TonBit: 2024 TON Ecosystem Overview and Security Research Report
TechFlow Selected TechFlow Selected

TonBit: 2024 TON Ecosystem Overview and Security Research Report
The report analyzes recent security incidents in the TON ecosystem projects and provides targeted vulnerability optimization measures to enhance the overall security level of the ecosystem.
Author: TonBit
1. Introduction
This report is jointly published by TonBit, a sub-brand of BitsLab — a Web3 blockchain security auditing company — and its partner TONX. As blockchain technology continues to evolve and expand into broader applications, the TON ecosystem has maintained strong growth momentum in 2024, attracting significant attention from developers, investors, and users.
In 2024, the TON ecosystem made notable progress in technological innovation, real-world application deployment, and community development, further solidifying its position within the blockchain space. However, as the ecosystem rapidly expands, security concerns have become increasingly prominent. Addressing evolving security threats effectively has emerged as a critical challenge for the TON ecosystem.
2. Overview of the TON Ecosystem
2.1 Introduction to the TON Ecosystem
Basic Introduction and Architecture
TON (The Open Network) is a blockchain and digital communication protocol created by Telegram, aiming to build a fast, secure, and scalable blockchain platform that provides decentralized applications and services to users. By integrating blockchain technology with Telegram's communication capabilities, TON achieves high performance, high security, and high scalability. It enables developers to build various decentralized applications and offers distributed storage solutions. Compared to traditional blockchain platforms, TON boasts faster processing speeds and higher throughput, utilizing a Proof-of-Stake (PoS) consensus mechanism.
2.2 Why Choose TON?
While competing against Bitcoin and Ethereum in terms of liquidity and community strength, TON demonstrates unique advantages. Vitalik Buterin’s blockchain trilemma describes the challenges Layer 1 networks face in balancing security, scalability, and efficiency. While Bitcoin and Ethereum each have their strengths and weaknesses, TON overcomes many of these challenges through its flexible and sharded PoS architecture.
2.2.1 Flexible and Sharded PoS Architecture
TON adopts a Proof-of-Stake consensus mechanism and achieves high performance and multifunctionality through Turing-complete smart contracts and an asynchronous blockchain structure. Its lightning-fast and low-cost transactions are supported by the chain’s flexible and sharded architecture, which allows seamless scaling without sacrificing performance. Dynamic sharding involves initially developing separate shards with distinct purposes that can run simultaneously and prevent large-scale backlogs. TON has a block time of 5 seconds and finality in under 6 seconds.
The existing infrastructure is divided into two main components:
● Masterchain: Handles all critical and essential protocol data, including validator addresses and staked token amounts.
● Workchain: Secondary chains connected to the masterchain, containing all transaction information and various smart contracts, with each workchain capable of having different rules.
2.2.2 Expanded Use Cases and Advantages
The TON Foundation, operated by the core TON community as a DAO, provides various forms of support to projects within the TON ecosystem, including developer assistance and liquidity incentive programs. In 2024, the TON community achieved significant progress across multiple fronts:
● Launch of TON Connect 2.0: Offers an intuitive way to connect wallets and applications, improving user experience.
● TON Verifier: A smart contract checker developed by the Orbs team, enhancing contract reliability.
● Blueprint Development Tools: Assist developers in writing, testing, and deploying smart contracts.
● Sandbox Developer Toolkit: Suitable for diverse use cases ranging from enterprises to government.
● Release of Tact Language Beta Version: Enables a more powerful programming environment.
● Global Expansion of TON Society: International centers launched in multiple cities worldwide.
● DeFi Liquidity Incentive Program: Provides funding to projects, promoting sustainability in the TON DeFi sector.
2.3 Overview of TON's Development Direction and Goals for 2024
TON’s development roadmap includes several exciting initiatives such as a stablecoin toolkit, sharding tools, and native bridges for BTC, ETH, and BNB.
