Mechanism Capital: Why We Believe zkTLS Is an Opportunity Now?
TechFlow Selected TechFlow Selected

Mechanism Capital: Why We Believe zkTLS Is an Opportunity Now?
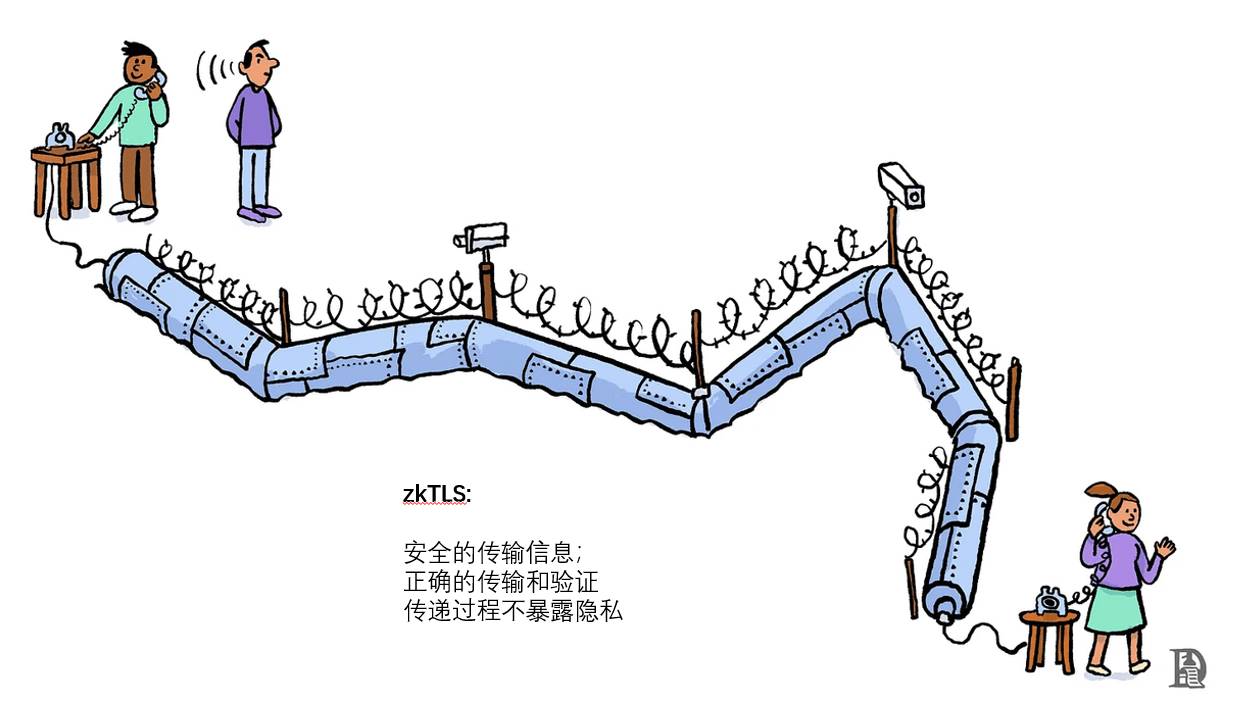
zkTLS makes it possible to create Web proofs without compromising privacy.
Author: Mechanism Capital
Translation: TechFlow
Key Takeaways:
-
Why is this an opportunity? It represents a significant improvement over existing oracle solutions, enabling protocols to expand their reach beyond current user bases to a global and diverse audience.
-
What is TLS? TLS (Transport Layer Security) is the "s" in "HTTPS," securing communication between servers and users.
-
zkTLS makes it possible to create web proofs without sacrificing privacy. A web proof is a zero-knowledge proof used to verify information from Web2 data sources.
-
The next evolution of oracles. Oracles powered the growth of decentralized finance (DeFi), and zkTLS will bring the world into DeFi. The limitation of oracles lies in their reliance on APIs for data ingestion.
-
zkTLS is currently more of a buzzword, as no existing technical implementation actually uses zkTLS at the message handshake level (the TLS handshake that occurs when you open a website in your browser).
-
Benefits: Protects user anonymity, security, and internet data privacy. Users can privately and verifiably share data—such as bank balances or average social media likes—without revealing personal information.
-
This extends the reach of crypto protocols beyond their current user base to a larger and more diverse audience. The guarantee here is limited to the authenticity of the data and its source.
-
zkTLS was first introduced in 2016 but has only recently gained attention. Currently, there are only a few use cases, such as exporting social media followers/following lists.
-
Opportunity to integrate Web2 data with Web3. This evolution will enable crypto protocols to solve real-world problems faster. The opportunity lies in protocols built on zkTLS, not the infrastructure itself.
