Physical Kidnapping: Wrench Attacks After Bitcoin Reaches New High
TechFlow Selected TechFlow Selected

Physical Kidnapping: Wrench Attacks After Bitcoin Reaches New High
As the crypto industry rapidly evolves, Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations play a crucial role in enhancing financial transparency and preventing illicit fund flows.
Author: SlowMist
Background
In the dark forest of blockchain, we often discuss on-chain attacks, smart contract vulnerabilities, and hacker intrusions. However, an increasing number of cases remind us that risks have now extended beyond the chain.
According to Decrypt and Eesti Ekspress, during a recent court hearing, crypto billionaire and entrepreneur Tim Heath recounted a thwarted kidnapping attempt he experienced last year. The attackers used GPS tracking, forged passports, and disposable phones to monitor his movements, ambushing him from behind as he went upstairs, attempting to hood him and forcibly take control. Heath managed to escape only after biting off a portion of one attacker's finger.
As the value of crypto assets continues to rise, wrench attacks targeting cryptocurrency users are becoming increasingly frequent. This article will delve into these attack methods, review notable cases, analyze the underlying criminal chains, and provide practical prevention and response recommendations.
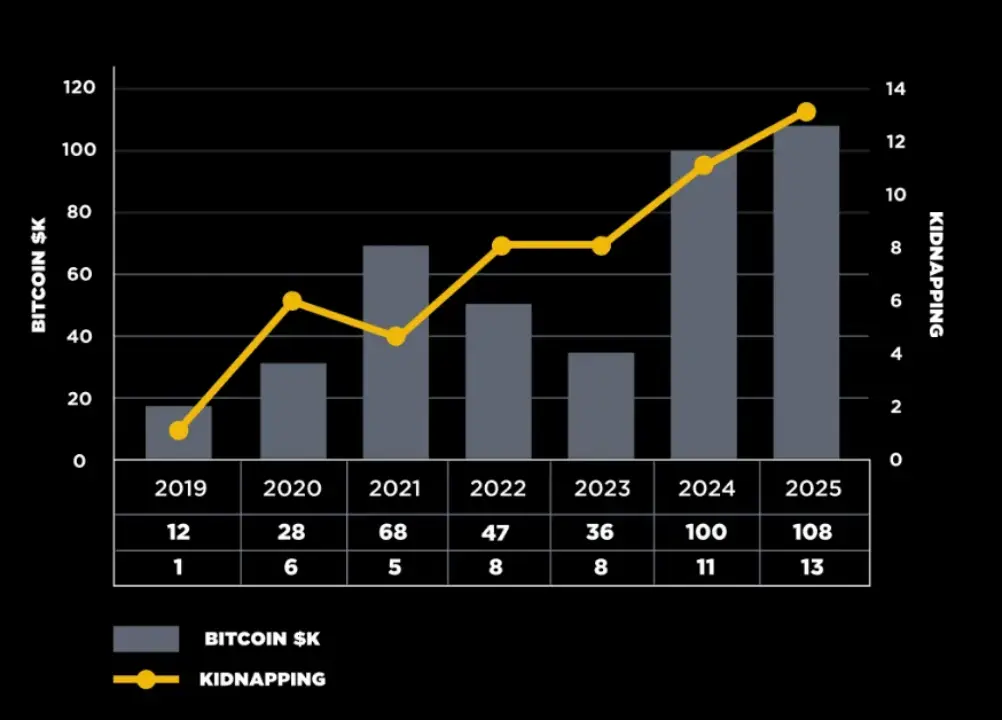
(https://www.binance.com/en/blog/security/binance-physical-security-team-on-how-to-avoid-the-threat-of-reallife-attacks-634293446955246772)
What Is a Wrench Attack?
"You can have the strongest technical protections in place, but all an attacker needs is a $5 wrench to hit you over the head, and you'll give up your password." The term "5-dollar wrench attack" originated from the webcomic XKCD, where attackers bypass technical defenses entirely, instead using threats, blackmail, or even kidnapping to force victims to surrender passwords or assets.