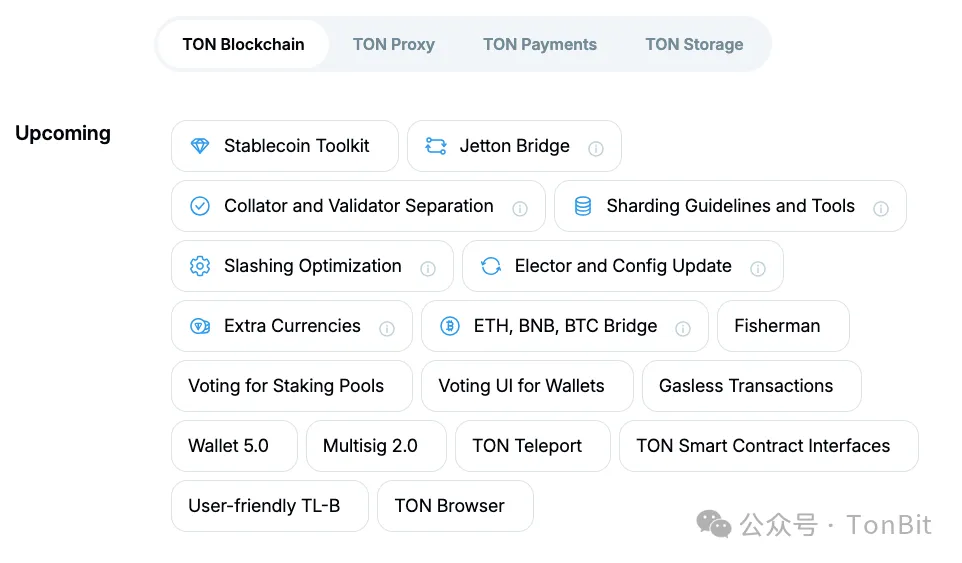
● Gas-Free Transactions: TON may subsidize gas fees in certain scenarios to attract more users.
● Separation of Validator and Block-Producing Nodes: A major upgrade to TON’s scalability, aiming to integrate up to 500 million Telegram users by 2028.
● Updates to Elector and Configuration Contracts: Allow users to vote on network proposals.
● TON Stablecoin Toolkit: Enable anyone to issue algorithmic stablecoins pegged to local fiat currencies.
● Jetton Bridge: Allow users to send TON tokens to other blockchains.
● ETH, BNB, and BTC Bridges: Official bridges will be launched to bring major cryptocurrencies onto TON.
● Non-Native Tokens: Allow TON users to create tokens that behave similarly to native ones.
3. Ecosystem Development Status
3.1 Ecosystem Overview
The official website of the TON Foundation showcases nearly 1,000 applications spanning a wide range of fields, including decentralized finance (DeFi), gaming, social media, and utility apps. Through these projects, the TON Foundation demonstrates its leadership in blockchain technology and drives innovation and ecosystem growth.
3.2 Key Metrics of the TON Ecosystem
As of July 27, 2024, there were 383 validator nodes on the TON chain, with over 590 million $TON tokens staked, distributed across 29 countries. The number of daily active addresses reached 373,000, representing a year-on-year increase of 5,360%. The DeFi ecosystem on the TON network shows robust growth, with 1,784,089 independent users, a total value locked (TVL) of $706,307,873, and 26,297 liquidity providers.
3.3 How TON Becomes a Powerful Decentralized Gaming Platform
3.3.1 Main Reasons for Building Decentralized Games on TON
Developing decentralized games on the TON blockchain offers numerous advantages for businesses and developers:
● Integration with Telegram: Provides access to over 900 million monthly active users.
● Strong User Acquisition and Retention Tools: Including the Telegram App Center and advertising tools.
● Fast and Efficient Blockchain: Capable of processing over 100,000 transactions per second at low fees.
● Diverse Monetization Opportunities: Such as in-app advertising and tradable non-fungible tokens (NFTs).
● Simple and Accessible: Offers a full suite of tools suitable for both GameFi Web3 developers and players.
4. Security Research on the TON Ecosystem
4.1 Secure Development Practices on TON
To ensure the security of smart contracts, we must implement a series of protective measures. Below are key security practices for the TON ecosystem:
1. Access Control
Description: When a contract contains critical logic or sensitive operations requiring execution by authorized users, proper access control must be implemented to prevent attackers from performing such actions and causing serious damage.
