In the crypto world, you need a more resilient investment philosophy
TechFlow Selected TechFlow Selected

In the crypto world, you need a more resilient investment philosophy
Through the jungle, see order and the long term.
By: Daii
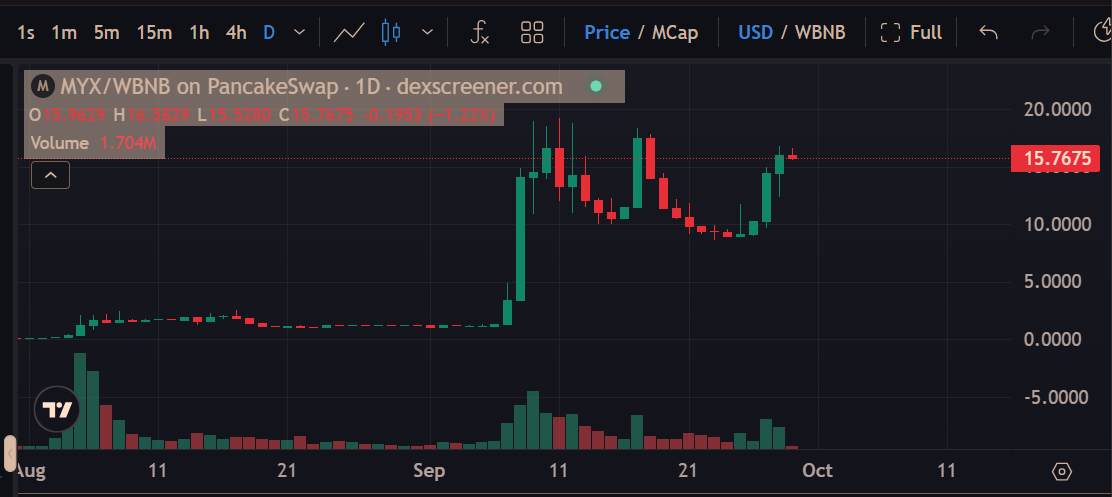
First, let's look at a recent MYX show.
In early September 2025, its price rocketed across multiple exchanges, surging as high as over ten dollars within a week, with media amplifying the hype.
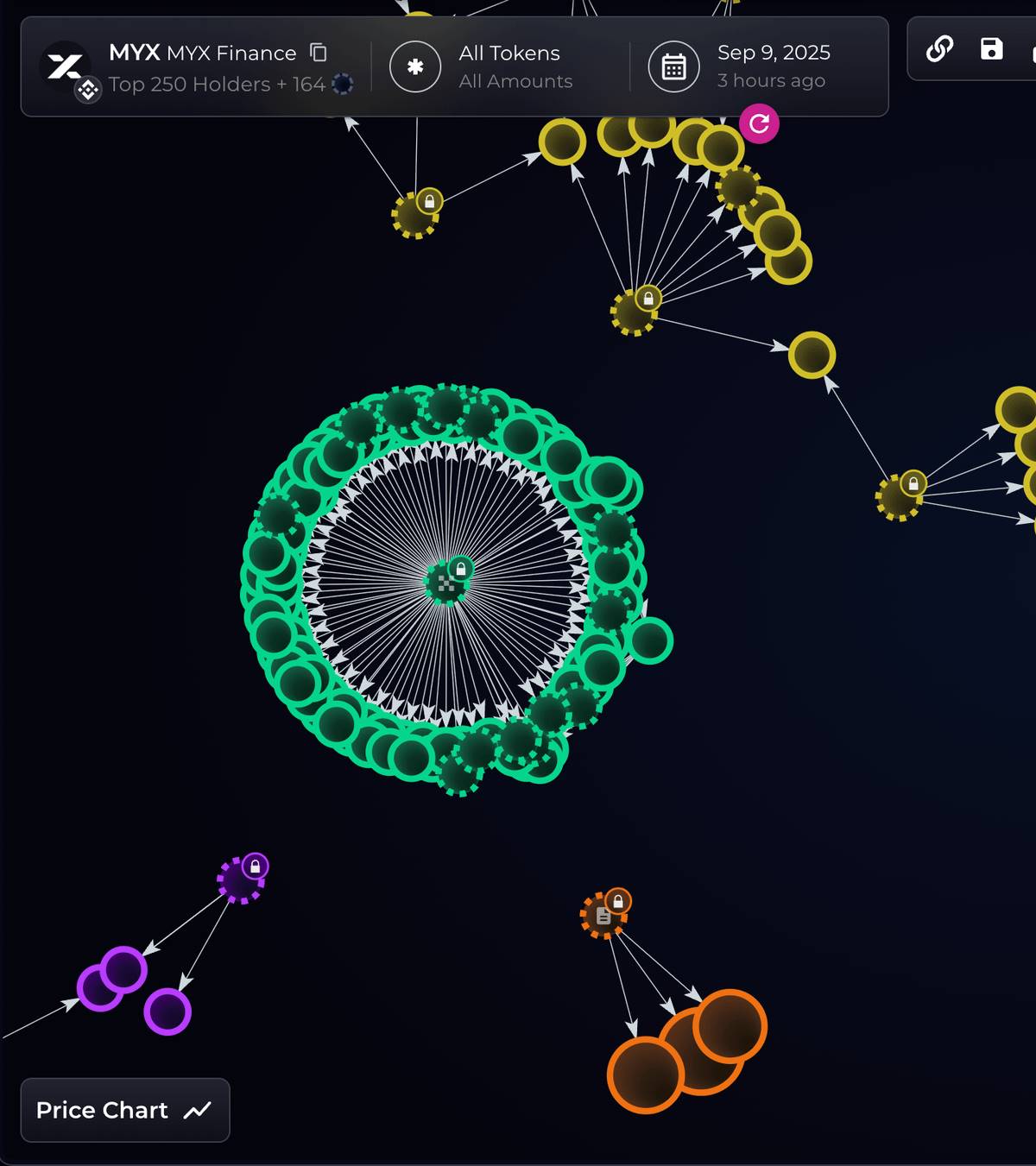
Shortly after, on-chain data team Bubblemaps posted a series of long threads on X (formerly Twitter): "A single entity used 100 newly funded wallets to claim approximately $170 million worth of tokens from the MYX airdrop," providing detailed on-chain tracking evidence (starting September 9).
Industry media and news platforms then picked up the story, causing it to escalate rapidly. Ordinary users also shared their direct experiences across different platforms:
-
User "Arfath 29" on Binance Square posted a warning: "The top 5 addresses hold 72.63% of the total supply—once they dump, retail investors will be left holding the bag." (Mid-September, posted on Binance Square). This isn't technical jargon; it’s plain language: a few large holders call the shots.
-
User "Lenora Opatz yMnL" on Binance Square was even more blunt: "Many people shorting this crap coin lost all their previous gains, like liquidity being drained every hour—they can’t even escape." (Mid-September, posted on Binance Square). This reflects the real sense of being trapped that retail investors feel amid extreme volatility.
The next day and the day after, media began systematically summarizing the entire incident: some articles described this price surge as a coordinated move of “spot pump – squeezing short contracts – offloading during peak momentum”; some even correlated the unlocking of 39 million tokens with the price peak, noting this was the “window of highest liquidity and easiest distribution.” Dates, magnitudes, and liquidation amounts were all quantified.
