
ArkStream Capital: Why We Invested in the FHE Sector?
TechFlow Selected TechFlow Selected

ArkStream Capital: Why We Invested in the FHE Sector?
The FHE ecosystem contains infinite potential and opportunities, worthy of our continuous in-depth exploration and development.

Introduction
In the past, cryptographic technologies have played a pivotal role in advancing human civilization, particularly in the fields of information security and privacy protection. They not only provide robust safeguards for data transmission and storage across various domains but also inspired Satoshi Nakamoto’s creative integration of asymmetric encryption (public-private key systems) and hash functions in 2008 to design the proof-of-work mechanism that solved the double-spending problem—catalyzing the birth of Bitcoin, a revolutionary digital currency, and ushering in a new era for the blockchain industry.
As the blockchain industry continues to evolve at a rapid pace, a series of cutting-edge cryptographic technologies have emerged, among which zero-knowledge proofs (ZKP), secure multi-party computation (MPC), and fully homomorphic encryption (FHE) stand out. These technologies are now being widely applied in numerous scenarios—for example, ZKP combined with Rollup architectures addresses blockchain's "impossible trinity," while MPC integrated with public-private key systems drives mass adoption of user-facing applications. Fully Homomorphic Encryption (FHE), often regarded as one of the holy grails of cryptography, possesses unique capabilities that allow third parties to perform unlimited computations on encrypted data without decryption, enabling composable privacy-preserving computation on-chain and unlocking new possibilities across multiple sectors.
A Quick Overview of FHE
When discussing FHE (Fully Homomorphic Encryption), it helps to first understand the meaning behind its name. HE stands for homomorphic encryption—a technology whose core feature allows operations to be performed directly on ciphertexts such that these operations correspond exactly to equivalent operations on the underlying plaintexts, thereby preserving the mathematical properties of encrypted data. The “F” in FHE signifies a breakthrough: this homomorphism supports an unlimited number of both addition and multiplication operations on encrypted data.
To aid understanding, we use a simple linear function as an illustrative encryption algorithm and demonstrate additive and multiplicative homomorphism through single operations. In practice, however, real-world FHE relies on far more complex mathematical algorithms that demand extremely high computational resources (CPU and memory).
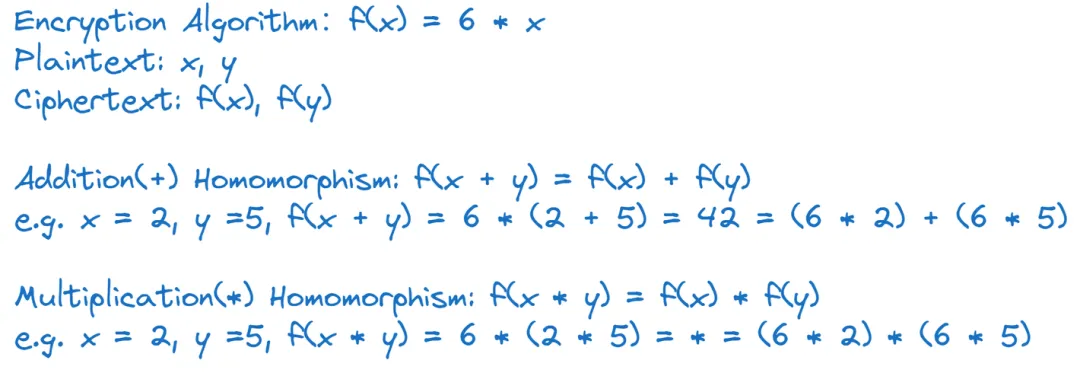
Although the mathematical foundations of FHE are profound and intricate, we will not delve deeply into them here. It is worth noting that beyond FHE, there exist partially homomorphic encryption (PHE) and somewhat homomorphic encryption (SHE), differing primarily in the types of operations supported and the number of allowable computations. While they also enable computation on encrypted data, their capabilities are limited compared to FHE. For simplicity, we won’t explore these variants further in this article.
Within the FHE landscape, several prominent companies are actively engaged in research and development. However, Microsoft and Zama stand out due to their exceptional open-source libraries, which offer unmatched usability and influence. Their contributions provide developers with stable and efficient implementations of FHE, significantly accelerating the technology’s advancement and broader adoption.
Microsoft SEAL: A fully homomorphic encryption library meticulously developed by Microsoft Research, supporting both full and partial homomorphic encryption. SEAL offers high-performance C++ interfaces and integrates numerous optimization techniques to dramatically improve computational efficiency.
