Keyless wallets based on MPC, the "breakthrough contender" for Web3 entry
TechFlow Selected TechFlow Selected

Keyless wallets based on MPC, the "breakthrough contender" for Web3 entry
A revolution about the gateway to Web3 may be about to begin.
By Professor Zhou, TechFlow
"Friend, welcome to the world of Web3."
Imagine a user traveling from 2012. When you introduce concepts like NFTs, DeFi, SBTs, and decentralized identity, they would surely be amazed by the rapid progress over the past decade.
But if this time-traveler attempts to connect a wallet, only to realize they’ve lost their private key, they might be even more shocked to discover:
After ten years, our management of crypto assets and the way we use wallets remains stuck in the primitive era since Bitcoin’s inception.
Yes, the private key remains that unchanging, fragile Achilles’ heel. No matter how wallet designs have evolved over the years, dependence on private keys has not diminished at all. Lose your private key, and everything is gone forever.
Meanwhile, securely and properly using wallets has become increasingly challenging.
Looking recently, in August this year, Solana’s Slope wallet suffered a breach where private keys and recovery phrases stored on servers were leaked, resulting in over $8 million worth of crypto assets stolen. Looking back historically, a Chainalysis research report shows that as of 2021, about 20% of circulating Bitcoin had been permanently lost due to owners forgetting their private keys.
Perhaps seasoned insiders have already mastered these security lessons; but for newcomers outside the ecosystem, they immediately hit a roadblock at the entrance to Web3:
What exactly is the difference between private keys, recovery phrases, and regular passwords? Why should I copy a sequence of words onto paper? Where can I find an offline computer to store my wallet file?
For ordinary users, this is far from being a qualified, friendly, or understandable solution. Even more strikingly, the practice of exposing low-level technical details directly to users has persisted for over a decade.
What determines today’s wallet experience and usage patterns? And do we have better wallet solutions available?
As wallets serve as the primary gateway to the Web3 world—holding user identities, assets, and even reputations—the answers to these questions are deeply relevant to each of us.
This article aims to trace the evolution of wallets, compare the pros and cons of current solutions, and attempt to answer these critical questions.
From Primitive to Modern: The Evolution of Wallets
History doesn't happen overnight—it's a gradual evolutionary process.
From the early days of Bitcoin to today’s popular Web3 landscape, throughout more than a decade of industry transformation, wallets have continuously evolved in form and function.
Yet all changes are built upon a relatively stable core.
Technically speaking, a wallet is essentially a public-private key manager. The private key, generated via asymmetric encryption, grants absolute control over the wallet, address (public key), and associated assets.
Various wallet types have offered different approaches to better safeguard and manage private keys. By reviewing these approaches together, a clear history of wallet evolution emerges.
History teaches us about change. Behind each transformation lie reflections of strengths and weaknesses.
As we seek better wallet experiences, it's worthwhile to examine what has happened from past to present.
CEX-Managed: The Unnoticed Wallet
In the early days when Bitcoin was still a niche experiment, the entire industry was growing wildly.
Chaotic, fearless, and somewhat ignorant, early adopters often didn’t fully grasp the concept of wallets or private keys—their first step into crypto was likely trading on centralized exchanges.
At that time, wallets weren’t even perceived. Exchange accounts effectively played the role of wallets: users created trading accounts displaying their asset balances.
Behind the scenes, you had no idea whether those numbers truly corresponded to actual crypto holdings.
At worst, early exchanges simply displayed arbitrary figures generated within their databases; at best, they might generate a unique address per user to track incoming and outgoing transactions.
In reality, this was the earliest form of a custodial wallet.
The exchange manages your assets on your behalf. Your control over assets depends not on a private key, but on the exchange’s integrity and compliance.
The benefit? You can manage, send, receive, and trade assets easily without worrying about technical details—just remember your login password. But the flaw is obvious: if the exchange crashes, disconnects, or runs away, your assets may vanish with it.