The pump-and-dump scheme became clear to everyone. In fact, the mechanics behind this short squeeze were obvious:
Low circulation + spot price pump → index shift → contract liquidations → forced buying pushes prices higher.
The core principle is: small capital in spot markets leverages massive derivatives exposure.
Once the price crosses several key levels, the liquidation engine automatically buys on behalf of longs, creating a feedback loop of “price rise → liquidation → further price rise,” systematically wiping out shorts. This was precisely the backdrop for the wave of “over $40 million in cumulative liquidations” between September 8–9.
However, MYX officially responded on September 10, denying fraud or manipulation, claiming airdrop rewards were “based on genuine trading and LP contributions,” and stating they would place greater emphasis on anti-Sybil measures (implying these airdropped tokens were claimed by Sybils). On the same day, multiple English-language media outlets reported this response and cited the link to Bubblemaps’ September 9 thread. In other words, accusations and rebuttals were both laid bare, with each side holding firm. (Coinspeaker)
MYX’s most critical defense for denying manipulation is: MYX is currently trading around $15.
But if you conclude from this that MYX did not conduct a pump-and-dump, you’d be dead wrong. The reason is simple:
“Holding at high prices” does not equal “reasonable valuation”—it’s more about structural and timing dynamics.
Currently, about 197 million MYX are in circulation, roughly 20% of the total supply. Under the “low circulation / high FDV” framework, unit price elasticity is very high—so long as new selling pressure isn’t sudden (MYX airdrops unlock monthly) and market makers are willing to absorb supply, prices can remain elevated for extended periods.
In short, the script behind this MYX show is nothing new:
-
Low float props up price, derivative leverage amplifies volatility, and liquidations turn shorts into forced buyers;
-
The reason price remains high is likely due to tight structural supply, increased access points, and upgraded narratives working together.
