
Understanding Singularity: Private Transactions on a Transparent Blockchain
TechFlow Selected TechFlow Selected

Understanding Singularity: Private Transactions on a Transparent Blockchain
Looking forward to Singularity becoming the next leader in the ZK privacy赛道 by embracing regulated dark pools.
Authors: Oliver, Andy, Howe
1 Introduction
In 1969, financial market trading was still conducted in traditional trading floors. At that time, computer technology had not matured, and traders relied on shouting to issue instructions. This inefficient and non-private method made it difficult for institutional investors to execute large trades without causing market fluctuations. Instinet, founded by Jerome Pustilnik, emerged as a solution. By offering an electronic trading platform that allowed anonymous order submission, Instinet matched buy and sell orders and executed trades. This model not only improved trading efficiency but also ensured confidentiality, effectively preventing market impact and information leakage.
Today, technological advancements have given rise to blockchain, a revolutionary innovation that brings unprecedented transparency and security to financial transactions. However, while blockchain’s public and immutable ledger offers many benefits, it poses new challenges for large traders. On a public blockchain ledger, every transaction is visible to all participants, making it difficult for large traders to maintain anonymity. Traditional exchange platforms cannot fully protect trader privacy—public disclosure of large orders may lead to price volatility, affecting trading efficiency and cost. Furthermore, regulatory uncertainty and market opacity add additional risks for investors.
This report explores dark pools in blockchain as an innovative solution, examining how they leverage advanced privacy-preserving technologies and automated trading mechanisms to provide a more secure and efficient environment for large-scale cryptocurrency trading. It also analyzes how Singularity delivers a private yet compliant decentralized trading platform for large investors using technologies such as FHE (Fully Homomorphic Encryption) and ZKP (Zero-Knowledge Proofs).
2 What Is a Dark Pool?
In traditional finance, dark pools refer to private trading platforms that do not publicly disclose trading information. They allow investors to conduct large trades without revealing their trading intentions. Dark pools originated in the U.S., emerging alongside increasing merger and acquisition activity and growing demand for large-scale equity transfers. As financial markets evolved, dark pools gained prominence across stocks, bonds, and foreign exchange, especially with the rise of high-frequency and algorithmic trading. Statistics show that dark pool trading now accounts for 30% to 50% of stock market volume, playing a critical role in market liquidity.
In the cryptocurrency market, the growing number of large holders has driven rising demand for block trades. These large orders can significantly impact the market, sometimes even triggering turmoil. To mitigate this risk, many traders turn to OTC markets or even Telegram groups. According to Kraken's 2020 data, global OTC trading volume surged 20-fold since 2018, reaching a daily average of approximately $300 billion, accounting for nearly 70% of total crypto trading volume. However, OTC markets face issues such as insufficient liquidity and lack of regulation. To address these challenges, dark pools have been introduced as a solution to provide a more stable and private trading environment.
Key features of dark pools include:
-
Privacy and Confidentiality: Dark pools enable anonymous trading, protecting traders’ identities and order sizes from public knowledge until execution.
-
Reduced Market Impact: Large institutional investors can execute block trades without causing significant price movements in public markets, minimizing slippage and market impact.
-
Protection of Trading Strategies: Dark pool trading helps conceal strategies from public view, avoiding exploitation through MEV arbitrage, copy-trading, or statistical arbitrage.
-
Liquidity and Price Improvement: By matching buyers and sellers who might not find each other on traditional exchanges, dark pools provide additional liquidity and potentially better pricing, especially for large orders.
-
Regulatory Oversight: Dark pools are subject to regulation, with authorities monitoring activities to prevent unfair access, insider trading, or market manipulation. However, centralized management models still pose risks related to security, trustworthiness, and potential misuse of private data. Historically, several cases have seen centralized dark pools penalized for violating trust principles.
Core Privacy Technologies
Dark pools represent a branch of the privacy sector, integrating privacy-enhancing technologies (PETs) such as Zero-Knowledge Proofs (ZKP), Multi-Party Computation (MPC), and Fully Homomorphic Encryption (FHE) into their architecture.
▪ Zero-Knowledge Proof (ZKP)
Zero-knowledge proofs (ZKPs) allow a prover to convince a verifier of a statement’s truth without revealing any underlying information. This technology is crucial in Ethereum Layer 2 scaling solutions like ZK Rollups, which compress transaction data into compact ZK proofs submitted to the main chain, enabling validity verification. These proofs consume minimal storage while preserving transaction privacy, showcasing the advantages of trustless systems. Beyond scalability, ZKPs support privacy computation, with implementations including zkSNARKs, zkSTARKs, and Bulletproofs, collectively advancing privacy protection and transaction efficiency in cryptocurrencies.
