
In-depth Analysis of the FHE (Fully Homomorphic Encryption) Sector: FHE is the Ideal Privacy Protection Technology
TechFlow Selected TechFlow Selected

In-depth Analysis of the FHE (Fully Homomorphic Encryption) Sector: FHE is the Ideal Privacy Protection Technology
Most FHE projects are scheduled to launch on mainnet from this year to the first quarter of next year.
Author: Maggie @ Foresight Ventures
TLDR:
-
Fully Homomorphic Encryption (FHE) is an emerging next-generation privacy-preserving technology worth investing in. FHE offers ideal privacy protection capabilities, though its performance still lags. We believe that with the influx of crypto capital, technological development and maturity will accelerate dramatically—just as we've seen with ZK in recent years.
-
In Web3, FHE can be applied to transaction privacy, AI privacy, and privacy-preserving co-processors. Among these, I am particularly bullish on privacy-preserving EVMs, which are more flexible and better suited for EVM than existing ring signatures, coin mixing techniques, or even ZK.
-
We have researched several outstanding FHE projects currently in development, most of which plan to launch mainnets between this year and next Q1. Among them, ZAMA leads in technical strength but has not announced any token issuance plans. Overall, we consider Fhenix to be the most promising FHE project after ZAMA.
1. FHE Is the Ideal Privacy-Preserving Technology
1.1 What FHE Does
Fully Homomorphic Encryption (FHE) is a form of encryption that allows arbitrary numbers of addition and multiplication operations to be performed directly on ciphertexts, producing encrypted results that, when decrypted, match the outcomes of performing those same operations on plaintext data—achieving “computable but invisible” data.
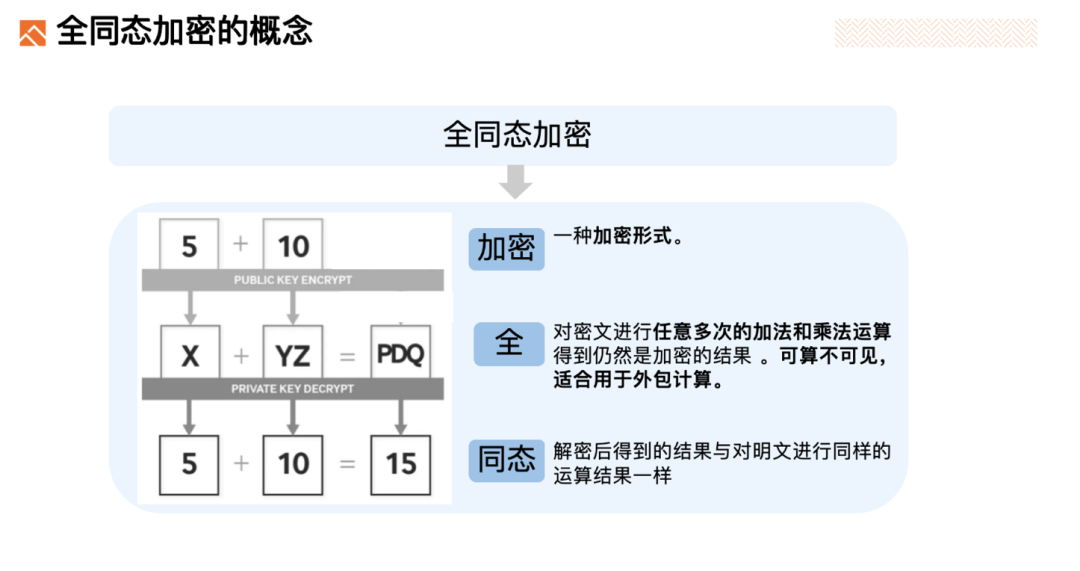
FHE is especially suitable for outsourced computation—you can delegate your data to external computing resources without worrying about data leakage.
To put it simply: imagine you run a company whose data is extremely valuable. You want to use powerful cloud services to process and compute this data, but you're concerned about potential leaks in the cloud. With FHE, you could:
-
Encrypt your data using FHE into ciphertext before uploading it to the cloud server. For example, the numbers 5 and 10 would be encrypted into symbols like "X" and "YZ".
-
When you need to perform computations—for instance, adding 5 and 10—you instruct the cloud server to execute the corresponding homomorphic operation on the ciphertexts "X" and "YZ", resulting in an encrypted output such as "PDQ".
-
After downloading the encrypted result from the cloud, you decrypt it locally and find that the decrypted plaintext matches exactly the result of 5 + 10.