Zama’s TFHE: An open-source library dedicated to high-performance fully homomorphic encryption. TFHE provides services via a C-language interface and employs advanced optimization algorithms aimed at achieving faster computation speeds and lower resource consumption.
The simplified workflow for using FHE can be outlined as follows:
-
Key Generation: Use an FHE library or framework to generate a public-private key pair.
-
Data Encryption: Encrypt the data intended for FHE processing using the public key.
-
Homomorphic Computation: Perform various operations—such as addition and multiplication—on the encrypted data using the homomorphic computing functions provided by the FHE library.
-
Decrypt Result: Authorized users decrypt the final result using the private key when needed.
In practical FHE applications, the management scheme for decryption keys (including generation, transfer, and usage) is especially critical. Since encrypted data must eventually be decrypted under certain conditions, the decryption key becomes central to ensuring the security and integrity of both original and processed data. While key management strategies share similarities with traditional approaches, FHE’s unique characteristics allow for even more rigorous and fine-grained designs.
For blockchains, leveraging threshold-based multi-party computation (Threshold Multi-Party Computation, TMPC) presents a highly promising solution. This approach enables multiple participants to jointly manage and control the decryption key, requiring a predefined threshold number of participants to collaborate before successful decryption occurs. This not only enhances key security but also reduces the risk of compromise from any single node, offering strong protection for FHE deployment in decentralized environments.
Laying the Foundation with fhEVM
From a minimal-intrusion perspective, the ideal way to implement FHE on blockchains is to encapsulate it as a general-purpose smart contract library, ensuring portability and flexibility. However, this requires the smart contract virtual machine to natively support specialized instruction sets for the complex mathematical operations and cryptographic primitives required by FHE. If the virtual machine lacks such support, deep architectural modifications are necessary to integrate FHE seamlessly.
Given its widespread adoption and long-standing validation, the Ethereum Virtual Machine (EVM) naturally emerges as the preferred platform for implementing FHE. Yet few have ventured into this space. Notably, Zama—the same company behind the open-source TFHE library—has made significant strides. Beyond providing the foundational TFHE library, Zama has positioned itself as a technology firm focused on applying FHE to AI and blockchain, launching two major open-source products: Concrete ML and fhEVM. Concrete ML focuses on privacy-preserving machine learning, enabling data scientists and ML practitioners to train and run inference models on sensitive data without exposing private information. The other product, fhEVM, is a fully homomorphic EVM that supports privacy-preserving computation using Solidity, allowing developers to incorporate FHE into Ethereum smart contracts for secure and private computation.
Based on available documentation, the core features of fhEVM include:
-
fhEVM: Provides FHE operation support through built-in functions implemented as precompiled contracts at the non-bytecode level. Additionally, it dedicates specific regions of EVM memory and storage for handling, reading, writing, and validating FHE ciphertexts;
-
Decryption mechanism based on distributed threshold protocols: Supports global FHE keys for mixed encrypted data shared across users and contracts, with decryption keys stored on-chain and managed asynchronously via threshold multi-party computation among multiple validators;
-
Solidity contract library lowering developer barriers: Introduces FHE-specific data types, operations, decryption calls, and encrypted outputs;
Zama’s fhEVM provides a solid foundation for FHE in blockchain applications. However, given Zama’s primary focus on R&D, its solutions remain largely technical, with less emphasis on engineering implementation and commercialization. As a result, deploying fhEVM in real-world settings may encounter unforeseen challenges, including steep learning curves and performance bottlenecks.
Building the Ecosystem: FHE-Rollups
On its own, fhEVM cannot constitute a standalone project or complete ecosystem—it resembles one of many diverse clients within the Ethereum ecosystem. To become an independent project, fhEVM must be built upon a public chain architecture or adopted within Layer 2/Layer 3 frameworks. Developing FHE-native blockchains inevitably faces the challenge of redundant and wasteful computation across distributed validator nodes. In contrast, Layer 2 / Layer 3 execution layers can offload computation to a smaller set of specialized nodes, reducing computational overhead by orders of magnitude. Recognizing this, Fhenix pioneers the integration of fhEVM with Rollup technology, proposing an advanced FHE-Rollups Layer 2 solution.
Considering that ZK Rollups rely on complex zero-knowledge proof mechanisms requiring massive computational power to generate validity proofs, combining them directly with FHE—which itself demands heavy computation—poses significant technical hurdles. Therefore, at this stage, adopting Optimistic Rollups instead of ZK Rollups represents a more practical and efficient choice for Fhenix.
