111 million ZK tokens suddenly stolen—Is ZKsync's story coming to an end?
TechFlow Selected TechFlow Selected

111 million ZK tokens suddenly stolen—Is ZKsync's story coming to an end?
ZKsync is heading toward Endgame—not the cinematic happy ending where superheroes defeat the boss, but the black-screen game over when you get wiped out because you're just too bad.
Recently, the industry has been collectively experiencing misfortunes, with security incidents occurring frequently.
On the evening of April 15, ZKsync, once hailed as one of the "Four Heavenly Kings" among Ethereum Layer 2 solutions, was caught in a token security incident—but not disclosed by the project team first. At 9:00 PM last night, community members revealed that ZKsync had minted 110 million tokens on-chain and already sold 66 million of them. However, according to the official vesting schedule, team and investor tokens remain locked.
Following this news, ZK dropped below 0.04 USDT within half an hour, hitting a low of 0.03972 USDT. South Korean exchange Bithumb announced it had detected security issues with ZK and temporarily suspended deposits and withdrawals until market stability could be ensured. At that time, ZKsync responded via its official Discord, stating it was conducting an investigation.
As the community speculated whether the team had maliciously inflated supply, ZKsync issued an official statement:
After investigation, the security incident was caused by compromised private keys of administrator accounts for three airdrop distribution contracts. The attacker invoked the sweepUnclaimed() function, minting approximately 111 million unclaimed ZK tokens from the airdrop contract—increasing circulating supply by about 0.45%, valued at around $5 million. However, this attack only affected the ZK token airdrop distribution contract. The ZKsync protocol, the ZK token contract, all three governance contracts, and all active token cap minter roles were unaffected. The team is currently coordinating with exchanges on recovery efforts and urges the attacker to return the funds to avoid legal consequences.
The investigation is ongoing, with detailed updates to be released later.
The Token Was Actually Stolen Two Days Earlier
However, the official explanation failed to convince the community. On-chain data shows the hacker successfully minted 111 million ZK tokens from the airdrop contract as early as 8:00 PM on April 13 (UTC+8), immediately beginning cross-chain transfers and sales. As of now, the address holds only about 44.68 million ZK tokens, worth roughly $2.12 million—still representing 0.34% of total supply.
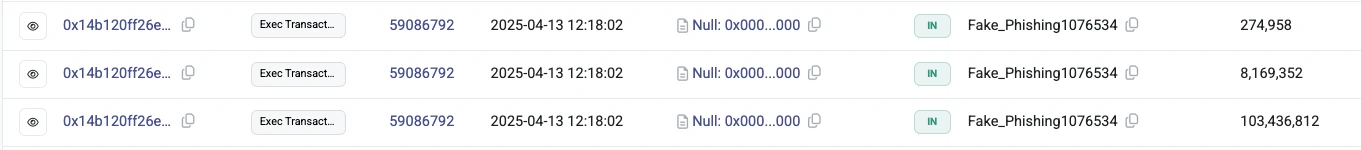
The hacker succeeded in the attack on April 13
It can thus be preliminarily concluded that last night's price drop wasn't entirely due to the hacker’s selling pressure, but mainly triggered by the leak of the theft scandal, causing panic-driven sell-offs within the community.
Although the ZK price has rebounded above 0.045 USDT, a critical question remains: if the airdropped tokens were stolen long ago, why did it take two days for the issue to surface through the community? Was ZKsync genuinely unaware, or deliberately concealing the breach to prevent chaos? If ZKsync only learned of the incident via community channels and then began investigating, one must wonder—has this former "heavenly king" project become nothing more than a makeshift operation, oblivious even when their system was breached?
The community reasonably suspects possible insider involvement: could it be that the administrator key for the airdrop contract was held by just one individual? And now that the theft has occurred, what will be done about the stolen funds? Can they be frozen or repurchased? These questions await answers from the team. Odaily Planet Daily will continue to follow up on the final investigation results.