Only you ever see the plaintext; all storage and computation on the cloud remain fully encrypted. This eliminates concerns over data leakage. Such a method of privacy protection is highly ideal.

-
Somewhat Homomorphic Encryption (SHE): Simpler and more practical. SHE supports only one type of homomorphic operation—either addition or multiplication.
-
Leveled Homomorphic Encryption: Enables both addition and multiplication on ciphertexts, but only up to a limited depth.
-
Leveled Fully Homomorphic Encryption: Allows arbitrary combinations of additions and multiplications without limit on number of operations, but imposes a complexity ceiling based on function depth.
-
Fully Homomorphic Encryption (FHE): Supports unlimited additions and multiplications with no constraints on complexity or operation count.
FHE represents the most challenging and ideal form of encryption, often referred to as the “Holy Grail of Cryptography.”
1.2 History
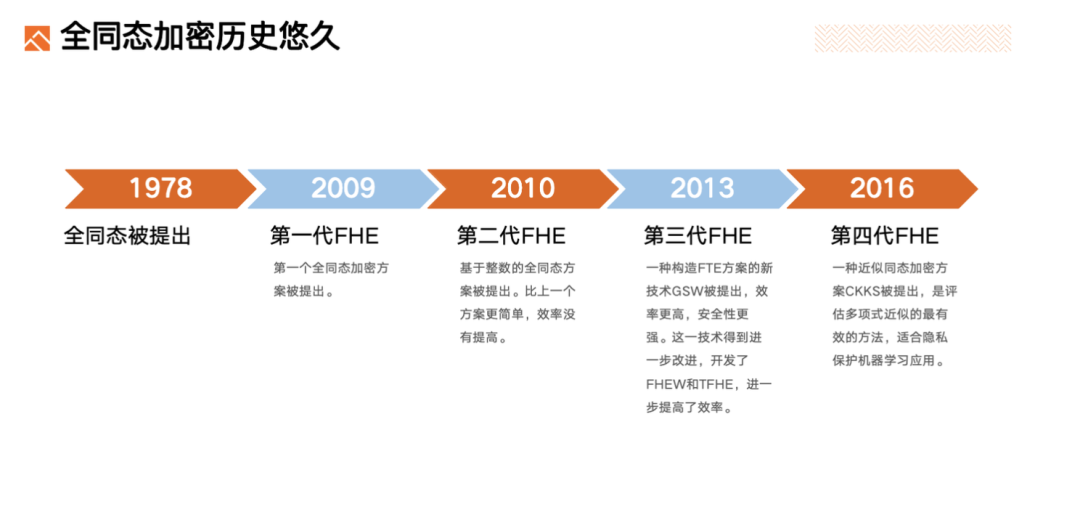
The history of Fully Homomorphic Encryption spans decades:
-
1978: The concept of FHE was first proposed.
-
2009 (First Generation): The first fully homomorphic encryption scheme was introduced.
-
2011 (Second Generation): An integer-based FHE scheme was developed—simpler than the prior version, but without performance improvements.
-
2013 (Third Generation): A new construction technique called GSW emerged, offering higher efficiency and stronger security. This led to further advancements with FHEW and TFHE, significantly improving speed.
-
2016 (Fourth Generation): The CKKS approximate homomorphic encryption scheme was introduced, becoming the most effective method for evaluating polynomial approximations—especially well-suited for privacy-preserving machine learning applications.
Today’s widely used homomorphic encryption libraries primarily implement third- and fourth-generation algorithms. Algorithmic innovation, engineering optimizations, blockchain-friendly designs, and hardware acceleration are all likely to emerge rapidly with increasing capital inflow.