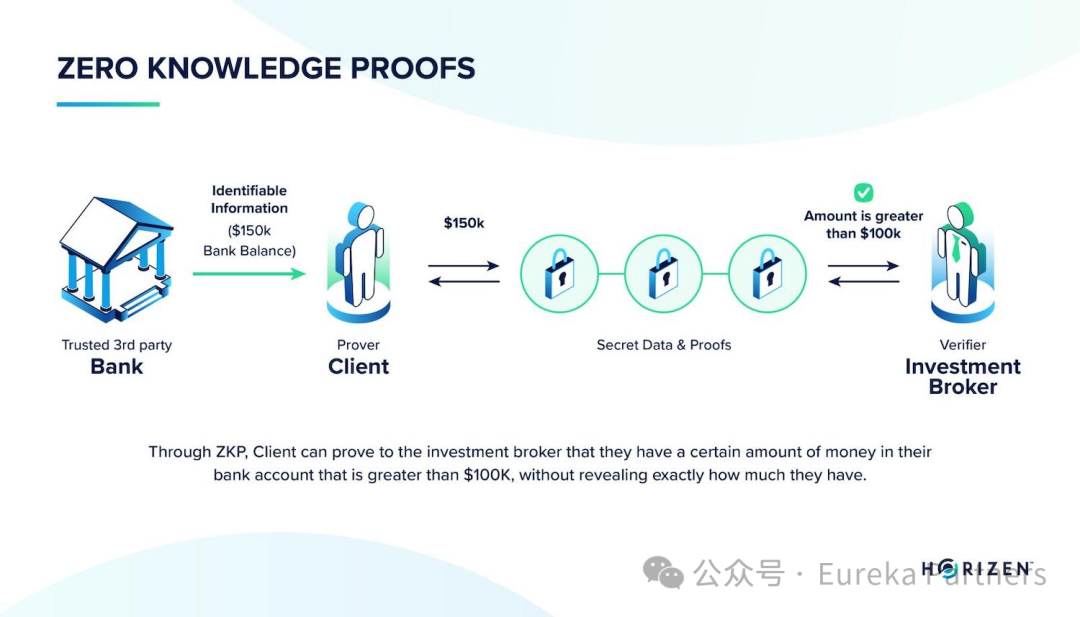
Introduction to Zero-Knowledge Proofs
▪ Secure Multi-Party Computation (MPC)
Secure multi-party computation (MPC) enables multiple parties to jointly compute a function without revealing their individual inputs. In privacy applications, MPC protects sensitive data by allowing collaborative analysis, computation, or decision-making without exposing personal data. Its core advantage lies in privacy preservation—through distributed computing and encryption, participants ensure their data remains confidential throughout the process.
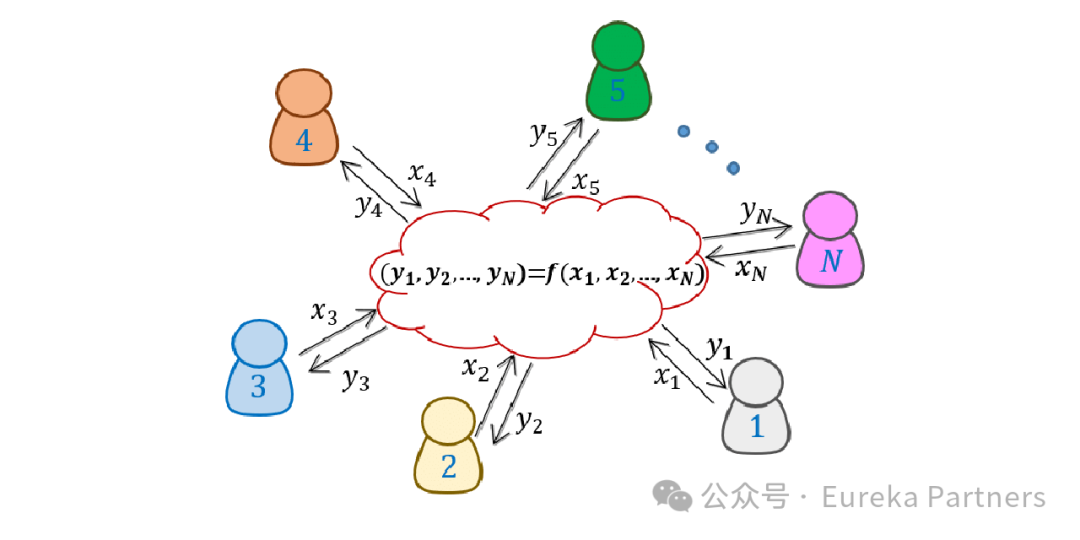
Introduction to Secure Multi-Party Computation
▪ Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) is a cryptographic technique that allows computations to be performed directly on encrypted data without decryption. This means operations like addition, subtraction, and multiplication can be carried out while data remains encrypted, and the decrypted result matches what would be obtained from operating on plaintext. FHE’s core value lies in its powerful privacy protection, ensuring data remains confidential during processing and greatly enhancing data security.
