
After freezing on-chain transactions following a hack of $260 million, Sui faces centralization criticism over "on-chain censorship"
TechFlow Selected TechFlow Selected

After freezing on-chain transactions following a hack of $260 million, Sui faces centralization criticism over "on-chain censorship"
Cetus' losses in this incident have exceeded the protocol's own TVL and total market capitalization, while Sui has transformed from a "public blockchain" into a "centralized permissioned database."
Author:0xFacai, BlockBeats
On the afternoon of May 22, CETUS, the token of Cetus Protocol—a leading DEX liquidity protocol on the Sui blockchain—plummeted sharply, nearly dropping to zero. Multiple trading pairs on Cetus also experienced steep declines. Subsequently, numerous KOLs posted on X indicating that Cetus Protocol's LP pools had been hacked.
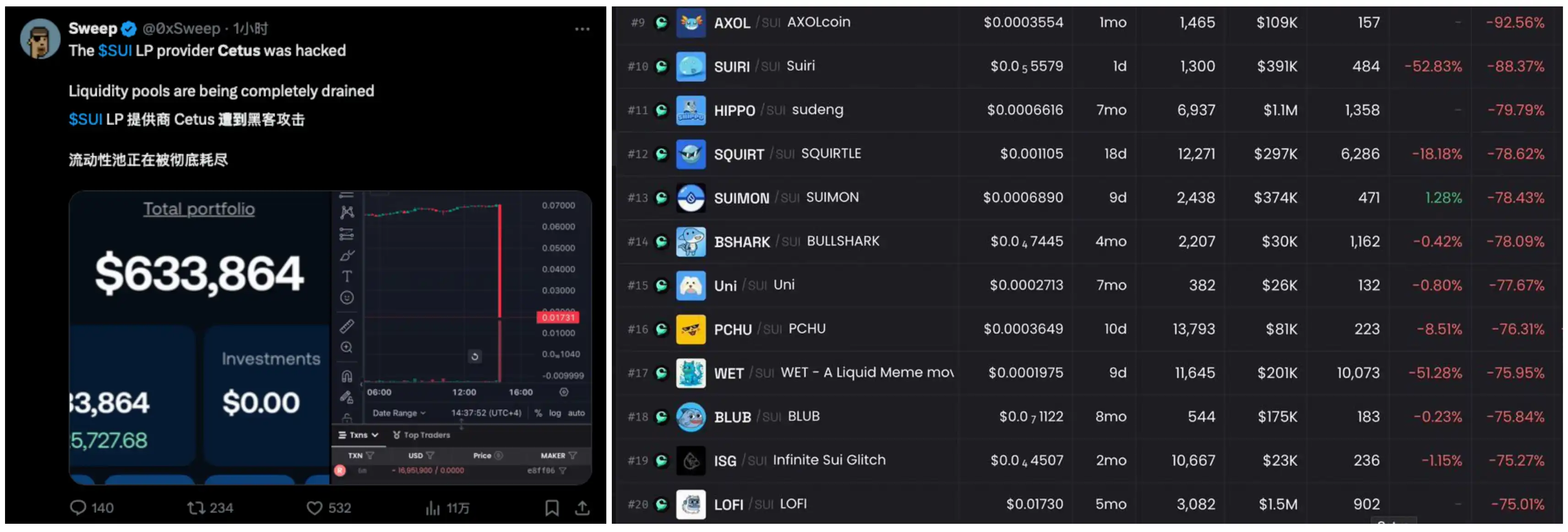
On-chain monitoring shows that the attacker appears to have taken control of all LP pools priced in SUI. At the time of writing, stolen funds exceeded $260 million. The hacker has already begun converting the funds into USDC and bridging them to the Ethereum mainnet for exchange into ETH, with approximately 60 million USDC successfully transferred cross-chain.
