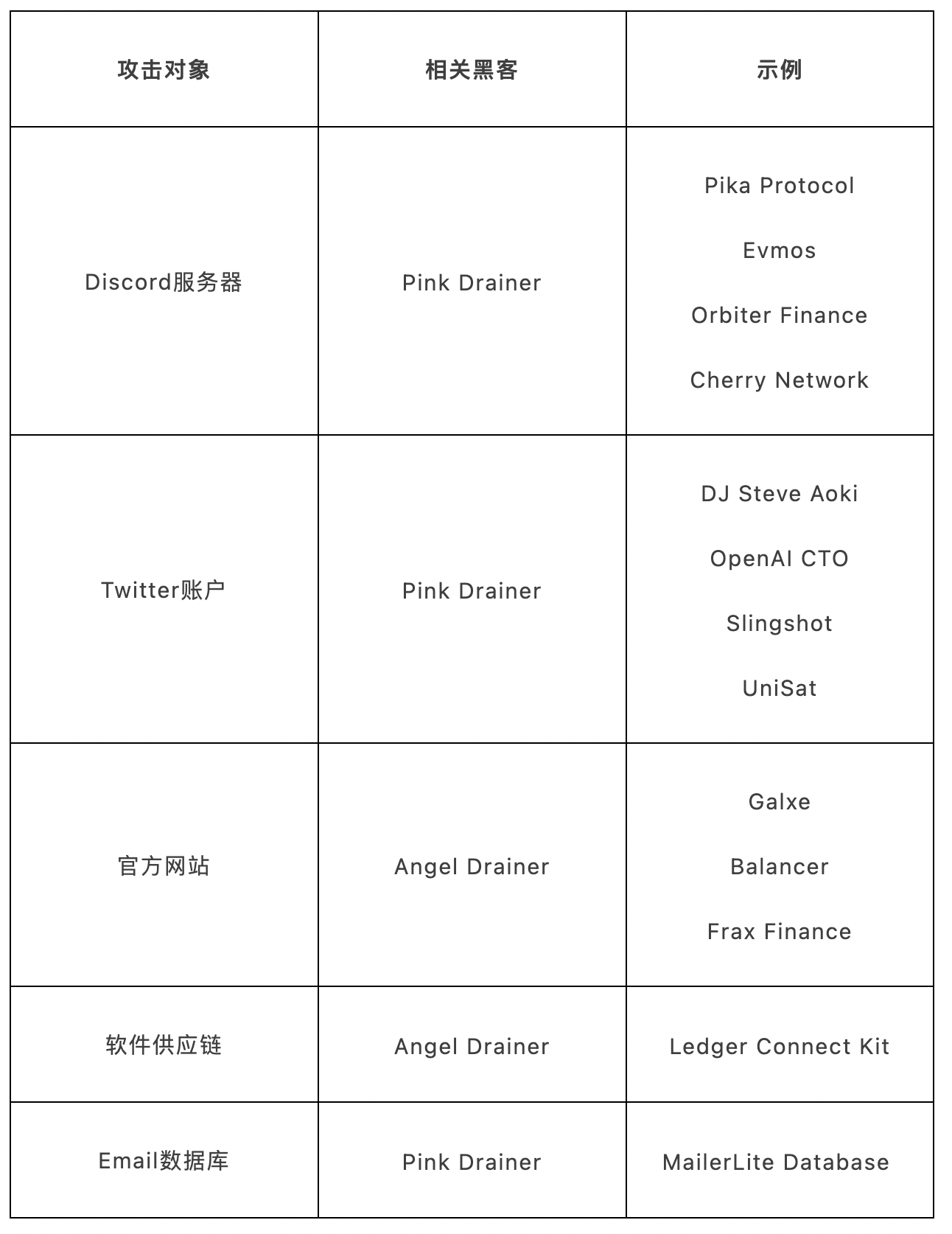
Discord Server Compromise
On May 31, 2023, Pika Protocol’s Discord server was hacked. Pink Drainer spread a phishing website containing malicious JavaScript code within the official Discord group. The site tricked Discord server administrators into visiting it and performing actions such as clicking buttons or adding bookmarks, which executed the malicious code and led to the theft of their Discord tokens. Around the same time, several other popular Web3 projects experienced similar attacks.