Balancing Censorship Resistance and Compliance
Decentralized exchanges (DEXs) like Uniswap and Curve, running on public blockchains, are vulnerable to Maximum Extractable Value (MEV) due to their transparent ledgers. This transparency exposes order details to all, enabling searchers and builders to reorder transactions for profit, often at the expense of other users.
Dark pools, as financial trading venues, offer key advantages in privacy protection and censorship resistance. In dark pools, order details remain secret from third parties because each order generates zero-knowledge proofs (ZKPs), reducing public disclosure. This structure is particularly attractive to large and institutional investors, protecting their strategies from competitors or market manipulators. Additionally, this design helps resist MEV, as transaction sequence and details are not public, reducing opportunities for reordering.
However, these advantages may diminish when transactions interact with public contracts or use shared sequencers, potentially exposing transaction data and creating MEV opportunities. Nevertheless, for large and institutional investors seeking privacy and censorship resistance—especially when their trading requires high confidentiality—dark pools remain an appealing option.
Tools like Tornado Cash have enabled anonymous on-chain financial activities, but they have also been exploited by criminals for money laundering. Tornado Cash’s smart contract addresses were added to the OFAC sanctions list due to non-compliance. The U.S. Office of Foreign Assets Control (OFAC) maintains a Specially Designated Nationals (SDN) list to sanction non-compliant individuals and entities. Non-compliant protocols risk having their transactions excluded from blocks. As of February 23, 2024, 45% of blocks underwent OFAC screening. This censorship-resistance issue affects not only block producers but also validators and relays, who may selectively ignore certain transactions or blocks.
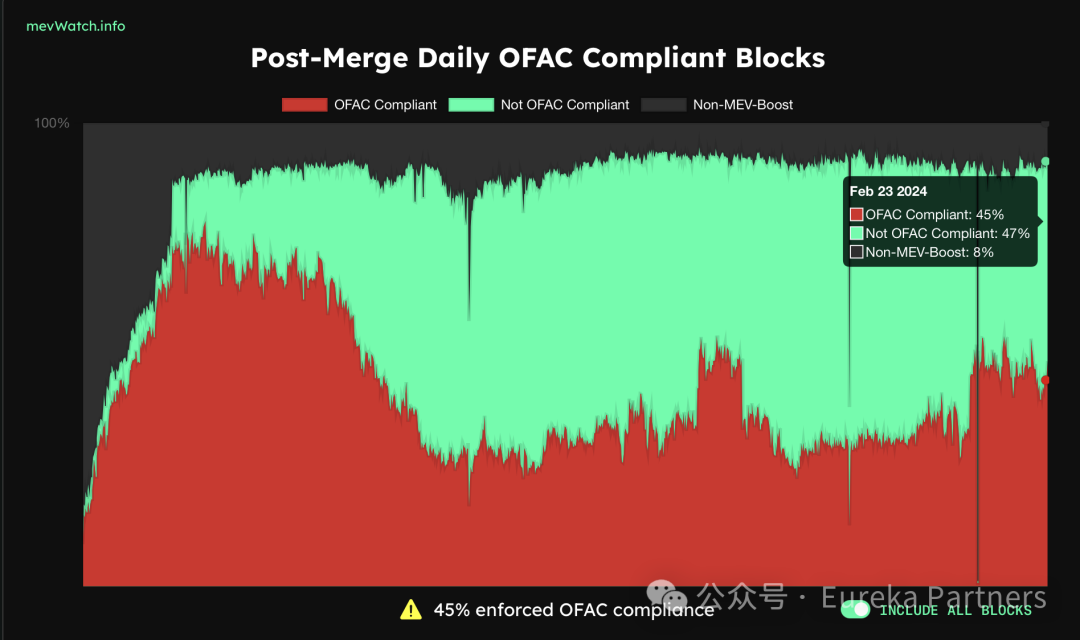
Percentage of Blocks Subject to OFAC Screening
Following the ban on Tornado Cash due to non-compliance, a demand vacuum emerged for compliant privacy solutions. To meet this need, newer dark pool projects must offer privacy protection while avoiding similar regulatory risks. We believe an effective approach is integrating verified KYB/KYC processes, ensuring user legitimacy and mitigating regulatory exposure. Regulation often lags behind technological advancement, making privacy projects prone to misuse for illicit activities. Ensuring project safety and legality requires proactive compliance with regulations.
3 Competitive Landscape & Project Analysis
Between 2010 and 2022, dark pool projects were limited and lacked broad public awareness. However, advances in privacy-enhancing technologies like Zero-Knowledge Proofs (ZKP) and Multi-Party Computation (MPC) have spurred innovative technical solutions in the space. These developments brought dark pools back into the spotlight in 2023. Despite ongoing technical complexity, the number of projects remains relatively small. Below are several relatively mature examples.
1. Renegade, founded in 2022, is a decentralized dark pool based on an MPC-ZKP architecture, designed specifically for institutional investors conducting large trades. Renegade uses a peer-to-peer network and MPC for order matching, and ZK-SNARKs to ensure transaction details remain anonymous during verification. It also employs a midpoint execution mechanism, guaranteeing all trades settle at the real-time mid-price of aggregated centralized exchanges to avoid slippage. Its default anonymous cross-trading feature, combined with interest indicators, enhances comprehensive price discovery and optimizes liquidity.