In 2014, Mt.Gox, once dominating 70% of global trading volume, announced it could no longer process withdrawals after hackers stole 850,000 Bitcoins, eventually declaring bankruptcy. This event left a lasting shadow over the industry’s development.
When custodians make wallets invisible, so too are the risks.
Software Wallets: Facing Private Keys and Recovery Phrases
Beyond exchanges, technically inclined early users also explored alternatives.
Older readers will likely recognize the two images below. Bitcoin Core—an ancient Bitcoin wallet client—that even allows syncing the full Bitcoin ledger upon installation; MyEtherWallet—a web-based Ethereum wallet enabling address creation and private key management directly through a browser.
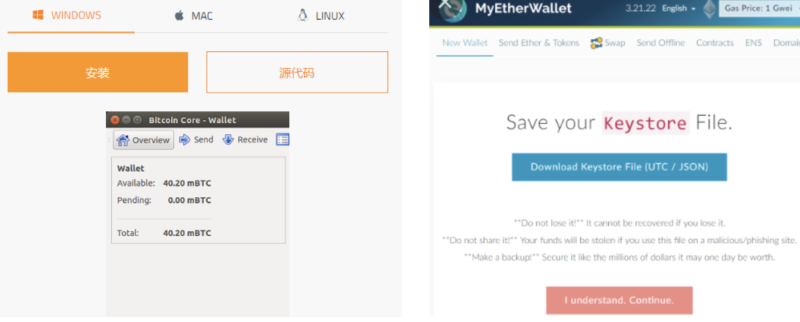
Today, Metamask’s browser extension has become far more widespread, pushing older tools out of view. Yet both belong to the category of “software wallets”:
Wallets implemented as visual software applications running locally on computers, browsers, or mobile devices.
Regardless of type, users must directly confront private keys and recovery phrases, bearing full responsibility for securing and backing them up. Some early wallets even required saving Keystore files—a JSON file encrypting the private key, which needed a password set in the wallet software to decrypt.
Private key, recovery phrase, wallet password.
Even today, many users struggle to understand the technical differences among these three. Exposing such complexity directly to users feels primitive and harsh.
But where did all this come from?
Current software wallets rely on public-private key cryptography. The private key is the ultimate gatekeeper—controlling it means controlling the assets.
When users interact directly with wallets, some UX improvements have already occurred: the public key is encoded into what users see as the “wallet address,” while the raw private key—a 64-character hexadecimal string—is hard to memorize and error-prone. Thus, as early as 2013, the Bitcoin community introduced BIP39: an algorithm converting the private key into a sequence of 12 to 24 easy-to-remember words, now known as “recovery phrases.”

Strangely enough, the private key and recovery phrase system remains largely unchanged a decade later. You still must guard your private key—never lose it, never share it—and carefully write down your recovery phrase on paper.
While self-custody empowers users to control their own financial fate, it brings unavoidable anxiety: a single point of failure—if both private key and recovery phrase are lost, everything is lost.
Moreover, because computers, browsers, and phones are vulnerable to attacks, software wallets running on them become prime targets. Safeguarding private keys becomes both psychologically stressful and operationally costly.