1.3 Current Performance and Usability
Commonly used homomorphic encryption libraries:
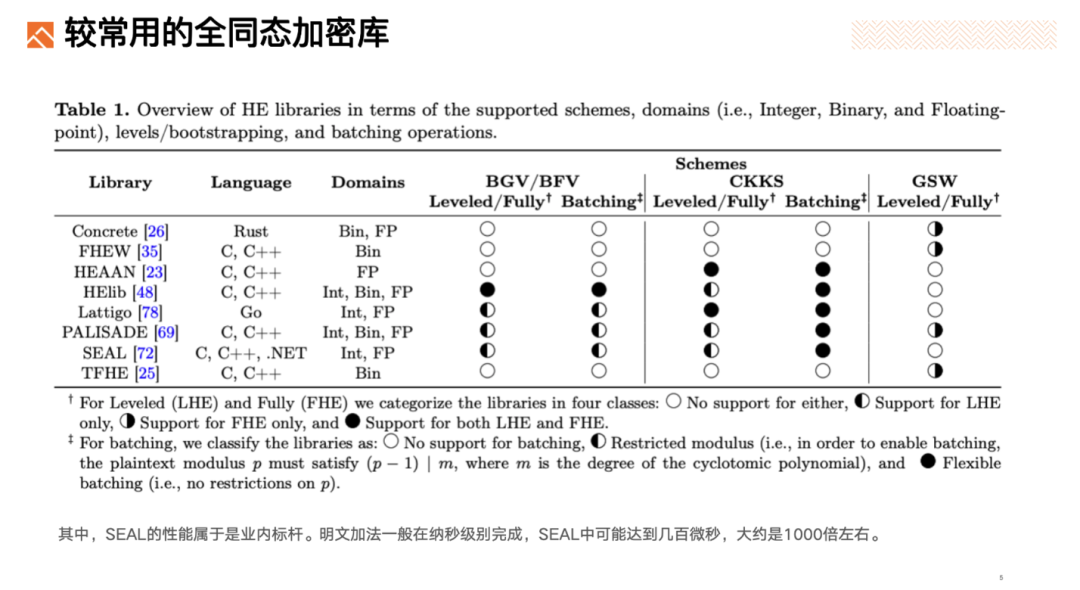
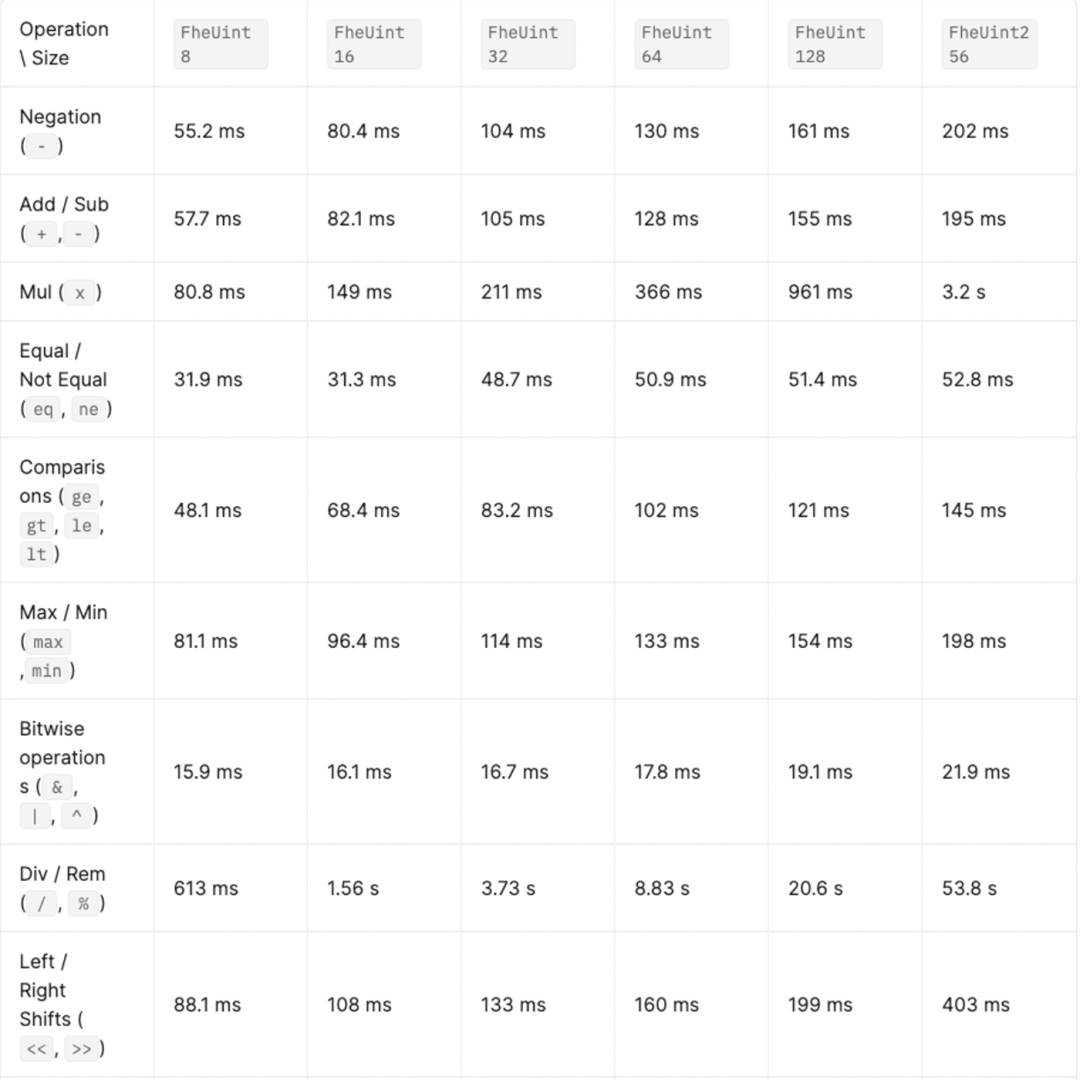
ZAMA TFHE Performance:
For example, ZAMA's TFHE takes around 200ms to perform 256-bit addition or subtraction. In contrast, plaintext computation takes tens to hundreds of nanoseconds—meaning FHE is roughly 10^6 times slower. Some optimized operations reduce this gap to about 1,000x slower. Of course, comparing ciphertext computation directly to plaintext isn’t entirely fair. Privacy comes at a cost—and especially so with FHE, the gold standard in privacy protection.