Best Practices:
➢ Identify which operations require permission controls.
➢ Restrict access to privileged operations by validating the message sender.
➢ Regularly review and update access control policies to adapt to changing contract requirements.
Refer to the following proposals:
https://github.com/ton-blockchain/TEPs/pull/180
https://github.com/ton-blockchain/TEPs/pull/181
2. Validate Message Inputs
Description: Lack of proper validation or filtering of external inputs in smart contracts may allow malicious users or attackers to inject harmful data, leading to unsafe behaviors or vulnerabilities.
Best Practices:
➢ Strictly validate and filter all external inputs, including verifying data types, checking boundary conditions, and sanitizing user input.
➢ Consider all possible input scenarios, including edge cases and unexpected inputs.
➢ Regularly audit and test input validation logic.
3. Monitor Gas Usage
Description: When handling internal messages, the sender typically pays the gas fee. When processing external messages, the contract itself pays for gas usage. Therefore, caution is required regarding gas consumption in external messages. Always test gas usage to verify correct operation and avoid vulnerabilities that could drain the contract’s balance.
Best Practices:
➢ Monitor and optimize gas usage during development.
➢ Implement gas limits to prevent high-consumption operations.
➢ Regularly test gas consumption under various scenarios.
4. Avoid Timestamp Dependency
Description: Some smart contract behaviors depend on block timestamps, which validators may manipulate. For example, validators can selectively include or exclude transactions or adjust timestamps for specific purposes. This behavior can compromise contract logic and introduce security risks.
Best Practices:
➢ Avoid relying directly on block timestamps for critical logic decisions.
➢ If timestamps are necessary, use more reliable and tamper-resistant methods.
➢ Implement time buffering mechanisms to allow variation within a reasonable range, reducing dependence on a single point in time.
➢ Regularly review contract logic to ensure it is not vulnerable to timestamp manipulation.
5. Integer Overflow
Description: Integer overflow and underflow occur when arithmetic operations exceed the representable range of a variable, resulting in incorrect calculations. These typically happen during addition, subtraction, or multiplication. If uncontrolled, they can lead to severe security issues such as incorrect balance calculations or unintended fund transfers.
Best Practices:
➢ Use safe math libraries for integer operations.
➢ Add overflow checks before and after all arithmetic operations.
➢ Regularly audit contract code to ensure all integer operations are protected.
6. Rounding Errors
Description: Rounding error risks arise from precision limitations or improper rounding methods in numerical computations, potentially leading to inaccurate results. Especially in financial or high-precision calculations, this can result in fund loss or unfair distribution.
Best Practices:
➢ Use high-precision or fixed-point arithmetic libraries for monetary calculations.
➢ Regularly test and verify numerical computation logic to ensure accuracy meets expectations.
➢ Clearly document rounding methods in code to maintain consistency.
7. Denial of Service (DoS)
Description: DoS risks involve exhausting a smart contract’s computational resources or triggering erroneous conditions, preventing the contract from functioning properly or entering infinite loops. This may block legitimate users from interacting with the contract or updating its state.
Best Practices:
➢ Limit loop iterations or recursion depth to avoid long-running operations.
➢ Check remaining gas before critical operations to prevent transaction failure due to insufficient gas.
➢ Regularly review and optimize contract logic for efficiency and reliability.
➢ Use event logs to record important operations, aiding in troubleshooting and recovery.
8. Business Logic
Description: Business logic vulnerabilities refer to design flaws or implementation errors in how a smart contract executes its intended processes, causing abnormal behavior under certain conditions. Malicious actors may exploit these vulnerabilities to cause fund loss, data tampering, or functional failures. These issues often stem not from coding errors but from misunderstandings or incomplete implementations of business requirements and workflows.
Best Practices:
➢ Deeply understand and analyze business requirements to ensure correct logical design.
➢ Conduct regular code audits and logic verification to identify and fix vulnerabilities promptly.