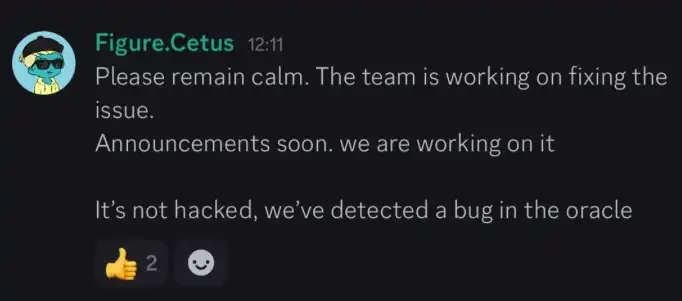
The hacker’s on-chain address is: 0xe28b50cef1d633ea43d3296a3f6b67ff0312a5f1a99f0af753c85b8b5de8ff06. The primary assets in this address remain SUI and USDT, though it also holds major Sui ecosystem tokens such as CETUS, WAL, and DEEP, indicating the wide scope of this hack.
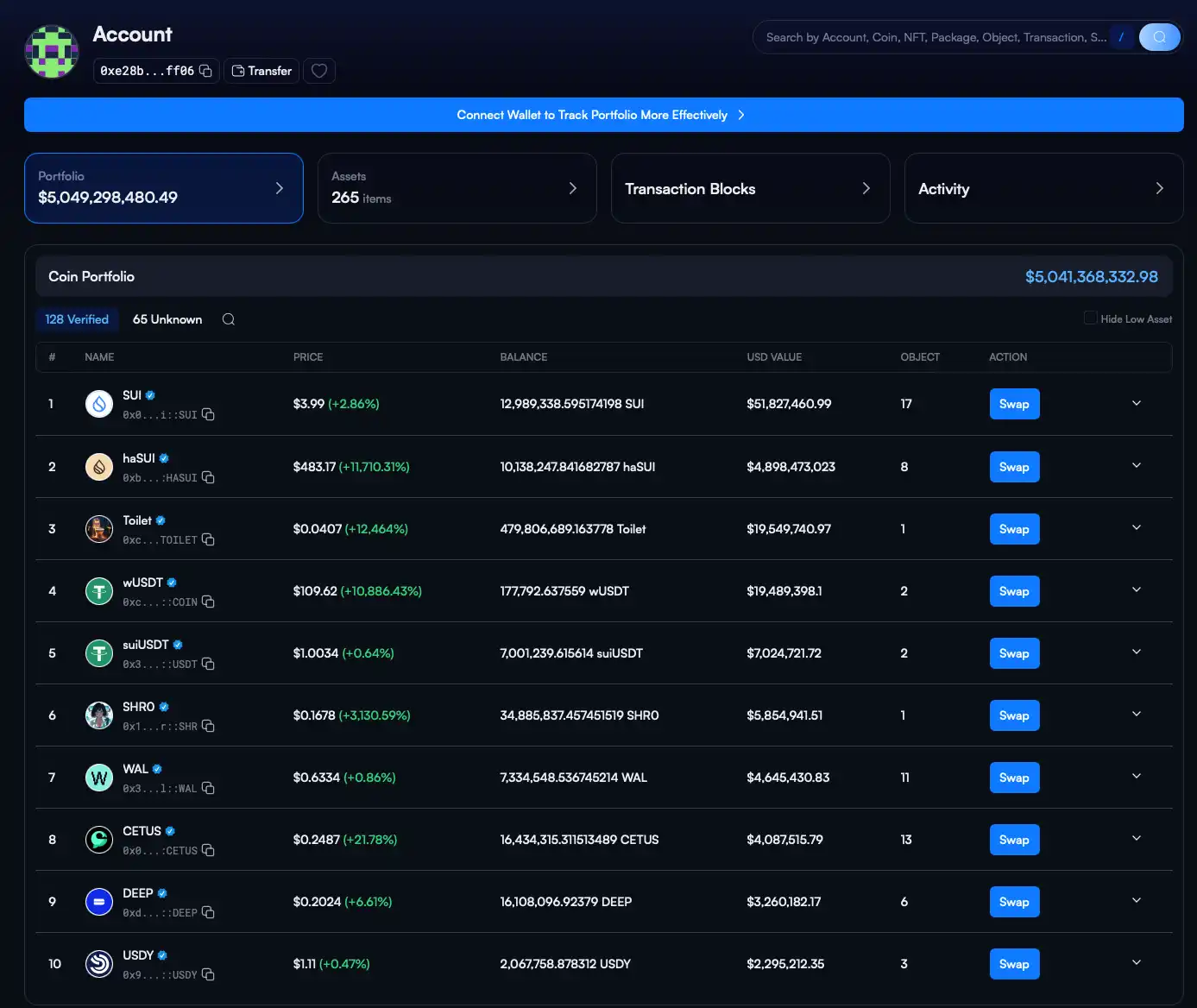
On the evening of the 22nd, a member of the Cetus team stated in the project’s Discord chat that the protocol was not hacked but instead suffered from an "oracle bug." However, on-chain data does not lie. Statistics show that within one hour of the incident, losses in Cetus Protocol's LP pools surpassed $260 million—exceeding both the protocol’s TVL ($240 million) and market cap ($180 million).
