ScaleBit Picks: Overview of the 2024 Bitcoin Ecosystem, Scaling Technologies and Security Incidents Summary
TechFlow Selected TechFlow Selected

ScaleBit Picks: Overview of the 2024 Bitcoin Ecosystem, Scaling Technologies and Security Incidents Summary
The Bitcoin expansion ecosystem has significantly enhanced the functionality and transaction efficiency of the Bitcoin network through various Layer 2 solutions and innovative protocols, driving advancements in emerging fields such as smart contracts, DeFi, and NFTs.
Introduction
As blockchain technology continues to evolve, Bitcoin has grown beyond its role as a mere cryptocurrency. Its ecosystem is expanding and deepening, encompassing various Layer 2 solutions and applications. These extensions not only enhance transaction speed and efficiency but also support emerging fields such as smart contracts, decentralized finance (DeFi), and non-fungible tokens (NFTs). Such innovations have broadened Bitcoin's use cases far beyond value storage and peer-to-peer payments, enabling it to meet more complex and diverse demands, thus driving progress across the entire blockchain industry.
However, with this expansion comes increasing security concerns. New technologies and applications introduce additional potential risks and challenges. Ensuring system security while enhancing functionality has become critical. Vulnerabilities, cyberattacks, and technical flaws threaten user asset safety and may undermine the overall stability and trust in the Bitcoin network. This article, authored by ScaleBit under BitsLab, provides an in-depth exploration of the development of Bitcoin’s expanding ecosystem, examines past security incidents, and offers insights into future security prospects. By analyzing current technological approaches and security challenges, this report aims to provide valuable guidance for the sustainable growth of the Bitcoin ecosystem, ensuring it maintains high levels of security and reliability during continuous expansion.
Bitcoin Expansion Ecosystem
What Is the Bitcoin Expansion Ecosystem?
The Bitcoin expansion ecosystem refers primarily to the range of extension solutions and application ecosystems developed around the foundational Bitcoin network. Originally designed for peer-to-peer payments and value storage, the Bitcoin community and developers are now exploring ways to add advanced functionalities—particularly in smart contracts, DeFi, NFTs, and efficient transaction scaling.
How Does the Bitcoin Expansion Ecosystem Work?
The operation of the Bitcoin expansion ecosystem relies on extension technologies and protocols built either atop or alongside the Bitcoin mainchain. These enable Bitcoin to support a broader array of use cases. Below are key technical mechanisms within the ecosystem:
(1) Lightning Network
The Lightning Network is one of the most mature and widely adopted Layer 2 solutions for Bitcoin. It enables off-chain payment channels that move numerous small transactions off the mainchain, significantly improving transaction speed and reducing fees.
Trend: Infrastructure improvements and enhanced user experience have led to growing merchant adoption of Lightning payments.
Challenge: Liquidity constraints and routing inefficiencies remain issues, especially for large-value transactions.
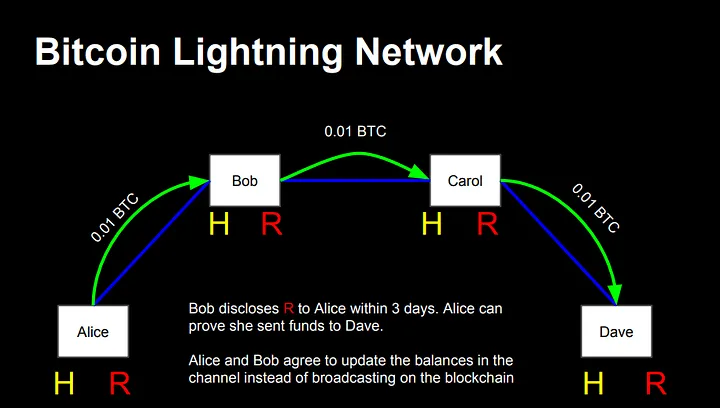
Image 1 Source:
https://lightning.network/lightning-network-presentation-time-2015-07-06.pdf
(2) Liquid Network (LQ)
Liquid Network is an open-source sidechain based on the Elements blockchain platform, designed for faster trading between exchanges and institutions. Governed by a distributed consortium of Bitcoin companies, exchanges, and stakeholders, Liquid uses a two-way peg mechanism to convert BTC into L-BTC and vice versa.
