When KYT tools become "zombie systems": The compliance you think you have is actually a trap
TechFlow Selected TechFlow Selected

When KYT tools become "zombie systems": The compliance you think you have is actually a trap
Pull back the curtain and see the truth behind the scenes.
Author: AiYing Compliance
Everyone in the industry knows there are two types of compliance: one designed for regulators, and one that actually works. The former is known as "compliance theater," while the latter represents genuine, effective risk management. Sadly, most organizations—especially fast-growing fintech companies riding the wave of innovation—are unconsciously performing the first type.
What exactly is "compliance theater"? It's a carefully staged performance meant to pass audits, secure licenses, and reassure investors. On this stage, procedural correctness trumps all else; polished reports matter far more than actual risk detection rates. Actors (compliance officers) recite pre-written scripts (compliance manuals) using elaborate props (expensive systems) to present an illusion of harmony and safety to the audience (regulators). As long as the show goes well, licenses are granted, funding flows in, and everyone celebrates.
And among all the props on this stage, the most dazzling, expensive, and deceptive are the so-called "zombie systems"—tools that appear to operate 24/7 but have long since lost their soul and function, becoming hollow shells. Nowhere is this more evident than with KYT (Know Your Transaction) systems. Designed to be the frontline scouts in anti-money laundering (AML), they often become the first casualties, turning into mindless zombies that consume budgets and provide false reassurance. They sit quietly on servers, green lights blinking, reports churning out—everything appears normal—until a real bomb detonates right before their eyes.
This is the greatest compliance trap. You believe you’ve invested in top-tier equipment and built an impenetrable defense, but in reality, you're just feeding resources to a zombie. It won't protect you. When disaster strikes, it will ensure your downfall comes without warning.
So here’s the question: Why do our heavily funded, labor-intensive KYT tools sometimes turn into lifeless husks? Is it due to fatal flaws in technology selection, a complete breakdown in process management, or inevitably, both?
Today, we turn our spotlight to the most dramatic stage of this "compliance theater": the fintech and payments industry—particularly Southeast Asia, where regulatory environments are complex and volatile, and business growth runs wild like an untamed horse. Real-life dramas unfold here daily. Our job is to pull back the curtain and expose what's happening behind the scenes.
Act One: Dissecting the Zombie System—How Did Your KYT Tool Die?
A zombie system doesn’t die overnight. Its death isn’t caused by a catastrophic bug or sudden outage. Instead, like boiling a frog slowly, it gradually loses its ability to sense, analyze, and respond amid the illusion of “normal operation,” until only a shell remains—alive in form, dead in function. This decay can be dissected from both technical and procedural angles, revealing how even a fully functional KYT system can slowly descend into oblivion.
Technical Brain Death: Single Points of Failure and Data Silos
The technology is the brain of any KYT system. When neural connections break, data input fails, and analytical models stagnate, the system enters a state of “brain death.” It still processes data, but it no longer understands or judges.
Cognitive Blind Spots from Single-Tool Dependence: Seeing the World Through One Eye
Over-reliance on a single KYT tool is the primary—and most common—reason for system failure. While this is nearly common knowledge in the industry, within the script of “compliance theater,” it’s often conveniently ignored in favor of perceived “authority” and “simplified management.”
Why is relying on a single tool fatal? Because no single tool covers all risks. It’s like assigning one sentry to guard against enemies from all directions—he will always have blind spots. A recent study by MetaComp, a licensed digital asset service provider in Singapore, revealed this harsh truth through empirical testing. By analyzing over 7,000 real transactions, the research found that relying on just one or two KYT tools could result in up to 25% of high-risk transactions being incorrectly cleared. That means one in four risks is completely ignored—not a blind spot, but a black hole.
