Sui blockchain distributed storage Walrus launches, Filecoin往事 sounds compliance warning bell
TechFlow Selected TechFlow Selected

Sui blockchain distributed storage Walrus launches, Filecoin往事 sounds compliance warning bell
From the Filecoin boom and its lessons to the rise of Walrus, ensuring legal operations across the entire upstream and downstream chain is the foundation for scaling up and growing stronger.
Authors: Liu Honglin, Mao Jiehao
Surpassing Filecoin? New Storage Protocol Walrus Launches
On March 27, 2025, Walrus, the decentralized storage protocol on the Sui blockchain, went live on mainnet. This marks another move by Mysten Labs following the launches of the Sui network and DeepBook—this time targeting the Web3 storage sector. Built atop the Sui blockchain, Walrus aims to optimize existing storage solutions in cost efficiency, programmability, data access, and deletion. It doesn't just aim to serve as Sui’s storage layer but aspires to become the leading decentralized storage protocol in Web3.
According to IBM's "Cost of a Data Breach Report 2020," approximately 99,730 data breaches occurred globally that year, resulting in hundreds of billions of dollars in economic losses. In 2018, a Google data center in Belgium was struck by lightning, causing disk damage and data loss. The fragility of centralized storage is a persistent headache, while distributed storage—encrypting, slicing, and dispersing data across global nodes—sounds like a tailor-made solution for privacy and security.
By distributing data across multiple physical nodes (typically servers or devices worldwide) and combining encryption with blockchain mechanisms, distributed storage achieves high availability and enhanced privacy and security. Compared to traditional storage methods, it offers numerous advantages:

As one of the most advanced projects in the decentralized storage space, Walrus has surged to the top of Rootdata’s storage category, generating significant buzz in an otherwise dormant sector and reminding many of the excitement once sparked by Filecoin.
In 2017, Filecoin launched with a record-breaking $200 million ICO, creating a sensation in the crypto industry. Its vision was to combine IPFS (InterPlanetary File System) with blockchain incentives to build a global decentralized storage market. After its mainnet launch in 2020, Filecoin quickly attracted a large number of miners and developers, surpassing 1EB (1 billion GB) in storage capacity within a year. The community had high hopes; FIL token prices soared, fueling a mining frenzy. At one point, even Chinese housewives were buying mining rigs, and claims that Filecoin would be the next Bitcoin became widespread.
However, Filecoin gradually lost momentum due to high storage costs, complex incentive mechanisms, and intensifying market competition. In many regions, it was even questioned as a scam, often associated with pyramid schemes, primarily because bad actors exploited its mining mechanism and expectations of token appreciation through exaggerated marketing, misleading investors and damaging its reputation—leaving behind a mess.
Despite this, distributed storage remains a key infrastructure track in Web3 and a critical technology for challenging monopolies in centralized cloud services, continuing to attract entrepreneurs and investors. From protecting user privacy to empowering data sovereignty, the rise of emerging projects like Walrus has reignited market enthusiasm.
In this article, ManQin Law will explore how distributed storage protects user privacy through encryption and decentralization, China's official regulatory stance on this technology, its commercial potential, and more importantly, the legal compliance considerations Web3 entrepreneurs must pay special attention to when developing distributed storage projects. Distributed storage has promise and represents the future—but only projects that are legally compliant can grow sustainably and at scale.
Why We Need Distributed Storage: Everyone Wants Privacy
Have you ever experienced this? One day you casually search for teeth whitening, only to start receiving daily spam calls from dental clinics offering eerily precise promotions. When and where did your data leak? This year's 315 Gala exposed the technical underpinnings of the data black market, revealing rampant trading of personal information. As data becomes a core production factor, security and privacy should be non-negotiable baselines. More people are realizing: privacy—data privacy—is important.
This year’s 315 Gala shocked us by revealing that several tech companies illegally process over 10 billion user data entries daily, including sensitive data such as phone numbers, purchase histories, and social media accounts. Some systems even steal enterprise public account and WeChat group member information, forming a closed-loop black industry chain of “data theft - precision marketing - commercial monetization.”
Privacy remains a constantly discussed topic. Ethereum founder Vitalik recently published a 10,000-word blog post titled “Why I Support Privacy,” in which he wrote:
"Privacy does not mean isolation—it means unity. Privacy isn’t something separate, but a shared foundation."