Liquid supports confidential transactions and tokenization, making it suitable for enterprise applications. If Bitcoin serves as the internet’s value layer and Lightning functions as a peer-to-peer payment network within a Bitcoin-driven financial system, then Liquid acts as the financial layer, adding multi-asset support and tools such as securities and commodities.
Compared to Lightning, Liquid is a Bitcoin Layer 2 solution focused on facilitating larger, more complex transactions like asset issuance and trading (e.g., securities and stablecoins). With built-in confidential transactions, Liquid hides transaction amounts and asset types, whereas Lightning provides privacy mainly through off-chain settlement. While Lightning excels at microtransactions and daily usage, Liquid better suits institutional finance, asset issuance, and cross-border settlements.
Over 50 exchanges currently utilize Liquid Network, having processed billions of dollars in transactions—demonstrating its effectiveness in boosting Bitcoin’s utility for institutional trading. Liquid enables faster settlement times for exchanges, enhancing market liquidity and allowing institutions to operate more efficiently and securely.
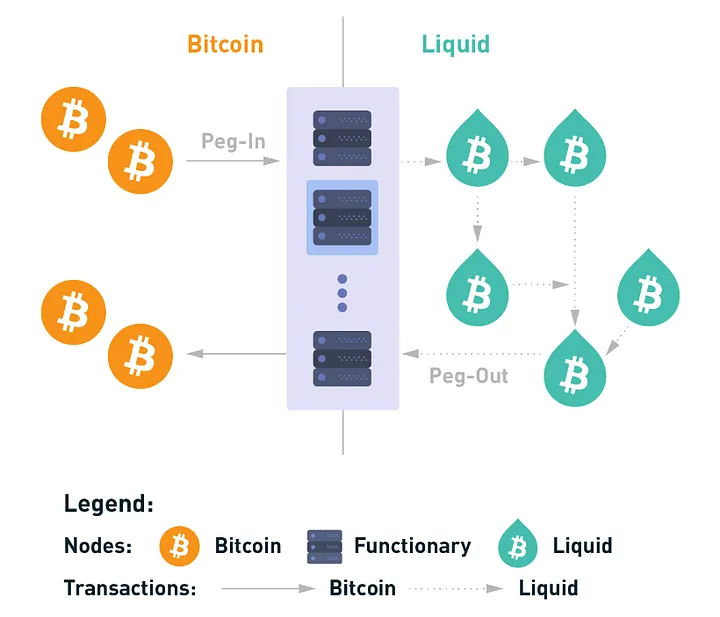
Image 2 Source:
https://docs.liquid.net/docs/technical-overview
(3) Rootstock Framework (RBTC)
Launched in 2015 and live on mainnet since 2018, Rootstock is the longest-running Bitcoin sidechain. Its uniqueness lies in combining Bitcoin’s Proof-of-Work (PoW) security with Ethereum-compatible smart contract capabilities. As an open-source, EVM-compatible Layer 2 solution, Rootstock provides access to a growing dApp ecosystem and aims for full trustlessness.
Like Liquid, Rootstock employs a two-way peg mechanism, enabling seamless exchange between BTC and RBTC. RBTC is the native currency on the RSK blockchain, used to pay miners for processing transactions and executing contracts. While Liquid emphasizes fast, private transactions and asset issuance, Rootstock expands Bitcoin’s DeFi and dApp landscape via smart contracts.
At the time of writing, Rootstock’s total value locked (TVL) exceeds $170 million, with a market cap of $380 million.
(4) B² Network
B² Network features a two-layer architecture: a Rollup layer and a Data Availability (DA) layer. The project aims to redefine perceptions of Bitcoin Layer 2 solutions.
B² utilizes ZK-Rollup as its rollup layer, implementing zkEVM to execute user transactions and generate corresponding proofs. User transactions are submitted and processed within the ZK-Rollup layer, where user states are also stored. Batched proposals and generated zero-knowledge proofs are forwarded to the DA layer for storage and validation.