On the morning of the 23rd, TechFlow announced via social media the latest developments regarding the breach, stating that the team had identified the root cause of the vulnerability and patched the relevant software package. They have also engaged a professional anti-cybercrime organization to assist with fund tracking and negotiations concerning the safe return of funds. The team is currently communicating with law enforcement and arranging further support.
Notably, the official statement confirmed the Ethereum wallet address controlled by the hacker involved in the earlier attack and indicated that discussions are underway regarding the return of customer funds. They have offered to pay the outstanding balance under the designation of a white-hat hacker, but with limited time. If the hacker accepts the terms, no further legal action will be taken.
Community points out team's prior history of breaches
Interestingly, as Cetus triggered a sharp decline across the SUI ecosystem, many community members pointed out on Twitter that Cetus was developed by the same team behind Crema Finance, a former DeFi protocol in the Solana ecosystem that had previously been hacked.
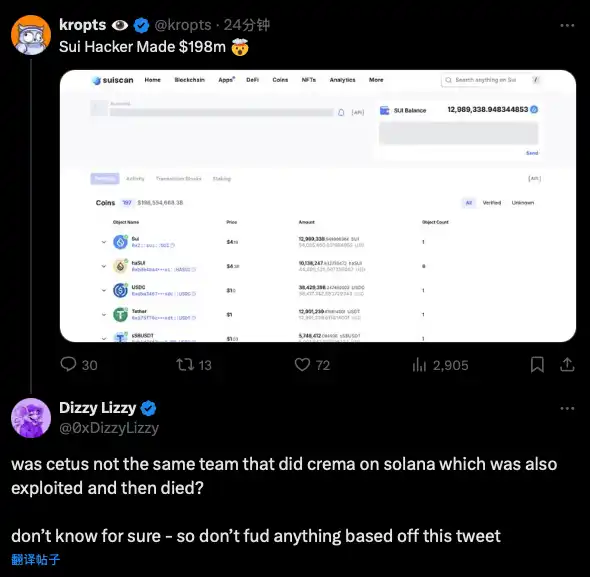
On July 3, 2022, Crema Finance was similarly attacked using Solend flash loans, draining its LP funds and causing over $8 million in losses. On July 7, the hacker returned $7.6 million worth of stolen cryptocurrency after negotiating with the team. According to the agreement, the hacker was allowed to keep 45,455 SOL (worth $1.65 million) as a bounty.
Looking at the current Cetus breach, the protocol again suffered losses due to the attacker gaining control of the LP pool, and the team once again resorted to negotiating with the hacker by offering payment of the remaining balance under the guise of a white-hat bounty. While there is currently no public confirmation that Crema and Cetus are indeed developed by the same team, both the cause of the breach and the subsequent handling appear strikingly consistent.
