TonBit under BitsLab discovers another vulnerability in TON Virtual Machine: RUNVM instruction may cause contamination of smart contract execution environment
TechFlow Selected TechFlow Selected

TonBit under BitsLab discovers another vulnerability in TON Virtual Machine: RUNVM instruction may cause contamination of smart contract execution environment
An attacker can exploit the moment when a sub-virtual machine exhausts gas to contaminate the parent virtual machine's libraries and trigger subsequent call failures, ultimately causing contracts relying on library integrity to exhibit abnormal behavior.
Author: BitsLab
TonBit, under BitsLab, has once again uncovered a "stealth bomb" deep within the TON Virtual Machine (TVM) codebase—the non-atomic state transition vulnerability in the RUNVM instruction. Attackers can exploit the moment when a child virtual machine exhausts its gas to pollute the parent virtual machine's libraries, causing subsequent calls to fail and ultimately leading to abnormal behavior in contracts relying on library integrity.
Below, we preserve the original technical details and present the complete process of vulnerability discovery and verification for developers, helping the community gain deeper understanding of this issue and enhance awareness against similar risks.

The following is a detailed description of the vulnerability:
The RUNVM instruction in TVM may pollute the caller's state and render libraries unusable. A new vulnerability has been discovered in the 'RUNVM' instruction code that allows pollution of the caller’s state. The relevant code snippet is as follows:
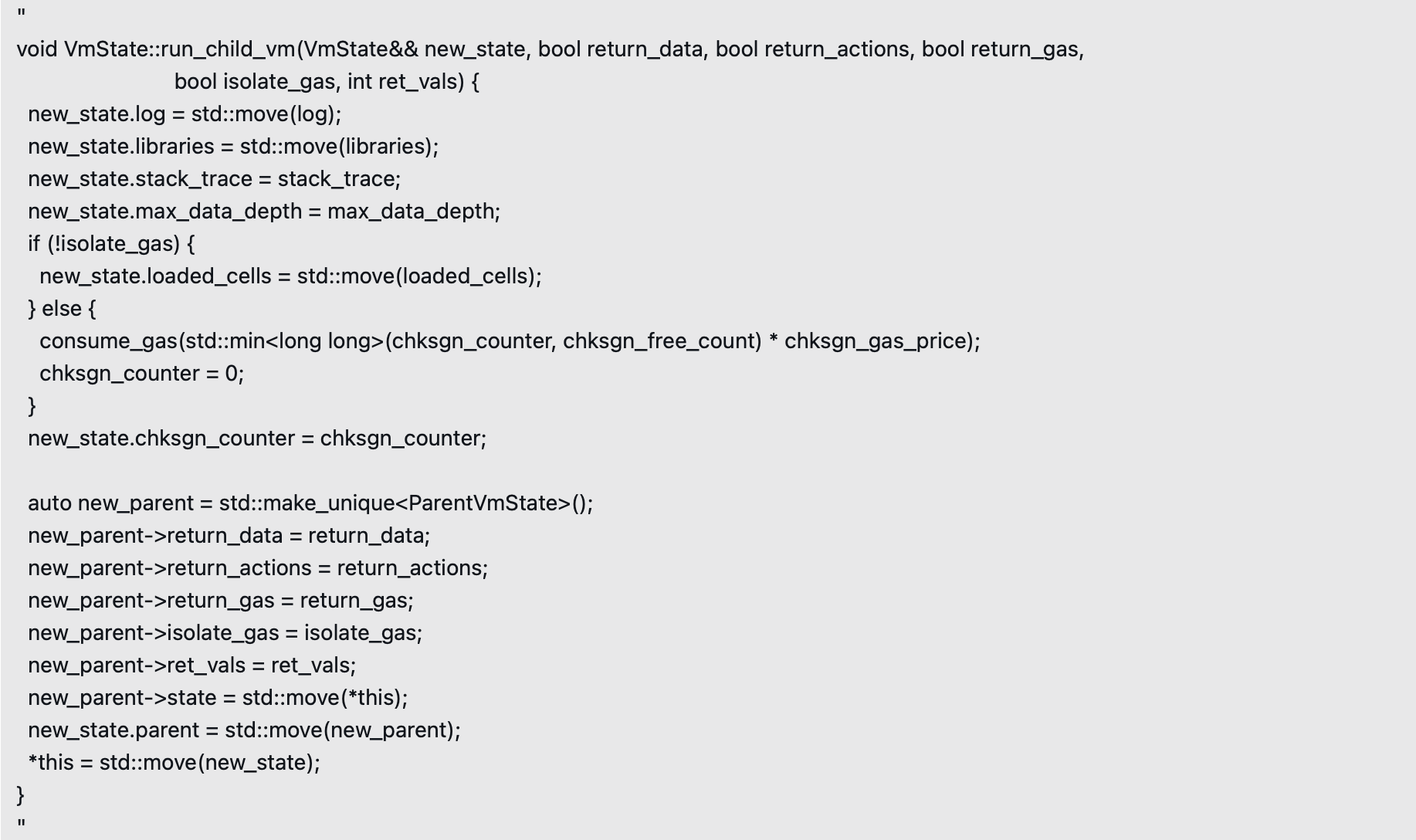
The above code is responsible for launching a child virtual machine. It moves the 'log' and 'libraries' from the current VmState into a new VmState object called 'new_state', then replaces the current VmState with 'new_state'.
The problem lies in the fact that this operation is not truly atomic. Before the statement '*this = std::move(new_state);' executes, the virtual machine may terminate due to gas exhaustion, failing to successfully replace the current state. At this point, 'libraries' may have already been moved out, leaving the child VM's libraries in a cleared (moved) state.
Since the RUNVM instruction implements gas isolation between child and parent virtual machines via the isolate_gas parameter, the following scenario arises:
Even if the child virtual machine triggers a gas exhaustion exception, the parent virtual machine retains sufficient gas to continue execution. However, during the failed state transition, the child VM has already moved/cleared the 'libraries', causing all subsequent operations dependent on 'libraries' to fail. This leads to unexpected behaviors in contracts assuming library integrity.
Vulnerability Verification (PoC)
We successfully reproduced this vulnerability using the following test case:



Key Test Modifications:
To facilitate local observation of library state, we modified the NOP instruction to forcibly register a library entry:

Reproduction Steps:
1) Add this test case to the crypto/test/vm.cpp file
2) Run the test-vm executable
3) Observe the exception thrown by the XLOAD instruction due to an empty library
Expected Behavior:
After NOP instruction execution: Library contains 1 entry
After RUNVMX instruction execution: Despite the parent VM continuing to run, the library becomes empty
XLOAD instruction fails and throws an exception
This fully demonstrates that the combined effect of non-atomic state transition and gas isolation mechanisms produces an inconsistent state that violates execution context integrity.
This discovery further highlights TonBit's deep expertise in TON ecosystem security research. We have promptly submitted the technical details and mitigation方案 to the TON Foundation and assisted them in completing the fix. We recommend all developers update their dependencies promptly upon release of the official patch; meanwhile, incorporate stricter library integrity checks and gas management logic in self-developed contracts to prevent malicious exploitation of similar issues. BitsLab will continue to uphold the principle of "responsible disclosure," working with the community to strengthen Web3 security defenses.
About BitsLab
BitsLab is a security organization dedicated to safeguarding and building emerging Web3 ecosystems, with a vision to become a respected Web3 security institution within the industry and among users. It operates three sub-brands: MoveBit, ScaleBit, and TonBit.
BitsLab specializes in infrastructure development and security audits for emerging ecosystems, covering but not limited to Sui, Aptos, TON, Linea, BNB Chain, Soneium, Starknet, Movement, Monad, Internet Computer, and Solana. Additionally, BitsLab demonstrates strong professional capabilities in auditing multiple programming languages including Circom, Halo2, Move, Cairo, Tact, FunC, Vyper, and Solidity.
The BitsLab team brings together several top-tier vulnerability researchers who have won international CTF awards and discovered critical vulnerabilities in well-known projects such as TON, Aptos, Sui, Nervos, OKX, and Cosmos.
About TonBit
TonBit, as a core sub-brand of BitsLab, is a security expert and early builder within the TON ecosystem. As a primary security provider for the TON blockchain, TonBit focuses on comprehensive security audits, including those for Tact and FunC languages, ensuring integrity and resilience for TON-based projects. To date, TonBit has successfully audited multiple notable projects including Catizen, Algebra, and UTonic, uncovering several critical vulnerabilities and demonstrating our outstanding capabilities in blockchain security. Furthermore, TonBit successfully hosted the TON CTF competition, attracting numerous participants and widespread attention, further solidifying its position as a security authority within the TON ecosystem. Going forward, TonBit will continue to protect blockchain security and drive sustained technological and ecological advancement.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News