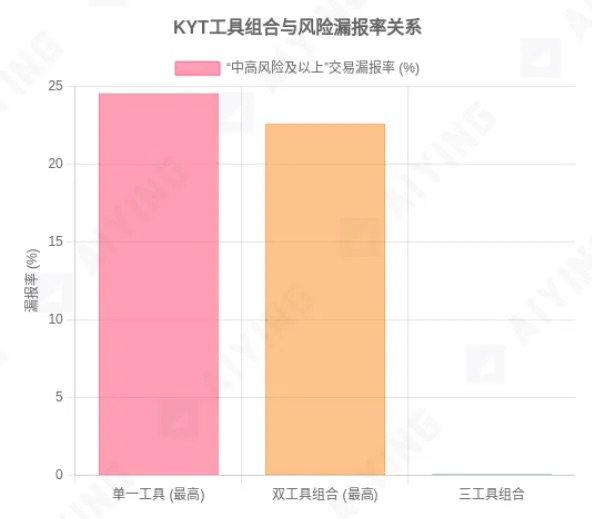
Figure 1: Comparison of False Clean Rate across different KYT tool combinations
Data source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart shows that when the risk threshold is set at "medium-high risk," the false clean rate reaches up to 24.55% with a single tool, up to 22.60% with dual tools, and drops sharply to 0.10% with three tools combined.
This massive exposure stems from inherent weaknesses in the KYT ecosystem. Each tool operates on proprietary datasets and intelligence-gathering strategies, leading to natural differences and blind spots in several areas:
-
Differences in data sources: Some tools may have closer ties to U.S. law enforcement and thus better coverage of North American risk addresses; others may focus on Asian markets and detect local fraud networks more promptly. No single tool can dominate intelligence gathering globally.
-
Different focuses on risk types: Some tools excel at tracking OFAC-sanctioned addresses, while others lead in detecting mixers or darknet market activity. If your chosen tool isn’t strong in identifying the specific risks your business faces, it becomes little more than decoration.
-
Update delays and intelligence lag: Criminal addresses often have short lifespans. One tool might flag a risky address today, while another takes days or even weeks to catch up. This time gap gives money launderers ample opportunity to complete multiple operations.
Therefore, when an organization pins all its hopes on a single KYT tool, it’s essentially gambling—that every risk it encounters happens to fall within that tool’s “field of vision.”
Data Silos and Systemic Malnutrition: Water Without a Source Cannot Flow
If single-tool dependence equates to narrow vision, then data silos represent full-blown malnutrition. A KYT system was never meant to stand alone. Its effectiveness depends on a holistic understanding of counterparties and transaction behaviors. It needs continuous “data nourishment” from KYC (Know Your Customer) systems, customer risk rating platforms, business systems, and other sources. When these data pipelines are blocked or the data itself is poor quality, the KYT system becomes water without a source—deprived of the baseline needed for judgment.
In many fast-growing payment companies, this scenario is all too common:
The KYC team handles customer onboarding, storing data in System A; the risk team monitors transactions via System B; the compliance team files AML reports using System C. These three systems belong to different departments, provided by different vendors, with almost no real-time data exchange between them. The result? When the KYT system analyzes a live transaction, the customer risk rating it relies on may still be static data entered three months ago. During that time, the customer may have exhibited numerous high-risk behaviors—but those signals are trapped inside System B, invisible to the KYT system.
The direct consequence of this malnutrition is that the KYT system cannot establish accurate behavioral baselines. A core capability of any effective KYT system is anomaly detection—identifying transactions that deviate from a customer’s normal behavior pattern. But if the system doesn’t know what “normal” looks like, how can it recognize “abnormal”? Eventually, it regresses to relying on primitive, blunt static rules, generating vast quantities of worthless “junk alerts”—taking another step toward zombification.
Static Rules and “Carving the Boat to Find the Sword”: Using Old Maps to Navigate New Lands
Criminals constantly evolve—from traditional smurfing to cross-chain money laundering via DeFi protocols, to fake NFT marketplace trades—their methods growing exponentially more complex and stealthy. Yet, many “zombie KYT systems” still run outdated rule sets, akin to using an old map to explore new continents—destined to fail.