ZAMA plans to develop FHE-specific hardware to further boost performance.
1.4 Research Directions for FHE + Web3
Web3 is decentralized, and integrating FHE opens numerous research avenues:
-
Innovative FHE schemes, compilers, and libraries to make FHE faster, easier to use, and better adapted to blockchains.
-
FHE hardware to improve computational performance.
-
FHE + ZKP: Use FHE for private computation while employing zero-knowledge proofs to verify that inputs/outputs meet certain conditions or that FHE was correctly executed.
-
Preventing malicious behavior by compute nodes, potentially leveraging EigenLayer restaking.
-
MPC decryption schemes: Encrypted shared state typically uses MPC-sharded keys, requiring secure and high-performance threshold decryption protocols.
-
Data availability (DA) layer: Requires higher-throughput DA solutions—current options like Celestia may not suffice.
In summary, we believe Fully Homomorphic Encryption (FHE) is poised to become the next-generation privacy technology. While FHE offers ideal privacy protection, its current performance remains suboptimal. However, with growing crypto investment, we expect rapid advancement and maturation—similar to the explosive progress seen in ZK technologies in recent years. This space is definitely worth strategic positioning.
2. FHE Enables Various Privacy Applications in Web3—Privacy EVM Stands Out
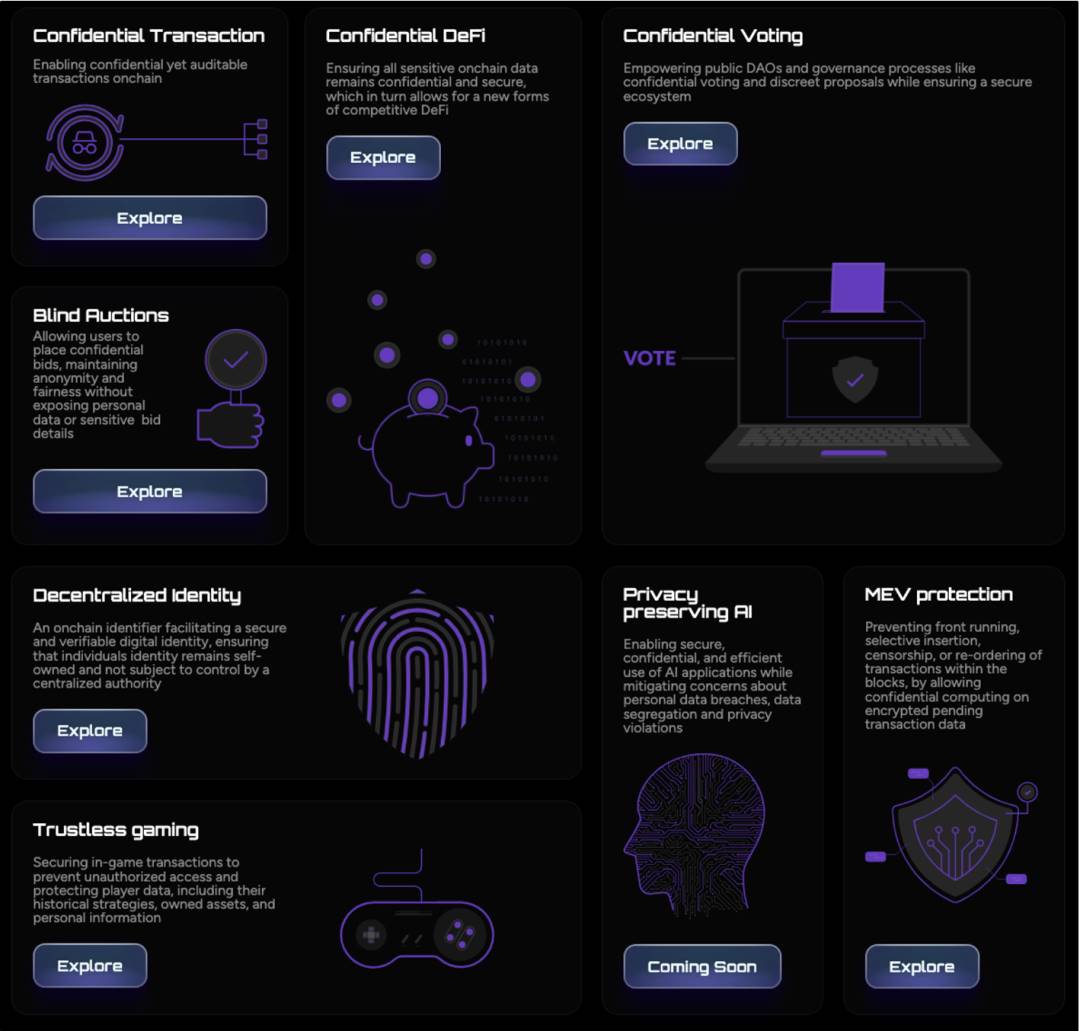
