Web3 Privacy Experts Unveil zkTLS and Its Applications
TechFlow Selected TechFlow Selected

Web3 Privacy Experts Unveil zkTLS and Its Applications
zkTLS represents not only improved availability of Web2 data within the Web3 ecosystem, but also a shift in data ownership.
Author: Xavier, Co-founder@Primus Lab
Ph.D. in Cryptography with over 10 years of research experience in privacy technologies such as MPC/ZK/PPML
Despite the unprecedented development of ZK technology represented by zkSNARKs in the blockchain industry, it remains far from the anticipated ultimate end game. On one hand, zkRollups have provided certain performance advantages for Ethereum, but as on-chain applications dwindle, the dilemma of having infrastructure without usage persists. On the other hand, ZK technology itself has yet to incubate high-value zk applications—whether privacy-centric on-chain transactions and confidential payments, or various zk+XXX (zkEmail, zkLogin, zkPassport, etc.)—many of which still suffer from unclear demand, forced zk integration, or technological gold-plating without truly solving real-world pain points.
What is zkTLS?
A common example: how do you prove to someone else that your bank account holds a large amount of money? The traditional method is to have your bank issue an asset verification document. This paper proof carries the bank's official seal, providing clear authenticity.

(Image source: internet)
But what if the question shifts: how do you prove your credit score, e-commerce spending, or gaming hours to someone else? We cannot expect websites holding your personal data to individually endorse or provide proof services for you. Alternatively, you might convince others via screenshots, but this process could still be seen as forged and risks leaking additional sensitive information.
zkTLS is a data validation technology based on the TLS protocol that objectively provides authenticity proofs for any internet-based data.
The earliest zkTLS product was PageSigner, released in 2015 by the TLSNotary project for Chrome browsers. From its name, it’s easy to see that TLSNotary originally aimed to build a tool capable of proving the authenticity of web data. In fact, it wasn't until 2020, when the ChainLink team published the DECO paper, that zkTLS gradually entered industry awareness, revealing another type of oracle capable of retrieving private off-chain data.
Objectively speaking, prior to 2023, zkTLS technology was only at the "usable" stage when integrating with real business needs, far from being "user-friendly," with single proof generation often taking several minutes. In 2023, given the excessive communication overhead caused by secure multi-party computation (MPC) in earlier zkTLS implementations, reclaim proposed a proxy-mode-based zkTLS approach, using traditional zkSNARKs along with a trusted proxy node to achieve verifiable TLS data. Mid-2023, the Primus team (formerly known as “PADO”) leveraged the garble-then-prove technique combined with the quicksilver algorithm to improve the overall performance of MPC-based zkTLS by more than 10x. Additionally, within proxy mode, replacing traditional zkSNARKs with the quicksilver algorithm also boosted performance by over 10x. Currently, Primus’s zkTLS technology performs well enough to meet the requirements of various business scenarios.
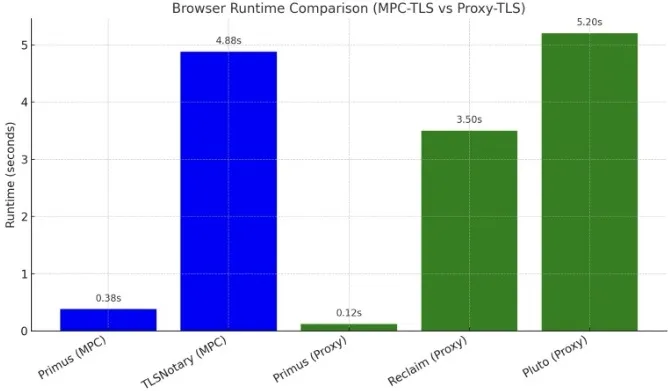
Readers can refer to relevant benchmarking tests for more details on zkTLS performance:
(https://hackmd.io/@-fI_Eu_rR8qs02aOhOPWNg/HkRyz5OF1g)
zkTLS Technology Classification
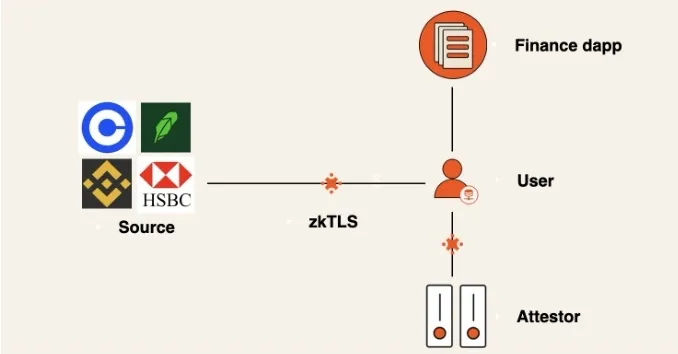
Typically, zkTLS achieves authenticity verification of web data through a third-party Attestor. The Attestor acts like an observer, verifying that user data (from server response messages) indeed originates from a specified data source (note: here, data source refers to the server domain and related API endpoints) by "reading" request and response messages during TLS protocol execution.