Static rules like “flag any transaction over $10,000” are laughably easy to bypass for today’s cybercriminals. Automated scripts effortlessly split large sums into thousands of sub-threshold micro-transactions, evading detection entirely. Real threats hide in sophisticated behavioral patterns:
-
A newly registered account conducting frequent small-value transactions with many unrelated parties in a short timeframe.
-
Funds rapidly flowing in, then immediately dispersed across multiple addresses without pause—forming a classic “peel chain.”
-
Transaction paths involving high-risk mixers, unregistered exchanges, or sanctioned-region addresses.
These complex patterns cannot be effectively described or captured by static rules. They require machine learning models capable of understanding transaction networks, tracing fund flows, and learning risk signatures from massive datasets. A healthy KYT system must have dynamic, self-evolving rules and models. A zombie system, however, has lost this ability—its rulebook, once set, rarely updated, leaving it hopelessly behind in the arms race against crime—a fully “brain-dead” entity.
Procedural Cardiac Arrest: From “Set-and-Forget” to “Alert Fatigue”
If technical flaws cause “brain death,” broken processes induce full cardiac arrest. Even the most advanced system is useless without proper operational workflows and response mechanisms. In “compliance theater,” procedural failures are often more insidious and damaging than technical ones.
The Illusion of “Launch Equals Victory”: Treating Marriage as the End of Love
Many companies, especially startups, adopt a project-based mindset toward compliance. They view KYT procurement and deployment as a finite project with clear start and end dates. Once the system goes live and passes regulatory review, the project is declared a success. This is the quintessential delusion of “compliance theater”—treating marriage as the end of romance, believing peace is guaranteed forever after.
But launching a KYT system marks only day one. It is not a “set-and-forget” tool, but a living entity requiring ongoing care and optimization. This includes:
-
Ongoing parameter calibration: Markets change, customer behaviors shift, laundering tactics evolve. Monitoring thresholds and risk parameters must adapt accordingly. A $10,000 alert threshold that made sense a year ago may be meaningless after a tenfold increase in transaction volume.
-
Regular rule optimization: As new threats emerge, new monitoring rules must be developed and deployed. At the same time, old rules must be reviewed and ineffective ones—those producing only false positives—should be retired.
-
Model retraining: For systems using machine learning, models must be regularly retrained on fresh data to maintain detection capabilities and prevent model decay.
When an organization falls for the “launch equals victory” myth, these critical maintenance tasks get neglected. No one takes ownership, no budget is allocated. The KYT system becomes like a sports car abandoned in a garage—no matter how powerful the engine, it rusts away into junk.
Alert Fatigue Crushes Compliance Officers: The Final Straw
The most immediate and disastrous consequence of a poorly configured, unmaintained zombie system is an avalanche of false positive alerts. Industry observations suggest that in many financial institutions, 95% or even 99% of KYT-generated alerts turn out to be false positives. This isn’t just inefficient—it triggers a deeper crisis: “alert fatigue.”
Imagine a typical compliance officer’s day:
Every morning, he opens his case management system to find hundreds of pending alerts. He investigates the first, spends half an hour, marks it as a false positive, closes it. The second? Same thing. The third? Again. Day after day, he drowns in an endless sea of false alarms. Initial vigilance gives way to numbness and complacency. He starts looking for shortcuts to close alerts faster, his trust in the system plummets. Eventually, when a real high-risk alert appears buried among the noise, he might glance at it briefly, reflexively mark it “false,” and close it.
Alert fatigue is the final straw that breaks the compliance line. It psychologically destroys the team’s fighting spirit, turning risk hunters into alert janitors. The entire department’s energy is wasted battling a zombie system, while real criminals walk freely through the防线 under cover of noise.
At this point, the KYT system suffers full procedural cardiac arrest. It still generates alerts, but these “heartbeats” have lost meaning—ignored, disbelieved. It has become a true zombie.
I once knew a company that staged a classic “compliance theater” to win a license and impress investors: executives proudly announced they’d purchased a top-tier KYT tool, using it as marketing proof of “commitment to highest compliance standards.” But to save costs, they subscribed to only one vendor. Their logic: “We used the best—if something goes wrong, it’s not our fault.” Conveniently forgotten: every single tool has blind spots.
