Understanding Chain Abstraction: How NEAR Solves the Fragmentation Experience Challenge?
TechFlow Selected TechFlow Selected

Understanding Chain Abstraction: How NEAR Solves the Fragmentation Experience Challenge?
NEAR's chain abstraction approach aims to simplify interactions across different chains by creating a unified, seamless interface that abstracts away the complexity.
Author: Reflexivity Research
Translation: 1912212.eth, Foresight News
With the introduction of numerous L1s, L2s, and L3s, the blockchain landscape has become increasingly complex. Navigating diverse ecosystems has emerged as a major challenge for users. Conducting transactions, managing assets, and interacting across multiple chains can become complicated, often resulting in disjointed and inefficient experiences. This report explores these challenges and highlights NEAR’s solution.
NEAR's approach to chain abstraction aims to simplify user interactions across different blockchains by creating a unified, seamless interface that abstracts away the underlying complexities.
Web3 Multichain User Experience Challenges
Over the past seven years, the evolution of the crypto space and the scalability race have ushered in a new normal—now composed of hundreds of L1s, L2s, and even L3s. These advancements have made cheap blockspace accessible (albeit with varying security trade-offs), but they’ve also increased user experience complexity due to the need to operate across multiple chains, manage gas fees, and use cross-chain bridges or wrapped assets. In short, the current user experience when interacting with DApps across multiple chains is cumbersome, expensive, and unintuitive.
In today’s multichain world, users are forced to navigate multiple interfaces and perform repetitive transactions to manage assets across protocols. This fragmentation not only complicates the user experience but also creates economic inefficiencies and burdens users.
For example, a large portion of cryptocurrency wallet users operate via externally owned accounts (EOAs), each identified by a unique 42-character alphanumeric string prefixed with "0x." This string serves as the private key, crucial for accessing and managing the account. A primary challenge users face is managing these keys, as blockchain’s (generic) security model does not allow password recovery like traditional web platforms. If a user loses or forgets their private key, they lose access to their account and its assets—with no recourse. Now, imagine if users want to transact across two, four, or ten incompatible chains—they must manage private keys for all these addresses.
Every interaction on a blockchain—whether purchasing an asset or minting an NFT—requires a separate transaction. This process is time-consuming, incurs additional gas fees, and can be a significant barrier in a fast-paced digital environment. Although advancements in blockchain technology aim to streamline these processes, the practical effectiveness of such solutions remains limited.
Cross-Chain Bridges
Cross-chain bridges were initially introduced as a solution to fragmentation, enabling interoperability between different blockchains. These bridges use paired smart contracts on each blockchain to manage assets and ensure data integrity through encrypted messages. Essentially, they allow virtual movement of assets by mirroring state changes between accounts on different blockchains, without physically transferring tokens. This enables cross-chain asset transfers and enhances DApp functionality across multiple blockchains, expanding the design space for innovation and liquidity.
Despite these benefits, using cross-chain bridges comes with notable drawbacks. Bridge infrastructure itself introduces various risks, including smart contract vulnerabilities, technical failures, and potential malicious attacks. Many bridge designs require trust in centralized operators, exacerbating these risks and leading to issues like censorship, theft, and custody concerns.
Moreover, cross-chain bridges have historically suffered from major security breaches—such as the Poly Network, Ronin, and Nomad hacks—resulting in massive financial losses. These incidents highlight persistent vulnerabilities associated with bridge technology, ranging from coding errors to compromised oracles and colluding validators. These risks threaten the safety of user funds and degrade overall user experience by introducing delays and uncertainty in transactions, especially under insufficient liquidity conditions.
Ultimately, this fragmented ecosystem—connected by several costly and insecure bridges—is a major barrier to broader adoption, especially for users unfamiliar with technical complexities. Numerous solutions have been proposed, including universal interoperability layers like LayerZero, compatible L2 architectures like OP Super Chains, and shared/aggregated liquidity initiatives like Polygon’s AggLayer. While each offers some improvements, these solutions remain incompatible with one another, and fragmentation among them persists. However, one particular solution tackles the problem from a completely new angle—and nearly eliminates fragmentation and friction for end users: chain abstraction.