No matter which side you’re on, at least clarify two things:
-
Whoever controls timing and flow dominates the rhythm;
-
Holding at high prices doesn’t mean risk has disappeared.
So, if you participated in MYX trading and lost a lot of money, that’s no surprise. This game inherently favors those who control narrative and tokens. For MYX, the right move is simply to avoid it. If you’re like me, just cash out your airdrop when the opportunity arises.
If we abstract such recurring stories into a framework, it has a name:
Predatory Market Structure
It’s not a single scam, but an entire intentionally assembled system of “institutional design + trading mechanisms + incentive structures” that enables better-informed, more powerful parties to consistently extract value from weaker participants.
To put it plainly, predatory market structure is jungle law—the only rule here is survival of the fittest.

-
In traditional finance, this structure hides in order flow rebates and dark pool internalization, in quote stuffing and spoofing;
-
In crypto, it transforms itself, leveraging “high FDV, low circulation” issuance models, creative distribution methods, sequencing rights (MEV), KOL amplification chains, and liquidation mechanisms to execute old tricks faster and harder.
In other words, it’s not a system “bug,” but a deliberately written “feature” embedded in products and institutions. Once you understand this, the question shifts from “who scammed whom” to why this structure can persist long-term, what sustains its moat, and what we can do about it.
Next, let’s break it down piece by piece.
1. Why Crypto “Predation” Persists
Like the MYX case above, what appears to be isolated incidents—specific projects, news events, stampedes—are actually underpinned by several enduring foundations: who has better information, who can convert information into profit, and where institutional gaps exist.
Understanding these three foundations explains why the same playbook keeps getting recycled—and reveals where self-protection should begin.
1.1 Three Pillars of Predation
If you only focus on individual price spikes and crashes, it’s easy to blame everything on “human greed.” But zooming out reveals a more stable “terrain”:
The first pillar is information asymmetry.
This isn’t a new concept—in 1970, economist George Akerlof explained it with the “lemons market”: when buyers can’t distinguish quality, bad products drive good ones out of the market.

“Lemon” isn’t literary metaphor—it’s American slang for defective cars/poor-quality goods (the U.S. even has dedicated “lemon laws” to protect buyers). Early 20th-century media used “lemon” to describe “bad purchases,” later specifically referring to risky used cars.
Akerlof used the used car market as a metaphor: sellers know the true condition best, while buyers can’t tell, so they bid based on “average quality,” causing high-quality owners to exit and lemons to dominate, dragging overall quality down.
In crypto, project teams know far more than ordinary users about token allocation, unlock schedules, and market-making arrangements—resulting in “quality scarcity, junk everywhere.”
This theory isn’t academic—it’s a well-documented, repeatedly verified problem.
The second pillar is the persistent existence of parties who have both the ability and motive to exploit asymmetry.
In traditional securities markets, whoever controls how your orders are routed and executed order can invisibly “capture a bit of spread” at your expense. That’s why U.S. regulators require brokers to disclose order routing and fulfill “best execution,” imposing heavy penalties for failure—for example, in 2020 Robinhood was fined $65 million by the SEC for inadequate rebate disclosure and failing to secure optimal prices for clients.
This shows that control over routing and sequence becomes an invisible cost to retail investors. (sec.gov)
Applying the same logic on-chain is even clearer: whoever can alter execution order might sandwich your trades for profit—this is commonly known as “sequencing rights” in research. Multiple papers since 2019 have systematically documented such “sandwich attacks,” showing they degrade average user trade quality and, in severe cases, even threaten consensus stability.
Sequencing rights are valuable precisely because they convert “timing” into “guaranteed profit.”
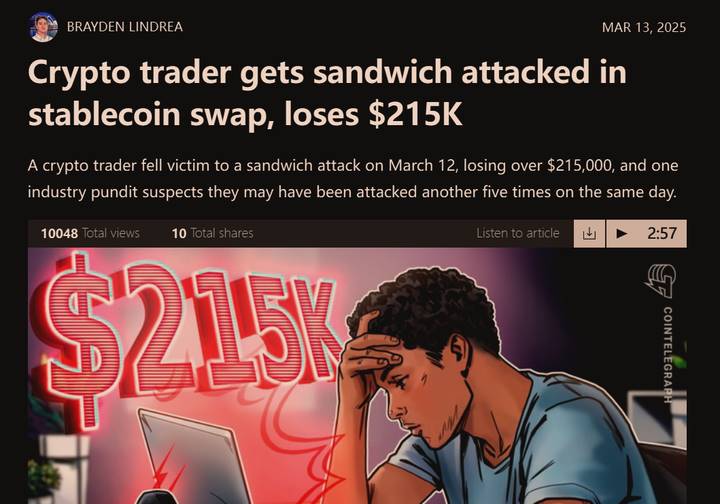
This is the MEV attack you often hear about. “MEV Sandwich Attacks Explained: From Ordering to Flash Swaps in a Deadly Chain” is my detailed breakdown of one such attack, which caused a trader to lose $215,000 in a single transaction.