Meanwhile, the compliance team was understaffed and lacked technical expertise, so they relied solely on basic static rule templates provided by the vendor. Monitoring large transactions and filtering a few public blacklist addresses counted as “mission accomplished.”
Worst of all, when transaction volume surged, alerts flooded in like snowflakes. Junior analysts quickly realized over 95% were false positives. To meet KPIs, their job shifted from “investigating risk” to “closing alerts.” Over time, no one took alerts seriously anymore.
Professional money laundering gangs soon smelled blood. Using simple yet effective tactics, they turned this zombie system into an ATM: employing the “smurfing” strategy to split funds from illegal online gambling into thousands of sub-threshold micro-transactions disguised as e-commerce refunds. The alarm wasn’t raised by their own team, but by their partner bank. When the regulator’s inquiry landed on the CEO’s desk, he was utterly baffled. Reportedly, the company later had its license revoked.
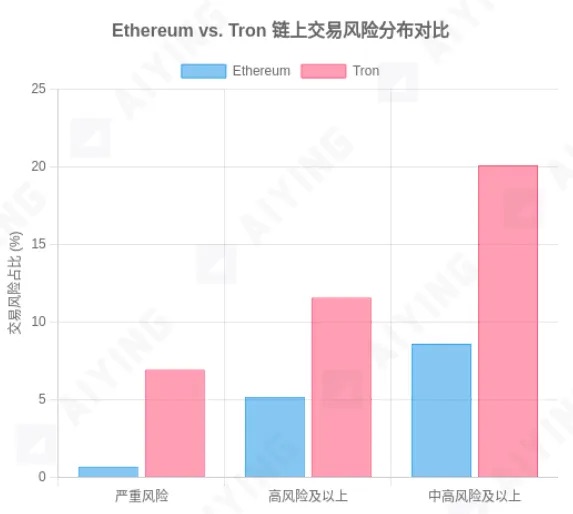
Figure 2: Risk level comparison across different blockchain networks
Data source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart shows that in sampled data, Tron network transactions rated as “severe,” “high,” or “medium-high” risk are significantly higher in proportion compared to Ethereum.
This real-life story is a mirror reflecting countless fintech companies currently performing “compliance theater.” They haven’t collapsed yet—not because they’re safe, but because they’ve been lucky enough not to attract professional criminals. But that’s only a matter of time.
Act Two: From Zombie to Sentinel—How to Revive Your Compliance System
Having dissected the pathology of zombie systems and witnessed the tragedies of “compliance theater,” we must move beyond criticism. As practitioners on the front lines, we ask: How do we break free? How do we resurrect a dying zombie into a battle-ready “frontline sentinel”?
The answer does not lie in buying more expensive or “authoritative” single tools, but in a fundamental transformation of mindset and tactics. This methodology is already an open secret among seasoned professionals in the field. MetaComp’s research now quantifies and publicly reveals it for the first time, offering us a clear, actionable playbook.
Core Solution: End the Solo Act, Embrace a Multi-Layered Defense
First, we must abandon the “buy-a-tool-and-done” theater mentality at its root. True compliance is not a solo performance, but a positional warfare requiring a layered defense. You can’t expect one sentry to stop an army—you need a multidimensional network of sentries, patrols, radar stations, and intelligence centers.
Tactical Core: The Multi-Tool Combo
The tactical heart of this defense is the “multi-tool combo.” Blind spots in a single tool are inevitable, but blind spots across multiple tools can be complementary. Through cross-verification, we minimize the space where risks can hide.
So how many tools do you really need? Two? Four? More is better?
MetaComp’s research delivers a crucial answer: a three-tool combination is the golden rule for optimal balance between effectiveness, cost, and efficiency.
We can understand this “trio” simply:
-
The first tool is your “frontline sentry”: broadest coverage, catching most routine risks.