-
Reclaim Protocol leads in development and market appeal. Other players include TLS Notary, zkPass, and Pluto.
Problem
The world lacks verifiability. In a decentralized and adversarial environment, many simple things we do in physical and digital spaces are hard to prove.
HTTPS offers limited verifiability. You can only verify data authenticity when you access it yourself. If you try to show that data to a third party, you lose verifiability because the third party cannot confirm whether what you’re showing is a legitimate copy of what you saw.
Web3 faces a “chicken-and-egg” problem—all relevant internet activities are siloed. There’s no bridge between Twitter and Instagram, between Instagram and Zora, or between Spotify and Sound.xyz. This may be acceptable for early adopters, but it's a major hurdle for time-sensitive users.
zkTLS, or zero-knowledge Transport Layer Security, offers a way to solve data provenance without compromising privacy. It is a zero-knowledge proof built atop the TLS protocol.
In practice, it enables users to securely export data from any website. There is no guarantee of data truthfulness—only of data integrity and provenance.
Opportunity: Mass Adoption of Web2 Data in Web3 Applications
This is the natural evolution of oracles. The issue with oracles is that they are limited to public data, expensive, and difficult to scale into personal identifiable information and Web2 contexts.
How does it work?
Three technical approaches to achieving HTTPS verifiability:
-
Raw TEE (Trusted Execution Environment) / SGX Attestation
-
A TEE is a secure area within the main processor of a device. It ensures that external processes or computations—even those with higher privileges—cannot access or alter data inside it. They protect critical data and also authenticate and verify computations performed within.
-
Attestation allows a remote party to verify that the intended software is running securely within an enclave on a fully patched, Intel SGX-enabled platform.
-
The TEE model does not use zero-knowledge proofs; it relies instead on the security guarantees of the TEE itself.
-
TEE models depend on trust assumptions about hardware providers.
-
-
Proxying Requests via Intermediary Third Parties
-
Uses the browser’s proxy functionality as a middleman between the user and the website. The proxy can generate zero-knowledge proofs.
-
This approach may be blocked, as bottlenecks exist at the proxy level.
-
The proxy model does use zero-knowledge proofs, but only after the TLS handshake is completed (the handshake your browser performs when opening any site).
-
-
Multiparty Computation (MPC)-Based Approach
-
Implements MPC across a network of nodes instead of letting the browser hold its own key. Thus, keys are held neither by the browser nor by any single node.
-
MPC solutions are costly, so in practice, 2PC (two-party computation) is often used instead of full MPC across multiple nodes.
-
This model provides strong security assurances, but setting up MPC requires significant network communication, resulting in high overhead.
-
The MPC/2PC model does not use zero-knowledge proofs; instead, it conducts the handshake via MPC.
-
MPC carries inherent collusion risks, which can be mitigated through various strategies.
-
The MPC-based model is generally considered best-in-class for security. However, only the proxy model uses zero-knowledge proofs to ensure data integrity. None of the models implement zero-knowledge proofs at the TLS handshake layer—thus falling short of the true definition implied by the term "zkTLS." As such, zkTLS remains more of a buzzword than a fully matured technology in practice.
Unique Selling Proposition (USP)
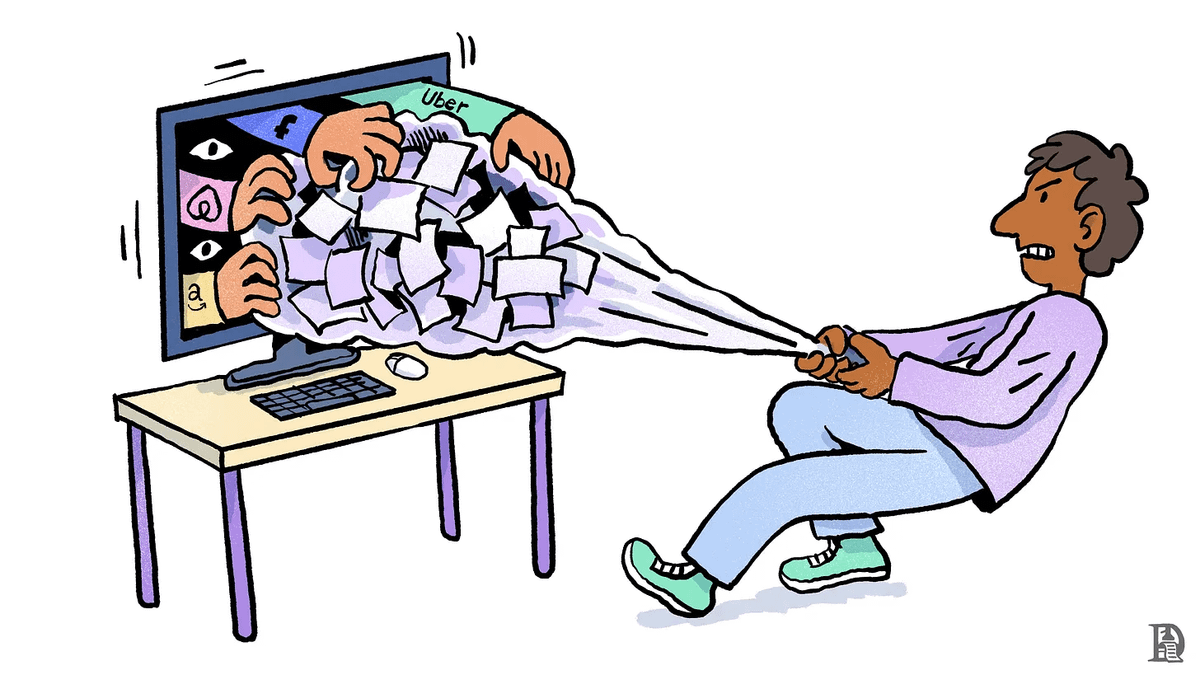