Chain Abstraction
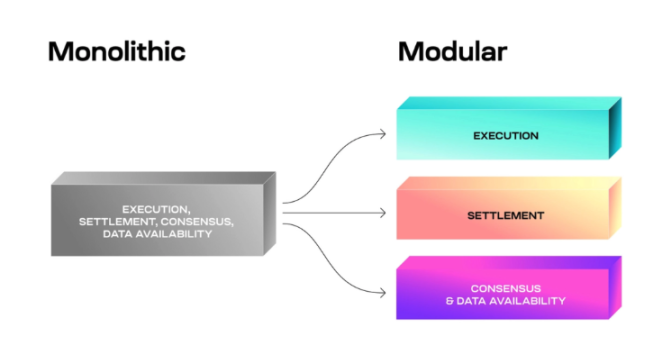
As the Web3 ecosystem continues to evolve, scalability remains a major challenge. Current modular scalability approaches involve separating different functional layers of blockchains—such as settlement, data availability, and execution.
While this approach has enabled the rise of various modular solutions—like L2s, OP Rollups, ZK Rollups, data availability layers, sidechains, and state channels—it has also led to fragmentation.
The days of “one chain to rule them all” are long gone.
Chain abstraction aims to consolidate the increasingly fragmented, modular nature of Web3. By abstracting away technical complexities, chain abstraction enables seamless interactions without requiring users to distinguish between different blockchains. This approach has the potential to significantly improve user experience by simplifying interactions across blockchains and reducing the complexity of managing multiple accounts and assets. Inspired by account abstraction, this design pattern minimizes the need for users to focus on the details of any specific underlying blockchain, instead allowing them to complete tasks in the most optimal way—even if it involves entirely different chains. In this context, understanding individual blockchains and their nuances becomes optional rather than mandatory, dramatically lowering the entry barrier for average users.
Account abstraction (AA) is a method in blockchain—particularly Ethereum—that integrates user accounts (EOAs) with smart contracts into a unified account type, enhancing flexibility and customizability in transaction validation. By enabling programmable validity conditions via smart contracts, this framework supports specific applications like automated payments and improves overall transaction efficiency on Ethereum and other chains. Similarly, chain abstraction aims to create a simpler and more powerful user experience for on-chain users.
Key features of chain abstraction:
-
Seamless chain interaction: Chain abstraction allows DApps to execute logic on any chain without requiring users to switch networks or manage multiple wallets.
-
Unified user interface: Users can interact with DApps using any supported token on any chain—all within a consistent interface, eliminating navigation hurdles for basic functions.
-
Gas and transaction management: By abstracting chain-specific details, users no longer need to acquire or spend gas on secondary chains, as these operations are managed within the abstraction layer.
Chain Abstraction and ZK Technology
At its core, chain abstraction addresses fragmentation by enhancing both user experience and network security. A notable innovation supporting this approach is the deployment of ZK technology and proofs.
Zero-knowledge proofs (ZKPs) are a cryptographic technique used to verify transactions. They work by allowing one party (the prover) to prove they possess certain information without revealing the actual details to another party (the verifier). This feature provides significant privacy advantages and reduces the computational and storage resources needed for transaction validation by hiding actual data.
ZKPs are built upon three key principles:
-
Completeness: If the prover has a valid proof, an honest verifier will accept it as correct, thereby confirming the transaction.
-
Soundness: This principle prevents provers from creating false proofs that appear valid, thus ensuring proof integrity.
-
Zero-knowledge: The verifier learns only that the proof is valid, gaining no additional information about the underlying data.
These properties make ZKPs a powerful tool for enhancing blockchain security and efficiency, ensuring only necessary information is verified while keeping all other details confidential.
ZKPs support secure, unified ledger systems in the realm of chain abstraction by enabling succinct proofs to validate transactions across multiple chains. This approach provides grid-level security, as all proofs are continuously aggregated, allowing assets to move securely between chains. This cross-settlement model protects transactions and ensures assets can be securely transferred across different blockchain networks.