2. Penumbra is a decentralized trading platform built within the Cosmos ecosystem, offering a dark-pool-like environment where users can trade privately. Through a private delegation mechanism, Penumbra combines privacy protection with POS (Proof-of-Stake) consensus, enabling staking derivatives, tax-efficient staking, and private voting for on-chain governance. Connected to the Cosmos ecosystem via IBC (Inter-Blockchain Communication), Penumbra acts as an ecosystem-wide dark pool, enabling private transactions in any IBC-compatible asset. Users can also swap assets via ZSwap, a private DEX supporting sealed-bid batch auctions and concentrated liquidity akin to Uniswap-V3.
3. Panther is a cross-chain DeFi platform combining zero-knowledge technology to deliver a solution that is both regulatory-compliant and privacy-preserving. Users deposit digital assets into Panther’s Multi-Asset Shielded Pools (MASPs) and receive zAssets at a 1:1 ratio. Through the Zswap module, Panther connects to other DeFi protocols, aggregating quotes for users. During trades, Zswap creates an encrypted escrow contract, enabling asset swaps without revealing transaction details. This design allows assets to coexist in diversified pools, maintaining data heterogeneity and making user tracking and de-anonymization extremely difficult. Panther’s shielded pools leverage ZK SNARKs and ZKP technology to ensure transaction privacy and compliance.
4. Railgun is a ZKP-MPC privacy system designed for Ethereum, BSC, Polygon, and Arbitrum, utilizing zero-knowledge (ZK) encryption and MPC for trusted setup ceremonies. It allows users to execute smart contract and DeFi operations while preserving transaction privacy. When a user submits a transaction via Railgun, an Adapt Module smart contract automatically handles private balance shielding/unshielding, validates order validity, then relays find optimal rates across aggregated DEX liquidity, finally re-shielding the assets to preserve user anonymity. This workflow applies not only to asset swaps but also extends to other DeFi transaction types.
4 Technical Deep Dive: Singularity’s Approach to Private Transactions
Understanding Private Transactions
Understanding private transactions involves considering two aspects: transaction parties and transaction details, distinguishing between anonymity and hiddenness.
A typical transaction includes the following elements:
-
Transaction Parties: The sender (Trader A) and receiver (Trader B).
-
Transaction Details: Specifics such as amount, number of sub-transactions, transaction hash, etc.
Private transactions can be categorized based on visibility to third parties:
-
Anonymous Transactions: In anonymous transactions, the sender and receiver addresses are unknown to third parties. Except for the two involved parties, no one else can identify the participants. For example, Tornado Cash is a privacy protocol that achieves anonymity by obfuscating transaction paths.
-
Hidden Transactions: In hidden transactions, although sender and receiver addresses are visible, the specific transaction details are concealed. Information such as amount, sub-transaction count, and hash remains hidden from third parties. This can be achieved using technologies like Zero-Knowledge Proofs (ZKPs). For instance, Zcash is a privacy coin that hides transaction details using zk-SNARKs.
Singularity Architecture Overview
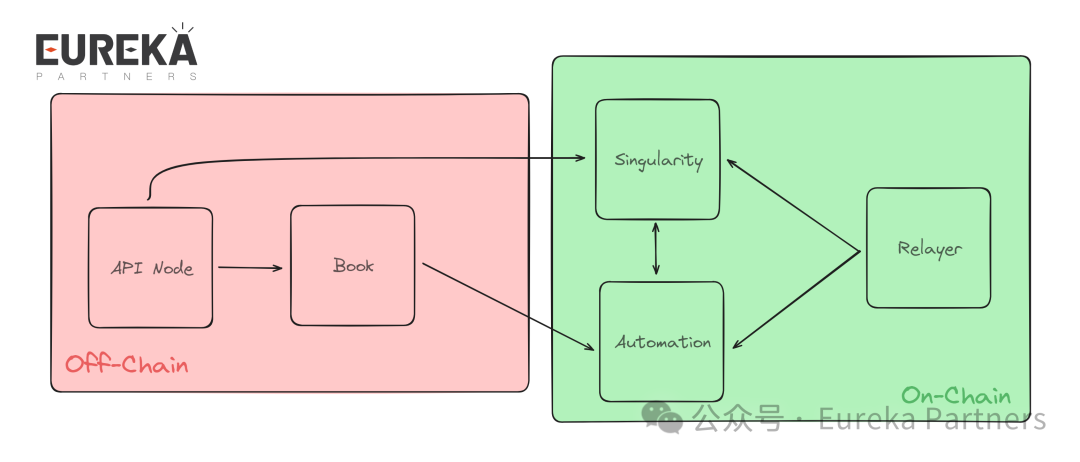
Singularity Architecture Diagram
The overall structure consists of five main modules:
1. Singularity
This is the primary smart contract interface for users, responsible for expressing and executing ZK circuit logic. It hides ETH/ERC20 token balances and transaction histories to achieve anonymity and conceal transaction content. Acting as a liquidity pool aggregating all assets from all types of traders, its name derives from a unique characteristic: to all observers, all protocol transactions appear to originate from this single smart contract, providing multidimensional privacy.