Fhenix’s tech stack comprises several key components: a modified version of Arbitrum Nitro’s fraud prover capable of executing fraud proofs in WebAssembly, allowing FHE logic to be compiled and securely executed in WASM; fheOS, the core library providing all functionalities needed to integrate FHE logic into smart contracts; and the Threshold Service Network (TSN), a crucial component responsible for hosting network-wide secret-shared keys. TSN uses advanced secret-sharing algorithms to split the decryption key into distributed fragments, enhancing security and performing decryption tasks when required.
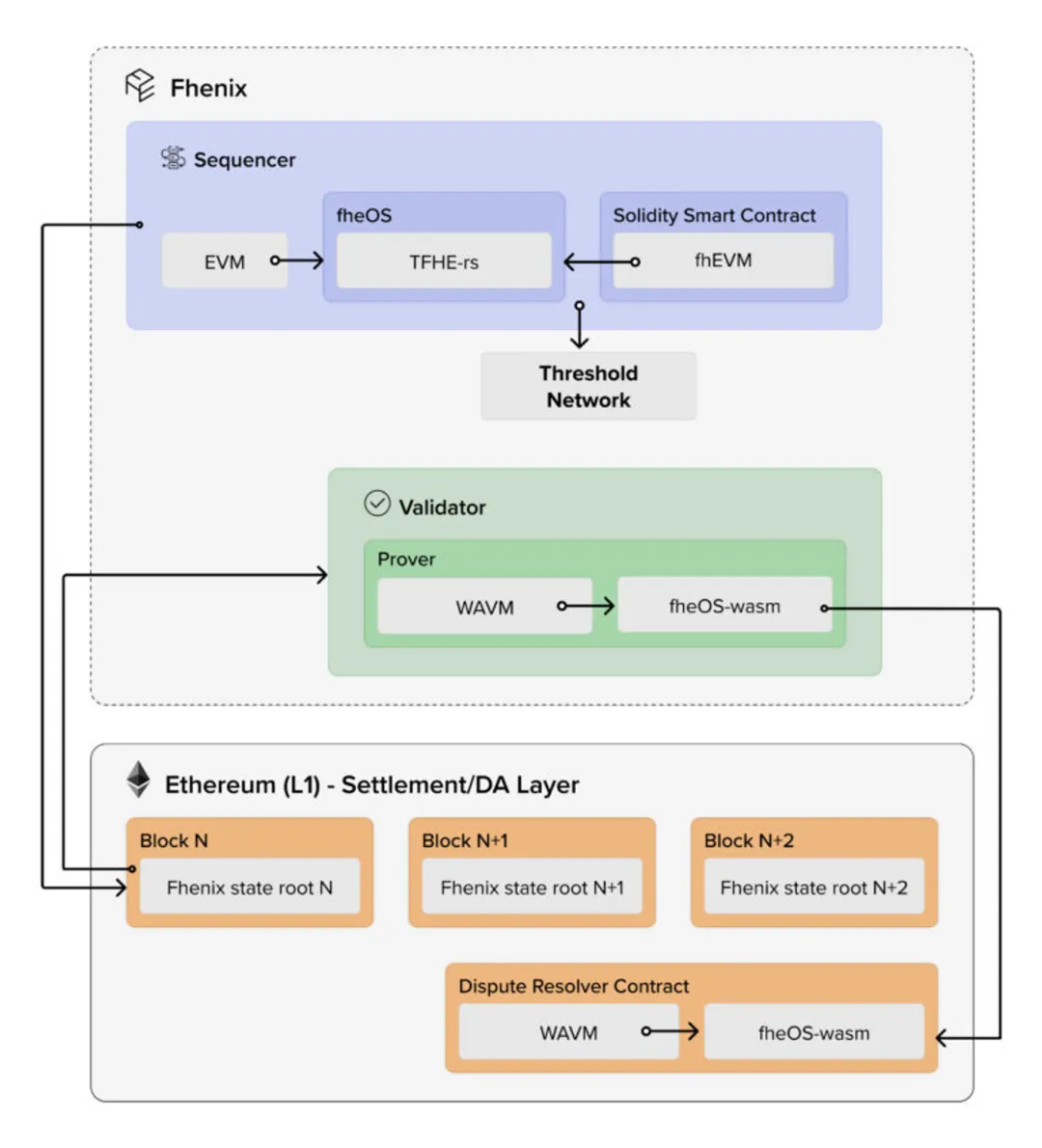
Leveraging this architecture, Fhenix launched its first public release, Fhenix Frontier. Though an early version with limitations and missing features, it already offers comprehensive documentation covering smart contract libraries, Solidity APIs, development tooling (e.g., Hardhat/Remix), and frontend JavaScript libraries. Developers and ecosystem builders interested in FHE are encouraged to explore the official docs.