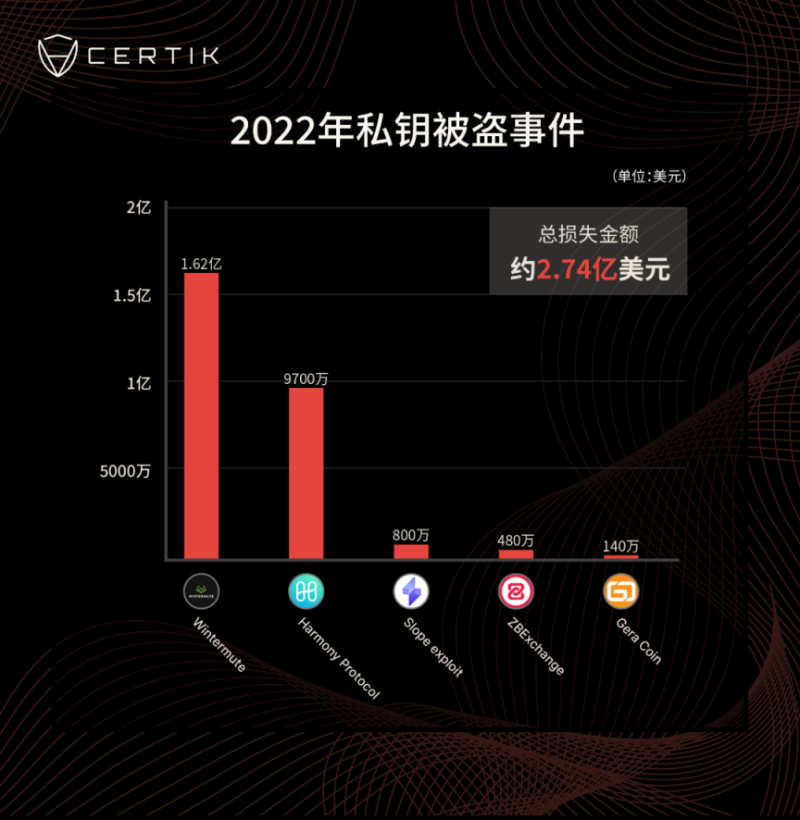
According to CertiK, losses due to private key leaks in 2022 alone totaled at least $274 million—including major players like Wintermute. If even professional market makers aren’t immune, what hope do average users have?
The legacy private key/recovery phrase system from the early days may always remain a ticking time bomb.
Hardware Wallets: The "Hard Box" and the "Hardcore"
When we worry about how to securely store private keys, hardware wallets emerged.
From a user’s perspective, a hardware wallet is a standalone physical device that stores crypto assets and connects to computers when needed.
With software wallets, private keys are usually stored on hard drives, making them susceptible to attacks. Hardware wallets store private keys directly in secure chips—plug-and-play, completely isolated from the internet.
In other words, hardware wallets create a more secure environment for storing private keys—but not without cost.
Does this remind you of something? Years ago, online banking transfers required a USB token—same idea.

As we know, USB tokens gradually faded from use, partly because their processes were cumbersome. Compared to today’s seamless mobile payments, they felt clunky and outdated.
The same applies to hardware wallets. To create a safer offline environment for private keys, users must buy dedicated hardware, learn new operations, and still securely back up recovery phrases.
In many ways, using a hardware wallet is even more hardcore than a software wallet.
This isn’t a user-friendly, mass-market solution. If you prioritize security over usability to such an extreme, it’s destined to serve only a few people in specific scenarios.
Also, hardware wallets aren’t 100% secure. As early as 2017, at DEFCON 25 in Las Vegas, a foreign tech team demonstrated how to crack a Bitcoin hardware wallet in under 15 seconds.
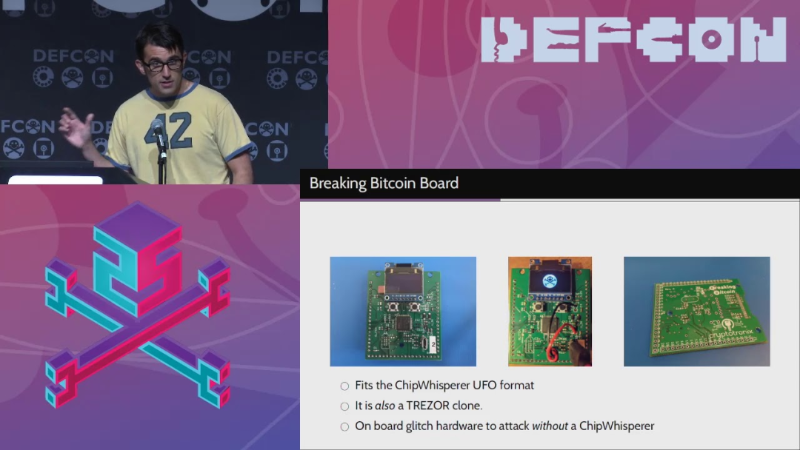
Using hardware to protect private keys doesn’t fully solve the underlying problem of private key vulnerability.