FHE falls under the broader privacy tech category, encompassing three core areas: transaction privacy, AI privacy, and privacy-preserving co-processors.
-
Transaction privacy includes private DeFi, voting, bidding, and MEV resistance.
-
AI privacy covers decentralized identity, and protecting AI models and training data.
-
Privacy-preserving co-processors offload FHE operations off-chain and return results on-chain—ideal for trustless games and other compute-heavy applications.
Of course, multiple privacy technologies exist. Comparing them highlights FHE’s unique advantages:
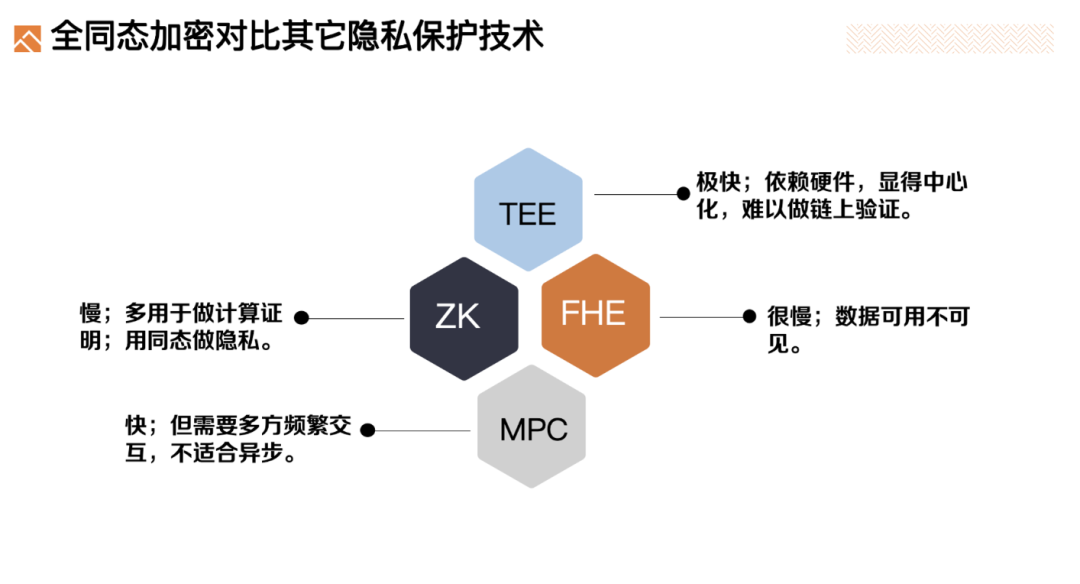
-
TEE (Trusted Execution Environment) is fast because data is processed in plaintext within secure hardware. But it relies on trusted hardware manufacturers, introducing centralized trust assumptions. Additionally, TEE verification often requires connecting to the manufacturer’s servers for remote attestation—making it incompatible with blockchain’s requirement for self-contained, trustless on-chain validation.
-
MPC (Multi-Party Computation) enables privacy-preserving collaborative computation among multiple parties. However, it usually requires all participants to be online simultaneously and interact frequently—unsuitable for asynchronous blockchain environments. MPC is mainly used today for distributed key management, such as in MPC wallets where private keys are split across devices and only reconstructed during signing via secure protocols.