Chain-Agnostic FHE Coprocessors
Building on FHE-Rollups, Fhenix introduces the Relay module to empower various public chains, L2s, and L3s to access FHE Coprocessor functionality. This means even Host Chains that do not natively support FHE can now leverage its powerful privacy-preserving computation. However, since FHE-Rollups typically involve a 7-day dispute period, widespread adoption is constrained. To overcome this, Fhenix partners with EigenLayer, utilizing EigenLayer’s restaking mechanism to create a faster, more flexible channel for FHE Coprocessor services, greatly improving efficiency and responsiveness.
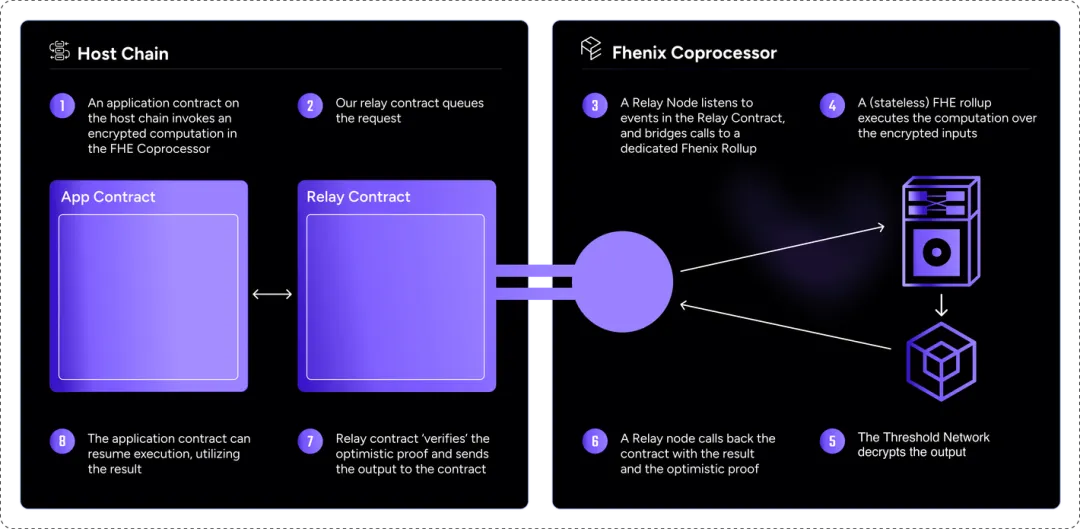
The process for using FHE Coprocessors is straightforward:
-
Application contract on Host Chain invokes FHE Coprocessor for encrypted computation
-
Relay contract queues the request
-
Relay nodes monitor the Relay contract and forward the call to a dedicated Fhenix Rollup
-
FHE Rollup executes the homomorphic computation
-
Threshold network decrypts the output
-
Relay nodes return the result and optimistic proof to the contract
-
Contract verifies the optimistic proof and forwards the result to the caller
-
Application contract proceeds with execution using the returned result
How to Get Involved with Fhenix
If you're a developer, dive into Fhenix’s documentation and start building your own FHE-powered applications to explore their real-world potential.
If you're a user, try out dApps running on Fhenix’s FHE-Rollups to experience firsthand how FHE enhances data security and privacy protection.
If you're a researcher, we strongly recommend studying Fhenix’s materials in depth to better understand FHE principles, technical details, and future applications, enabling more impactful contributions in your field.
Promising Application Scenarios for FHE
FHE shows immense promise, particularly in areas like on-chain gaming, DeFi, and AI—we firmly believe it holds vast potential and broad applicability in these domains:
-
Privacy-Preserving On-Chain Games: FHE strengthens financial transactions and player actions within game economies, effectively preventing real-time manipulation and ensuring fairness. It also anonymizes player activity, significantly reducing risks of exposure to financial assets and personal information, thereby comprehensively safeguarding user privacy.
-
DeFi / MEV: As DeFi activity grows, many transactions fall prey to MEV attacks in the so-called "dark forest." FHE offers a solution by protecting sensitive data—such as position sizes, liquidation thresholds, and slippage settings—without compromising computational integrity. By integrating FHE, on-chain DeFi ecosystems can become healthier and significantly reduce harmful MEV behaviors.
-
AI: Training AI models requires large datasets. When individual data is involved, protecting personal privacy becomes paramount. FHE emerges as an ideal solution, enabling AI models to process encrypted data without ever exposing sensitive personal information during training.