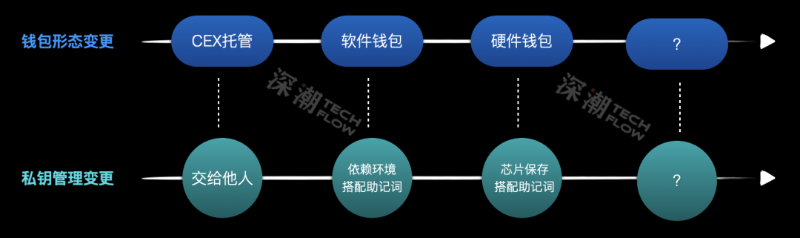
Changing Lanes, Same Bottleneck
Looking from afar to near, we see shifts in wallet ownership models, user interfaces, and hardware/software implementations, spawning various sub-sectors.
But one thing remains unchanged: private keys are still the painful bottleneck.
Giving users control over private keys is empowering yet burdensome. The single point of failure remains a psychological burden, hindering large-scale adoption, understanding, and experience by outsiders.
To make an imperfect analogy: running different races while carrying a heavy stone—if you’re afraid of dropping it, you’ll never reach your top speed.
Is there a way to break free from private key constraints and achieve more usable and secure wallet solutions?
MPC Wallets: The New Challenger
While most wallets remain trapped within the old walls built by legacy private keys and recovery phrases, others have begun breaking through from another dimension:
Eliminate private keys. Eliminate recovery phrases.
This sounds heretical. When “private key equals security” is deeply ingrained, removing private keys feels riskier.
But fear stems from the unknown. Thanks to MPC (Secure Multi-Party Computation) combined with blockchain signing, keyless MPC wallets have quietly emerged.
In the *Blockchain Dark Forest Self-Defense Manual* published by Slowmist, a well-known security auditing firm, author Yu Xian advocates for rapid adoption of MPC-based keyless solutions.

After studying MPC technology, we found that eliminating private keys isn’t counterintuitive—in fact, it naturally solves most risks caused by private keys in existing wallets.
So, what advantages does the MPC wallet solution offer, and how does the experience differ?
Given the complexity of underlying technologies, we’ll avoid excessive jargon and aim for clarity in answering these questions.
Let’s start with two familiar scenarios: wallet creation and transaction execution.
When creating a traditional wallet, you get a pair of public and private keys. The public key is transformed into your wallet address, which you can safely share. The private key stays with you and must never be shared.
Then, when initiating a transaction, you sign it with your private key—signaling “I approve this transaction.” Others can verify this using your public key (address), confirming authenticity through validation, thus marking the transaction as valid.
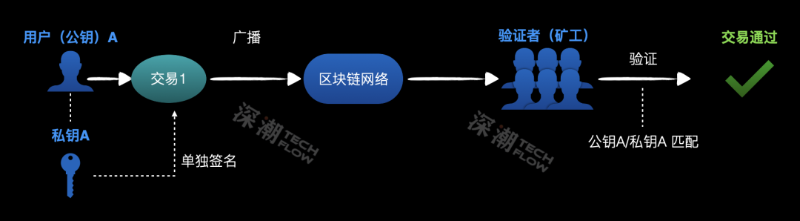
If someone obtains your private key, they can sign transactions and steal your assets.
The issue here is that traditional wallets use single-party signing, relying entirely on private key security. We recognize only the private key’s uniqueness, with no way to distinguish whether it’s held by the rightful owner or a thief.