Why do we want privacy? Everyone has different answers. He breaks his own down into three parts:
-
Privacy is freedom: Privacy gives us space to live in ways that best suit our needs, without constantly worrying about how our actions will be perceived in various political and social games.
-
Privacy is order: A series of mechanisms underpinning basic societal operations depend on privacy to function properly.
-
Privacy is progress: If we gain new ways to selectively share our information while protecting it from abuse, we can unlock immense value and accelerate technological and social advancement.
Vitalik summarized his overall argument on privacy in one sentence: Privacy gives you the freedom to live in the way that best aligns with your personal goals and needs, without constantly having to balance between the "private game" (your own needs) and the "public game" (how others, through various mechanisms—including social media dynamics, commercial incentives, politics, institutions—react to and perceive your behavior).
Looking back, as early as 1993, the Cypherpunk Manifesto issued a call for privacy and freedom—"Privacy is the power to selectively reveal oneself to the world... We are defending our privacy with cryptography, anonymous mail forwarding systems, digital signatures, and electronic money." Bitcoin didn’t emerge out of thin air—it was the culmination of a long and difficult journey. Today, this path toward privacy continues to extend further.
We need distributed storage because we all desire privacy.
Follow the Data: Commercial Prospects Are Vast
The essence of blockchain technology is decentralization. The tamper-resistant nature and encrypted information of distributed storage align perfectly with the "decentralized" direction of the Web3.0 era, making it an indispensable component of future blockchain development and adoption—and naturally, its commercial prospects are vast.
Let’s look at the data:
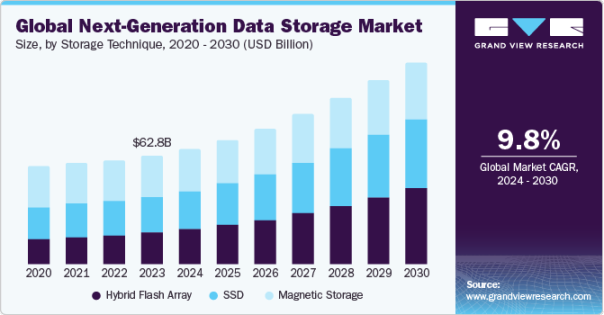
According to Grand View Research, the global data storage market reached $62.83 billion in 2023 and is projected to grow at a compound annual growth rate (CAGR) of 9.8% from 2024 to 2030, exceeding $100 billion by 2030.
According to the latest MRA research, the distributed storage market alone is expected to grow from approximately $15 billion in 2025 to over $50 billion by 2033, with a CAGR of around 16%, seeing the highest adoption rates in the business sector.
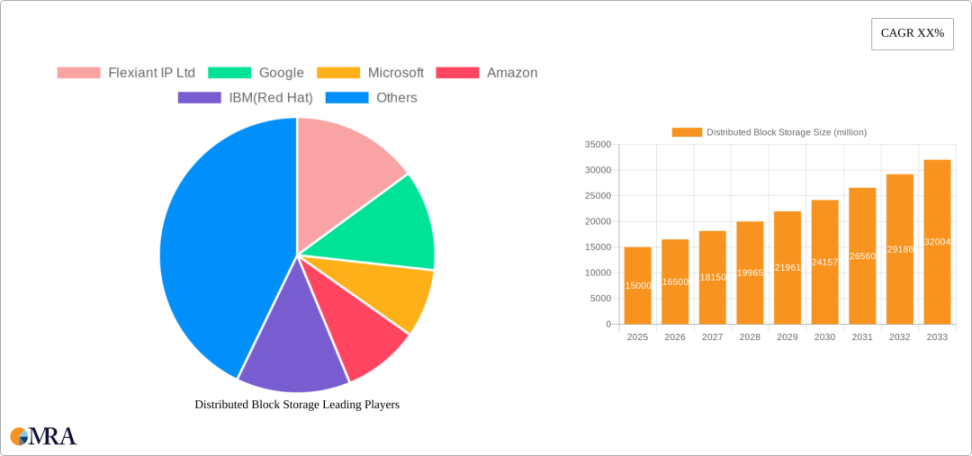
Clearly, the distributed storage market demonstrates strong growth potential and extensive commercial opportunities. An increasing number of blockchain projects are adopting distributed storage as foundational infrastructure. Governments, enterprises, and individuals worldwide are gradually embracing it—Google Chrome already supports built-in IPFS components, Ethereum has achieved full integration with the IPFS network, and domestic internet giants Tencent, Baidu, and Alibaba are also beginning to invest in related technologies. The growing convergence of distributed storage with other technologies like artificial intelligence and machine learning will unlock even more possibilities.