The TLS protocol generally consists of two phases: handshake and session. During the handshake phase, the client and server perform a series of communications to jointly compute a session key used for encrypted communication in the next phase. In the session phase, the client sends requests to the server, which responds accordingly, with all messages encrypted using the session key to prevent third-party eavesdropping.
Based on different core components, zkTLS mainly falls into two categories: those based on secure multi-party computation (MPC) and those based on proxy techniques.
MPC Mode
The MPC mode primarily relies on secure multi-party computation. In this scheme, the Attestor and Client use a two-party computation (2PC) protocol to simulate the client-side portion of the TLS handshake. This means that after the handshake phase, the client does not directly obtain the full session key. Only after the Attestor receives the ciphertext response will it send its key share to the client, enabling decryption of all ciphertexts.
«Quick Fact: MPC stands for Secure Multi-Party Computation, typically involving two parties (i.e., 2PC) or three or more parties (referred to as MPC). Whether 2PC or MPC, all participating parties must ensure their individual inputs remain hidden while collaboratively completing a specific computational task—such as computing average salaries without revealing individual wages, or multiple data providers jointly training an AI model without exposing their respective datasets.»
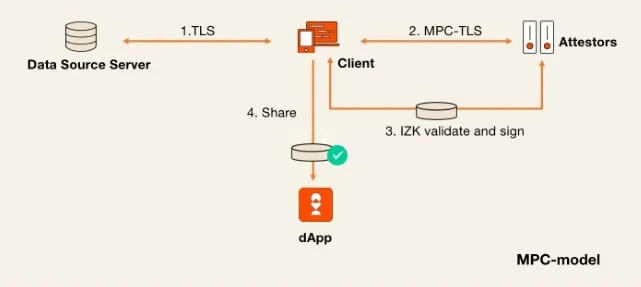
The intuitive flow of MPC mode is as follows:
-
Handshake Phase: The Client and Attestor run a 2PC protocol to jointly compute the session key. During this process, both the Client and Attestor hold only shares of the session key, not the complete key.
-
Request Encryption: The Client and Attestor run the 2PC protocol again to compute the encrypted request data.
-
Response Handling: The Client receives the encrypted response from the Data Source and forwards it to the Attestor.
-
Key Unsealing and Verification: The Attestor sends its key share to the Client, allowing the Client to reconstruct the full session key. The Client then uses this key to decrypt the response and proves to the Attestor that the ciphertext is valid and satisfies predefined security properties. Note that the Client and Attestor do not use 2PC to decrypt the response; decryption is independently performed by the Client once it obtains the full key.
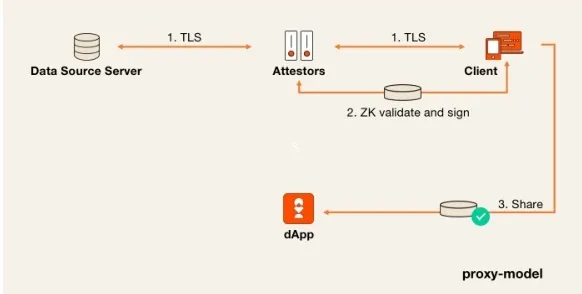
Proxy Mode
In proxy mode, the Attestor acts as an intermediary, forwarding all TLS interaction data (including handshake information and encrypted communication data) between the Client and the Data Source. At the end of the TLS protocol, the Client must prove the validity of the ciphertext to the Attestor using zero-knowledge (ZK) proofs.