NEAR’s Solution
NEAR’s solution includes secure aggregation, account aggregation, DA, intent brokers, decentralized frontends, and super wallet development. By simplifying user and application interactions across various chains, NEAR enables users to seamlessly interact with Ethereum, Avalanche, and others using a single NEAR account.

A key feature of NEAR’s infrastructure is its secure aggregation stack, which incorporates several innovative technologies:
-
NEAR DA: Data availability ensures all transaction data is recorded in blocks and accessible to all network nodes—critical for maintaining network trust and integrity. For instance, NEAR’s DA approach enables Ethereum rollups to process transactions more efficiently and securely by leveraging NEAR’s infrastructure.
-
zkWASM x Polygon Labs: The WebAssembly (WASM) standard acts as an intermediary language, accepting user inputs and reliably executing state transitions in crypto-native programming languages. This makes it easier for developers to write code in various languages and execute it within a virtual machine. zkWASM leverages zero-knowledge proofs to enhance the privacy and security of smart contracts, making them more efficient and scalable.
-
Identity management: Another cornerstone of chain abstraction is identity management, which allows users to maintain identities across multiple blockchain networks, streamlining asset management and transfer. This system, often referred to as account aggregation, simplifies user interaction with various blockchain ecosystems.
-
Decentralized frontend: NEAR has also launched decentralized frontends, highlighted by initiatives like the Blockchain Operating System (BOS), which delivers a unified user experience across various blockchain applications. These platforms provide a cohesive interface for accessing diverse blockchain apps, further simplifying user experience and encouraging broader adoption.
-
Account aggregation: Account aggregation allows users to have a single address across all possible chains and freely move assets between them. This approach simplifies the user experience by providing one account through which users can interact with applications on different chains, manage their on-chain identities across chains, and enable automatic bridging or swapping of assets.
-
Super wallet: NEAR wallets simplify user interactions on Web3 networks by eliminating the need to switch networks or manage different gas tokens. These wallets streamline the process of interacting with multiple blockchains, greatly improving user convenience and efficiency.
Chain Signatures
Chain signatures enable NEAR accounts—including smart contracts—to execute transactions across different blockchains and allow users to pay gas fees using a Multi-chain Gas Relayer (MGR). This alleviates the traditionally cumbersome process of acquiring and managing different native tokens to cover transaction fees across various chains.
Key benefits of MGR:
-
Simplified transactions: Users no longer need to purchase and manage multiple types of gas tokens, streamlining participation in cross-chain activities.
-
Enhanced accessibility: By lowering entry barriers, more users may be encouraged to explore and engage in cross-chain transactions.
-
Support for non-EVM chains: Beyond EVM-compatible chains, the relayer expands the range of accessible networks, increasing the utility and reach of NEAR tokens.
Chain signatures also introduce a form of multi-chain account abstraction, allowing a single NEAR account to manage numerous accounts across various chains. This feature offers functionality similar to ERC-4337 but extends it to include non-EVM and non-smart-contract chains, further enhancing the flexibility and capabilities of NEAR accounts. Users can manage their cross-chain assets through one NEAR account and even use USDC to pay transaction fees across chains, enabling smoother and more predictable financial transactions.
Initially, chain signatures will operate on Bitcoin, Ethereum, Cosmos, Dogecoin, and Ripple. However, NEAR aims to rapidly expand compatibility to support Solana, Polkadot, TON Network, and others.
Core Mechanism
Chain signatures leverage a decentralized multi-party computation (MPC) network, enabling NEAR accounts to interact with and control addresses on multiple chains. This technology allows NEAR accounts (including smart contracts) to request NEAR validators or MPC nodes to sign payloads—such as transactions for another blockchain. The signed payload can then be sent to the target chain, facilitating seamless transactions across different blockchain networks.