Community Recognition of FHE
Technological progress depends on more than just technical brilliance—it requires sustained academic research and active community engagement. In this regard, FHE, hailed as a holy grail in cryptography, has already gained wide recognition for its transformative potential. In 2020, Vitalik Buterin expressed strong support for FHE in his article *Exploring Fully Homomorphic Encryption*. Recently, he reiterated this stance on social media, further amplifying attention and calling for greater investment and effort toward advancing FHE. Meanwhile, a growing number of new projects, nonprofit research initiatives, educational organizations, and increasing market funding suggest that a technological breakthrough may be on the horizon.
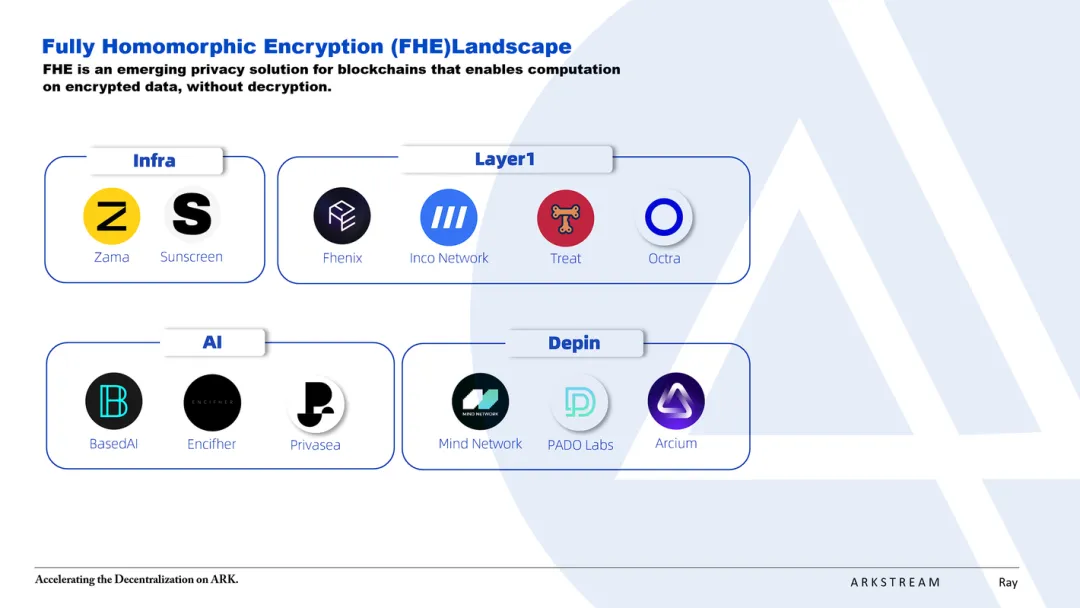
The Emerging FHE Ecosystem
In the early stages of FHE ecosystem development, alongside foundational players like Zama and standout projects like Fhenix, several other notable initiatives deserve close attention:
-
Sunscreen: Developed an FHE compiler enabling conversion from traditional programming languages to FHE-compatible code, designed decentralized ciphertext storage, and delivers FHE capabilities to Web3 apps via SDKs
-
Mind Network: Leverages EigenLayer’s restaking mechanism to build an FHE network enhancing security for AI and DePIN networks
-
PADO Labs: Introduced zkFHE, combining ZKP and FHE, and built a decentralized computing network atop it
-
Arcium: Formerly Solana’s privacy protocol Elusiv, recently rebranded and pivoted to a parallel confidential computing network powered by FHE
-
Inco Network: Built on Zama’s fhEVM, focusing on optimizing FHE computation costs and efficiency to develop a full-fledged Layer 1 ecosystem
-
Treat: A collaboration between the Shiba team and Zama, developing an FHE-powered Layer 3 to expand the Shiba ecosystem
-
octra: An FHE network developed using OCaml, AST, ReasonML, and C++, supporting isolated execution environments
-
BasedAI: A distributed network enabling FHE-enhanced LLM models
-
Encifher: Previously known as BananaHQ, now renamed Rize Labs, focusing on FHEML (FHE for Machine Learning)
-
Privasea: An FHE network developed by NuLink’s core team using Zama’s Concrete ML framework, aiming to protect data privacy during AI model inference
For nonprofit research and education, we highly recommend FHE.org and FHE Onchain, which offer invaluable resources for academic advancement and community education.
Due to space constraints, we cannot list every outstanding project in the FHE ecosystem. But rest assured, this space brims with untapped potential and opportunities, well worth continued exploration.
Conclusion
We are highly optimistic about the future of FHE technology and hold great expectations for the Fhenix project. Once Fhenix launches its mainnet, we anticipate that applications across diverse domains will be elevated by FHE’s capabilities. We firmly believe that this innovative and dynamic future is already within reach.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















