5 Years, 6 Incidents, Losses Exceeding $100 Million: The Hacking History of Veteran DeFi Protocol Balancer
TechFlow Selected TechFlow Selected

5 Years, 6 Incidents, Losses Exceeding $100 Million: The Hacking History of Veteran DeFi Protocol Balancer
对于旁观者,DeFi 是一场新奇的社会实验;对于参与者,DeFi 被盗是一次昂贵的教训。
Author: David, TechFlow
When it rains, it pours; hackers strike hardest during downturns.
In the recent bearish climate across the entire crypto market, a veteran DeFi protocol has been hit hard once again.
On November 3, on-chain data indicated that Balancer was suspected of being hacked. Approximately $70.9 million worth of assets were transferred to a new wallet, including 6,850 osETH, 6,590 WETH, and 4,260 wstETH.
Subsequently, according to Lookonchain monitoring of related wallet addresses, the total loss from the attack has risen to $116.6 million.

After the incident, the Balancer team stated:
"A vulnerability potentially affecting Balancer v2 pools has been identified. Our engineering and security teams are prioritizing investigation into this event and will share verified updates and next steps as more information becomes available."
In addition, the official team publicly offered a white-hat reward of 20% of the stolen assets to recover them, valid within 48 hours.
The response was timely, yet very formal.
However, if you're a seasoned DeFi user, you wouldn't find the headline "Balancer hacked" surprising—rather, it feels eerily familiar.
As a veteran DeFi protocol founded in 2020, Balancer has suffered security incidents six times over five years—almost an annual tradition—with this latest one being the most expensive.
Looking back, when market conditions turn extremely difficult for trading, even earning yield through DeFi may not be safe.
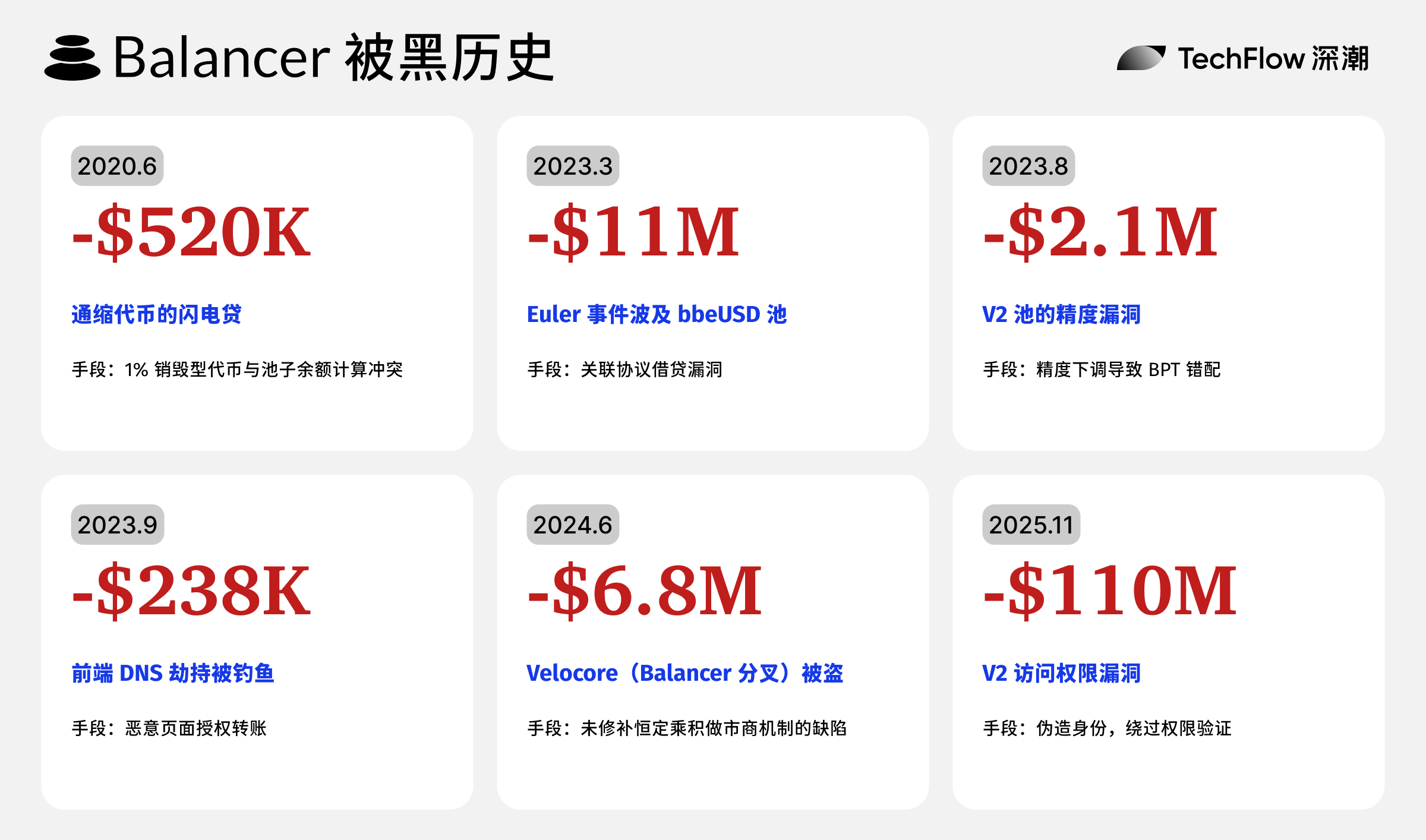
June 2020: Deflationary Token Vulnerability, ~$520,000 Lost
In March 2020, Balancer entered the DeFi space with its innovative concept of a "flexible automated market maker." Just three months later, the ambitious protocol faced its first nightmare.
Attackers exploited a flaw in how the protocol handled deflationary tokens, resulting in losses of approximately $520,000.
The basic mechanism involved STA, a token that automatically burned 1% of each transfer as a fee.
The attacker borrowed 104,000 ETH via flash loans from dYdX and conducted 24 round-trip trades between STA and ETH. Since Balancer failed to correctly calculate actual balances after each transaction, the STA balance in the pool was drained down to just 1 wei. The attacker then exploited the severe price imbalance to exchange negligible amounts of STA for large quantities of ETH, WBTC, LINK, and SNX.
March 2023: Caught in Euler Hack, ~$11.9 Million Lost
This time, Balancer was an indirect victim.
Euler Finance suffered a $197 million flash loan attack, and Balancer’s bb-e-USD pool was affected due to holding Euler’s eTokens.
When Euler was attacked, about $11.9 million was transferred from Balancer’s bb-e-USD pool to Euler, representing 65% of the pool’s TVL. Although Balancer urgently paused the affected pool, the damage had already been done and could not be reversed.
August 2023: Balancer V2 Pool Precision Bug, ~$2.1 Million Lost
This attack had warning signs. On August 22, Balancer proactively disclosed a vulnerability and warned users to withdraw funds, but the attack still occurred five days later.
The vulnerability involved rounding errors in the V2 Boosted Pool. By precise manipulation, attackers caused discrepancies in the calculation of BPT (Balancer Pool Token) supply, enabling them to extract pool assets at unfair exchange rates. The attack was executed using multiple flash loan transactions, with different security firms estimating losses ranging from $979,000 to $2.1 million.
September 2023: DNS Hijacking Attack, ~$240,000 Lost
This was a social engineering attack targeting traditional internet infrastructure rather than smart contracts.
Hackers breached domain registrar EuroDNS through social engineering, hijacking the balancer.fi domain. Users were redirected to a phishing site that used the malicious Angel Drainer contract to trick them into authorizing fund transfers.