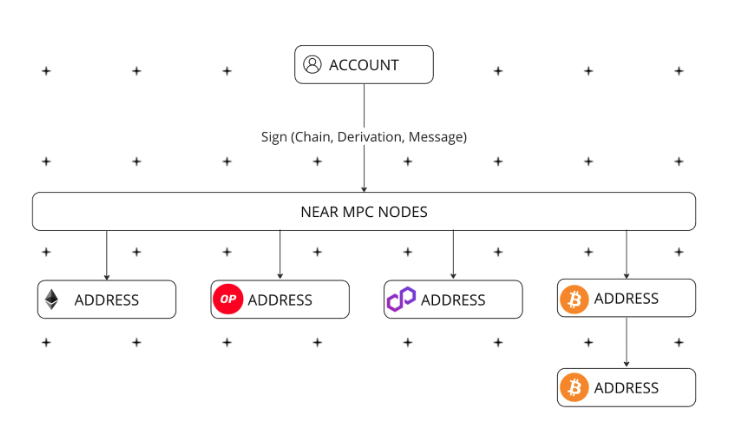
MPC
Multi-party computation (MPC) is a technique that preserves data privacy among multiple participants. It allows multiple parties, each holding private data, to jointly compute and verify results without revealing their private information to others. In practice, each participant holds a segment of an encrypted key, which together enables secure transactions or operations.
In an MPC setup, the private key is split into several parts and distributed among participants. When a transaction needs authorization, a specified number of participants or nodes must contribute their key segments to sign the transaction. This ensures no single participant can control the transaction independently. The final digital signature is then verified using a public key, which confirms the transaction’s authenticity without exposing individual key segments.
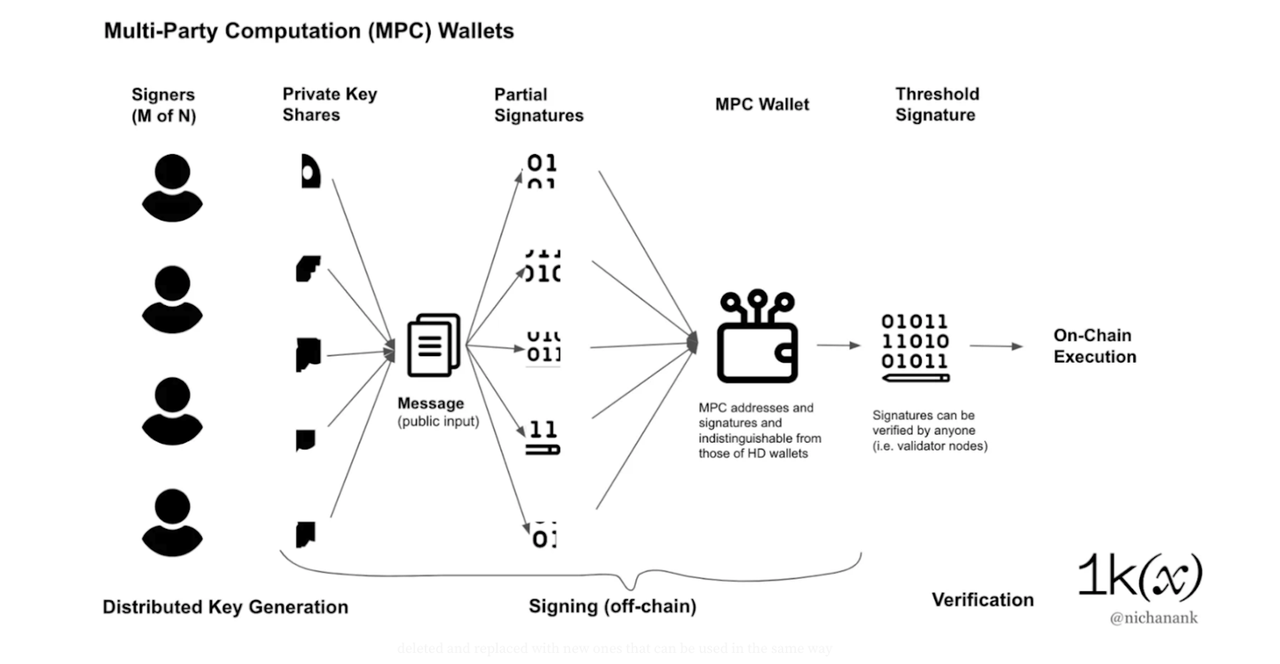
MPC is particularly useful for cross-chain transactions that require multiple approvals before execution. It offers strong security advantages, including no single point of failure, flexible signing workflows, and granular control over who can access and sign transactions. Compared to other methods, MPC also allows easier recovery from issues.