-
The second is your “special forces patrol”: excels in a niche area (e.g., DeFi risks, regional intelligence), spotting hidden threats the “sentry” misses.
-
The third is your “back-end intelligence analyst”: strongest in data correlation and analysis, connecting fragmented clues from the first two into a complete risk profile.
When these three work together, their power exceeds the sum of parts. Data shows upgrading from two to three tools brings a qualitative leap in compliance efficacy. MetaComp reports that a well-designed three-tool screening model reduces the false clean rate for high-risk transactions to below 0.10%. This means 99.9% of known high-risk transactions are caught. This is what we mean by “combat-ready compliance.”
In contrast, moving from three to four tools offers diminishing returns—only marginal improvements in detection, while significantly increasing cost and processing delay. Research shows four-tool screening can take up to 11 seconds, versus around 2 seconds for three tools. In real-time payment scenarios, that 9-second difference can make or break user experience.
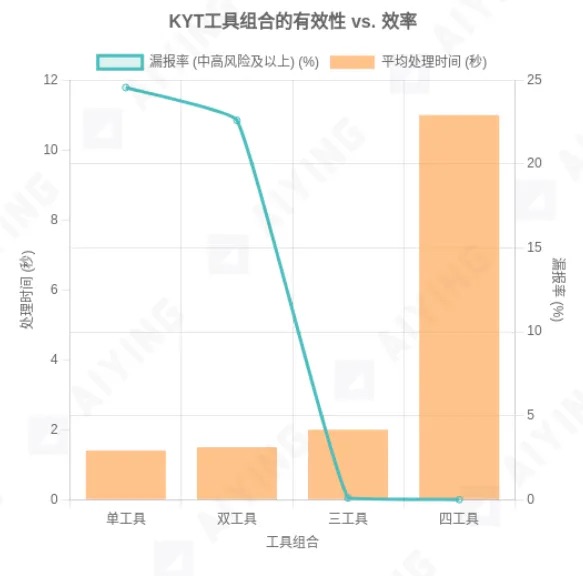
Figure 3: Trade-off between effectiveness and efficiency in KYT tool combinations
Data source: MetaComp Research - Comparative Analysis of On-Chain KYT for AML&CFT, July 2025. The chart clearly illustrates how adding more tools reduces false clean rate (effectiveness) while increasing processing time (efficiency), demonstrating that the three-tool setup offers the best cost-performance ratio.
Implementing the Methodology: Building Your Own Rule Engine
Selecting the right “trio” completes the hardware upgrade. But more importantly, how do you command this multi-unit force? You can’t let each tool speak its own language. You need a central command post—an independent rule engine, separate from any single vendor.
Step One: Standardize Risk Classification—Speak the Same Language
You shouldn’t be led by the tools. Different vendors may use labels like “Coin Mixer,” “Protocol Privacy,” or “Shield” to describe the same risk. Requiring compliance officers to memorize each tool’s dialect is a recipe for disaster. The correct approach is to establish a unified internal classification standard, then map all incoming tool tags to this internal framework.
For example, you could create a standardized taxonomy such as:
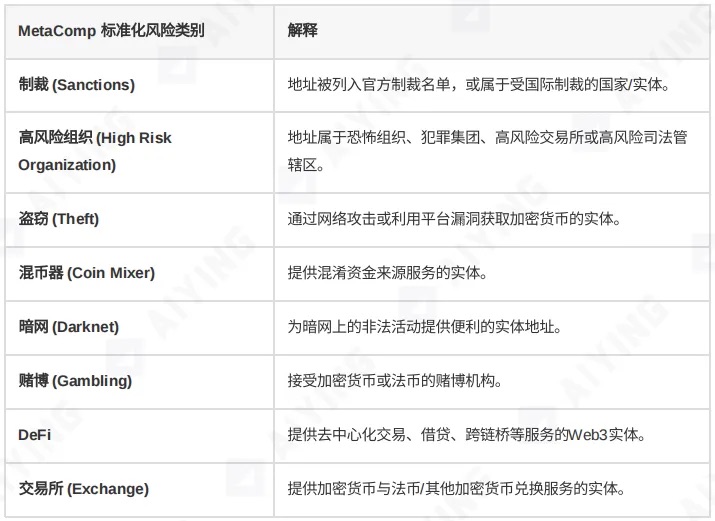
Table 1: Example of risk category mapping table
With this method, no matter which new tool you integrate, you can instantly “translate” it into a common internal language, enabling cross-platform comparison and consistent decision-making.