Mainland China’s Stance on Distributed Storage
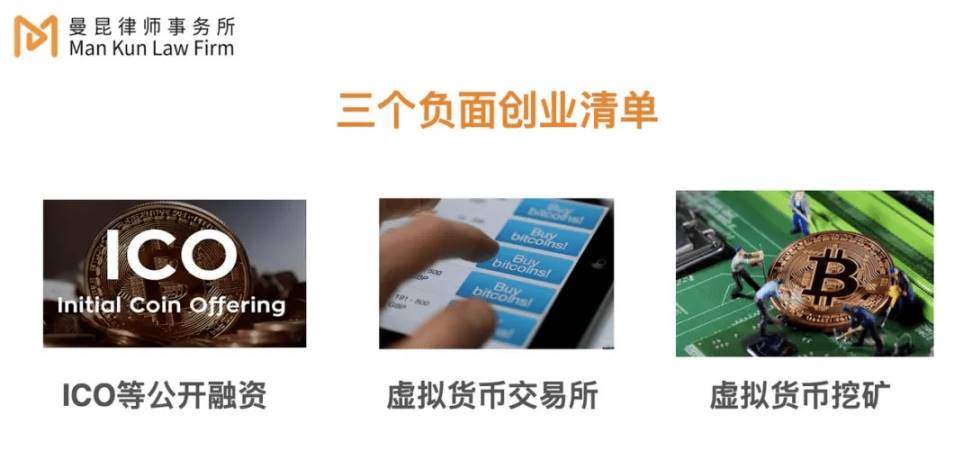
Frequent readers of ManQin Law’s analyses will surely recall that there are three legal red lines Web3 entrepreneurs in mainland China must never cross. In distributed storage projects, users earn tokens by maintaining and improving project infrastructure, and these tokens can gain liquidity via exchanges or other means—easily triggering the latter two items on the negative list.
In September 2021, ten departments including the People’s Bank of China jointly issued the “Notice on Rectifying Virtual Currency ‘Mining’ Activities,” stating that the state does not support cryptocurrency mining projects such as Bitcoin to achieve energy conservation and emission reduction goals.
However, distributed storage projects like Filecoin—the incentivized layer of IPFS—operate on a proof-of-work model fundamentally different from Bitcoin, consuming far less electricity and instead improving the utilization of idle resources. By simply providing storage space and bandwidth, they theoretically face lower compliance risks, especially if the project avoids excessive focus on tokens and is viewed purely from a technological perspective. The notice also emphasized distinguishing between “mining” and blockchain- or big-data-related industries, encouraging resource-efficient, high-value-added tech sectors. At the national and governmental level, distributed storage technology itself has not faced policy restrictions—in fact, it has been somewhat encouraged and optimized.
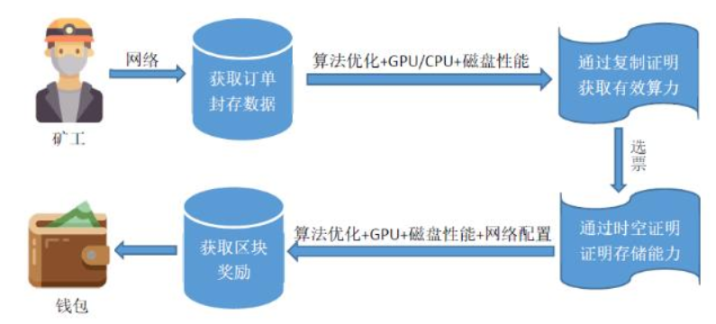
Additionally, although China does not deny the property attributes of virtual currencies, initial coin offerings (ICOs) are strictly prohibited, easily touching the first item on the negative list. Judicial practices regarding contracts involving cryptocurrency-related hardware remain inconsistent. The following sections will explain how entrepreneurial teams can avoid these risks.
We can also see that the implementation of the “Data Security Law of the People’s Republic of China” in September 2021 marked China’s formal entry into a rule-of-law framework for data resource development and application. While providing legal protection for data security in distributed storage, the law also sets new behavioral standards for operational enterprises, legally guiding standardization reforms in the IPFS space.