Sui foundation intervenes to freeze hacker transactions, sparking centralization concerns over on-chain censorship
According to DeFiLlama data, Cetus had long been the leading DEX and liquidity hub in the Sui ecosystem, accounting for over 60% of total ecosystem trading volume. This "liquidation-style" attack directly compromised the ecosystem’s core liquidity center—an event that would be devastating for any so-called "second-tier public chain."
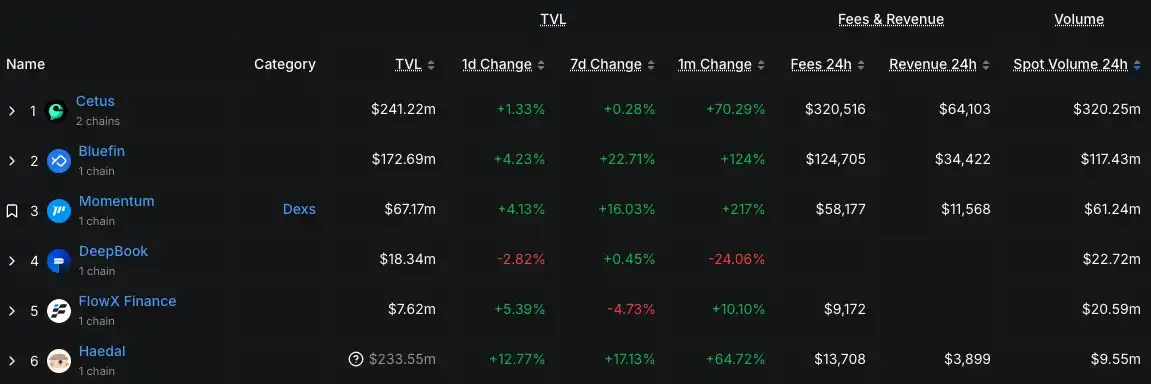
Since March last year, on-chain trading volume in the Sui ecosystem has shown a generally upward trend, with major ecosystem tokens like CETUS, DEEP, and WAL surging in price. The network has widely been seen by the community as one of the most promising high-return chains in this cycle and dubbed the "next Solana."
However, interestingly, Dune data indicates that the Sui chain has consistently exhibited a large amount of wash trading, with long-term flow toxicity hovering near 50%. This partly explains community feedback describing the Sui ecosystem as “nothing tangible, yet prices just keep rising.”