The stolen funds were then laundered through Tornado Cash.
Although this wasn't directly Balancer's fault, its high profile made it a target for phishing attacks—difficult to guard against despite best efforts.
June 2024: Velocore Hack, ~$6.8 Million Lost
Velocore is an independent project, so its hack wasn't directly related to Balancer. However, as a Balancer fork, it used the same CPMM (Constant Product Market Maker) pool design—making it technically similar, like a theft elsewhere but rooted in Balancer's mechanics.
The attack exploited an overflow vulnerability in Velocore’s Balancer-style CPMM pool contract by manipulating the feeMultiplier parameter to exceed 100%, causing miscalculations.
The attacker ultimately stole approximately $6.8 million using flash loans combined with carefully crafted withdrawal operations.
November 2025: Latest Attack, Over $100 Million Lost
The technical cause of this latest attack has now been preliminarily identified. According to security researchers, the vulnerability lies in the access control check within the manageUserBalance function of the Balancer V2 protocol, which governs user permission checks.
As analyzed by security monitoring agencies Defimon Alerts and Decurity, the system should verify whether the caller is the true owner of the account when validating withdrawal permissions in Balancer V2. However, the code incorrectly checks whether msg.sender (the actual caller) equals the op.sender parameter provided by the user.
Since op.sender is a user-controllable input parameter, attackers can forge identities at will, bypassing permission checks and executing WITHDRAW_INTERNAL operations.
In plain terms, this vulnerability allows anyone to impersonate any account owner and directly withdraw internal balances. Such a fundamental access control error resembles a basic coding mistake—and its presence in a mature, five-year-old protocol is shocking.
Reflections on the Hack History
What can we learn from this “history of hacks”?
The takeaway is that DeFi protocols in the crypto world are more like “something to admire from afar, not to touch lightly.” From a distance, everything seems calm—but upon closer inspection, there are likely significant technical debts behind the narratives that need to be addressed.
Take Balancer, for example. One of its innovations is allowing custom-weighted pools with up to eight tokens.
Compared to Uniswap’s simplicity, Balancer’s complexity grows exponentially.
Each additional token drastically expands the state space of the pool. When trying to balance prices, weights, and liquidity of eight different tokens within a single pool, the attack surface widens accordingly. The 2020 deflationary token attack and the 2023 rounding error vulnerability were both fundamentally due to mishandling edge cases caused by complexity.
Even more concerning is Balancer’s choice of rapid iteration. From V1 to V2,再到 various Boosted Pools, each upgrade layered new features atop old code. This accumulation of "technical debt" turned the codebase into a fragile tower of blocks.
For instance, the recent attack due to a permission flaw—a basic design error—should not occur in a five-year-old protocol. It may indicate that code maintenance has, to some extent, spiraled out of control.
Or perhaps, in today’s environment where narrative, profit, and sentiment outweigh technology, whether underlying code has vulnerabilities no longer matters.
Balancer won’t be the last. You never know when black swans built upon DeFi’s composability might strike. The complex web of dependencies in the DeFi world makes risk assessment nearly impossible.
Even if you trust Balancer’s code, can you trust all its integrations and partners?
To observers, DeFi is a fascinating social experiment; to participants, a DeFi hack is an expensive lesson; to the industry as a whole, DeFi’s growing pains are tuition fees on the path to maturity.
Let’s just hope this tuition isn’t too costly.

Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News