The third pillar is permissive or lagging external environments.
When activities perform the same functions as traditional finance but operate outside regulation, they create a “low-risk, high-reward” safe haven for predators.
The International Organization of Securities Commissions (IOSCO) issued two sets of final recommendations in 2023–2024—one targeting crypto and digital asset service providers (18 items), another targeting DeFi (9 items)—with a core principle: “same activity, same risk, same regulatory outcome.” If you engage in risks that traditional securities markets regulate, you should face similar constraints on conflicts of interest, disclosure, and market manipulation.
In other words, regulatory fences are being built, but gaps still exist—and predators thrive precisely in these gaps. (iosco.org)
1.2 Weaponizing “Complexity”
Information asymmetry isn’t always “natural”—often it’s deliberately amplified.
The 2008 financial crisis serves as a textbook lesson in “complexity”: layering high-risk loans into complex securities with overly optimistic ratings made it nearly impossible to see the underlying risks. The Financial Crisis Inquiry Commission (FCIC) report reconstructed this chain with extensive evidence, concluding bluntly: complex structures obscured real risks. (fcic-static.law.stanford.edu)
Crypto’s “complexity” wears a new skin: tokenomics can be written in ways designed to be incomprehensible—permissions, minting, blacklists, taxes, unlocks—with enough variables, “ordinary people can’t understand it” becomes inevitable. Complexity here is given a mission: I don’t need every investor to understand; as long as most don’t, tokens can transfer under seemingly fair but deeply asymmetric conditions. (Kaiko Research)
“Complexity” also serves another purpose: diffusing accountability.
When processes are long and roles numerous, each participant can claim, “I was just following procedure.” This echoes the 2008 “originate-to-distribute” model: risks were fragmented, responsibilities even more so—when disaster struck, no clear line of liability could be drawn.
Crypto often replicates this “chain-like” division of labor—issuance, market making, listing, custody, marketing—with interconnected yet legally distinct entities. This is exactly why IOSCO repeatedly warns that vertical integration creates serious conflicts of interest, and only by dismantling this “complexity” can repeated predation be prevented—a point we’ll revisit later. (iosco.org)
1.3 “Emotion” Mass-Produced
If “complexity” blinds you, “mass-produced emotion” keeps you from stopping.
Social platforms have transformed the speed and reach of narratives—“emotion” can now be manufactured like a product. Chainalysis’ 2024 annual report found that 54% of ERC-20 tokens newly listed on DEXs in 2023 showed “suspected pump-and-dump” characteristics—not implying all were scams, but indicating that “scripted hype” is extremely common. Yet collectively, these tokens accounted for only 1.3% of DEX trading volume—small in size but dense and easily manipulated. This fits the business logic of “using small money to generate big noise, then using big noise to attract real liquidity.” (Chainalysis)
More frighteningly, the “amplifier” keeps evolving—even automating.
Research in 2023 revealed a network of crypto “bot armies” operating on X, using generative AI to auto-generate content and replies, mass-driving traffic to suspicious sites. The tech isn’t sophisticated, but the strategy is clear: transform “hype-building” from a manual workshop into an assembly line.
By 2024 and 2025, media and on-chain investigators observed that AI-powered scams and “pig-butchering” schemes had not declined but risen, even becoming “template-based outsourcing.”
When “scripts” and “emotions” become ultra-low-cost, information cascades keep pushing people to the same familiar place—rushing in at peak excitement, stuck at the most crowded exit. (WIRED)
1.4 Summary
Put these three pillars together, and it becomes clear: often it’s not bad luck—you’re facing powerful players who turn information gaps into business, complexity into weapons, and emotions into assembly-line products. As long as “control” and “profit distribution” aren’t aligned, this game will replay endlessly—whether Wall Street’s CDOs or on-chain memes.
You might ask: everything ends eventually—when will crypto’s “predation” end?
2. Will Crypto “Predation” Ever End?
Yes—but “predation” never vanishes on its own. Capital market order almost always emerges from scars. Today’s crypto predation is merely a rerun of stock market history. Understanding how stock market predation ended gives us clues about crypto’s timeline.
