
Fixing Social Login in Web3: zkWaaS (Zero-Knowledge Wallet as a Service)
TechFlow Selected TechFlow Selected

Fixing Social Login in Web3: zkWaaS (Zero-Knowledge Wallet as a Service)
By enabling private logins and private transactions, zkWaaS provides a direct solution to the privacy issues posed by transparency.

Social login functionality in dApps—automatically creating embedded wallets for end users—has undergone a journey from rejection to experimentation, partial adoption, and is now gradually becoming a standardized configuration across Web3. From DeFi and RWA to Web3 gaming, WaaS (Wallet-as-a-Service) products featuring social login are increasingly visible across all sectors.
This evolution reflects a broader shift in product development philosophy—from the purist crypto-punk mindset toward a demand-driven, product-manager-oriented approach.
Particle Network, as a core infrastructure provider of modular smart WaaS, has been one of the biggest beneficiaries of this transformation.
However, as central practitioners within the WaaS industry, we also more readily observe that during the use of traditional WaaS products, compromises around user privacy and data protection emerge among three parties: dApp developers, WaaS providers, and end users.
These compromises manifest in two key aspects:
-
When an end user creates a non-custodial, dApp-embedded wallet via social login, they must share their social login data with the WaaS provider, which then synchronizes part of this information with the dApp developer;
-
Even if a user only performs small on-chain transactions using a newly created wallet via social login within a dApp, chain analysis can still link these activities back to their primary wallet.
The potential consequence? The mapping between a user’s off-chain social identity and on-chain activity becomes fully traceable:
You are Zhang San, your Gmail is zhangsan@gmail.com, you hold $100,000 in crypto assets distributed across 100 addresses.
If we apply traditional mobile internet logic here, the WaaS provider becomes the beneficiary once again—because it is the only entity possessing a complete mapping of users’ on-chain and off-chain identities and assets.
After 12 months of growth, Particle Network’s Modular Smart WaaS has become the industry leader in both number of end users and partnered dApps.
Now comes a critical decision point: Do we follow the well-trodden path of Web2—prioritizing efficiency and convenience to onboard the next billion users into Web3, but at the cost of allowing third parties to possess user data and build data moats? Or do we uphold the foundational principles of Web3—reaffirming users’ sovereignty over their assets and data—and onboard the next billion users the Web3 way?
We choose the latter.
Today, we launch Zero-Knowledge Wallet-as-a-Service (zkWaaS), featuring two core components: private login and private transactions.
By integrating zero-knowledge technology, users can now create and log into non-custodial, dApp-embedded wallets via social login without exposing any personal information to third parties. Furthermore, through the use of smart stealth addresses, individual on-chain transaction records cannot be linked to other wallet addresses held by the same user.
In the following sections, my colleagues Vijaykumar Singh and Peter Pan will dive deeper into the product design of our zkWaaS.
Balancing Usability and Privacy with Zero-Knowledge Technology
Although WaaS tools can be fully self-custodial when properly implemented—ensuring users’ assets remain secure—it is also true that they expose certain personal information to third parties during account creation and on-chain transactions. If mismanaged, this data can be pieced together to reveal which other wallets, CEX accounts, or assets a particular user owns, significantly undermining their data autonomy.
Blockchain privacy itself presents inherent challenges. The verifiability and reliability of blockchains stem partly from their transparency—anyone can audit on-chain data at any time. Creating a blockchain that is by default private, efficient, scalable, and yet verifiable and trustworthy is nearly impossible. A few solutions aiming to achieve this have struggled with adoption due to incompatibility with existing ecosystems, fragmenting liquidity and interoperability further.
Within these constraints, zero-knowledge (ZK) technology emerges as a much-needed solution—one that is fully compatible with and integrable into current ecosystems. In short, ZK allows one party (the prover) to prove knowledge of a fact (e.g., identity, ownership) to another party (the verifier) without revealing the underlying data. For example, sending an Ethereum transaction implicitly reveals the sender’s balance, transaction history, and sometimes identity. ZK is already used in scalability solutions like zkEVMs to boost throughput, and privacy-focused projects like Zcash use it to obscure balances and transaction histories.
Introducing ZK into WaaS means users can generate a non-custodial on-chain wallet from their social identity, while no observer can learn the connection—let alone identify which wallet belongs to whom. ZK also brings additional benefits, such as regulatory compliance. Its privacy model—with voluntary disclosure mechanisms and exclusionary privacy sets—is inherently regulation-friendly.
Thus, integrating zero-knowledge proofs into WaaS solves two persistent problems:

Let’s now explore how zkWaaS achieves this, along with its implications.
A Quick Summary of the Benefits of Particle Network’s zkWaaS
Particle Network’s zkWaaS achieves two main goals:
-
Protecting user identity so that personal information is never exposed during wallet creation, and on-chain addresses cannot be linked to their owners—enabling private login;
-
Working seamlessly with other Particle Network components (such as Omnichain Account Abstraction) to enable private transactions.
Beyond the obvious advantages—private transactions and exclusive user control over identity—there are several derivative benefits of zkWaaS:
-
For developers and projects, having a reliable system that does not require handling user data saves significant overhead. Regulations like Europe’s GDPR have made strides in data privacy, but compliance demands time and effort, increasing project costs. By completely avoiding user data processing, developers save substantial resources.
-
For end users, unobservable transactions mean their strategies cannot be leaked, copied, front-run, or directly replicated.
-
Likewise, users can be confident their data won’t be sold, stolen, leaked, or otherwise mishandled—whether intentionally or unintentionally—by service operators.
While the above list is not exhaustive (privacy offers many benefits!), it should now be clear that privacy represents an absolute improvement for all participants in the WaaS framework. Let’s now examine how zkWaaS works under the hood.
How Particle Network’s zkWaaS Works
The overall design incorporates multiple components that together constitute zkWaaS. For private login, the system uses JWTs (JSON Web Tokens) as private witnesses in a zero-knowledge circuit to verify provider signatures and user claims. Particle Network also leverages Particle Chain—a proprietary zkEVM powered by the network’s native Unified Gas Token—to generate ZK proofs. This includes confidential Paymasters that pay transaction fees on behalf of users to protect their privacy.
While differing in key aspects, the overall architecture draws inspiration from Sui’s zkLogin.
Now, let’s delve deeper into how zkWaaS achieves its two core objectives.
Goal #1: Identity Privacy
To onboard users while preserving privacy, zkWaaS employs a system where users first generate a temporary key pair during the authentication process. They then use verified credentials to generate a ZK proof via Particle Chain and submit it to a verifier to complete the login.
Here is a visual representation of the flow:

Particle Network’s zkWaaS user flow.
More specifically, private login works as follows:
A) Setup
To generate the common reference string (CRS) for the Confidential Login circuit, Particle Network currently uses Groth16—but may consider zkSTARK in the future. A trusted setup generates a proving key and a verification key for each OAuth provider. Particle Network is also actively working toward a trustless setup.
B) Signing
Temporary Key Generation: When accessing their wallet, the user generates a temporary key pair. They select a maximum lifespan, determining when the key expires. The app prompts the user to authenticate via OAuth using a custom nonce constructed from randomness, the temporary private key, and the chosen lifespan. This returns a JWT containing header and payload. The JWT is sent to a salt service, which returns a unique salt—a random string—after verifying the JWT. The JWT, salt, and temporary public key are sent to Particle Chain, which generates a ZK proof attesting to the following claim:
i) The nonce was correctly formed and includes the public key.
ii) The key claim matches the JWT.
iii) The Particle address matches the key claim and salt.
iv) The OAuth provider’s signature is valid.
Alongside the ZK proof, the address seed, claim, and header are sent to the dApp.
Note: The circuit generates a zk-address for the user. The user creates and signs a transaction to obtain a temporary signature. They also send additional data including the temporary public key, signature, proof, address seed, claim, and header.
C) Verification
Two verification methods are possible:
-
On-chain verification via a smart contract on Particle Chain.
-
Decentralized verification by validators on Particle Chain, who are rewarded with Particle Network’s native token.
Verification Process:
The verifier receives the user’s data and performs the following checks:
-
Verify sender: Ensure the transaction originates from the address seed and matches the public claim.
-
Match signed user with public key.
-
Verify the ZK proof.
-
Retrieve the public key and confirm it matches the one used in the ZK proof.
D) Storage
Once authenticated, a mapping is stored on-chain to enable automatic login until the user-defined expiration period ends.
Goal #2: Private Transactions
Particle Network leverages ERC-4337 Account Abstraction (AA) to protect user privacy during transactions. The system uses confidential Paymasters to sponsor user transactions, breaking direct on-chain links. It also employs a stealth smart account mechanism to preserve recipient privacy. Additionally, Particle Network implements Guardian Accounts and user-controlled social recovery features.
The private transaction system in Particle Network’s zkWaaS is illustrated below:
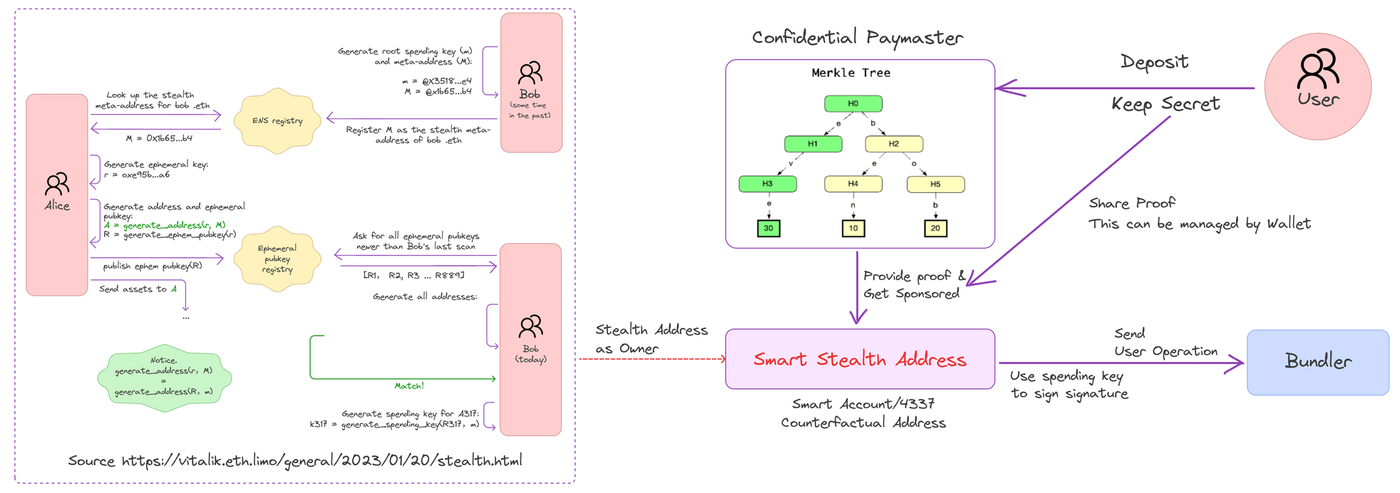
Particle Network's system for private transactions (click image to expand or open in a new tab).
The process unfolds as follows:
-
Dynamic Stealth Address Computation: At the start of a transaction, sender Alice dynamically computes Bob’s stealth address using Bob’s meta-stealth data. This step is crucial for ensuring privacy and security in subsequent steps.
-
Smart Stealth Address Calculation: Based on the dynamically computed stealth address, Alice calculates a “stealth smart account.” This specialized address serves as the destination for asset transfers, adding an extra layer of privacy and complexity.
-
Secure Stealth Address Retrieval: On the receiving end, Bob systematically scans incoming transactions for his stealth address. Once located, he generates a spending key to securely access and manage the received assets.
-
Confidential Gas Fee Deposit: To facilitate the transaction and cover gas fees, Bob deposits the required amount into the confidential Paymaster from any address. This confidential deposit ensures both transaction integrity and privacy.
-
Flexible Transaction Signing: With the spending key, Bob can now sign a UserOperation associated with the stealth smart account at his convenience. The flexibility in signing timing adds an additional security layer, allowing Bob to strategically execute the signing process.
-
Submit Proof to Confidential Paymaster: After signing the UserOperation, Bob submits the generated proof to the confidential Paymaster. This proof acts as confirmation, enabling the Paymaster to sponsor the required gas fees. This final step ensures smooth transaction execution while maintaining the highest privacy standards.
At its core, this sophisticated, multi-step process not only safeguards transaction privacy but also establishes a robust foundation for secure and confidential smart contract interactions. By seamlessly integrating ERC-4337 AA, stealth addresses, and confidential Paymasters, Particle Network demonstrates a deep commitment to transactional privacy.
Closing Thoughts
In the past, we’ve written extensively about the need for decentralized applications to compete with their Web2 counterparts. This is only possible by leveraging Web3’s unique advantages—self-ownership, self-custody, near-instant settlement—while delivering exceptional user experience. However, it’s equally important to recognize that full transparency introduces problems that Web2 solutions typically avoid.
By enabling private login and private transactions, zkWaaS directly addresses the privacy challenges posed by transparency, while further empowering users to become the sole controllers and owners of their data. Developers can leverage this powerful tool to build more compelling products for end users—whether those users are actively interested in protecting their privacy or simply want peace of mind knowing their data won’t be leaked or exploited by malicious observers.
Again, by combining zkWaaS with other core infrastructure components of Particle Network, we aim to streamline development and enable the creation of highly advanced dApps—all while delivering outstanding UX.
The interplay between Particle Network’s three pillars—Modular Smart WaaS, zero-knowledge-powered private login and transactions, and the intent-centric Intent Fusion Protocol—alongside its foundational OmniChain Account Abstraction, opens up new possibilities for developers to create innovative products and services, ultimately accelerating Web3’s evolution into a consumer-friendly mainstream industry.

Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