-
ZKPs (Zero-Knowledge Proofs) are primarily used for proving correct execution of computations rather than privacy preservation per se. That said, ZK and homomorphic techniques are closely related—some privacy features in ZK systems also rely on homomorphic properties.
-
FHE performs computations entirely on ciphertext without needing intermediate data exchange—making it fully compatible with single-server or node-based environments. Unlike MPC, it doesn’t require constant interaction or real-time coordination. Compared to TEE, it’s trustless. Its only drawback is performance.
Therefore, as FHE performance improves, its privacy-preserving capability becomes increasingly well-suited for Web3.
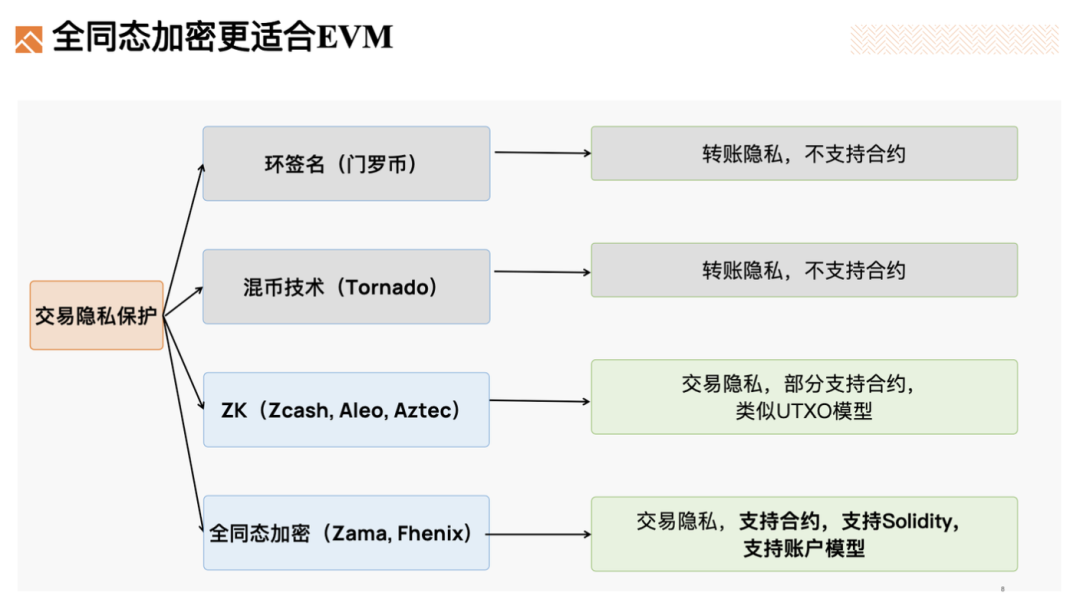
Moreover, in transaction privacy, FHE is especially well-adapted to EVM due to the following reasons:
-
Ring signatures and coin mixers do not support smart contracts.
-
Privacy-focused ZK projects like Aleo use UTXO-like models, whereas EVM relies on account-based models.
-
FHE supports both smart contracts and account models, making integration with EVM straightforward.
All things considered, a fully homomorphic EVM is highly compelling.
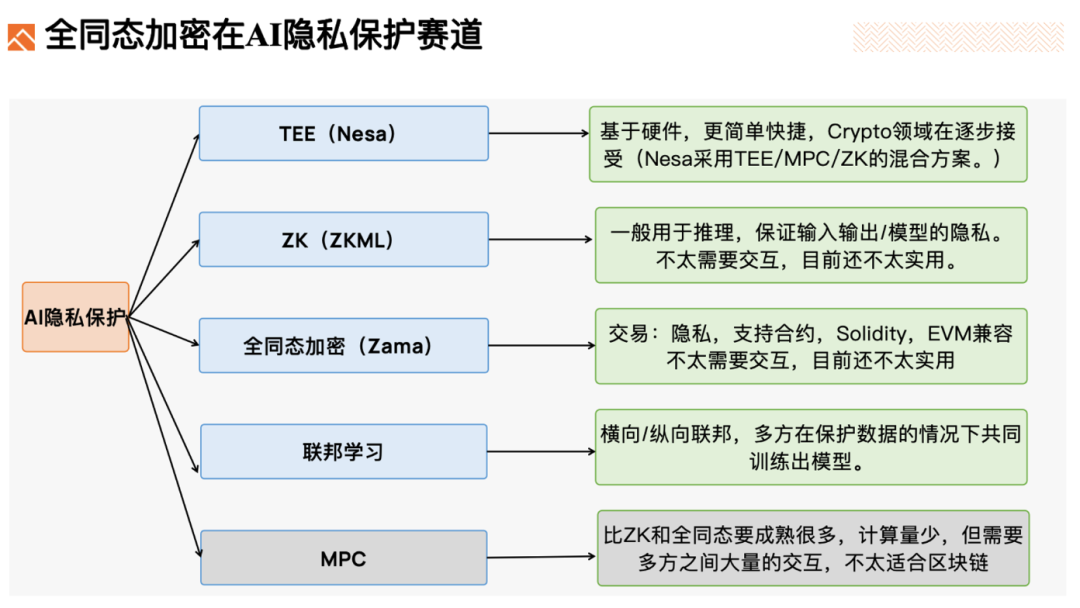
AI computations are already resource-intensive. Adding FHE—a complex cryptographic layer—may currently result in prohibitively low performance and high costs. I believe long-term AI privacy will likely rely on hybrid approaches combining TEE, MPC, ZK, and partially homomorphic encryption.