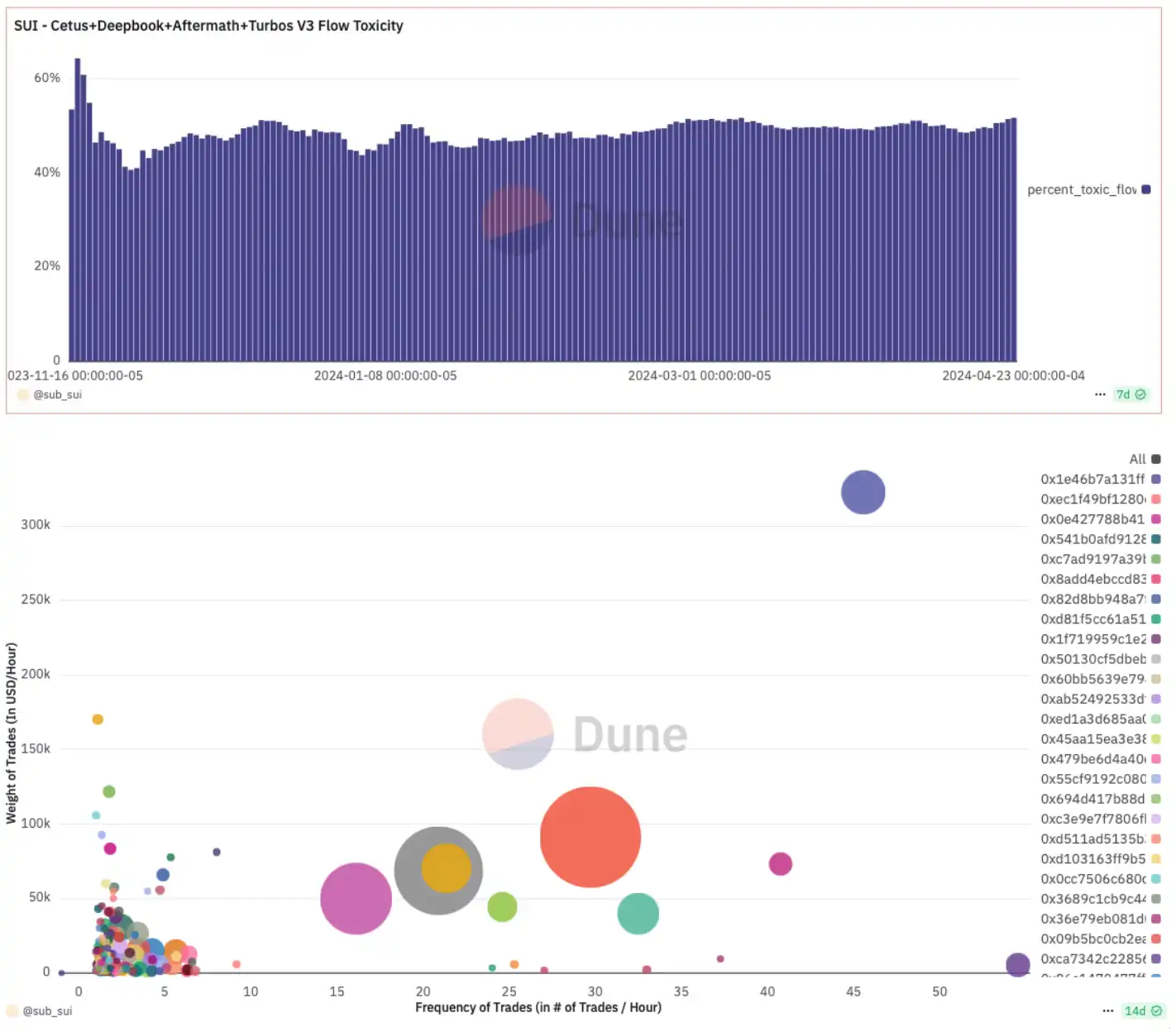
Caption: In the chart below, circle radius represents the total trading volume of a single address. The largest trading wallets also show high transaction frequency, suggesting possible wash trading; Data source: Dune Analytics
Nonetheless, Sui’s reputation as a “heavily backed chain” has long been established among traders. During the recent altcoin recovery, Sui stood out as the best-performing major public chain. Faced with this major ecosystem breach, the foundation lived up to expectations by quickly responding, further reinforcing its image as a “heavily backed chain.”
At around 11 PM on May 22, the Sui Foundation issued a statement saying that, in order to “protect the Sui ecosystem,” a large number of Sui network validators had identified the hacker’s addresses using the stolen funds and were ignoring transactions from these addresses. Meanwhile, the CETUS team is actively exploring ways to recover the funds and return them to the community, and will soon release a detailed incident report.