In the Singularity protocol, ZK Notes serve as the basic unit of transactions, containing critical information such as asset type, amount, and owner-related encrypted identifiers. These Notes are designed for high privacy, ensuring trader identity and asset details are well protected.
Each Note includes the following key fields:
-
Asset Type: Indicates the type of asset involved, such as a cryptocurrency token or other digital asset.
-
Amount: Specifies the quantity of assets in the Note, determining the transaction value.
-
Rho (Random Value): A randomly generated field enhancing privacy by preventing external tracking and analysis.
-
Schnorr Public Key: Used for encrypted signatures and identity verification, ensuring only authorized users can perform valid transactions.
Additionally, each Note generates a corresponding Nullifier using a cryptographic hash function that takes the Note’s random value and public key as inputs. This design provides extra security, ensuring only legitimate authorized users can operate or spend the Note.
Note Storage and Addition
In the Singularity protocol, all Notes are appended to an append-only Merkle tree, with the root of the updated tree permanently stored. This ensures transaction integrity and security, preventing tampering or corruption.
For example:
Suppose Alice, a Singularity user, deposits 1 ETH into the Singularity contract. This transaction is recorded as a Note and appended to the current Merkle tree. The Merkle root is computed from this single Note.
Later, Bob deposits 0.5 ETH into the contract. His transaction is also recorded as a Note and appended to the Merkle tree, updating the root.
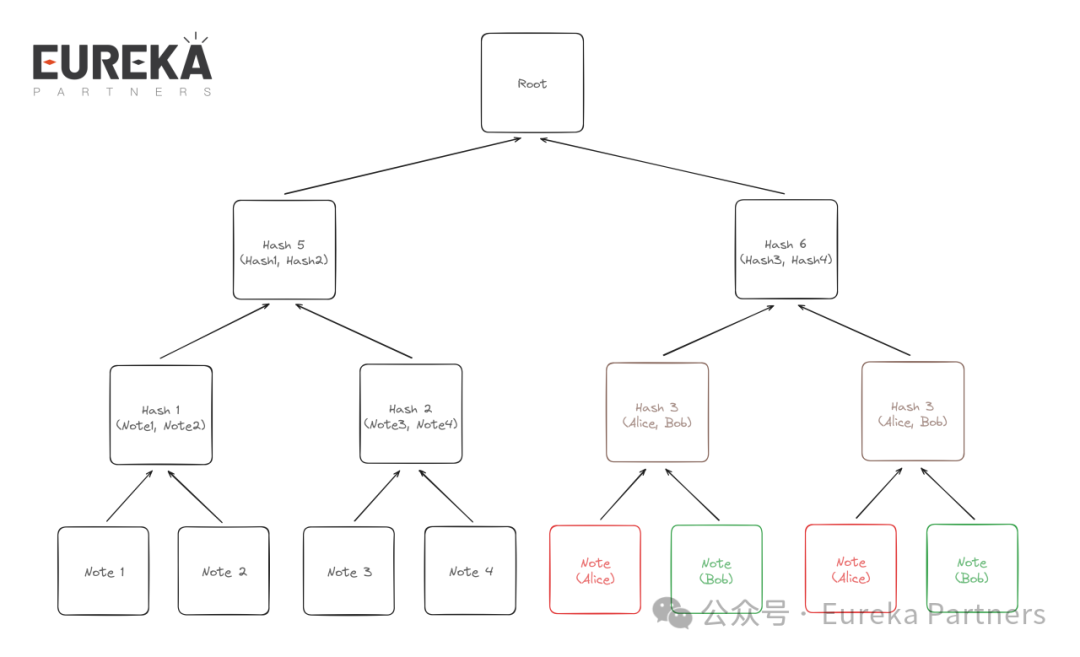
Note: In cases with an odd number of Notes, the diagram duplicates and hashes two separate Notes to generate the Merkle root.
As more users transact, each new Note is added sequentially to the Merkle tree. Every user’s transaction history is preserved in the same structure, and the integrity of the entire history can be efficiently verified by computing the Merkle root hash. Since the tree is append-only, previously added Notes cannot be modified or deleted, ensuring data security and immutability.
Note Transaction Verification
When a trader spends a Note, they must reveal the corresponding Nullifier and provide evidence within a zero-knowledge proof to verify its association with the Note and prove the Note’s existence in the Merkle tree. The smart contract verifies the Nullifier’s uniqueness and the proof’s validity to ensure transaction legitimacy and security.