For details, see 🔗: https://www.secureblink.com/cyber-security-news/3-million-crypto-stolen-by-pink-drainer-exploiting-discord-and-twitter
Twitter Account Takeover
On May 26, 2023, Steve Aoki’s Twitter account was compromised, resulting in $170,000 in losses for cryptocurrency investors. Investigation of the phishing account’s transactions revealed a connection to Pink Drainer, stemming from a SIM swap attack. In such attacks, hackers use social engineering (often leveraging the victim’s personal information) to deceive telecom providers into transferring the victim’s phone number to a SIM card controlled by the attacker. Once successful, the hacker gains control over the victim’s Twitter account. Similar incidents have occurred with the Twitter accounts of OpenAI CTO Slingshot and Vitalik Buterin, all linked to Pink Drainer.
For details, see 🔗: https://www.bitdefender.com/blog/hotforsecurity/hacked-djs-twitter-account-costs-cryptocurrency-investors-170-000/
Official Website Hijacking
On October 6, 2023, Galxe’s official website was redirected to a phishing site, causing victims to lose $270,000. According to the official statement, an unidentified hacker impersonated a Galxe representative and submitted forged documents to the domain service provider, resetting login credentials and bypassing Galxe’s security procedures to gain unauthorized access to the domain account. Transaction records from affected wallets indicate that the attack was carried out by Angel Drainer. Balancer and Frax Finance have also suffered similar attacks from Angel Drainer.
For details, see 🔗: https://www.secureblink.com/cyber-security-news/3-million-crypto-stolen-by-pink-drainer-exploiting-discord-and-twitter
- 4 -
Software Supply Chain Attack
On December 14, 2023, Ledger Connect Kit—a JavaScript library designed to facilitate connections between websites and wallets—was found to contain a vulnerability. A former Ledger employee fell victim to a phishing attack, allowing hackers to upload malicious files to Ledger’s NPMJS repository, creating the vulnerability. As a result, attackers were able to inject malicious scripts into popular cryptocurrency websites, prompting users to sign fraudulent transactions via phishing accounts. Platforms including SushiSwap and Revoke.cash have seen over $600,000 in user funds stolen. Transaction analysis confirms that Angel Drainer is behind this campaign.
For details, see 🔗: https://www.ledger.com/blog/a-letter-from-ledger-chairman-ceo-pascal-gauthier-regarding-ledger-connect-kit-exploit
- 5 -
Email Database Breach
On January 23, 2024, email service provider MailerLite was breached through a social engineering attack. This led to a large volume of phishing emails containing malicious links from Pink Drainer being sent out under the official accounts of WalletConnect, Token Terminal, and De.Fi. The breach originated when a team member inadvertently clicked on an image linking to a fake Google login page, granting hackers access to MailerLite’s internal admin panel. The attackers then reset passwords for specific users via the admin panel, leading to the exposure of their email databases and widespread distribution of phishing emails.
For details, see:
🔗 https://cointelegraph.com/news/mailerlite-confirms-hack-crypto-phishing-email-3m-attacks
Conclusion: Understanding Drainer Tactics to Counter Web3 Phishing Risks
Drainer developers continue refining techniques to infiltrate well-known projects and exploit their traffic to propagate phishing sites. We remain vigilant against these evolving tactics and continuously monitor related phishing addresses and transactions. Users must also carefully verify all transaction details before taking any action.
This article aims to help users understand how hackers target projects, enabling better protection against Web3 phishing risks and safeguarding against Drainer-related fraudulent transactions.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