2.1 How Stock Market “Predation” Ended
The last century’s stock markets were like this: the 1929 “Black Thursday” crash dethroned Wall Street, with the Dow Jones Index falling nearly 90% by 1932, triggering bank failures and collapsing confidence—forcing the creation of the Securities Act (1933), Securities Exchange Act (1934), and the now-familiar SEC (U.S. Securities and Exchange Commission).
The SEC’s mission is simple: protect investors, maintain fair and orderly markets, facilitate capital formation. Its birth marked a turning point: capital markets shifting from a “wild jungle” to a “regulated playing field.”
Crisis → reform → evolution is a recurring rhythm across a century of stock markets.
China’s experience is similar. The 1992 “Shenzhen 8·10” incident nearly halved the nascent stock market in days, directly leading to the establishment of China’s CSRC (China Securities Regulatory Commission) in October that year—transitioning from a “free-for-all” experiment to a “regulated” market. Below is an image of people queuing to buy new share subscription lottery forms during the incident.

So, when we ask “will crypto predation end?”, a more accurate phrasing is:
Yes, but it won’t come automatically.
Judging from stock market history, endings typically follow major chaos, marked by systematic rules, disclosures, and “circuit breakers” being implemented.
2.2 Where Can Crypto Go From Here?
The solutions already exist—the challenge lies in implementation.
As early as November 2023, IOSCO released 18 final recommendations for crypto and digital asset markets (CDA), translating traditional securities market frameworks into crypto contexts:
Same activity, same risk, same regulatory outcome.
These recommendations target most of crypto’s chronic issues: conflicts from vertical integration of centralized service providers (CASPs), market manipulation and insider trading, custody and client asset segregation, tech and operational risks, and suitability and marketing boundaries for retail users. IOSCO’s press release highlighted “same activity, same risk, same outcome” as a core principle, attaching the full report. (iosco.org)

In December that year, IOSCO issued another 9 final recommendations for DeFi, identifying “responsible persons” within the seemingly ownerless “decentralized” space:
Whoever designs the product, operates the front-end, or collects fees should bear corresponding obligations for disclosure, risk management, and cross-border cooperation.
The accompanying Umbrella Note explains how the CDA and DeFi recommendations interconnect—whether you’re a centralized platform or an organizer, distributor, or front-end operator of smart contracts, as long as you perform similar securities market activities, you fall under the same outcome-oriented regulatory framework.
This isn’t “one-size-fits-all,” but rather transplanting “intended outcomes”: what you do determines what rules apply. All original documents are available for download on the IOSCO website. (iosco.org)
If we imagine what a “post-implementation crypto world” might look like, it wouldn’t seem unfamiliar:
-
Execution order must have clear boundaries, avoiding sandwiching ordinary users, similar to traditional markets’ “no inferior-price execution” rules;
-
Disclosure must shift from “polished whitepapers” to “auditable fact sheets,” openly laying out token allocations, unlock schedules, contract permissions, and related-party interests;
-
Conflicts of interest must either be isolated or resolved through competitive pricing—whoever holds sequencing/traffic rights must make those profits transparent and auction them off, returning fees to users instead of letting them vanish into black boxes.
Familiar stock market safeguards—“circuit breakers,” “no inferior-price execution,” “broker-dealer vs. proprietary trading separation”—all have counterparts in crypto. IOSCO’s two recommendation sets are called “outcome-oriented” precisely because they don’t care whether you use blockchains or databases—they only care about the financial functions you deliver, and demand equivalent order and responsibility. (sec.gov)
2.3 Summary
Of course, the end of “predation” won’t arrive by itself. Stock market order grew out of crashes, scandals, and costs; crypto won’t skip its “growing pains.”
But the good news is: this time we’re not starting from scratch. The toolkit is already on the table—reports, clauses, procedures, disclosure templates, even bridges connecting centralized and decentralized systems have been drafted.
What remains is for industry and regulators to implement them: hand speed to technology, but anchor order in rules. Once these nails are firmly driven in, while “predation” won’t disappear entirely, it will become increasingly costly, difficult, and unprofitable.
But remember: before “predation” fades, it’s also the most dangerous moment.
3. Right Now, You Need a Resilient Investment Philosophy
Resilience isn’t about predicting tops and bottoms—it’s about having an internal order that doesn’t self-destruct in any market.
It consists of three principles:
Only invest in assets you’re willing to hold for ten years; reverse information asymmetry through systematic due diligence; delete leverage from your vocabulary.