For example:
Suppose Alice owns a Note representing 1 ETH deposited into the Singularity contract, with a Nullifier "AAA123". Now she wants to spend these funds, so she must provide "AAA123" as the Nullifier and use a zero-knowledge proof to demonstrate two things:
-
Prove that "AAA123" is linked to the spent Note—i.e., the funds originate from this Note.
-
Prove that the Note exists in the Merkle tree—i.e., it was previously deposited and has not been altered.
The smart contract verifies Alice’s provided Nullifier and proof, checking uniqueness and validity. Only upon successful validation will the contract execute the transfer to her designated recipient, ensuring transaction legitimacy and preventing fraud.
Below is a pseudocode implementation of the above logic:
// Pseudocode
pragma solidity ^0.8.0;
contract SingularityContract {
mapping(address => mapping(bytes32 => bool)) private invalidValues;
mapping(bytes32 => bool) private merkleTree;
// Deposit operation: deposit funds into Singularity contract
function deposit(bytes32 noteHash, bytes32 invalidValue) public payable {
require(msg.value > 0, "Deposit amount must be greater than 0");
// Add Note to Merkle tree
merkleTree[noteHash] = true;
// Store nullifier
invalidValues[msg.sender][noteHash] = true;
}
// Spend operation: validate nullifier and proof, execute transaction
function spend(bytes32 noteHash, bytes32 invalidValue, bytes memory proof) public {
// Verify that provided nullifier matches stored value
require(invalidValues[msg.sender][noteHash], "Invalid value does not match");
// Verify Note existence in Merkle tree
require(merkleTree[noteHash], "Note does not exist in the Merkle tree");
// Perform zero-knowledge proof verification
require(_verifyProof(noteHash, invalidValue, proof), "Proof verification failed");
// Execute transfer to recipient
// Transfer logic omitted
}
// Zero-knowledge proof verification function
function _verifyProof(bytes32 noteHash, bytes32 invalidValue, bytes memory proof) private view returns (bool) {
// Actual ZKP verification would occur here
// Verification process omitted
// Return true if proof valid, false otherwise
return true;
}
}
2. Book
Book leverages Fully Homomorphic Encryption (FHE) to build a fully private off-chain order book, providing traders with a secure and reliable trading environment.
Within the Book system, a group of special FHE nodes—called Bookies—play a crucial role in collectively managing the order book. The matching process includes:
API nodes encrypt orders to ensure content confidentiality, then Bookies use FHE protocols to perform matching calculations while preserving information secrecy.
Matching results are published, but original order contents remain private to protect trader confidentiality.
Matched traders can directly communicate and settle via the Swap function in the Singularity contract. Traders failing to settle face reputation penalties.
To ensure stable operation, Book implements a majority-rules incentive mechanism requiring Bookies to stake tokens:
A majority-decision mechanism among Bookies resolves discrepancies in encrypted order matching, preventing malicious behavior.
Token staking prevents Sybil attacks and incentivizes Bookies to fulfill their duties, ensuring system integrity.
Identity and reputation management are central innovations in the Book system:
Each anonymous identity carries a reputation score reflecting historical settlement probability, while preserving identity privacy.
Traders can set reputation thresholds to filter counterparties, enhancing trade safety and reliability.
Traders failing to settle face reputation penalties, which also affect their counterparties.
Example: Suppose Alice wants to buy 1 ETH.
-
Order Submission: Alice submits a buy order for 1 ETH at $2000 USDT.
-
Order Matching: The Book system finds Bob, willing to sell 1 ETH for $2000 USDT.
-
Trade Confirmation: Alice and Bob confirm their orders are matched.
-
Settlement: Alice pays Bob $2000 USDT and receives 1 ETH. The Singularity system updates their balances.
-
Reputation Management: If Bob fails to complete the trade or engages in bad behavior, his reputation decreases. Suppose Bob has a reputation score of 5, indicating reliability. But if he repeatedly cancels orders or manipulates the market, his score may drop by 1 point to 4, raising barriers for future trades.
3. Automation
Automation is a protocol-integrated AMM-DEX where Book serves as a backup liquidity provider. Because traders deposit funds via Singularity—which is anonymous—the funds in Automation are also anonymous. This protects trader identities from public exposure.
Traders can withdraw funds from Automation to the Singularity contract at any time. This flexibility allows free fund management and withdrawals when needed. Likewise, since the Singularity contract is anonymous, the withdrawal process preserves trader anonymity.
For orders unmatched in Book, Automation provides matching to boost liquidity. This ensures unmatched orders are still processed, enabling continued trading. By adding liquidity, Automation improves overall protocol efficiency and user experience.
4. Relayer
Relayers play a vital role in Singularity by submitting meta-transactions on behalf of users and paying Gas Fees. This design protects user anonymity—since Gas Fees are paid on typically public base-layer blockchains, if users paid fees themselves, their identities could be exposed.
Relayers submit meta-transactions, which are natively verifiable and tamper-proof, ensuring transaction integrity. To prevent malicious behavior, the system features a trustless relayer network—anyone can run a relayer without staking.