Step Two: Unified Risk Parameters and Thresholds—Draw Clear Red Lines
With a common language established, the next step is defining unified “rules of engagement.” Based on your organization’s risk appetite and regulatory requirements, set clear, quantifiable risk thresholds. This is the key step in transforming subjective risk preferences into objective, machine-executable instructions.
These rules should go beyond simple amount thresholds, incorporating complex, multi-dimensional parameters such as:
-
Severity level definitions: Clearly define which categories are “critical” (e.g., sanctions, terrorist financing), “high-risk” (e.g., theft, darknet), or “acceptable” (e.g., exchanges, DeFi).
-
Transaction-level taint threshold (Taint %): Define the percentage of funds indirectly linked to high-risk sources that should trigger an alert. This threshold must be scientifically determined through data analysis, not arbitrarily set.
-
Wallet-level cumulative taint threshold (Cumulative Taint %): Define the proportion of historical transactions with high-risk addresses that would classify a wallet as high-risk. This helps identify long-term “career offenders” in gray-market activities.
These thresholds are your red lines. Once crossed, the system must respond according to predefined protocols. This makes the entire compliance decision process transparent, consistent, and defensible.
Step Three: Design a Multi-Layer Screening Workflow—A 3D Strike from Point to Surface
Finally, integrate standardized classifications and unified parameters into an automated, multi-layer screening workflow. This process should function like a precision funnel—filtering progressively, focusing narrowly—to enable accurate risk targeting while minimizing disruption to low-risk transactions.
An effective workflow should include at least these steps:
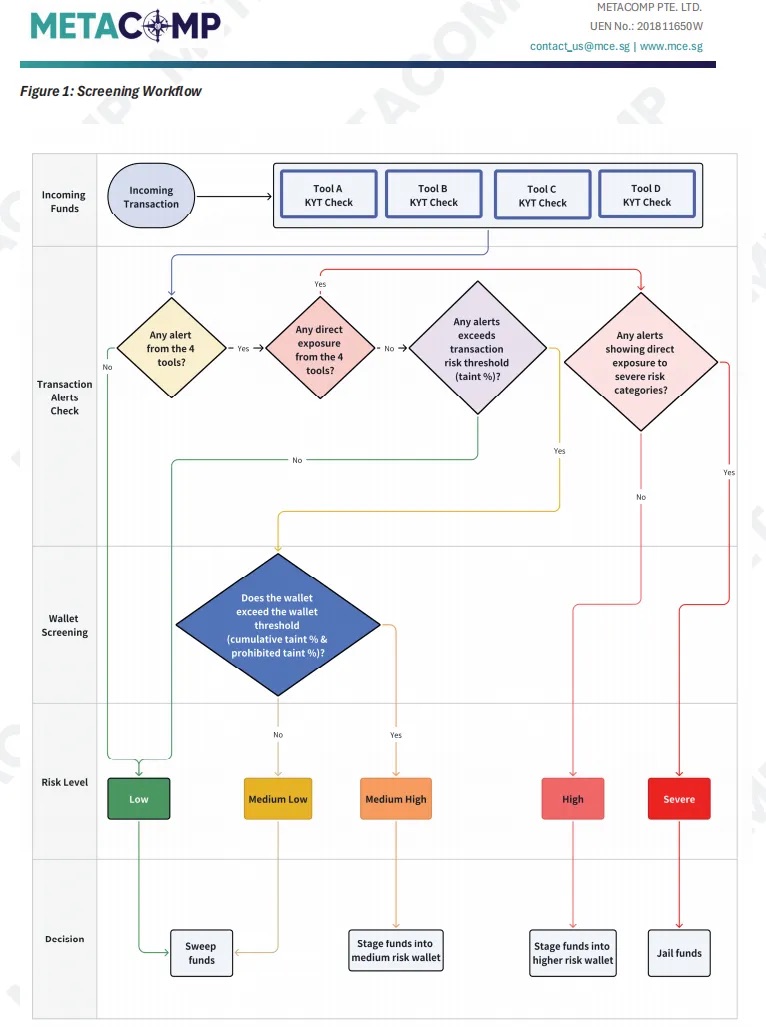
Figure 4: Example of an effective multi-layer screening workflow (adapted from MetaComp KYT methodology)
-
Initial Screening: All transaction hashes and counterparty addresses undergo parallel scanning by the “trio” of tools. Any single alert triggers escalation to the next stage.