3.1 Only Invest in Coins You’d Hold for Ten Years
“Willingness to hold for 10 years” is a gatekeeper—it forces definition.
Benjamin Graham defined investing as “an operation involving thorough analysis, promising safety of principal and satisfactory return; anything else is speculation.” This isn’t motivational talk—it reframes the question from “how much can I earn?” back to “what am I actually buying?” (Novel Investor)
What you’re willing to hold for ten years usually has clear utility, sustainable cash flows, or network effects; what fails this test is likely just the next wave of “hype.” The value of this boundary lies in forcing you to answer “what am I buying?” before “how much can I earn?”

Data also reminds us not to overestimate our “reflexes.” A classic large-sample study tracked 66,465 household accounts: the more frequently they traded, the worse their returns. The most active group averaged only 11.4% annualized return, versus a market benchmark of 17.9%. Institutional results are similar: S&P’s SPIVA scorecard shows that in 2024, 65% of U.S. large-cap active funds underperformed the S&P 500; over longer periods, the underperformance rate is even higher.
In plain terms: make fewer decisions, but make them count. (faculty.haas.berkeley.edu)
3.2 Turn “Information Asymmetry” Into “I Understand It Before I Buy”
In crypto, “complexity” is often armor: permissions, taxes, blacklists, minting, unlock schedules—the more variables, the easier it is to exclude ordinary users. Instead of being passive, systematize your due diligence and reclaim control over your odds.
Step one: examine supply structure—put fully diluted valuation (FDV), circulation ratio, and unlock schedule on one page. Multiple verifiable studies consistently observe a common phenomenon: volatility increases and prices weaken around large unlocks, with larger unlocks bringing greater pressure. You can cross-check Kaiko’s quarterly/annual research with TokenUnlocks’ calendar to first identify “who will add selling pressure in the coming months” (Kaiko Research; TokenUnlocks).
Step two: conduct contract health checks. Tools like De.Fi Scanner offer one-click screening to flag red flags early—they’re not audits, but they can highlight obvious dangers (see image below).
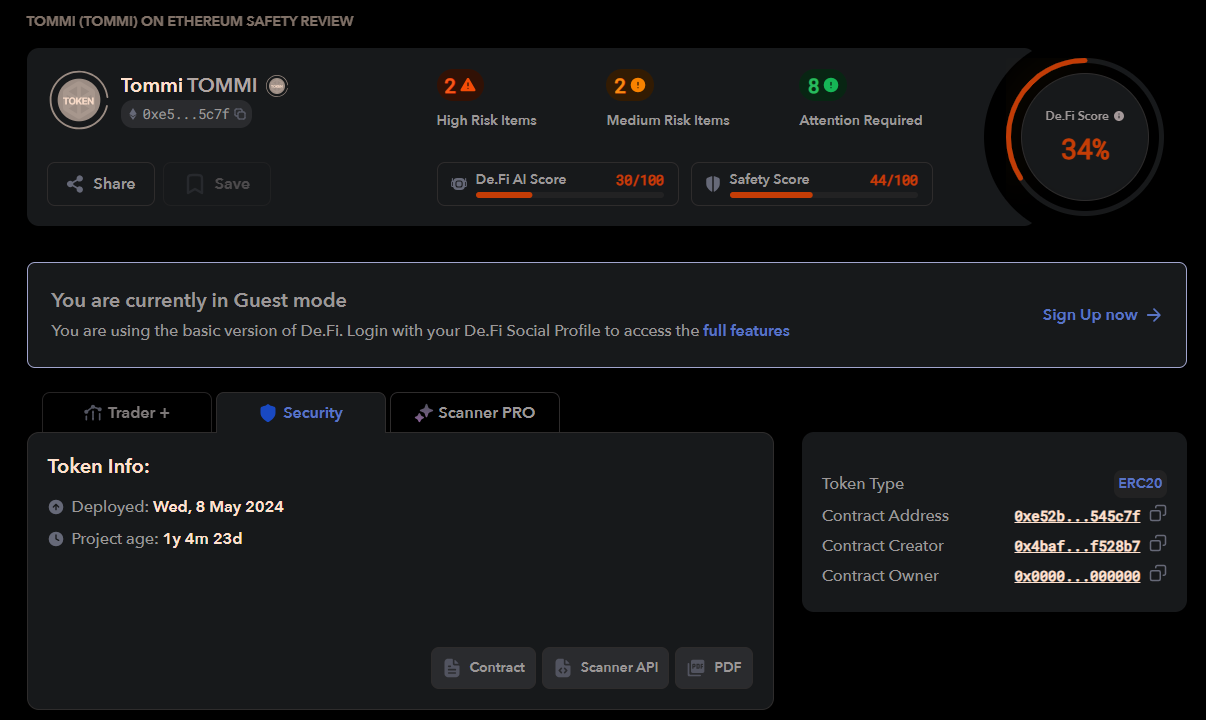
If you want deeper contract analysis, use AI. In “Beginner’s Guide: How to Avoid ‘100x Coin’ Traps,” I explain how ChatGPT helped uncover that the TOMMI project not only had a backdoor but also carried blacklist risks.