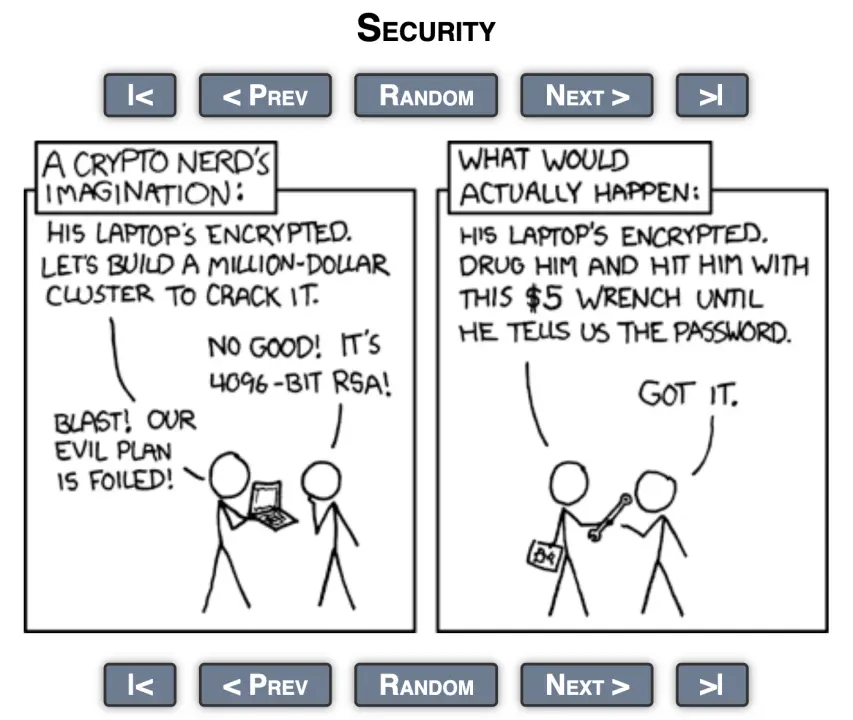
(https://xkcd.com/538/)
Review of Notable Kidnapping Cases
This year, kidnappings targeting crypto users have surged, affecting core project team members, KOLs, and even ordinary holders. In early May, French police rescued the father of a kidnapped cryptocurrency tycoon. The kidnappers demanded millions of euros in ransom and brutally cut off his fingers to pressure the family.
Similar incidents emerged earlier this year: In January, David Balland, co-founder of Ledger, and his wife were attacked at home by armed assailants who also severed his fingers and recorded videos demanding 100 BTC. In early June, a dual French-Moroccan national, Badiss Mohamed Amide Bajjou, was arrested in Tangier. According to Barrons, he is suspected of orchestrating multiple kidnappings of French crypto entrepreneurs. France’s Minister of Justice confirmed that the suspect is wanted internationally for charges including “kidnapping” and “unlawful hostage detention.” Bajjou is also believed to be one of the masterminds behind the Ledger co-founder’s abduction.
Another shocking case occurred in New York. Italian crypto investor Michael Valentino Teofrasto Carturan was lured to a villa and held captive for three weeks under torture. The criminal gang used chainsaws, electric shock devices, and drugs to threaten him, even suspending him from a high-rise rooftop to force disclosure of his wallet private keys. The perpetrators were “insiders” who had precisely identified their target through on-chain analysis and social media surveillance.

In mid-May, the daughter and young grandson of Paymium co-founder Pierre Noizat narrowly escaped being dragged into a white van on the streets of Paris. According to Le Parisien, Noizat’s daughter fiercely resisted, and a passerby smashed the van with a fire extinguisher, forcing the kidnappers to flee.

These cases show that compared to on-chain attacks, offline physical threats are more direct, efficient, and require lower barriers to entry. The attackers are typically young individuals aged between 16 and 23, possessing basic knowledge of cryptocurrencies. According to data released by French prosecutors, several minors have already been formally charged in such cases.
Beyond publicly reported incidents, SlowMist’s security team has observed, while reviewing victim-submitted forms, that some users have suffered asset loss due to coercion or control during in-person transactions.
Additionally, there are non-violent coercion incidents that stop short of physical violence. For example, attackers may threaten victims using exposed privacy, location data, or other compromising information to force fund transfers. While no direct physical harm occurs, these acts cross into personal threat territory—whether they qualify as “wrench attacks” remains a topic for further discussion.
It must be emphasized that disclosed cases likely represent just the tip of the iceberg. Many victims remain silent due to fears of retaliation, lack of law enforcement response, or concerns over identity exposure, making it difficult to accurately assess the true scale of off-chain attacks.