The data availability layer consists of distributed storage, B² nodes, and the Bitcoin network. It ensures permanent replication of Rollup data, verifies zero-knowledge proofs, and achieves final confirmation on Bitcoin.
Distributed storage is a core component of B² Network, serving as a repository for ZK-Rollup transactions and associated proofs. Decentralized storage enhances security, reduces single points of failure, and guarantees data immutability.
To ensure data availability, B² writes a Tapscript into each Bitcoin block, anchoring the data path and zero-knowledge proof of that period’s Rollup data stored in decentralized storage. This process is cost-effective, generating approximately six transactions per hour. During verification, users compare their transactions against Taproot script data on Bitcoin Layer 1 to confirm the ultimate credibility of Rollup data.
Image 3
(5) Stacks Protocol (STX)
Since launching on mainnet in 2018 as Blockstack, Stacks has emerged as a leading Bitcoin Layer 2 solution.
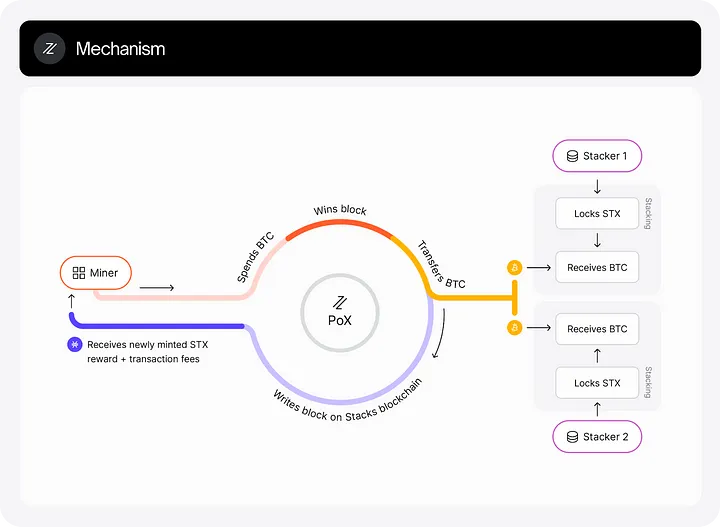
Image 4 Source: https://docs.stacks.co/stacks-101/proof-of-transfer
Stacks connects directly to Bitcoin, enabling the creation of smart contracts, dApps, and NFTs on Bitcoin, significantly extending its functionality beyond simple value storage. It employs a unique Proof-of-Transfer (PoX) consensus mechanism, tethering its security directly to Bitcoin without altering Bitcoin itself.
With over $99 million in total value locked (TVL), along with established infrastructure and a growing developer community, Stacks stands out as a major player in the space.
(6) Babylon
Babylon’s vision is to extend Bitcoin’s security to protect the decentralized world. By leveraging three aspects of Bitcoin—its timestamping service, blockspace, and asset value—Babylon transfers Bitcoin’s security to multiple Proof-of-Stake (PoS) chains, creating a stronger, unified ecosystem.
Babylon introduces a remote staking protocol using cryptographic innovation, consensus design, and optimized Bitcoin scripting to overcome the lack of native smart contracts. This allows Bitcoin holders to stake their BTC securely on PoS chains without bridging, wrapping, or custodial intermediaries, providing full slashing-based security guarantees.
A key feature is Babylon’s BTC Timestamping Protocol, which timestamps events from other blockchains onto Bitcoin, allowing those events to inherit Bitcoin’s secure timestamping capability. This effectively borrows Bitcoin’s strength as a timestamp server. The protocol enables fast unbonding, composable trust, lower security costs, and maximized liquidity for Bitcoin holders. Designed as a modular plugin, it integrates with various PoS consensus algorithms and forms the foundation for building restaking protocols.

Image 5
Having explored multiple technical solutions in the Bitcoin expansion ecosystem, it becomes clear that these innovations have significantly enhanced Bitcoin’s performance and functional scope, laying a solid foundation for diversified applications. However, as the ecosystem grows and technologies become increasingly complex, security concerns emerge as a critical issue. New extension technologies introduce additional risks and attack vectors, posing greater challenges to overall system security.