➢ Write comprehensive test cases covering all possible business scenarios.
By following these security practices, we can significantly enhance the security of smart contracts, reduce risks, and ensure stable contract operation and user fund safety.
4.2 Review of Security Incidents in the TON Ecosystem
In 2024, multiple security incidents occurred within the TON ecosystem, highlighting ongoing security challenges. Below are detailed descriptions of key events, analyses of root causes and impacts, solutions implemented, and summaries of typical security vulnerabilities.
1. Staking Contract of a Protocol Hacked, Resulting in Significant Token Loss
Date: May 22, 2024
Loss Amount: /
Root Cause: Incorrect parameter configuration
Description:
Following a staking campaign celebrating the prosperity of the TON ecosystem, a protocol’s staking contract was hacked due to incorrect parameter configuration, resulting in the theft of a large number of tokens. After the incident, the project immediately suspended the staking reward withdrawal function and allocated a substantial amount of $USDT to repurchase the lost 307,264 tokens.
After the attack, the project team quickly engaged TonBit for an audit. TonBit demonstrated professionalism by responding swiftly and mobilizing a team of security experts to conduct a comprehensive and meticulous security audit of the project’s core code. TonBit’s security experts identified six low-severity issues and promptly communicated them in detail to the project team. Leveraging extensive experience and technical expertise, TonBit not only provided specific remediation solutions but also assisted the team in rapidly resolving all issues, ensuring the contract’s security and stability.
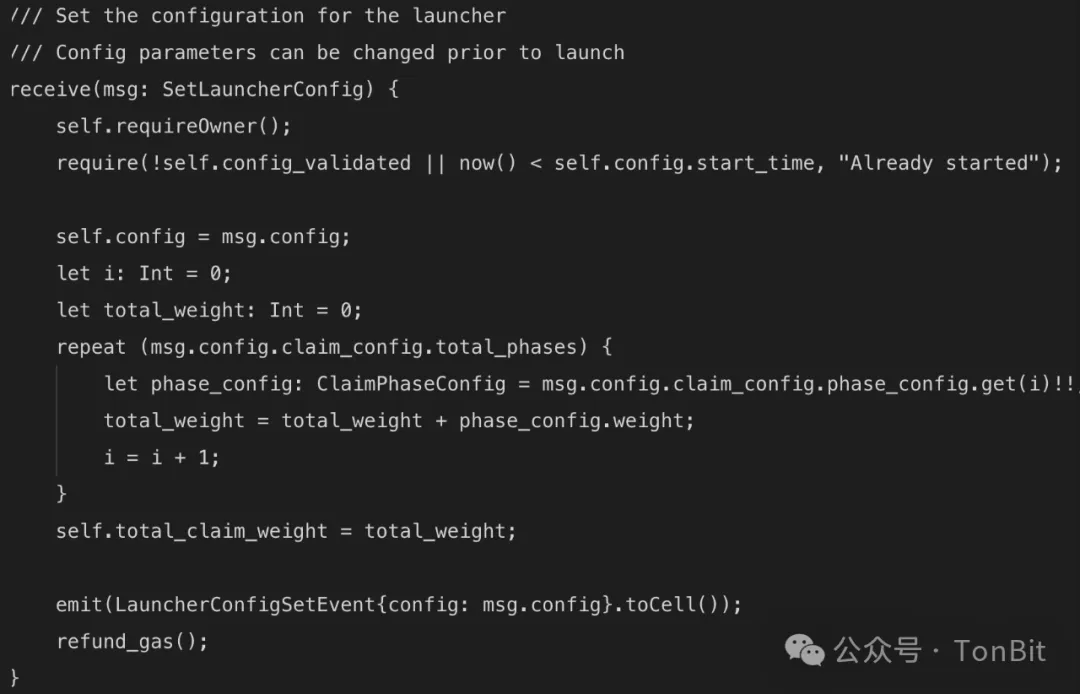
Issues related to configuration found by TonBit’s audit:
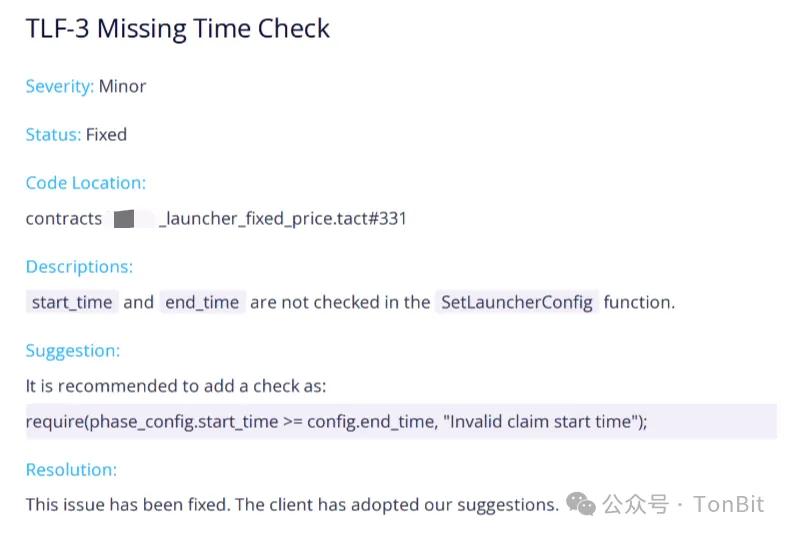
Solution: Correct parameter configuration
2. Hackers Exploited Wallet-Displayed Comment Field to Mislead Users
Date: May 10, 2024
Loss Amount: 22,000 TON
Root Cause: Wallet UI design for displaying comment field in transactions may mislead users
Description:
When processing transfer messages in TON, although comments can be added, some wallets’ UI designs for displaying these comments pose potential misleading risks. Hackers exploited this design flaw by manipulating the content of transfer message comments, presenting false information during transactions to deceive users into making mistaken transactions, resulting in financial losses.
Solution:
To address this issue, wallet applications should add prominent warnings when displaying such information, reminding users that the content is untrustworthy. Additionally, wallet development teams should improve UI design to ensure transparency and reliability in transaction information display. Users must also enhance their ability to discern suspicious transaction details.
Further Measures:
TonBit recommends that wallet development teams introduce multi-layered verification mechanisms when displaying transaction comment fields—such as source validation of comment content—to ensure reliability. Furthermore, regular user education and security alerts should be issued to help users recognize and defend against potential fraud. Combining technical improvements with user awareness can effectively reduce the occurrence of such security incidents.
3. BookPad Used a Backdoored Contract to Scam Funds and Flee
Date: April 15, 2024
Loss Amount: 74,424 TON
Root Cause: BookPad used a backdoored contract to withdraw user funds and absconded
Description:
BookPad released a pre-sale campaign using a closed-source smart contract containing a backdoor. After collecting sufficient funds, they exploited the backdoor to withdraw all funds and fled immediately.
Solution:
To prevent similar incidents, users should gather as much information as possible about project teams before participating in any investment activities, prioritizing open-source projects that have undergone rigorous security audits.
TonBit advises users to pay special attention to the following points:
1. Project Open-Source Status: Confirm that the smart contract code is open-source, allowing independent security experts to review it for hidden vulnerabilities or malicious code.
2. Security Audits: Choose projects audited by reputable security firms. Audits help identify and fix potential vulnerabilities, providing additional protection.
3. Background Checks on Project Teams: Investigate the background, reputation, and track record of the project team. Transparent and trustworthy teams are more reliable.
4. Community Feedback: Pay attention to community sentiment and discussions to understand the project’s reputation and potential risks.
Further Measures:
TonBit recommends introducing stricter regulatory and review mechanisms within the TON ecosystem, conducting qualification reviews for new projects to ensure compliance with security standards. Additionally, a public contract code repository could be established, where only approved contracts are allowed for use. This would significantly reduce the risk of user fund theft and enhance the overall security and trustworthiness of the TON ecosystem.
5. How Users Can Stay Safe on TON and Telegram
With the rapid development of the TON and Telegram ecosystems, there are now over 38 million active accounts, bringing increased attention—and greater risks.