Criminal Chain Analysis
A 2024 research paper from the University of Cambridge titled *Investigating Wrench Attacks: Physical Attacks Targeting Cryptocurrency Users* systematically analyzed global cases of violent coercion against crypto users, revealing attack patterns and defense challenges. The image below is a translated version of the original figure from the paper (original source: https://www.repository.cam.ac.uk/items/d988e10f-b751-408a-a79e-54f2518b3e70).
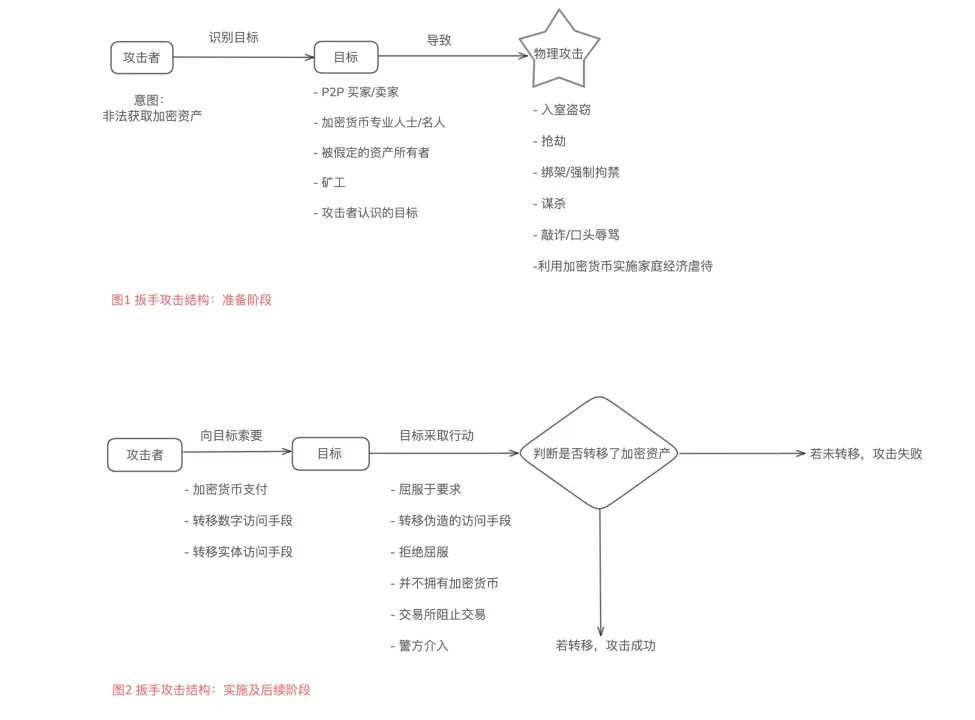
Based on multiple typical cases, we summarize the criminal chain of wrench attacks into the following key stages:
1. Information Targeting
Attackers usually start with on-chain data, analyzing transaction behavior, address labels, NFT holdings, and other indicators to estimate a target’s asset size. Meanwhile, Telegram groups, X (formerly Twitter) posts, KOL interviews, and leaked datasets serve as important supplementary intelligence sources.
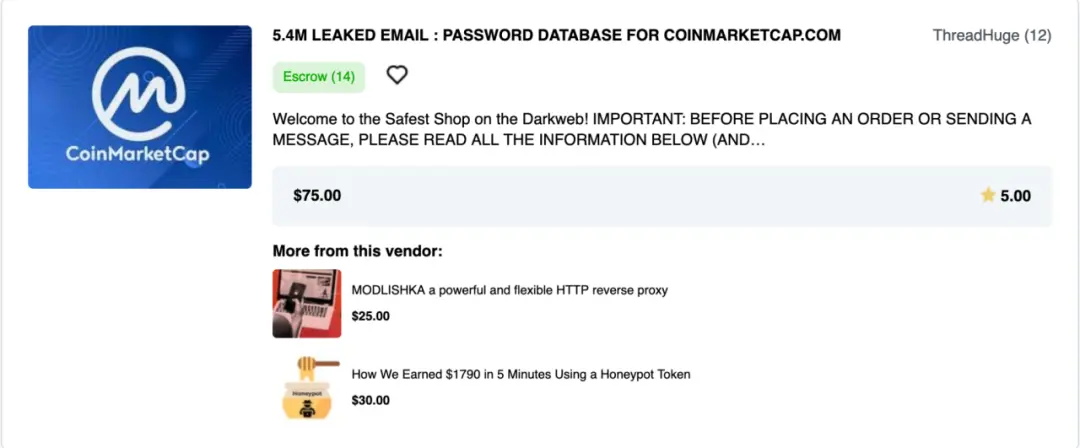
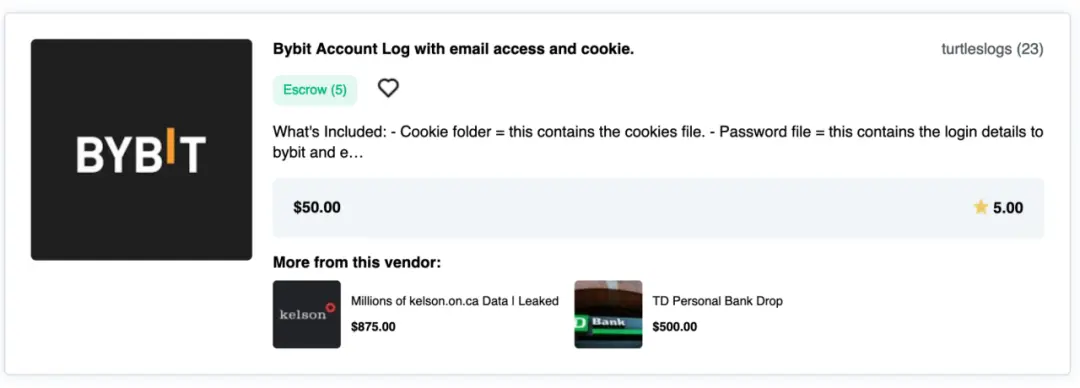
2. Real-World Location and Contact
Once a target's identity is confirmed, attackers seek real-world personal details such as residence, frequented locations, and family structure. Common methods include:
-
Inducing targets to reveal information on social platforms;
-
Reverse searching via public registration records (e.g., ENS-bound emails, domain registration info);
-
Conducting reverse searches using leaked data;
-
Tracking or luring targets into controlled environments through false invitations.
3. Violence and Extortion
Upon gaining control of the target, attackers often resort to violence to extract wallet private keys, recovery phrases, or second-factor authentication access. Common tactics include:
-
Physical harm such as beating, electrocution, or limb amputation;
-
Forcing victims to execute fund transfers;
-
Threatening relatives to compel family members to transfer funds.
4. Money Laundering and Fund Transfer
After obtaining private keys or seed phrases, attackers swiftly move assets using techniques such as:
-
Mixers to obscure fund origins;
-
Transferring to controlled addresses or non-compliant centralized exchange accounts;
-
Cashing out via OTC channels or black markets.
Some attackers possess blockchain expertise and understand on-chain tracing mechanisms, deliberately creating multi-hop paths or cross-chain obfuscation to evade detection.