In summary, mainland China maintains an open stance toward distributed storage, clearly differentiating it from high-energy-consuming cryptocurrency mining. Regulations such as the “Data Security Law” provide legal safeguards for industry standardization. Policy is not a roadblock but a filter—only compliant projects can ride the favorable winds. For Chinese Web3 entrepreneurs, distributed storage may represent a policy-feasible track.
Compliance Across the Entire Project Ecosystem:
Unlike other Web3 projects, distributed storage projects are closely tied to hardware, forming a well-defined upstream-downstream industrial chain. The value chain is long—from technology development and hardware distribution to marketing—and each link carries potential risks. Below is ManQin Law’s “risk avoidance guide”:
Upstream: Project Teams—Don’t Focus Only on Technology
The project team is central, responsible for protocol design, business model development, and operational coordination, but compliance must begin from day one. Key areas include corporate entity structure, data security and cross-border compliance, and anti-financial crime measures.
1. Corporate Entity: Going Overseas Is an Option
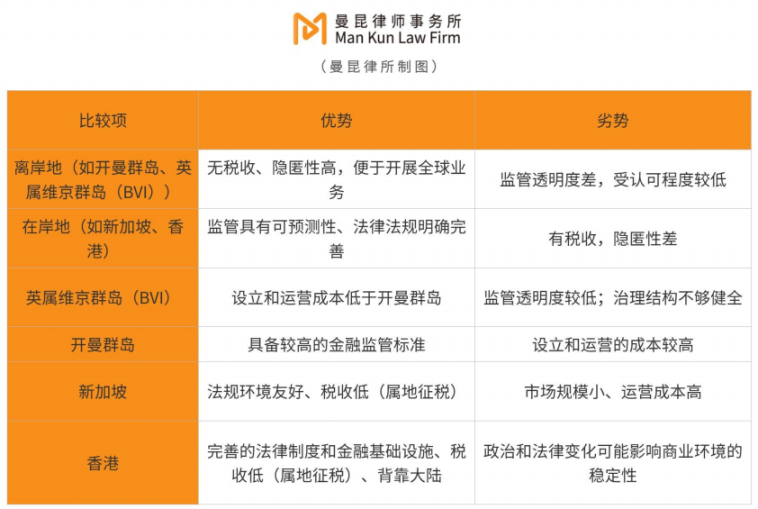
Some activities face limitations domestically, so startups may seek opportunities abroad. Increasingly, project teams choose to establish companies overseas and form teams in crypto-friendly jurisdictions such as Hong Kong, Singapore, and Dubai, retaining only limited support staff domestically. For teams planning to launch distributed storage businesses—especially those intending to issue tokens—an early offshore strategy is recommended, with the main project entity established overseas.
ManQin Law advises:
-
Select an appropriate overseas jurisdiction to ensure the corporate entity complies with local laws;
-
Clearly define roles between overseas entities and domestic teams to mitigate domestic regulatory risks;
-
Explore compliant business models that account for differing regulatory environments;
-
Consult professional lawyers early to plan compliant token issuance pathways.
2. Data Security: Privacy Isn’t Just a Slogan
Although distributed storage projects are inherently decentralized, their practical operation still involves a degree of centralized management and coordination. Moreover, most such projects involve large numbers of overseas users, requiring data to be posted on blockchains across borders—making cross-border data flow a necessity. Therefore, data compliance and security require careful consideration.
Personal Information Protection
Projects must have privacy policies clearly explaining how personal information is collected, used, stored, and transmitted, ensuring compliance with laws such as the “Personal Information Protection Law.” Explicit user consent must be obtained before collecting or processing personal data, with clear disclosure of the purpose, method, and scope of data processing. Projects should also follow the data minimization principle, collecting and processing only the minimum amount of personal data necessary to achieve specific purposes.