User-submitted transactions and associated fees are public and paid to relayers as compensation. This creates a rational system where relayers accept profitable transactions. Even if malicious relayers exist, as long as at least one honest relayer operates, system integrity is maintained. Of course, traders may choose to run their own relayer and pay Gas Fees, though this sacrifices some privacy.
5. API
The API serves as the interface node for user-protocol interaction. Through the API, users can generate and submit proofs to the Singularity contract, manage Book orders, monitor Book for matches, negotiate settlements on the Singularity contract, and interact with Relayers.
Private Transactions
Based on the above architecture, the previously mentioned private transactions can be realized:
▪ Anonymous Transactions (via Automation)
When trading via Automation, traders must deposit funds, exposing the deposit amount. Just like depositing into Singularity, third parties may observe transaction details. Thus, Automation trades sacrifice detail concealment.
Note that when Book fails to match a trader, although their order may enter the Automation pool (appearing to expose the trader’s address), trader anonymity is preserved because the liquidity source is Singularity.
▪ Anonymous + Hidden Transactions (via Singularity Settlement)
When settling via Singularity, regardless of how price discovery or intent matching occurred, the final settlement ensures both anonymity and concealment. The Singularity contract holds and transfers funds, achieving "making public pools dark."
5 Dark Pool Trading: Singularity’s Implementation
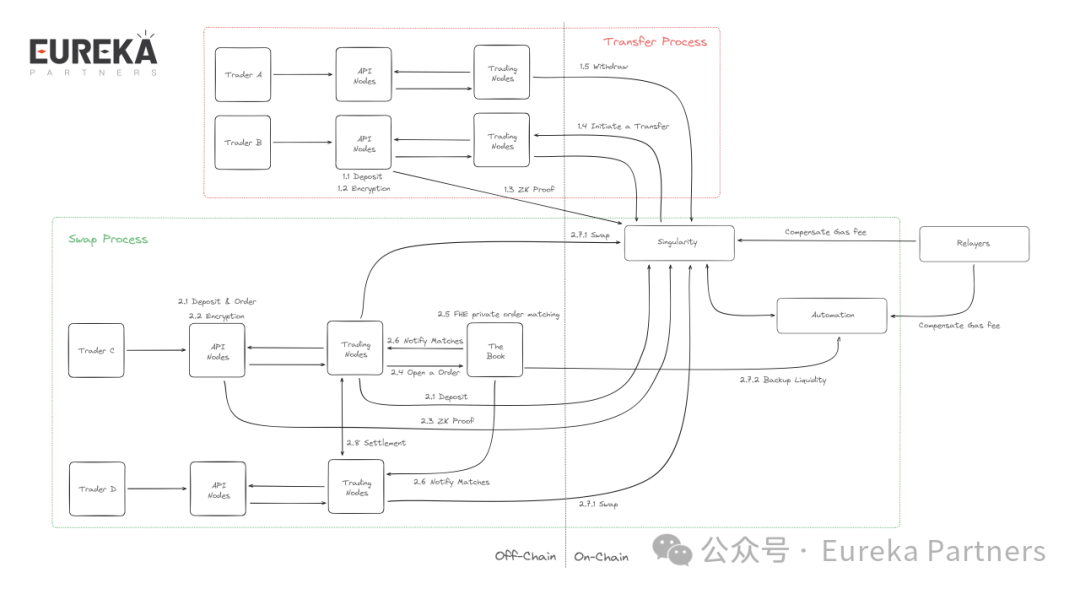
Singularity Transaction Flow
As a trading platform for large institutions and professional traders aiming to avoid market impact, dark pools primarily serve two transaction needs: Transfer and Swap. Below we detail Singularity’s implementation of these two types based on the diagram above.
Note: API Nodes and Trading Nodes in the diagram belong to the same node; they are separated here for clarity.
1. Transfer Transactions
Transfer transactions mainly occur between two Trader nodes. Define the receiving trader as Trader A and the sending trader as Trader B. Their transaction flow is as follows:
1) Before trading, Trader B must deposit funds into the Singularity contract. Trader B calls the API to encrypt this deposit, generating a ZK Proof (the aforementioned ZK Note) submitted to the Singularity contract to verify the deposit.
2) After depositing, Trader B initiates a Transfer transaction via the API, again in the form of a ZK Note sent to the Singularity contract.
3) Upon receiving Trader B’s Note, the Singularity contract locates Trader A based on the content. Trader A can then withdraw the transferred amount from the contract.
Here, interactions between nodes and the contract occur via ZK Notes using a UTXO model, which inherently provides privacy and anonymity compared to account-based models. This method ensures only the initiator knows transaction details, while externally, it appears as if only an address interacted with the Singularity contract—key details like recipient address or amount remain undetectable.
2. Swap Transactions
Swap transactions are more complex than Transfers due to counterparty discovery. Define the initiating trader as Trader C and the matched trader as Trader D. Their transaction flow is as follows:
1) Similar to Step 1 in Transfer, Trader C deposits funds into the Singularity contract and simultaneously submits an Order to the Book node via the API.