Countermeasures
Using multi-sig wallets or splitting recovery phrases is often impractical in extreme scenarios involving physical threats, as attackers may interpret such actions as resistance, escalating violence. A more prudent strategy against wrench attacks is to “have something to give, with losses under control”:
-
Create decoy wallets: Prepare a wallet that appears to be your main one but holds only minimal funds, to use as a “loss-minimizing bait” in dangerous situations.
-
Family security management: Ensure family members understand where assets are stored and how to respond cooperatively; establish a safety word to signal danger during abnormal situations; strengthen security settings on household devices and physical premises.
-
Avoid identity exposure: Refrain from flaunting wealth or sharing trading records on social media; avoid disclosing crypto holdings in real life; manage friend circle information carefully to prevent leaks by acquaintances. The most effective protection is ensuring others simply don’t know “you’re a worthwhile target.”
Final Thoughts
As the crypto industry rapidly evolves, Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations play a crucial role in enhancing financial transparency and curbing illicit fund flows. However, implementation still faces significant challenges, particularly regarding data security and user privacy. For instance, large volumes of sensitive data (such as identity documents and biometric information) collected by platforms to meet regulatory requirements can become attack vectors if not properly protected.
Therefore, we recommend augmenting traditional KYC processes with dynamic risk identification systems to minimize unnecessary data collection and reduce data breach risks. Platforms should also integrate comprehensive AML and tracking solutions like MistTrack to help identify suspicious transactions early and enhance overall risk control capabilities. Additionally, building robust data security capacity is essential—platforms can leverage SlowMist’s Red Team Testing service (https://cn.slowmist.com/service-red-teaming.html) to simulate real-world attack scenarios and comprehensively evaluate exposure pathways and vulnerabilities of sensitive data.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News