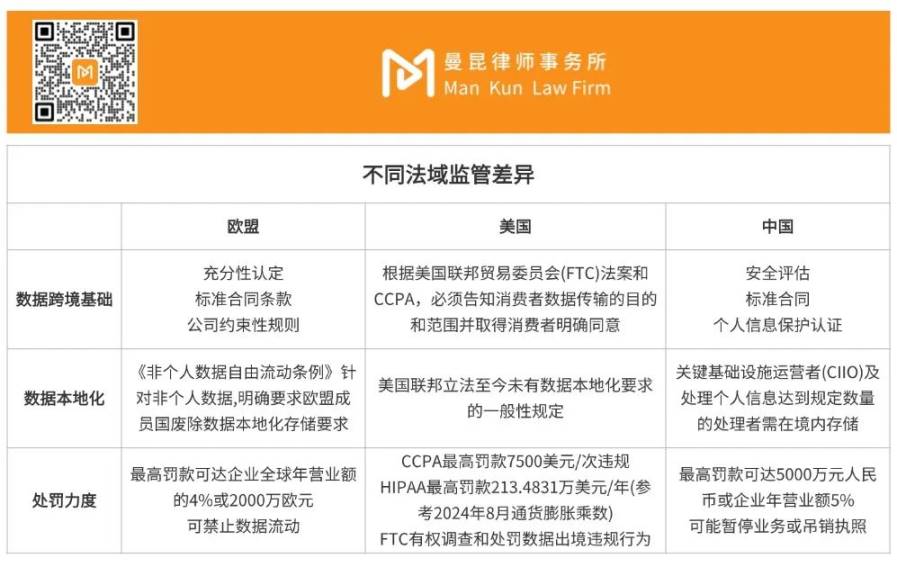
Projects must also navigate differences across jurisdictions. Companies expanding overseas must precisely understand the compliance requirements of major markets. The “Personal Information Protection Law” requires user consent and security assessments for data exports, while GDPR (EU) emphasizes user privacy rights (such as the “right to be forgotten”) and transparency.
Data Security
Establish a data security management system: Develop and implement comprehensive data security policies in accordance with the “Cybersecurity Law” and “Data Security Law” to ensure data safety during storage, transmission, and processing.
Data Encryption: Use strong encryption techniques to protect data in transit and at rest, preventing unauthorized access and data leaks.
Regular Security Assessments: Conduct regular data security risk assessments and vulnerability scans, promptly patching any discovered vulnerabilities to enhance system security.
Data Storage and Cross-Border Transfer
Cross-border data flows are inevitable in distributed storage projects, given their globally distributed nodes. However, both the “Cybersecurity Law” and “Data Security Law” stipulate that “critical data” affecting national security or public interest must be stored domestically. Transferring data overseas is not simple.
For example, if your project involves user information, a security assessment must be conducted before transferring it abroad to prove the data won’t be misused. The EU’s GDPR also grants users the “right to be forgotten”—non-compliance could result in heavy fines. Therefore, feasibility assessments should be conducted before launching the project, and security assessments completed prior to any cross-border data transfer to ensure compliance with relevant regulations.

3. Anti-Financial Crime: KYC Is Not Optional
Anti-money laundering (AML) and counter-terrorism financing (CTF) are global red lines. KYC (“Know Your Customer”) is widely understood—projects must rigorously implement it to prevent fraud, protect user interests, and enhance platform compliance. This includes requiring users to submit identity documents (e.g., ID cards, passports) and address proofs for verification, and regularly updating and reviewing user information to maintain accuracy.
One project assumed that being “decentralized” and storing data on-chain exempted them from KYC. But when money-laundering groups infiltrated their user base, regulators stepped in and shut the project down immediately. Compliance isn’t a technical issue—it’s a survival issue.
Downstream ①: Hardware Distributors
In the distributed storage space, hardware sales—a key link—often become breeding grounds for pyramid schemes and illegal fundraising due to profit-driven motives. History offers cautionary tales: during the Filecoin boom, numerous unscrupulous companies leveraged the names “IPFS” and “Filecoin” to aggressively promote storage investment returns while deliberately concealing investment risks, leading to massive investor losses. Two cases stand out.
In the 2021 Xuzhou Filecoin mining rig fraud case, certain IPFSUnion distributors lured investors with promises of “high returns” and “fast ROI,” selling Filecoin mining rigs through multi-level distribution models to illegally raise funds totaling 400 million RMB. Police intervention led to asset seizures and the arrest of 31 individuals. Although IPFSUnion claimed employees were merely “assisting with investigations,” the incident severely damaged the project’s credibility.
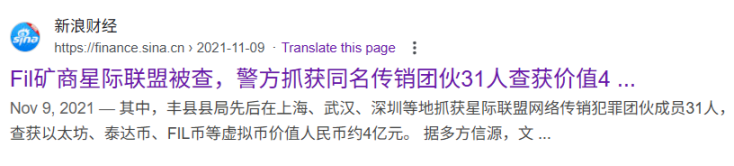
The 2023 Shenzhen SpaceTime Cloud case was equally shocking. SpaceTime Cloud used the filpool.io platform to sell Filecoin mining rigs under the guise of a “joint mining” program, operating a pyramid-style Ponzi scheme. The case involved 607 million RMB (about $83 million), including 62 million RMB in cryptocurrency, with over 57,000 registered members—further damaging Filecoin’s ecosystem reputation.