2) The Book node, acting as an off-chain order book, attempts to match different Orders under FHE (Fully Homomorphic Encryption) without accessing specific order details.
a. On successful match, the Book node notifies both traders to proceed.
b. On failure, the Book places the corresponding funds into the on-chain Automation pool as backup liquidity. This resembles putting spare cash into a money market fund; later unmatched trades first draw from Automation, resorting to external DEXs like Uniswap via the Singularity contract only if Automation lacks sufficient funds.
After finding a counterparty and negotiating Swap terms, traders sign the transaction details. Either party can then construct a zero-knowledge proof using these signatures, enabling ownership transfer of Notes without requiring both parties to be online. Note: To preserve privacy, Swap transactions are still executed through the Singularity contract.
Thus, we see that Singularity primarily leverages ZK and FHE technologies to achieve transaction privacy and anonymity. ZK enables only the initiator to know transaction details while allowing others or the contract to quickly verify validity. FHE allows Book nodes to compute matching trades without accessing specific data, and notifications do not reveal original details—traders only learn whom they traded with, not the asset type or amount.
6 Summary and Evaluation
The fact that OTC markets account for nearly 70% of total cryptocurrency trading volume underscores the massive user demand for private transactions in Web3. Yet the privacy transaction space still faces numerous challenges: meeting regulatory requirements, executing trades without revealing user or transaction details, preventing counterparty malfeasance, etc. Decentralized dark pools like Singularity offer innovative solutions, leveraging privacy technologies and smart contracts to deliver higher levels of privacy and censorship resistance while reducing reliance on centralized entities. These platforms support anonymous large trades and can integrate with compliance services to create decentralized yet regulation-compliant environments. Therefore, for the dark pool sector, we believe the following four dimensions warrant close attention:
▪ Technology Architecture
ZKP, MPC, and other privacy-enhancing technologies are foundational to the dark pool sector, enabling transaction validity verification without revealing details. Many current protocols rely heavily or entirely on Multi-Party Computation (MPC), which has two major drawbacks: low computational efficiency and protocol complexity. MPC requires proving and verifying zero-knowledge proofs (ZKPs) within the MPC environment—a computationally intensive task. Additionally, MPC often demands stable network connections, difficult to maintain in a globally distributed network. Together, these factors make fully MPC-based protocols impractical for large-scale applications like order-matching engines.
▪ Anonymity and Privacy Protection
Regulation is an unavoidable topic in the privacy space. Achieving full user and transaction anonymity while providing sufficient privacy protection remains challenging—especially for users wishing to engage with compliant capital. Clearly, dark pool projects urgently need to integrate KYB/KYC processes, proactively embrace regulation, and implement measures to prevent leakage of KYC/KYB data to ensure platform legality and user trust.
▪ Liquidity & Fund Security
Liquidity is a critical factor for dark pool operations. Ensuring sufficient trading volume and fund security is essential—not only for efficient order matching but also for enhancing trader anonymity and participation willingness. In dark pools, fund anonymity increases with pool size, as more potential depositors make tracing specific ones harder. Under liquidity scarcity, many order-book-based protocols face limitations in peer-to-peer matching due to insufficient available liquidity. Beyond order books, innovative AMM mechanisms and integration with more DeFi applications across public chains may be effective expansion paths.
▪ Scalability
Ensuring strong scalability to handle growing user numbers and transaction volumes is essential for dark pools. If a dark pool faces a surge in LPs but cannot match corresponding orders, it risks losses. Therefore, during design, considerations around settlement layers, technical architecture, and ecosystem roadmap must accommodate rising demand—especially as regulatory frameworks evolve, and institutional capital enters, catching poorly prepared platforms off guard.
Dark pool trading, with a proven history in traditional finance and unchallenged viability, still holds immense market demand and growth potential. Traditional dark pools face trust risks from centralized brokers, whereas Singularity, as a decentralized dark pool project, innovatively adopts a "dark pool + making public pools dark" model to solve pain points like centralization dependency, inadequate privacy, and weak censorship resistance.
Unlike previous privacy transaction projects, Singularity offers both asset privacy and DeFi trading capabilities. While countless trading aggregators exist today, few possess distinctive designs with user stickiness. As a privacy layer for public pools, Singularity first addresses institutional and whale trading pain points, preserving informational asymmetry. Compared to current privacy solutions, the dark pool (privacy layer) design naturally supports “keeping money in the pocket”—if traders frequently move funds in and out, privacy loses meaning, equivalent to self-disclosure. Hence, most funds tend to remain in the dark pool for extended periods before withdrawal, benefiting TVL stability and user confidence.
Join TechFlow official community to stay tuned Telegram:https://t.me/TechFlowDaily X (Twitter):https://x.com/TechFlowPost X (Twitter) EN:https://x.com/BlockFlow_News

















