
A Brief Analysis of Zircuit's Sequencer Mechanism
TechFlow Selected TechFlow Selected

A Brief Analysis of Zircuit's Sequencer Mechanism
Zircuit has enabled the SLS mechanism, which is designed to isolate "malicious transactions."
Author: 0xTodd
With Zircuit's $ZRC approaching its official TGE, let's discuss an interesting mechanism within this project regarding the sequencer.
Zircuit has its own L2, which features a solution called "Sequencer Level Security (SLS)."
We all know that currently, transactions on L2s enter and exit through the project team's official sequencer. Of course, thanks to ZK proofs or challenge mechanisms, we generally don't worry too much about malicious behavior from sequencers.
Overall, the sequencer acts as a neutral party, faithfully executing every transaction without bias.
But even though the sequencer is neutral, can we push it one step further—can we make it join the ranks of the good guys?
This is where Zircuit introduces its SLS mechanism, designed specifically to isolate "malicious transactions."
Normally, how does an L2 transaction get onto the chain? It’s a simple four-step process:
1. User initiates and broadcasts the transaction
2. Transaction waits in the mempool
3. The sequencer, acting as a neutral party, packages it into a block
4. Transaction is confirmed on-chain
However, under the SLS mechanism, this becomes a five-step process:
1. User initiates and broadcasts the transaction
2. Transaction waits in the mempool
3. The sequencer, now acting as a proactive guardian, uses tools to check whether the transaction is potentially malicious
4. If no threat is detected, it proceeds to package the transaction into a block
5. Transaction is confirmed on-chain
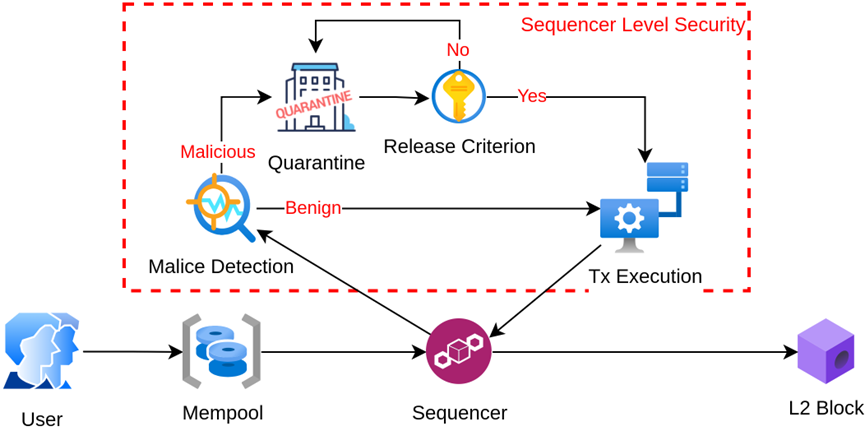
But what if a transaction appears suspiciously malicious? Starting from step 4, the flow changes:
4. If deemed suspicious, the transaction enters an isolation pool
5. After review in the isolation pool confirms it's safe, the sequencer proceeds with packaging
Or:
4. If deemed suspicious, the transaction enters an isolation pool
5. If the review identifies it as genuinely malicious, the sequencer refuses to include it in the block
The criteria for detecting malicious activity may involve using open-source libraries, assisted by AI analysis.
In the future, this could enable powerful outcomes—for example, stolen assets might be permanently blocked from being transferred or withdrawn back to L1. In today’s harsh "dark forest" on-chain environment, such capabilities are highly meaningful.
Of course, transaction screening inevitably risks false positives. However, I believe that by refining the isolation pool’s algorithms, these issues can be minimized as much as possible.
This is a double-edged sword. Blockchains emphasize permissionless access, and SLS slightly contradicts this principle. But from the perspective of regular users, such an L2 is indeed safer.
Overall, while there is a minor trade-off against permissionless ideals, the enhanced security—especially in protecting inexperienced users—is well worth it.
At the end, here is the original research paper on Zircuit’s SLS mechanism: https://arxiv.org/html/2405.01819v1
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