When accessing data via APIs, that data can easily be shut down. If tech companies don’t want apps using their data for token distribution or off-platform financial activity, they can simply disable those APIs. With web proofs, however, as long as a user can access data on a website via HTTPS, that data cannot be blocked.
This means nearly any Web2 data can be securely brought on-chain without requiring any action—or ability to prevent it—from the data source.
zkTLS ushers in a more open future internet where data is no longer siloed. This disrupts the unique selling propositions of traditional Web2 business models. Users will be able to integrate and use new types of interoperable frontends.
Use Cases
-
Zero-Knowledge KYC (zkKYC)
-
More expressive oracles, such as weather oracles, sports score oracles, and stock market pricing oracles
-
Web3 airdrops targeted at Web2 users. Enables connectivity between Web3 and Web2 users and defends against sybil attacks.
-
Looking back at how quickly we've built new financial systems, our industry has particularly excelled in incentive design. Rather than spending massive ad budgets hoping users will come, blockchains have industrialized user behavior shaping and participation rewards.
-
Airdrops are among the most effective user engagement strategies we’ve seen—activities that don’t require millions in upfront investment. The current main limitation: Web3 protocols can only reach users with on-chain history.
-
-
Current on-chain users represent only a small fraction of these applications’ ideal target audiences.
-
Airdrop targets have expanded from a few million existing crypto users to most of the global population. They’ll need a wallet to receive airdrops, but this process can be simplified through account abstraction or chain abstraction.
-
Integration of Web3 with real-world loyalty programs
-
A breakthrough moment for zero-knowledge peer-to-peer payments
-
A fiat on/off-ramp channel enabling P2P transactions. One party sends fiat via a Venmo-like service, the other sends cryptocurrency, with automatic release upon payment completion via web proof. Requires either a smart contract or centralized solution acting as custodian.
-
Anonymous sharing of information and insights
-
Tokenization of domains. Turn domains into liquid assets with verified ownership. Ownership proofs could be used as collateral in DeFi. This would allow Web2 assets to be tokenized on Web3—similar to ENS, but for website domains.
-
Ride-sharing platforms: Import a user’s number of rides on Uber to build a competing ride-sharing platform.
-
E-commerce personalization: Import a user’s purchase preferences from Amazon to offer targeted discounts.
-
Blockchain economics: Use users’ off-chain activity data to enable economic functions on-chain.
Example Use Cases include:
-
Proving your bank balance and that the data comes from a specific bank
-
Proving you are over 21 without revealing your birthday
-
Proving ESPN.com reported the outcome of a sports match
-
Proving a user purchased concert tickets
-
Proving an Uber driver has completed 1,000 trips and maintains a 5.00 rating.
Related Projects
Reclaim Protocol
https://www.reclaimprotocol.org/
Reclaim Protocol’s zkTLS infrastructure enables both Web2 and Web3 users to generate verified credentials via zero-knowledge proofs, securely verifying online data without exposing sensitive information. Unlike other solutions, it requires no app installation or browser extension, allowing users to seamlessly share selected data with third-party applications.
Reclaim Protocol is one of the most advanced in the space, open-source, with over 40 verified templates and 240 community-built ones. They currently use HTTPS proxies to forward user responses and plan to decentralize their nodes soon. We should reach out to explore investment opportunities and synergies to better understand protocols being built on their infrastructure.