Scammers and malicious actors target the influx of new users. Even within the most secure ecosystems, staying vigilant and informed about potential risks remains crucial. Be especially cautious of the following common scams.
5.1 Common Scams
1. The "Friend in Need" Scam: Imposters pretend to be friends or family members urgently requesting money. Always verify identities independently.
2. Phishing Websites: Fake websites mimic legitimate ones to steal login credentials. Double-check URLs and avoid clicking unknown links.
3. Investment Scams: Very common in crypto, promising high returns without proof. Research thoroughly; if it sounds too good to be true, it probably is.
4. Fake Surveys: Offer rewards for completing surveys to collect personal information. Avoid sharing sensitive details with unknown surveyors.
5. Fake Job Offers: Attractive job ads ask for personal information, app downloads, or upfront payments. Verify through official channels.
6. Classified Ad Scams: Fraudulent ads redirect you to fake Telegram bots to steal your information.
7. Pump-and-Dump Schemes: Groups manipulate cryptocurrency prices for profit, leaving others with losses. Always research and verify investment advice.
8. Romance Scams: Online relationships where scammers eventually request money or personal data. Stay alert if someone you met online asks for money.
5.2 Beware of Toncoin Pyramid Schemes
Telegram’s support for the TON blockchain has unfortunately attracted scammers seeking to exploit unsuspecting users. Below is a detailed breakdown of this scam:
1. Setup: Scammers send links to an “exclusive money-making program,” appearing to come from friends or contacts. They direct users to join an unofficial Telegram bot, falsely claiming it’s for storing cryptocurrency.
2. Investment: Users are instructed to buy Toncoin via legitimate channels (e.g., wallets, P2P markets, or exchanges), adding a layer of false credibility. Once purchased, users must transfer their Toncoin to the scam bot.
3. Accelerators: Victims are forced to purchase “accelerators” via a separate bot, costing between 5 and 500 Toncoin. At this stage, users lose their cryptocurrency permanently.
4. Recruitment: Scammers promote referral programs requiring users to create private Telegram groups and invite friends. They promise a fixed payment of 25 TON per referral plus commissions based on the accelerators purchased by referrals.
In reality, this is a classic pyramid scheme. Only the scammers profit, while others lose their invested capital.
5.3 How to Avoid Online Scams
To protect yourself from online scams and ensure Telegram account security, follow these essential steps:
1. Enable Two-Step Verification on Telegram: Go to “Settings > Privacy and Security > Two-Step Verification” to add an extra layer of account protection.
2. Verify Contacts: Be cautious of unsolicited messages, especially those requesting personal information or funds. Confirm the sender’s identity through alternative means.
3. Regularly Check Telegram Account Activity: Go to “Settings > Devices > Active Sessions” to check for unknown devices or sessions linked to your account.
4. Report Suspicious Activity: If you encounter fraudulent behavior, report it to Telegram.
5. Avoid Get-Rich-Quick Schemes: Remain skeptical of such schemes, even if recommended by friends or family—they may be victims themselves.
6. Never Send Cryptocurrency to Unknown Wallets: Always verify the recipient’s identity before transferring cryptocurrency to avoid being scammed.
Staying safe on TON and Telegram requires vigilance and awareness. By recognizing common scams and following these security tips, you can protect your assets and personal information. Always verify sources, remain skeptical of too-good-to-be-true offers, and conduct transactions only through official channels. Stay informed and cautious, and you can confidently enjoy the benefits of TON and Telegram without falling victim to fraud!
6. Conclusion
The rationale for choosing TON lies in recognizing the inherent strength of Telegram’s own ecosystem. Deploying your Web3 project on TON allows you to leverage Telegram’s massive user base of over 700 million monthly active users. This integration creates fertile ground for the flourishing of decentralized applications. TonBit is committed to providing comprehensive security support for the TON ecosystem, helping projects achieve higher security standards and greater user trust. As a guardian of security within the TON ecosystem, TonBit will continue its efforts to contribute to the advancement of blockchain technology.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News