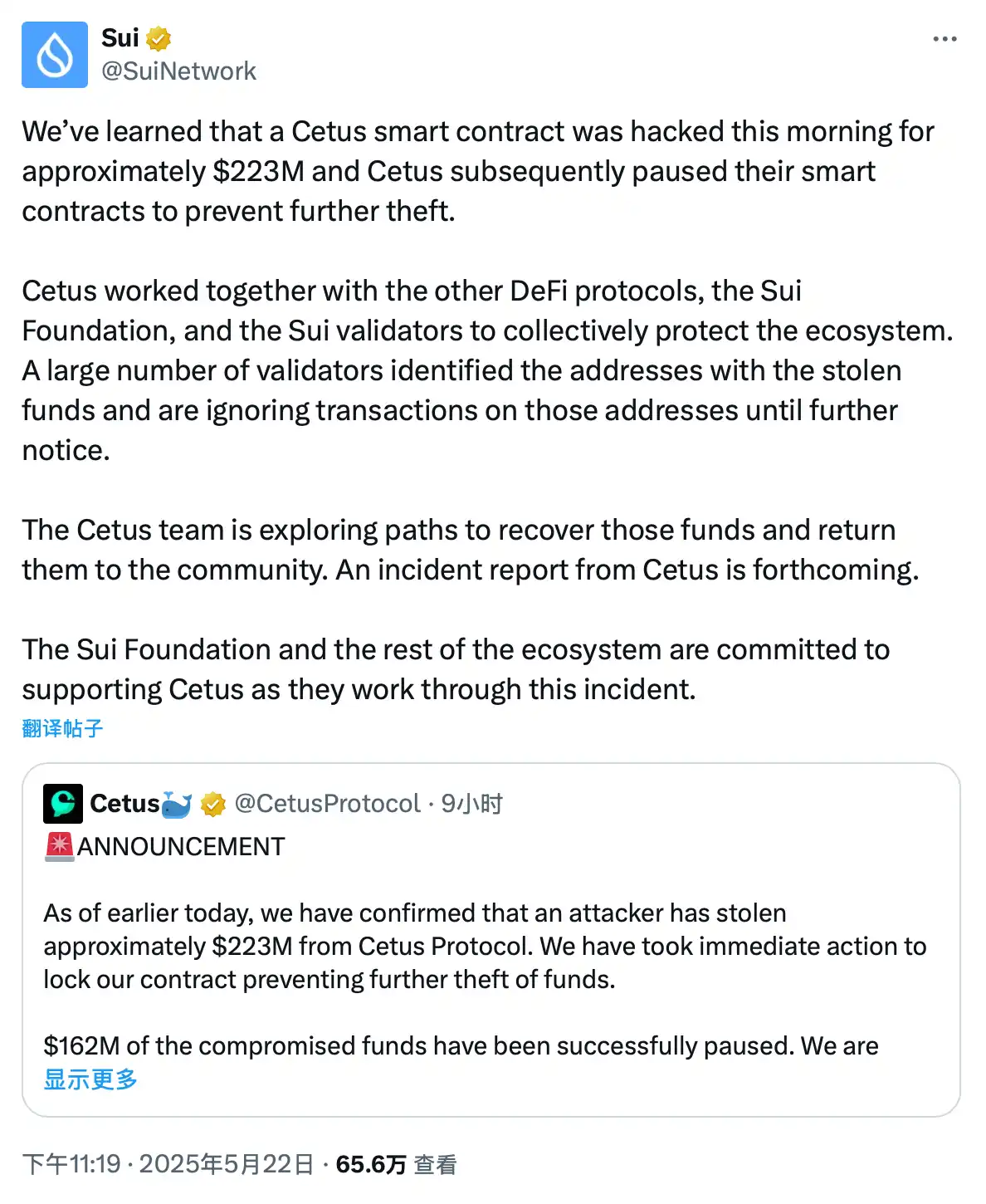
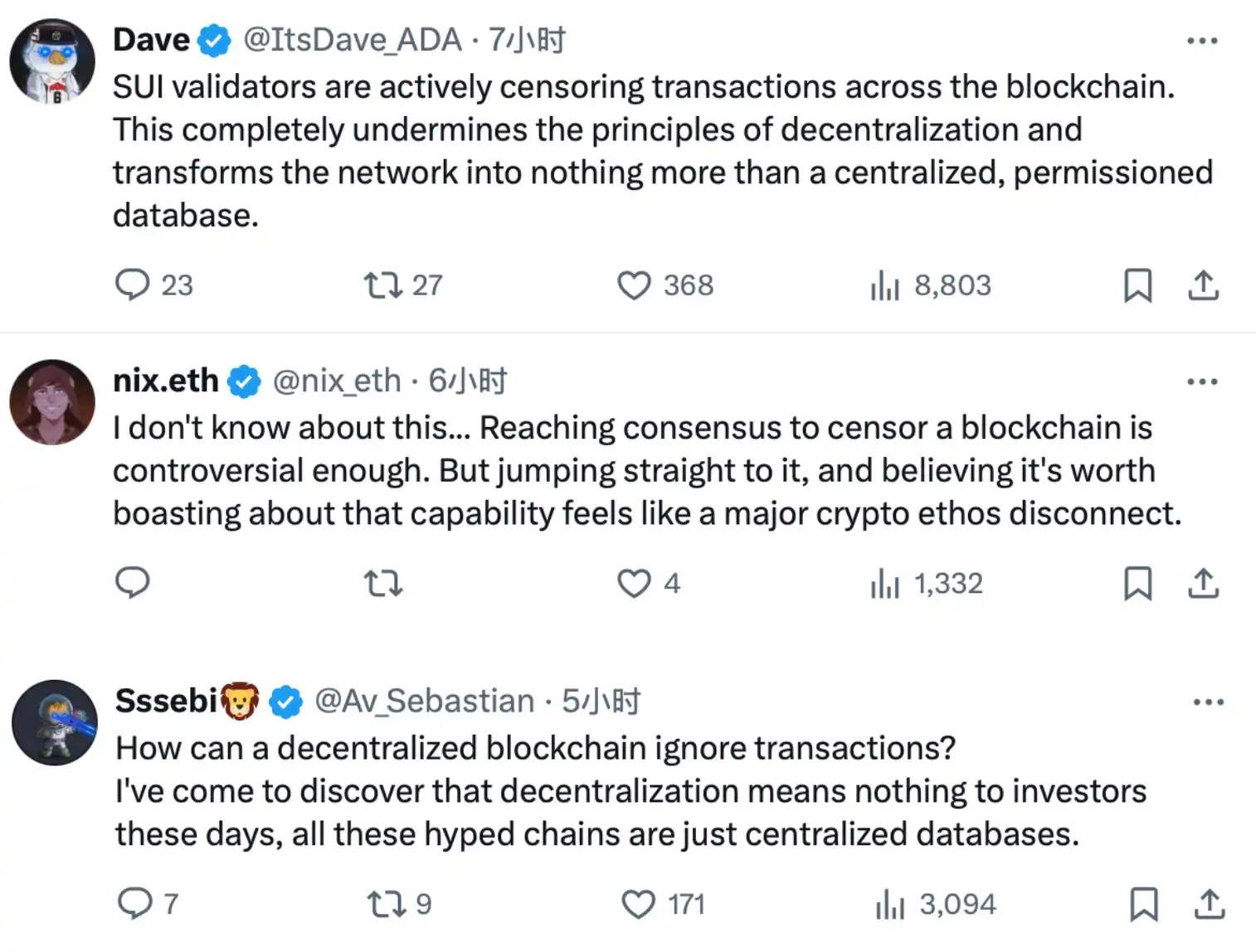
Upon release of this news, the community erupted, with “chain-level transaction censorship” becoming the biggest point of contention. Many users on X argued that Sui’s response undermined its decentralized positioning, effectively transforming it from a “public blockchain” into a “centralized permissioned database.”
According to Sui’s official documentation, transactions on the Sui network are divided into two types: those involving only "owned objects" and those involving "shared objects." Only transactions involving shared objects require full network consensus, while pure owned-object transactions can take a "direct fast path," executing without global ordering. As long as more than 2/3 of the total staked weight in the network remains honest, the network theoretically maintains both security (no double-spends) and liveness (valid transactions are eventually executed).
Under Sui’s delegated PoS + BFT design, sustained and indiscriminate transaction censorship would require controlling at least 1/3 of the staked voting power. Individual or minority node censorship could only cause temporary delays and would likely be flagged as malicious behavior, leading stakers to "vote them offline" in the next epoch—this is what the official documentation refers to as "censorship resistance and openness." Clearly, in this hacking incident, the Sui Foundation controlled at least 1/3 of the network’s staked voting power.