Unlike traditional MPC networks, which typically rely on deposit-based or bridge-based models, chain signatures operate on an account-based model. This approach eliminates the need to manage multiple blockchain addresses or navigate cumbersome bridging processes, reducing user complexity. The chain signature MPC network acts as a decentralized signer, handling requests on behalf of NEAR accounts and smart contracts and managing cross-chain addresses.
However, MPC also has drawbacks. The coordination required to manage signing policies and approve transactions occurs off-chain, which may introduce centralization-related risks. Additionally, MPC is incompatible with many traditional wallets and lacks standardization, meaning it cannot be easily implemented on widely used security devices like smartphones or hardware security modules. Currently, MPC solutions are often custom-built for specific needs and rely on proprietary technologies.
Finally, the chain signature MPC network will launch in collaboration with Eigenlayer, a key partner of the project. Eigenlayer aims to enhance Ethereum’s network security and extend its functionality using a novel mechanism called restaking. Essentially, Eigenlayer allows Ethereum validators to restake their ETH. In this process, validators commit their staked ETH—which is traditionally locked to maintain blockchain integrity—to support additional services and applications. By doing so, validators can strengthen the security provided to the Ethereum network and applications built on it, effectively utilizing their staked capital in a more dynamic and versatile manner.
Network security will initially be managed by Eigenlayer’s Ethereum restakers and NEAR stakers through a Proof of Authority (PoA) model. The network aims to transition to a permissionless model with a broader set of node operators, enhancing both security and decentralization.
Impact on DeFi and Blockchain Development
Chain signatures enable assets from one chain to be used within another, unlocking vast new possibilities for DeFi applications. For example, users could use BTC as collateral to borrow USDC or easily trade their XRP tokens for ETH. This flexibility is critical for DeFi’s growth, offering users enhanced liquidity options and more diversified financial products.
Revolutionary use cases unlocked by chain signatures:
-
Cross-chain DeFi applications: NEAR can now operate DeFi protocols using native assets from non-smart-contract chains, opening up entirely new pools of previously inaccessible liquidity.
-
Bridgeless transactions: By enabling direct custody and management of cross-chain assets, NEAR eliminates the need for bridges and traditional message-passing layers, simplifying operations and reducing potential security risks.
-
Instant multichain accessibility for applications: Developers can now launch applications instantly accessible across multiple blockchains, significantly expanding their potential user base and market reach.
However, unlocking chain abstraction does require new developer efforts and tools. To successfully integrate chain abstraction, developers must adopt toolkits that support this design pattern. Such toolkits should include:
Cross-chain logic handlers: Components capable of interpreting and executing DApp logic across different blockchain infrastructures.
-
Token management systems: Tools for handling various token types across chains, enabling seamless asset transfers and interactions within DApps.
-
User experience optimization: Features designed to make user interfaces intuitive and consistent across different blockchain operations.
Integration with the chain-abstraction world may remain limited until these tools become mainstream.
Conclusion
Although today’s multichain environment offers abundant opportunities for innovation and diversification in the blockchain space, it also presents significant challenges in usability and security for users. NEAR’s introduction of chain abstraction represents a crucial step toward simplifying this landscape, aiming to enhance user experience by streamlining interactions across different blockchains.
As the Web3 ecosystem continues to evolve, industry progress will depend not only on technological innovation but also on user-centric solutions that prioritize reducing complexity, promoting inclusivity, and ensuring security.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News