What Kind of Endgame Is ZKsync Heading Toward?
This incident highlights the risks posed by centralized administrative privileges within otherwise decentralized systems. Strong access control and smart contract security are equally important; the security of admin keys directly impacts the overall safety of crypto projects and cannot be treated separately.
Yet, while suspicion looms and the hacker continues happily selling tokens, ZKsync’s founder confidently posted on X: “In this attack, the project code wasn’t leaked—only an admin key was compromised. That’s precisely why ZK is the endgame.”
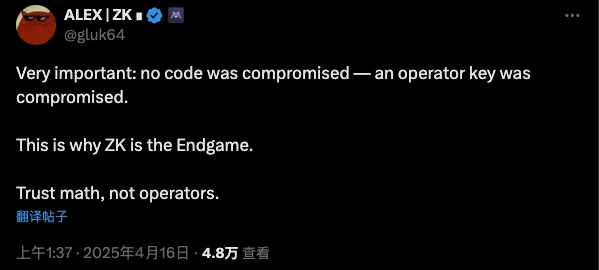
ZK-based validity proofs have long been touted as more secure than Optimistic Rollups (Op), often considered the ultimate technical form for Ethereum L2s—what some call the "Endgame." Yet, despite not affecting core protocol tokens, the weak safeguards around the airdrop distribution contract feel like stuffing ancient straw inside an otherwise high-tech fortress wall.
In response to community criticism asking, “As a leader in the ZK space, why didn’t you foresee this attack?” the founder boldly replied, “We couldn’t predict a black swan event.” But private key compromise is one of the most common attack vectors in blockchain—akin to everyday phishing threats. To label such a foreseeable risk a “black swan” simply because no preventive measures were taken reveals dangerously poor security awareness.
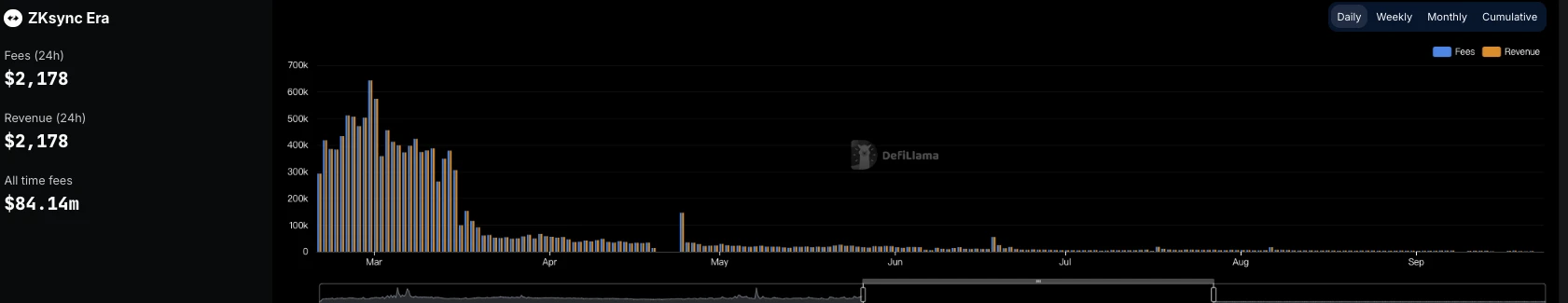
Moreover, how has ZKsync performed in real-world adoption? According to DeFiLlama, ZKsync currently has a TVL of $55.29 million, ranking 52nd. Its daily chain income stands at just $2,178, having remained under $5,000 since September 2024. In contrast, Arbitrum still generates over $10,000 daily. ZKsync has effectively become a so-called “ghost chain.”
ZKsync may indeed be approaching an endgame—but not the cinematic kind where heroes triumph over villains. Rather, it resembles the black screen after a player gets wiped out in a game for being too weak. Before the final defeat, let’s hope ZKsync at least tries to rescue its trapped investors.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News