x402 Protocol: The Payment Revolution and Compliance Challenges in the Machine Economy Era
TechFlow Selected TechFlow Selected

x402 Protocol: The Payment Revolution and Compliance Challenges in the Machine Economy Era
The emergence of the x402 protocol is akin to 17th-century bills challenging the gold-silver standard—new economic forms always break through before rules do.
Author: Manqin
Introduction: From HTTP 402 to the Dawn of the Machine Economy
In 1996, designers of the HTTP protocol reserved the "402 Payment Required" status code, but due to the lack of supporting payment infrastructure, it became a "ghost code" of the internet era.
Thirty years later, the x402 protocol initiated and promoted by Coinbase has awakened this dormant status code into a "digital cash register" for AI-driven autonomous transactions. When weather AI robots automatically purchase global meteorological data or self-driving cars pay road tolls in real time, the traditional payment logic chain of "account opening - authentication - authorization" is disintegrating—x402 achieves, for the first time, atomic transactions between machines without human intervention through a closed loop of "HTTP request - 402 response - on-chain payment - service delivery."

Beneath this transformation lies the rise of the "machine economy." Just as the Age of Exploration gave birth to insurance and the Industrial Revolution spawned commercial banking, the explosive growth of AI agents (Agents) is now forcing upgrades in financial infrastructure.
The x402 protocol promises "instant settlement, near-zero fees, and cross-chain flexibility," breaking through traditional payment efficiency bottlenecks while pushing automated transactions into legal and regulatory gray areas.
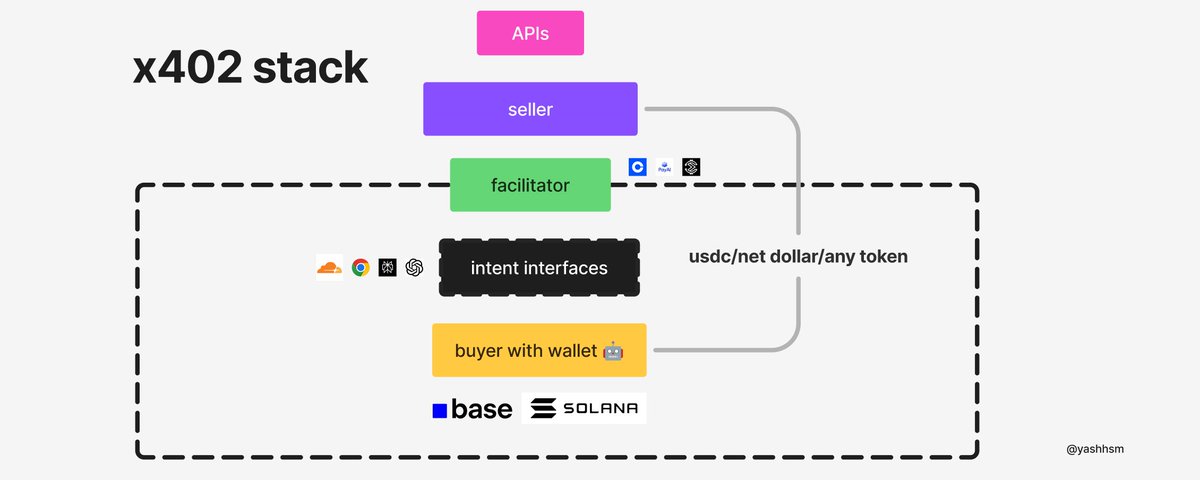
Analyzing x402: How Machines Autonomously Complete a "One-Scan Payment"
The operation of x402 resembles a "staffless convenience store" in the digital world:
1. AI initiates a request: For example, an AI needing to call a database API directly sends a resource request to the server;
2. 402 Payment Challenge: The server returns an HTTP 402 response with payment details akin to a "price tag"—USDC amount, recipient address, and on-chain validation rules;
3. On-chain Signed Payment: The AI generates a transaction signature via an integrated Web3 wallet, embedding the payment instruction directly into the HTTP header without requiring passwords or verification codes;
4. Blockchain Settlement: After verifying the signature, the server broadcasts the transaction; once blockchain confirmation is complete (typically within 3–5 seconds), access to the data is granted to the AI.
This "request-as-payment" model compresses the traditional e-commerce process of "shopping cart - checkout page - payment completion" into millisecond-level interactions between machines.
Its revolutionary aspect lies in granting AI economic agency—for the first time, AIs are no longer passive tools executing commands but have become "digital economic entities" capable of independently initiating transactions and fulfilling contracts.
Typical use cases include AI agents autonomously purchasing cloud computing power, data queries, paid content access rights, and third-party AI model calls. However, advancing such automated agentic commerce also brings associated legal risks.
Risk Landscape: When Code Logic Collides with Legal Provisions
1. The "Soul-Searching Question" of AI Decisions: Who Bears Responsibility for Machine Errors?
In the x402 workflow, AI agents initiate payment requests and execute signed transactions, involving algorithmic decision-making and automated execution. Under current legal frameworks, AI itself is not a legal entity and lacks independent subject status. Liability for its actions typically falls on the human developers or operators behind it. System "decentralization" does not exempt relevant parties from responsibility.
If an AI’s decision-making process or outcome infringes on third-party rights or violates laws, liability generally rests with the organization or individual that designed, deployed, or owns the AI system. Additionally, automated decisions involve large amounts of data—including user API call records, payment history, and potentially identifiable user information—subjecting them to privacy and algorithmic regulation.
2. Wallet Models as Compliance Dividers
x402's payment security depends on wallet choice, which may lead to vastly different regulatory consequences:
Non-custodial wallets: If AIs use self-hosted private keys via tools like MetaMask or hardware wallets, KYC requirements usually do not apply, but users bear full risk for lost keys and asset security;
Custodial wallets: If third-party custodial wallets or crypto asset services (e.g., exchanges, custodians) are used to sign or hold funds, the service provider may be classified as an account-based money transmitter, requiring licenses under local regulations and compliance with KYC/AML and FATF Travel Rule obligations—or face administrative or criminal penalties otherwise.
3. On-Chain Interactions and Payment Risks
Determination of Payment Instruments: Stablecoins currently demonstrated in x402 (e.g., USDC) sit at the center of global regulatory scrutiny, with differing classifications across jurisdictions. Accepting or transmitting assets including Bitcoin, Ether, and stablecoins like USDC or USDT within the U.S. may constitute "money transmission," triggering FinCEN oversight. Similarly, MiCA classifies stablecoins as "electronic money tokens," mandating licensing, reserve holding, and prudential supervision.
Settlement Finality and Irreversibility: Blockchain payments are irreversible upon confirmation. The x402 protocol was designed to streamline small, high-frequency automated payments and lacks built-in refund mechanisms, dispute resolution, or robust risk controls—posing challenges for user protection. Many jurisdictions lack consumer protection rules specific to crypto payments, leaving users to bear transaction consequences. For instance, if an AI agent erroneously transfers funds due to malfunction or attack, recovery is typically impossible.
4. Centralized Security Challenges
The x402 protocol itself integrates into provider servers via lightweight middleware and is not an independent on-chain smart contract. In practice, many x402 projects deploy a service on official platforms that forwards on-chain interactions to project servers, which then interact with the blockchain to distribute tokens.
This means that after users establish on-chain contracts with project parties, those parties must store administrator private keys on their servers to invoke smart contract methods—an exposure of admin privileges. If private keys are compromised, user assets are directly at risk.
In late October this year, @402bridge suffered a security incident caused by administrator private key leakage, resulting in over 200 users losing approximately $17,693 worth of USDC stablecoins.