-
Direct Exposure Assessment: The system checks whether the alert indicates “direct exposure”—i.e., the counterparty address itself is flagged as “critical” or “high-risk.” If so, it becomes top-priority, triggering immediate freeze or manual review.
-
Transaction-Level Exposure Analysis: If no direct exposure, the system performs “fund溯源,” calculating the percentage (Taint %) of funds indirectly traceable to risk sources. If this exceeds the preset transaction-level threshold, proceed to next step.
-
Wallet-Level Exposure Analysis: For cases exceeding transaction-level risk, the system conducts a “full health check” on the counterparty wallet, assessing its overall historical risk (Cumulative Taint %). If the wallet’s “health score” also falls below the wallet-level threshold, the transaction is confirmed as high-risk.
-
Final Decision: Based on the final risk rating (critical, high, medium-high, medium-low, low), the system automatically executes or prompts manual action: approve, block, refund, or report.
The brilliance of this workflow lies in transforming risk identification from a binary yes/no decision into a three-dimensional assessment—from individual transactions (point), to fund pathways (line), to wallet profiles (surface). It effectively distinguishes between severe “direct hits” and lower-grade “indirect contamination,” optimizing resource allocation: fastest response to highest risks, deeper analysis for medium risks, and rapid clearance for most low-risk transactions—perfectly resolving the tension between alert fatigue and user experience.
Epilogue: Tear Down the Stage, Return to the Battlefield
We’ve spent considerable time dissecting the zombie system, reviewing the tragedy of “compliance theater,” and exploring the playbook for revival. Now, it’s time to return to the beginning.
The greatest harm of “compliance theater” isn’t the budget or manpower it wastes, but the deadly false sense of “security” it creates. It tricks decision-makers into believing risks are under control, and numbs executors through endless, futile labor. A silent zombie system is far more dangerous than no system at all—because it lets you walk defenseless into danger.
In today’s era, where criminal tech evolves in lockstep with financial innovation, relying on a single tool for KYT monitoring is like running naked through a hail of bullets. Criminals wield unprecedented arsenals—automated scripts, cross-chain bridges, privacy coins, DeFi mixers—while your defenses remain stuck years in the past. Breach is inevitable.
Real compliance has never been a performance to please audiences or pass inspections. It’s a hard fight—a prolonged war requiring elite gear (multi-layer tool combos), rigorous tactics (unified risk methodology), and skilled soldiers (professional compliance teams). It doesn’t need grand stages or fake applause. What it needs is respect for risk, honesty with data, and relentless refinement of processes.
Therefore, I call on all professionals in this industry—especially those with resources and decision-making power: abandon the fantasy of a silver bullet solution. No magical tool exists that solves everything once and for all. Compliance building has no finish line—it’s a dynamic lifecycle that must continuously iterate and improve based on data feedback. The defense system you build today will have new vulnerabilities tomorrow. The only response is vigilance, continuous learning, and constant evolution.
It’s time to tear down the fake stage of “compliance theater.” Let’s bring our battle-ready “sentinel systems” back to the real, challenging, yet opportunity-rich battlefield of genuine risk management. Because only there can we truly protect the value we seek to create.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News