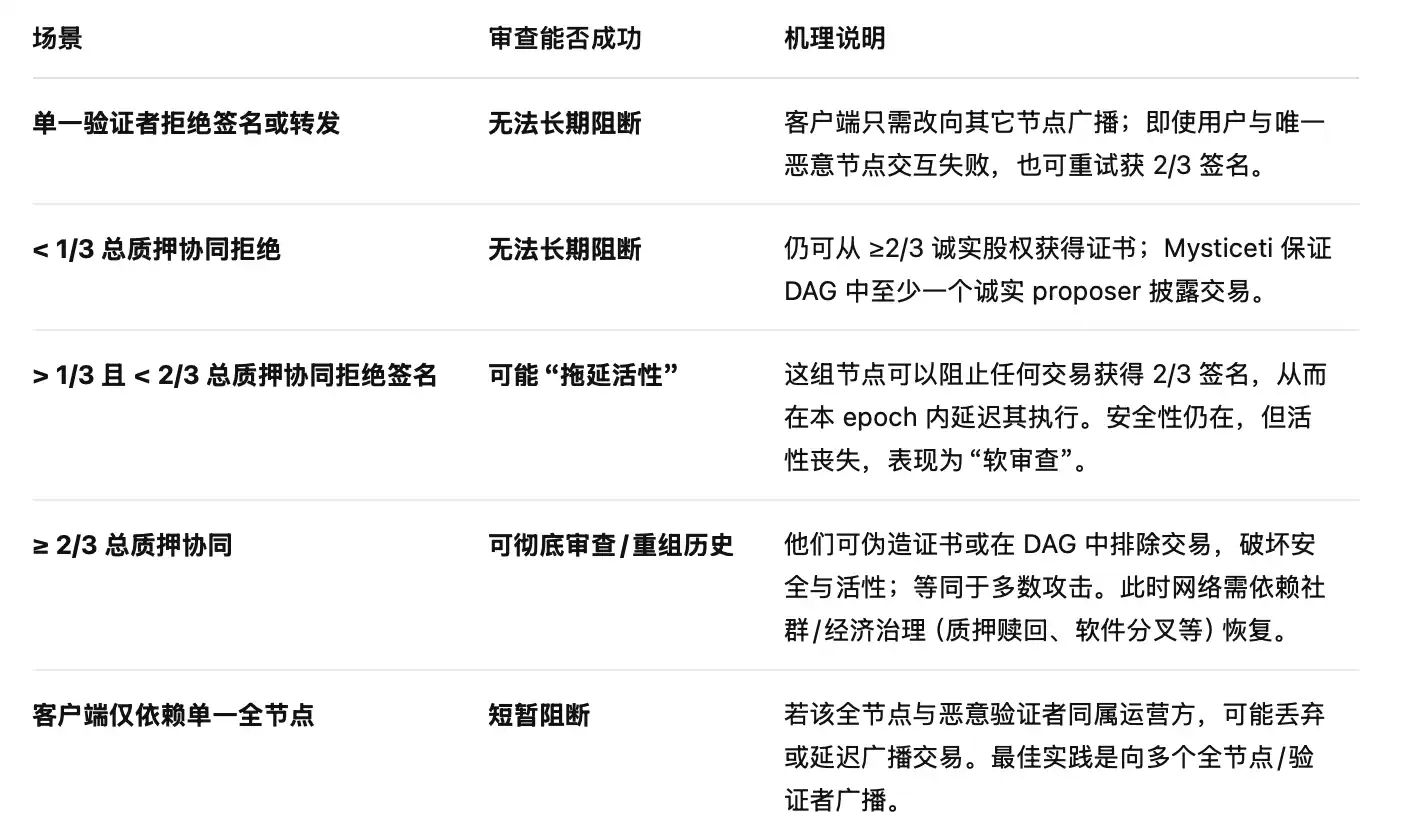
Comparison of transaction censorship scenarios under Sui network consensus mechanism
The debate over "centralized blockchains" dates back to Solana in the previous cycle. Some community members have noted that "censorship resistance" may not be the top priority for current crypto investors. In a world still driven primarily by returns, perhaps "price pumping" is seen as justice.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