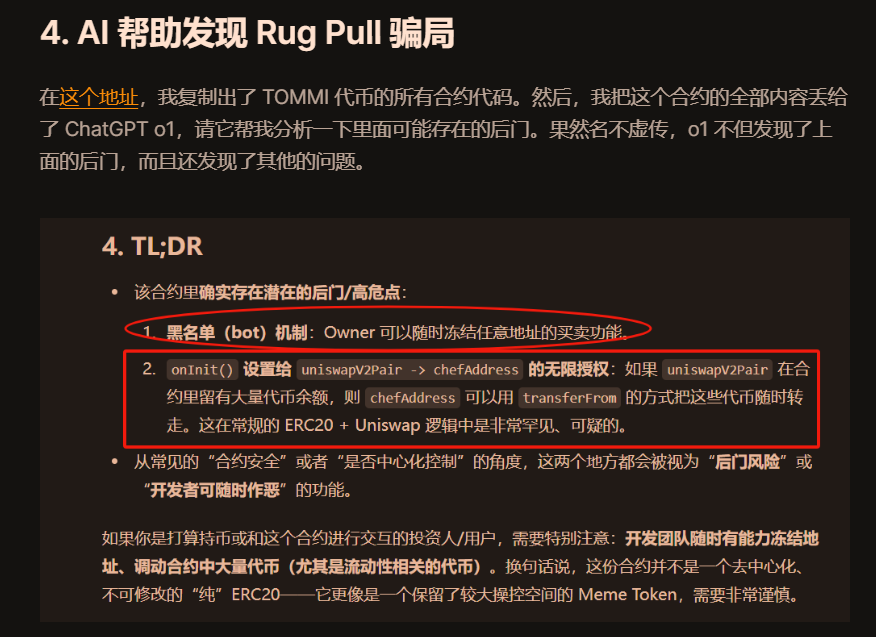
Step three: control trade execution and remove yourself from the “sandwiched” queue. Always compare prices via aggregators—use the one offering the best actual execution price.
On EVM chains: I commonly use 1inch (with Fusion/RFQ) and Odos (Protected Swaps). The former accesses market maker quotes, the latter offers MEV-protected routing (see image below), significantly reducing slippage and sandwich attacks.
On Solana, Jupiter and Titan’s routing capabilities and private channels similarly reduce the chance of being hunted. Regardless of chain, tighten slippage tolerance, split large trades, and prioritize routes with MEV protection or private mempools—these are actionable “physical isolations” you can implement today.
In short: understand “supply–permissions–execution” before deciding to act. By doing this, you’ve already turned most information asymmetry into personal certainty.
3.3 Delete “Leverage” From Your Dictionary
Leverage is the trigger that turns normal volatility into stampedes.
The Financial Stability Board bluntly states: automatic liquidation mechanisms, collateral chains, and pseudo-anonymous leverage on crypto CEXs and DeFi make forced deleveraging during downturns more contagious and self-amplifying. Once prices hit liquidation thresholds, machines act before humans—accelerating the decline.
History speaks clearly: Bitcoin retracing 30%–50% during bull markets is common, and full cycles have seen 80% drawdowns from peak to bear market bottom, as shown below.