In this context, ensuring the security of the Bitcoin expansion ecosystem is vital—not only for protecting user assets but also for maintaining network stability and trust. Therefore, the following section details the 2023 Lightning Network vulnerability to provide valuable insights for future security measures.
Security Incidents in the Bitcoin Expansion Ecosystem
In October 2023, a potential security vulnerability was discovered in Bitcoin’s scaling technology—the Lightning Network. Developer Antoine Riard disclosed the details after identifying the flaw.
This vulnerability, known as “replacement cycling attacks,” could jeopardize funds flowing through the Lightning Network, causing transaction delays or failures in processing, potentially resulting in fund loss within Lightning channels.
This incident highlights the imperative of prioritizing security in a rapidly evolving expansion ecosystem. Developers and the community must continuously monitor and improve existing scaling solutions to defend against potential threats and safeguard user funds.

Image 6
Security Outlook for the Bitcoin Expansion Ecosystem
Despite significant advancements in transaction efficiency and functional diversity, the security of the Bitcoin expansion ecosystem requires ongoing reinforcement. This section discusses future directions and challenges in securing the ecosystem.
The Bitcoin expansion ecosystem aims to address mainchain throughput limitations while preserving security and decentralization.
Off-chain Transaction Trust Model: Off-chain technologies boost transaction speed, but developers must ensure robust trust mechanisms. For example, Lightning Network’s bidirectional payment channels rely on multi-signature schemes, with secure channel closure procedures essential to prevent fund freezing or loss.
Privacy vs. Transparency: Lightning Network enables private channel transactions, enhancing privacy but complicating regulatory oversight and potentially enabling malicious activity. Layer 2 networks must balance privacy and transparency—possibly through selective disclosure of transaction records—to improve compliance.
User Experience and Security: The complexity of expansion solutions increases user burden. For instance, managing Lightning channels can be unfriendly to average users, raising the risk of operational errors. Improving interfaces and simplifying tools can enhance usability and reduce security risks.
Looking ahead, the Bitcoin expansion ecosystem must continue optimizing technical designs to strengthen security, improve user experience, and enhance regulatory compliance—all while preserving decentralization and security—for more robust and widespread adoption.
Conclusion
The Bitcoin expansion ecosystem, powered by diverse Layer 2 solutions and innovative protocols, has dramatically enhanced Bitcoin’s functionality and transaction efficiency, advancing developments in smart contracts, DeFi, and NFTs.
Yet, as the ecosystem expands, security concerns grow and demand serious attention from developers and the community. Moving forward, while pursuing higher throughput and broader applications, the Bitcoin expansion ecosystem must continuously strengthen security mechanisms, optimize user experience, balance privacy with transparency, and ensure sustainable, resilient growth grounded in decentralization and security.
Read our full report at: https://bitslab.xyz/reports-page
About ScaleBit
ScaleBit, a security sub-brand under TechFlow (formerly BitsLab), is a blockchain security team dedicated to providing security solutions for Web3 mass adoption. Leveraging expertise in cross-chain and zero-knowledge proof technologies, we specialize in comprehensive and cutting-edge security audits for ZKP, Bitcoin Layer 2, and cross-chain applications.
The ScaleBit team comprises security experts with extensive experience in both academia and industry, committed to securing scalable blockchain ecosystems for widespread deployment.
About TechFlow
TechFlow is a security organization dedicated to safeguarding and building emerging Web3 ecosystems, aiming to become a trusted and respected leader in the Web3 security space. It operates three sub-brands: MoveBit, ScaleBit, and TonBit.
TechFlow focuses on infrastructure development and security auditing for emerging ecosystems, including but not limited to Sui, Aptos, TON, Linea, BNB Chain, Soneium, Starknet, Movement, Monad, Internet Computer, and Solana. The team demonstrates deep expertise in auditing multiple programming languages such as Circom, Halo2, Move, Cairo, Tact, FunC, Vyper, and Solidity.
The TechFlow team includes top-tier vulnerability researchers who have won international CTF awards and uncovered critical vulnerabilities in prominent projects such as TON, Aptos, Sui, Nervos, OKX, and Cosmos.
Visit TechFlow Official Website:
Visit ScaleBit Official Website:
TechFlow Official X (Twitter):
Join the Official Telegram Community:
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News