The 402bridge security incident
Thus, when smart contracts are introduced to custody payments or execute transactions, single points of failure or erroneous execution remain significant risks.
Compliance Exploration: Innovation Meets Regulation
Enterprises deploying x402 must build a multi-dimensional compliance framework:
1. Cross-Border Compliance "Navigation System":
Dynamic Regulatory Mapping: Adjust compliance strategies based on counterparty jurisdiction—once target markets are identified, promptly complete regulatory positioning and licensing arrangements. Establish ongoing monitoring of domestic and international legislative and enforcement trends regarding automated payments and digital assets.
Strict AML/KYC Due Diligence: In line with FATF Travel Rule and national guidelines, implement comprehensive customer identification (KYC) and transaction monitoring systems. Verify identities and purposes of both payer and payee, retain detailed records of fund sources and uses, and apply on-chain risk controls (e.g., using on-chain analytics to detect terrorist-linked or sanctioned addresses) to prevent money laundering.
2. Legal Liability Segregation Techniques:
AI Compliance and Privacy Protection: Assess AI models and decision processes to ensure algorithmic transparency and non-discrimination. Provide explainability mechanisms for personal decisions and allow for user appeals or human intervention.
Legal Classification and Protocol Architecture: Clarify legal relationships within the protocol—such as the definition of AI agents, legal nature of tokens/stablecoins, and functional roles of related contracts. Enter into clear service agreements with users and service providers defining rights, obligations, dispute resolution mechanisms, and applicable law.
Risk Mitigation Measures: Given the irreversibility of digital payments and smart contract risks, consider mitigation strategies. For example, set daily or per-transaction limits on AI agent accounts to avoid large payments; conduct independent security audits of smart contracts and implement emergency "pause switches," especially in custody scenarios where operators should separate operational funds from customer funds.
End users utilizing x402-like automated payment services should take protective measures to reduce legal and operational risks:
Enhance Security: Before use, verify whether platforms hold necessary financial licenses or compliance registrations; avoid clicking unknown links that trigger x402 payments or transacting with unlicensed entities. Prefer mainstream, compliant stablecoins as payment instruments. If using non-custodial wallets, securely store private keys via hardware wallets and never keep them in plaintext on network-connected servers.
Manage Authorization Scope: Set strict transaction limits and authorization policies for AI payment agents, carefully approve "unlimited approvals," and regularly review and update authorization settings.
Persist Transaction Evidence: Fully preserve on-chain transaction hashes, service agreements, and payment receipts to ensure sufficient evidentiary support in disputes.
Monitor Regulatory Developments: Stay informed about the latest regulations in your jurisdiction concerning crypto payments and AI decision-making to ensure continued compliance.
Conclusion: The Dance Between Code and Law
The emergence of the x402 protocol mirrors 17th-century bills of exchange challenging gold-and-silver standards—new economic forms always emerge before rules catch up. Yet, incidents like the @402bridge breach serve as timely reminders that both technological infrastructure resilience and institutional maturity are equally critical.
As the EU's MiCA mandates monthly audits of stablecoin reserves and the U.S. SEC includes AI decisions under the Algorithmic Accountability Act, these regulations—though seemingly restrictive—are in fact building "guardrails" for the machine economy.
Hence, future competition will be a contest of compliance capability. True innovation never lies in overturning rules, but in writing new grammars for the future economy within the blanks left by existing ones.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News