With MPC wallets, the situation differs.
First, the wallet is jointly created by multiple parties. Suppose Party A, B, and C co-create a wallet address. Using a multi-party key generation protocol, no single private key is ever created. Instead, each party receives a fragment of the key (keyshare).
Note: None of the three holds the complete private key—only three distinct key fragments. Any single fragment cannot control the wallet’s assets, yet each corresponds to the same wallet address.
Next, during transactions, secure multi-party computation and multi-party signing work together. Parties A, B, and C each use their key fragment to sign a transaction—think of it as three signature fragments.
Like multisig wallets, you can set a threshold—for example, requiring all three signatures to authorize a transaction.
Then, MPC securely aggregates the three signature fragments without revealing any individual fragment, producing a complete multi-party signature. Others can easily verify this signature against the wallet address, confirming the transaction’s validity.
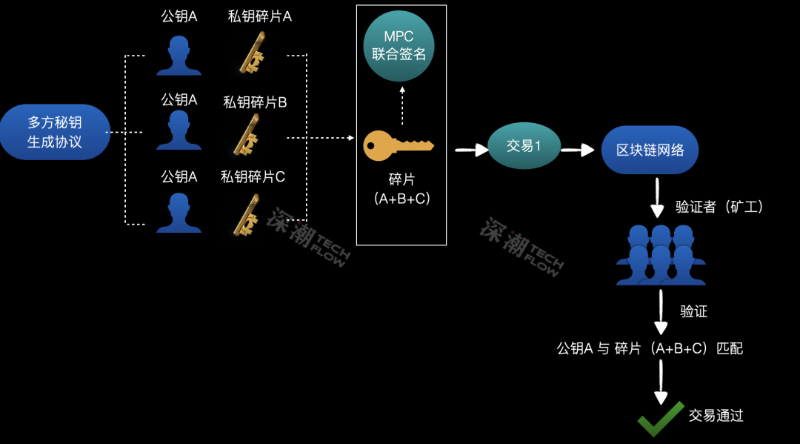
Under this MPC model, you no longer face single-point failure risks. No single private key is ever created—instead, it’s split into multiple fragments stored separately. Even if one fragment is stolen, the attacker cannot control the wallet.
Additionally, if you suspect a key fragment is lost or compromised, MPC supports key refresh: replacing old fragments with new ones across all parties. Compromised or lost fragments become useless—like reporting a lost card.
Finally, without private keys, there’s no need to memorize recovery phrases or worry about storage.
This approach fundamentally differs from current key-dependent wallets. Shifting from “securely storing private keys/recovery phrases” to “no need to store them at all” may bring massive improvements in user experience and security levels.
Reviewing wallet evolution and including MPC wallets, their handling of the persistent private key/recovery phrase issue appears more rational and secure. As such products enter commercial use and gain traction, older solutions may inevitably face disruption.
New contenders in the wallet space are breaking through the high walls of private key and recovery phrase management.
Take Bitizen as an Example: Exploring the Keyless, Phraseless Experience
If the concept feels abstract, diving into real MPC wallet products makes it clearer.
Currently, few mature, consumer-ready MPC wallets exist on the market. After comparing options across five dimensions—security, usability, censorship resistance, privacy, and multi-chain compatibility—we believe Bitizen stands out as the most balanced and comprehensive solution. Especially notable is how it elevates the Web3 wallet experience to match Web2 simplicity—without sacrificing security, privacy, or censorship resistance. It nearly perfectly fulfills all user expectations for a Web3 wallet.
Unlike traditional wallets that prompt users to write down recovery phrases, Bitizen’s setup page shows no mention of private keys or recovery phrases. From clicking “create” to completion takes less than 5 seconds—smooth and effortless. No recovery phrases, no private keys, no learning curve—ready to use instantly.