In summary, FHE in Web3 can enable transaction privacy, AI privacy, and privacy-preserving co-processors. Among these, I’m most excited about privacy-preserving EVMs—they’re more flexible and EVM-compatible than ring signatures, mixers, or even ZK-based solutions.
3. Most FHE Projects Will Launch Mainnets This Year to Early Next Year—We Believe Fhenix Is the Best FHE Project After ZAMA
We’ve analyzed several leading FHE projects currently in development. Here's a brief overview:
3.1 ZAMA (Tools)
-
Narrative: Delivering FHE for blockchain and AI
-
Tool: TFHE-rs, Rust implementation of TFHE
-
Tool: Concrete, compiler for TFHE
-
Product: Concrete ML, privacy-preserving machine learning
-
Product: fhEVM, privacy-preserving smart contracts
-
Team: CTO Pascal Paillier, renowned cryptographer
-
CTO & Co-founder: Pascal Paillier. PhD from Telecom ParisTech (1999), inventor of the Paillier cryptosystem. Has published extensively on homomorphic encryption since 2013—one of the top experts in FHE.
-
CEO & Co-founder: Rand Hindi. PhD in Bioinformatics from UCL (2011). Background in data science and advisory roles across multiple projects.
-
Funding: Over $82M raised over four years. Most recent Series A: $73M led by Multicoin Capital and Protocol Labs.
-
September 26, 2023: Seed round of $7M led by Multicoin Capital, with participation from Node Capital, Bankless Ventures, Robot Ventures, Tane Labs, HackVC, and Metaplanet.
3.2 Fhenix (EVM + AI)
-
Narrative: FHE co-processor / L2 FHE Rollup (EVM-compatible privacy L2)
-
Product: FHE-enabled Rollup supporting confidential smart contracts compatible with EVM. Developers build DApps using Solidity while preserving data privacy.
-
Product: FHE co-processor—offloads encrypted computation tasks from host chains (whether Ethereum, L2, or L3) to off-chain networks, greatly enhancing FHE operation efficiency.
-
Partnership: Collaborates with ZAMA, using their fhEVM; GitHub repo is forked from ZAMA’s library.
-
Partnership: Works with EigenLayer—nodes must re-stake via EigenLayer.
-
Team: Guy Itzhaki spent over seven years at Intel as Director of Business Development for Homomorphic Encryption and Blockchain.
-
Founder: Guy Zyskind, MIT PhD candidate, MSC from MIT (2016). Contributed to MIT Enigma privacy protocol—strong R&D background.
-
CEO: Guy Itzhaki – 7+ years at Intel, deep hands-on experience in privacy tech, served as Intel’s Director of Homomorphic Encryption & Blockchain Business Development.
-
Prof. Chris Peikert: Leading FHE cryptographer and cryptography lead at Algorand.
-
Funding: Raised $15M in Series A within one year, led by Hack VC, with participation from Foresight Ventures and others.
-
May 2024: $15M Series A led by Hack VC, joined by Foresight Ventures and others.
-
September 26, 2023: $7M Seed Round led by Multicoin Capital, with Node Capital, Bankless Ventures, Robot Ventures, Tane Labs, HackVC, and Metaplanet participating.
-
Roadmap: Testnet launch Q2 2024, mainnet Q1 2025.
-
Q2 2024: Launch threshold network.
-
Q3 2024: FHE Co-processor V0.
-
Q1 2025: Mainnet launch.
-
Q3 2025: FHE Co-processor V1.
3.3 Inco (EVM)
-
Narrative: Modular privacy computation layer / EVM chain support
-
Product: FHE-powered Rollup enabling confidential EVM-compatible smart contracts. Developers write DApps in Solidity with guaranteed data privacy.