The design motivation behind proxy mode is to eliminate the 2PC protocol used in MPC-TLS, as 2PC represents the most computationally expensive component. By reducing computational complexity, the overall protocol execution efficiency is improved.
What Can zkTLS Bring Us?
The core value of zkTLS lies primarily in verifiability.
Prior to this, there were no effective methods to support users in providing trustworthy personal data under trustless conditions. This verifiability offers broad flexibility and practicality, including:
-
- Non-intrusive to data sources: Data sources are unaware they are interacting with a new zkTLS protocol and simply follow standard TLS protocol logic. This means zkTLS can theoretically integrate widely with any underlying TLS-based data sources or API services, although unusually frequent interactions may still trigger risk control mechanisms on the data source side.
-
- Universality: “What you see is what you can prove”—in theory, any web data, whether public or private, sensitive or non-sensitive, can be attested by an Attestor via zkTLS.
-
- Blockchain-agnostic: zkTLS is purely an off-chain cryptographic operation. Its output is typically data signed by the Attestor, which can be verified off-chain or later validated within smart contracts on-chain.
-
- Privacy-friendly: Leveraging zero-knowledge proofs, zkTLS supports minimal disclosure for sensitive information sharing. Simply put, for response messages returned by the TLS protocol, constraints can be defined on computable data (numerical types), such as age > 18 or balance ≥ 10,000, with the corresponding proof results embedded in the output data.
zkTLS Application Cases
You might wonder: what are potential use cases for data sharing based on zkTLS? Below are some ideas we believe worth exploring:
-
Low-collateral lending: Proving off-chain credit scores, bank balances, income, and other financial data via zkTLS allows lending protocols to offer better capital efficiency.
-
Off-chain identity verification: Acquiring user KYC information from traditional institutions and utilizing it within on-chain financial protocols.
-
P2P transactions: Creating a peer-to-peer digital goods marketplace. Buyers can use zkTLS to prove ownership transfer of items such as e-tickets, domains, in-game assets, or even fiat currency; sellers can control token transfers via smart contracts.
-
AI Agents: With zkTLS, we can ensure AI Agent behaviors are fully reliable—verifying market-influencing statements from social media agents, unlocking AI trading bots, enabling AI participation in DAO governance, and reducing trust costs throughout these processes.
-
Fan verification: For example, allowing users to prove their fan status and receive rewards from KOLs/artists.
-
Social account tipping/payments: Enables anyone to send crypto assets to one or more social accounts without knowing their wallet addresses. Conversely, users must provide social account proof via zkTLS to claim tokens under their name.
-
Social login: Using zkTLS to verify ownership of social platform accounts and develop a new login mechanism. Users can log in using accounts from any web service provider, eliminating reliance on specific Google or Meta accounts.
A New Paradigm for Valuable Data Verification and Computation
zkTLS represents not just enhanced usability of Web2 data within the Web3 ecosystem, but also a shift in data ownership. Data previously locked within platforms can now flow freely, stay privacy-protected, and become programmable. This evolution transforms users from passive recipients into true data owners.
As zkTLS adoption accelerates, we will witness combinatorial effects brought by verifiable data—more verified data enabling more powerful applications. Meanwhile, as these verified data move across applications carrying value, a new challenge arises: how to compute over such critical data while ensuring correctness of the results.
In fact, computation on sensitive on-chain data often relies on more complex cryptographic techniques like Fully Homomorphic Encryption (FHE). By redesigning FHE algorithms integrated with zero-knowledge proofs, Primus has introduced the zkFHE (Verifiable Fully Homomorphic Encryption) protocol, supporting trustless confidential computation on-chain. This extends zkTLS—a cross-cyber-space data verification technology—into the realm of data computation, creating possibilities for unlocking further innovative applications.
Disclaimer:
This article was written by Xavier from the Primus team. Some content may involve conflicts of interest; readers should evaluate accordingly.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News