Pluto
Pluto allows you to add verifiable data from any internet source. They’ve demonstrated integrations with Venmo and Reddit, implementing a zero-knowledge version of TLSNotary.
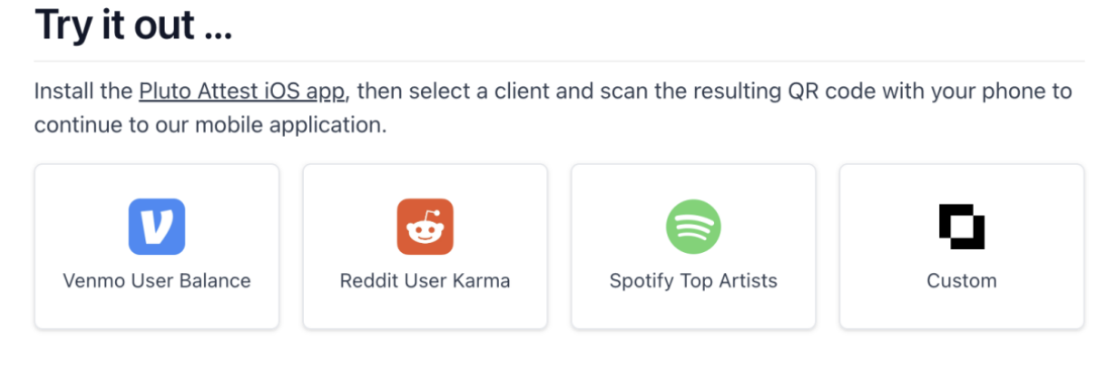
Current prototype use cases involve developers integrating web proofs into their apps. Pluto explores multiple directions in applied cryptography, developing tools involving zero-knowledge proofs (ZKP), multiparty computation (MPC), fully homomorphic encryption (FHE), and witness encryption (WE).
Pluto is built by a small team of engineers and operators from Stripe, Aztec, Y Combinator, Hubspot, and Uber. You can learn more about the team on their website.
TLSNotary
TLSNotary is an open-source protocol designed to verify the authenticity of TLS data while preserving user privacy. It uses a multiparty computation (MPC) solution. Its name draws inspiration from a 2013 Bitcointalk post aiming to let Bitcoin buyers prove to a third-party arbitrator that they successfully transferred funds to a seller.
Opacity Network
Opacity’s zero-knowledge proof protocol connects provers and verifiers within minutes, enabling trustless sharing and verification of information.
DECO (Chainlink)
This is Chainlink’s pioneering zkTLS protocol and research initiative.
PADO Labs
PADO uses standard TLS protocols combined with multiparty computation to collaboratively process data. They claim to be building the world’s first zkFHE decentralized computing network. In 2023, they raised $3 million from Arweave, Hash Global, and Berkeley Blockchain Xcelerator.
zkPass
zkPass raised $2.5 million from firms like Sequoia and Binance to develop TransGate—a platform enabling users to selectively and privately verify data on any HTTPS website and connect it to the Web3 world. Currently in pre-alpha testnet, zkPass already supports over 50 verified templates across sites like Uber, Instagram, and Coursera.
They claim to have generated over 315,000 zero-knowledge proofs and use zkSBTs for authentication. Additionally, users can create custom templates via a Chrome extension—a significant advantage.
Conclusion
As cryptocurrency reaches a pivotal moment, web proofs emerge as a powerful tool connecting early adopters with the mainstream. By generating verifiable on-chain data from any Web2 source, web proofs extend crypto incentives beyond current users to a broader, more diverse audience.
zkTLS technology will gradually bring the world on-chain. Combining crypto-optimized incentive mechanisms with real-world Web2 applications is a path to success. I believe this represents a major breakthrough in crypto use cases.
Open Questions
-
How can economic incentives be designed to ensure honest behavior from third-party provers?
-
How does the system handle website updates to their data structures? How can systems relying on third parties maintain reliability?
-
How can we prove the existence of something across long or varying timescales?
-
Currently, zkTLS focuses on “proving”—i.e., that an action was done at a point in time. But for protocols, data changes may be more valuable—for example, updating credit risk or airdrop eligibility based on Web3 behaviors.
-
How do end users connect with their websites today? Most projects currently rely on Chrome extensions or Appclips.
Additional Resources
Non-technical, Beginner
What is zkTLS
Semi-technical, Intermediate
Beginner's Guide to zkTLS
MPC TLS
Technical, Advanced
-
Whitepapers
-
Research Papers
-
Open-Source Projects
These resources allow readers to select appropriate materials based on their technical proficiency to deepen their understanding of the related technologies and applications.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News