-
Partnership: Collaborates with ZAMA, using fhEVM.
-
Team: Founder Remi Ga, former software engineer at Microsoft and Google, previously worked on Parallel Finance (DeFi).
-
Founder: Remi Gai – 6–9 months each as software engineer at Microsoft and Google (~2022), later involved in Parallel Finance (DeFi).
-
Tech Lead: Amaury A, core developer at Cosmos.
-
Funding: Latest Seed round: $4.5M led by 1kx.
-
February 2024: Inco Network raised $4.5M in seed funding led by 1kx, with participation from Circle Ventures, Robot Ventures, Portal VC, Alliance DAO, Big Brain Holdings, Symbolic, GSR, Polygon Ventures, Daedalus, Matter Labs, and Fenbushi.
-
Progress: Testnet launched March 2024, mainnet expected Q4 2024.
-
March 2024: Launched testnet featuring fhEVM, including examples of private ERC-20, private voting, blind auctions, and private DID.
-
Q2–Q3 2024: Expanded testnet with fhEVM.
-
Q4 2024: Mainnet launch.
-
2025 roadmap: FPGA hardware acceleration targeting 100–1,000 TPS.
3.4 Mind Network (AI & DePIN)
-
Narrative: Data privacy and private computation for AI and DePIN models/data.
-
Product: Originally positioned as a “private data lake” (2023)—secure storage and computation. Shifted focus in 2024 toward privacy for AI and DePIN data/models.
-
Partnership: Collaborates with ZAMA, using their FHE libraries.
-
Partnership: Works with Fhenix and Inco, using fhEVM for rollups.
-
Partnership: Integrates with Arweave for storing encrypted data.
-
Partnership: Collaborates with EigenLayer, Babylon, etc., implementing restaking for service nodes. Reference: https://mindnetwork.medium.com/fhe-secured-restaking-layer-scaling-security-for-ai-depin-networks-73d5c6e5dda3
-
Team: CTO George, former Cambridge University researcher.
-
Co-founder & CTO: George – ex-Cambridge researcher, former tech executive at multinational banks, with extensive fintech industry experience.
-
Funding: $2.5M Seed round over two years, incubated by Binance Labs.
-
June 20, 2023: $2.5M Seed Round led by Binance Labs, with HashKey, SevenX, and others participating.
-
Roadmap: Testnet live with restaking functionality. Remaining roadmap not yet disclosed.
3.5 Privasea (AI & DePIN)
-
Narrative: Privacy computing for AI and DePIN.
-
Product: Uses FHE to train ML models. Optimized Boolean gates in TFHE.
-
Product: FaceID—an FHE-based, privacy-preserving facial recognition system for Sybil resistance and KYC.
-
Integration: Leverages BNB Greenfield to store encrypted data.
-
Team: CTO Zhuan Cheng, PhD in Mathematics from University of Chicago, experienced in cryptographic R&D.
-
CEO: David Jiao – Previously raised $20M for an AI project and $4M for a blockchain project.
-
CTO Zhuan Cheng – PhD in Mathematics from University of Chicago, experienced in cryptography R&D, previously worked on NuLink’s ZK privacy project.
-
Funding: $5M Seed round in one year, incubated by Binance Labs.
-
March 2024: $5M Seed Round, incubated by Binance Labs, with MH Ventures, K300, Gate Labs, 1NVST, and others participating.
-
Roadmap: Testnet V2 launched April 2024, mainnet launch expected Q3 2024.
-
January 2024: Testnet V1.
-
April 2024: Testnet V2.
-
Q3 2024: Token Generation Event (TGE).
3.6 Optalysys (Tools)
Narrative: Homomorphic encryption hardware.
From the above analysis, ZAMA provides the foundational open-source FHE libraries powering many of these projects—undoubtedly the current technical leader. However, ZAMA has not announced any token plans, so our focus turns to Fhenix.
Fhenix aims to deliver a privacy-preserving EVM and confidential smart contracts. They plan to build Fhenix L2—an FHE-secured EVM enabling private transactions and DeFi. This L2 will include a threshold network for encryption/decryption tasks and deploy an FHE co-processor network capable of serving not only Fhenix but other EVM chains with homomorphic computation services.
Fhenix boasts strong technical talent—including experts from Intel in privacy computing, an MIT PhD who contributed to the Enigma privacy protocol, and the cryptography lead from Algorand.
In conclusion, we believe projects like ZAMA and Fhenix will bring truly ideal privacy tools to blockchain.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