Prosecutors determined that defendants, including Lai Mouhang, required participants to pay mining rig fees or rental charges to join, developed downlines hierarchically, and offered rewards based on recruitment numbers, using high returns to lure others into participation. Their actions violated criminal law, warranting prosecution for organizing and leading pyramid schemes.
To avoid such risks, ManQin Law recommends:
-
Standardize sales language, strictly prohibiting exaggerated returns or guaranteed profits;
-
Clearly disclose investment risks and fully safeguard user right to know; establish compliance training for distributors, conduct regular audits of sales practices, and carefully select partners;
-
Work with professional lawyers to thoroughly review distribution contracts and eliminate legal loopholes.
Downstream ②: Marketing and Promotion Teams
In the distributed storage field, marketing teams are crucial for user acquisition and brand outreach but pose significant risks due to false advertising. Misleading promotion not only deceives users but may also violate laws and damage overall project credibility.
As early as 2021, IPFS-related promotions drew regulatory scrutiny for overstating returns. Some promoters used highly enticing slogans like “mine multiple coins with one device” and “quick ROI,” amplifying investment gains while completely ignoring risk disclosures. Such one-sided, exaggerated claims seriously violate the “Advertising Law” provisions on truthfulness and legality of advertisements and infringe upon consumer rights under the “Consumer Rights Protection Law.” Ultimately, these improper promotions damaged project reputations and disrupted market order.
That same year, the China Association of Communication Industry issued a warning directly criticizing some Filecoin promoters for using “distributed storage appreciation” as a hook, focusing solely on high returns while neglecting risk disclosures. Regulators swiftly intervened, imposing fines and ordering corrections on companies engaging in false advertising—demonstrating firm resolve to clean up market chaos.
ManQin Law advises:
Ensure objective messaging: Marketing teams should accurately disclose equipment performance and objectively present the uncertainty of returns to avoid misleading users. For instance, when introducing mining rigs, actual computing power and operating environment requirements should be clearly stated, with revenue ranges reasonably estimated using historical data.
Strengthen risk warnings: Prominent risk disclaimers such as “Investment involves risk; returns are not guaranteed” should appear in all promotional materials, ensuring users notice them immediately.
Regulate promotional language: Absolutely avoid absolute terms like “guaranteed returns” or “risk-free profits.” Content should remain neutral and objective, using precise language and data to reduce legal risks and trust crises caused by exaggeration.
ManQin Law Summary
Distributed storage is core Web3 infrastructure that protects privacy through encryption and decentralization, meets user demands for data sovereignty, and shows immense commercial potential. This year’s CCTV 315 Gala exposed the chaos of the data black market, highlighting the privacy crisis of centralized storage and affirming distributed storage as a key technology against data abuse. From Filecoin’s rise and fall to Walrus’s emergence, ensuring legal and compliant operations across the entire upstream-downstream chain is the foundation for sustainable growth.
Upstream project teams can establish overseas corporate entities, design business models adaptable to varying domestic and international regulatory environments, ensure data security and cross-border compliance, implement KYC procedures, and guard against financial crime risks.
Downstream hardware distributors must remain vigilant against pyramid schemes and illegal fundraising. They should standardize sales language, disclose risks transparently, and minimize legal vulnerabilities through compliance training and contract reviews.
Promotion teams must eliminate false advertising to avoid regulatory penalties, market disorder, and reputational damage. Marketing content should be truthful and transparent, with clear risk disclosures.
Many also recognize that distributed storage is just one branch of the DePIN sector. Other innovative DePIN projects include Render Network (a leader in decentralized AI compute) and Hivemapper (a decentralized encrypted mapping project). These initiatives all aim to break centralized monopolies and build a globally interconnected physical infrastructure network ecosystem. Most DePIN projects are tightly coupled with hardware and must similarly manage upstream-downstream risks.
"Privacy is the cornerstone of freedom, order, and progress." The internet is undergoing a decentralized revolution, and distributed data storage is a key pillar of society’s digital transformation. Expanding from distributed storage to the broader DePIN sector reveals vast commercial potential and a promising future. In this blue ocean of entrepreneurship, only projects that achieve legal compliance can grow sustainably and at scale.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News