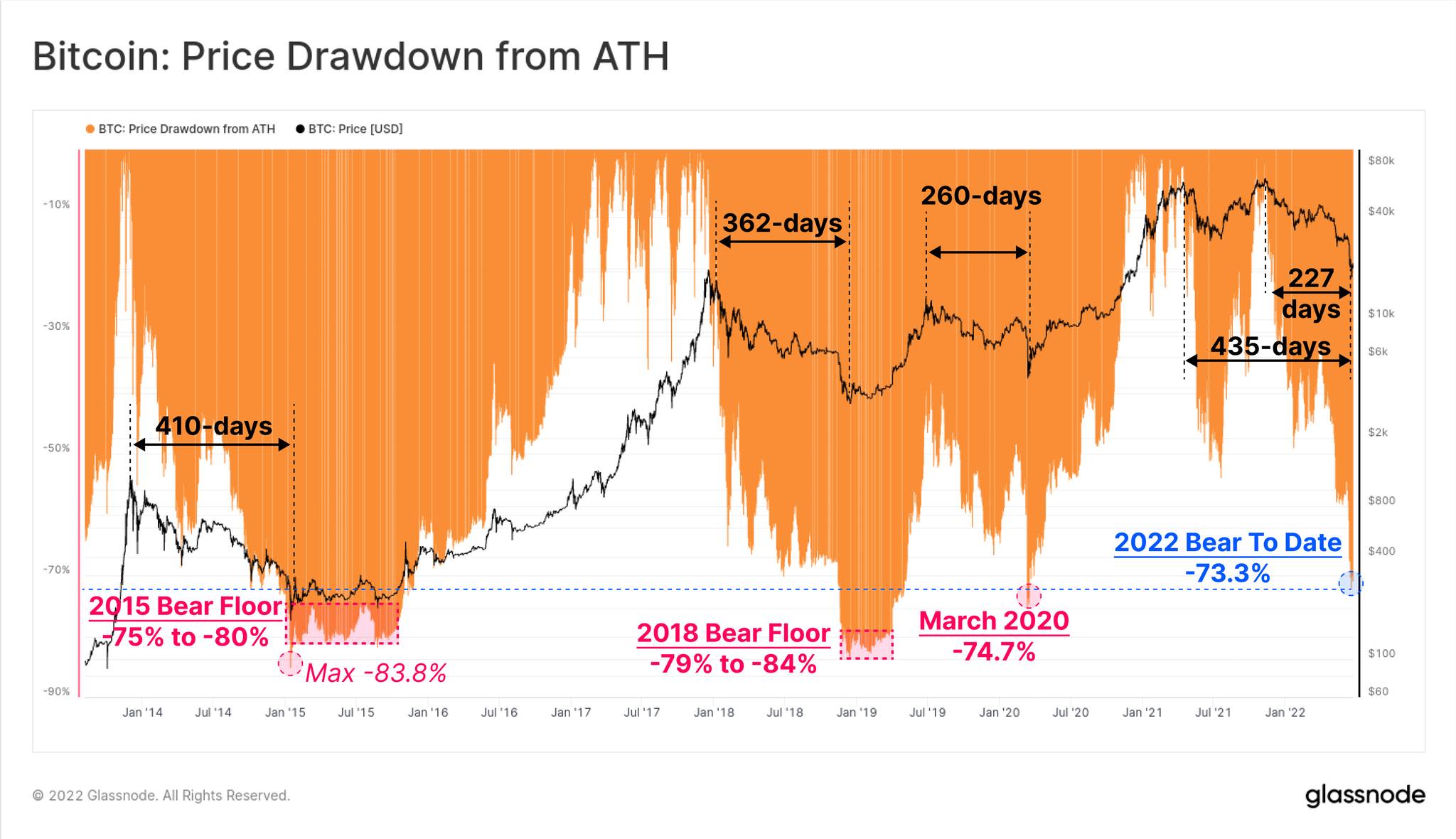
So set your life-or-death rule: no leverage, especially never entrusting your survival to liquidation engines; reduce position size and frequency to levels where you can sleep soundly.
3.4 Summary
On-chain data has long warned us: hype often outweighs substance, exits are often narrow—while order and compounding require slowness and patience.
Resilience isn’t about sharpening yourself into a blade, but equipping yourself with armor.
Don’t bet against the structural advantages of “predators.”

Conclusion: Through the Jungle, Toward Order and Long-Term Value
Zoom out, and you’ll see two forces advancing simultaneously:
One side sees gold rushes and predation alternating; the other sees order slowly but steadily growing.
Crypto’s transition “from chaos to order” has entered the construction phase—IOSCO’s outcome-oriented framework is being implemented, European compliance rules are accelerating, and compliant capital is converging with on-chain infrastructure.
Stablecoins are transforming cross-border settlement into “real-time, programmable” public utilities, while ETFs and tokenized assets are bringing trust and auditability back into the system.
All these changes send one message:
Predation is not the endgame—order is approaching; bubbles aren’t the whole story—value is consolidating.
But before rules are fully established, keep your armor on—don’t gamble against structural advantages.
Remember: let others have speed; keep survival for yourself. Cycles are ruthless, but compounding rewards patience.
When order arrives, advantage will shift from “fast hands” back to “patience and discipline,” and you’ll be glad you stood on the side of long slopes with deep snow.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News