Bitizen still requires asset backup, but not via recovery phrases—instead, it uses common multi-factor authentication:
Users verify their email and complete biometric authentication, linking multiple traits to a backup file for convenient, secure recovery anytime, anywhere. Key fragments are encrypted, and the decryption key is stored in a cloud drive controlled solely by the user. Multi-factor protection ensures that compromise of any single factor won’t jeopardize overall security. For instance, even if the decryption key leaks, thieves can’t use it without matching your email and biometrics—theft becomes futile.
Moreover, Bitizen offers greater flexibility in MPC multisig design.
You can add a second device in a 2-of-3 setup: Device 1, Device 2, and Bitizen’s server each hold a fragment, and any two can jointly sign a transaction. This means you can bypass Bitizen’s server entirely, using just your two devices to co-sign—retaining full control. This adds another crucial trait beyond security and ease of use: censorship resistance.
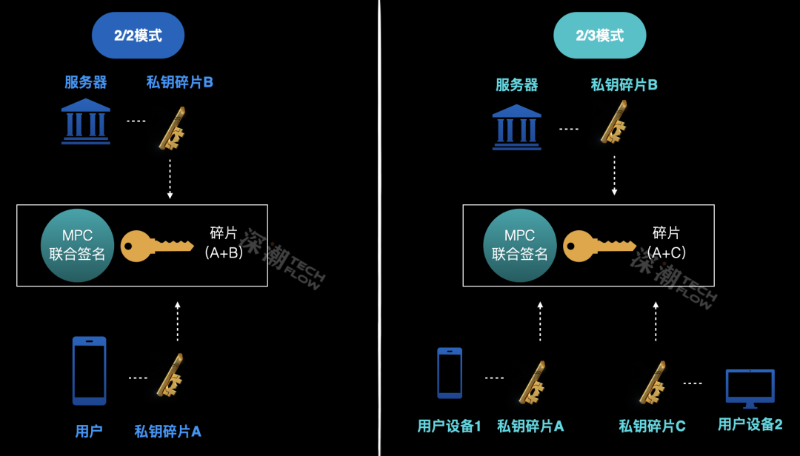
You might feel uneasy about servers, emails, biometrics, and cloud drives—they seem too centralized, non-Web3, and potentially privacy-invasive. But after examining Bitizen’s design closely, we found reality contradicts intuition.
First, these seemingly centralized elements in Bitizen are designed to be replaceable (not mandatory dependencies). Even if they fail, your asset security and accessibility remain unaffected.
Second, these components are carefully encrypted or anonymized. The data is useless to third parties—including Bitizen itself—only you can decrypt and access it, so privacy leaks are not a concern.
To quote Bitizen’s documentation: even Bitizen’s tech team cannot identify who uses the wallet; even if hackers fully compromise Bitizen’s servers, or if the servers go down, shut down, or the team disappears—your assets remain safe and accessible, and your privacy remains intact.
The subtle difference between Bitizen and Citizen seems to reflect a vision of empowering more people to become digital citizens in Web3. Yet we keep saying large-scale adoption into Web3 will take time.
Rome wasn’t built in a day, but upgrading outdated entry points is the practical path toward that vision.
As MPC-based wallets like Bitizen continue emerging, they will inevitably reshape how users enter and experience Web3. Free from private keys and recovery phrases, and without fear of server malice—this is how wallet products should truly appear to users.
A single article cannot fully cover all wallet technical principles. On October 21, we’ll host an educational event with Bitizen and other wallet projects, VCs, and industry KOLs. Over two hours, we’ll dive deeper into the technical foundations of various wallets. Interested readers are welcome to join via the link below.
https://bit.ly/3sbCPWQ
Perhaps as Mark Twain said, history doesn’t repeat itself, but it rhymes. Behind every successful product lies a similar rhythm of meeting user needs.
As the legacy private key/recovery phrase system faces the rising wave of MPC wallets,
the balance hasn’t clearly tipped—yet a revolution at the Web3 gateway may already be underway.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News