Infini stolen 50 million USD: Suspected insider involvement, contract engineer's 100x leveraged token trade liquidated
TechFlow Selected TechFlow Selected

Infini stolen 50 million USD: Suspected insider involvement, contract engineer's 100x leveraged token trade liquidated
When all the evidence pointed to someone who had once been highly trusted within the team, everyone was shocked.
Author: Cat Brother, Wu Shuo Blockchain
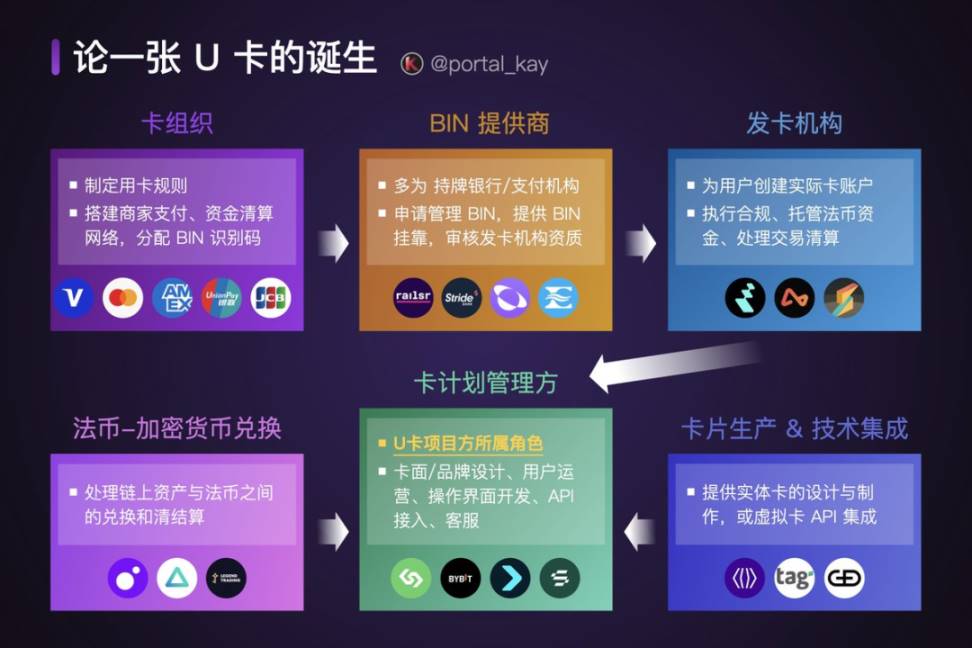
Background
On February 24, the Web3 credit card and wealth management project Infini was hacked, resulting in $49.5 million being drained from the Morpho MEV Capital Usual USDC Vault. At the time, Infini founder Christian stated: "70% of the $50 million stolen belongs to close acquaintances and large holders; I have personally communicated with each of them and will bear any potential losses myself. The remaining funds will be reinvested into the Infini vault before next Monday, and operations will continue as normal." He also offered to pay the hacker 20% of the stolen amount as a ransom and promised not to pursue legal action if the funds were returned.
At 8:00 PM on February 24, the Infini Team sent an on-chain message to Infini Exploiter 2: 0xfc...6e49:
We hereby notify you that we have obtained critical IP and device information related to your attack on Infini. This has been made possible through strong support from top-tier exchanges, security agencies, partners, and our community. We are closely monitoring the relevant addresses and are fully prepared to freeze the stolen funds at any moment. To resolve this matter peacefully, we are willing to offer 20% of the stolen assets as a reward, provided you choose to return the funds. Upon receipt of the returned assets, we will cease all further tracking or analysis, and you will face no liability. We kindly urge you to act within the next 48 hours so a solution can be reached swiftly. If we do not receive a response within this timeframe, we will have no choice but to cooperate further with local law enforcement agencies to conduct an in-depth investigation. We sincerely hope to reach a solution that benefits all parties involved.
On February 26, the Infini Team sent another on-chain message:
More than 48 hours have passed since the attack. We are offering you one final opportunity to return the stolen funds. If you return the assets, we will immediately halt all tracking and analysis, and you will face no consequences. Please send 14,156 ETH (80% of the stolen funds) to our Cobo custodial wallet:
Wallet Address: 0x7e857de437a4dda3a98cf3fd37d6b36c139594e8
On February 27, Christian announced that a formal case regarding the Infini hack had been filed in Hong Kong.
On the financial side, the hacker's address 0x3a...5Ed0 converted 49.52 million USDC into an equivalent amount of DAI via Sky (MakerDAO) on February 24, then swapped the DAI for approximately 17,700 ETH in multiple transactions via Uniswap, sending them to a new address: 0xfcC8Ad911976d752890f2140D9F4edd2c64a6e49. Since then, these funds have not moved further (suggesting the individual may have been promptly taken into custody by authorities). However, due to the recent drop in ETH prices, the ETH is now worth only $35.15 million.
https://intel.arkm.com/explorer/address/0xfcC8Ad911976d752890f2140D9F4edd2c64a6e49
Lawsuit Details
At 6:00 PM on March 20, the Infini Team sent another on-chain message to Infini Exploiter 2: 0xfc...6e49, issuing a warning stating that the $50 million lost in the Infini attack is currently subject to ongoing legal disputes and is contested. Any subsequent holders of the crypto assets previously held in the said wallet (if any) cannot claim to be bona fide purchasers.
The message also included, via link, court litigation documents with the following details:
The plaintiff is Chou Christian-Long, CEO of BP SG Investment Holding Limited—a Hong Kong-registered company fully owned by Infini Labs. The first defendant is Chen Shanxuan, based in Foshan, Guangdong, who worked remotely. The second to fourth defendants are currently unidentified.
The plaintiff, together with BP Singapore, developed a smart contract to manage company and client funds, which was primarily coded by the first defendant. The contract originally implemented a multi-signature ("multi-sig") permission system to strictly control all fund withdrawals.
Upon deployment to the mainnet, the first defendant allegedly retained the highest-level "super admin" privilege, while falsely claiming to other team members that he had transferred or removed this authority.
In late February 2025, the plaintiff discovered that approximately $49,516,662.977 worth of USDC had been transferred without multi-sig approval to several unknown wallet addresses—controlled by the second to fourth defendants.
Fearing that the defendants or unidentified individuals might further transfer or launder the assets, the plaintiff petitioned the court to:
-
Issue an injunction to restrict the first defendant and related unidentified persons from transferring or disposing of the stolen assets;
-
Require the defendants or actual controllers of the wallets to disclose their identities;
-
Issue mandatory orders prohibiting the disposal of assets by the first defendant and other unknown wallet holders;
-
Require disclosure of transaction and asset information;
-
Allow the plaintiff to serve legal documents extraterritorially (i.e., to defendants abroad) via alternative means.
In the body of one affidavit, the plaintiff stated: "Only recently did I learn that the first defendant has a serious gambling habit, possibly leading to massive debts. I believe this motivated him to steal the assets to alleviate his financial burden." The plaintiff submitted screenshots of messaging records to support claims that the first defendant may be deeply indebted. (The plaintiff alleges the defendant later became obsessed, routinely opening 100x leveraged futures contracts.)
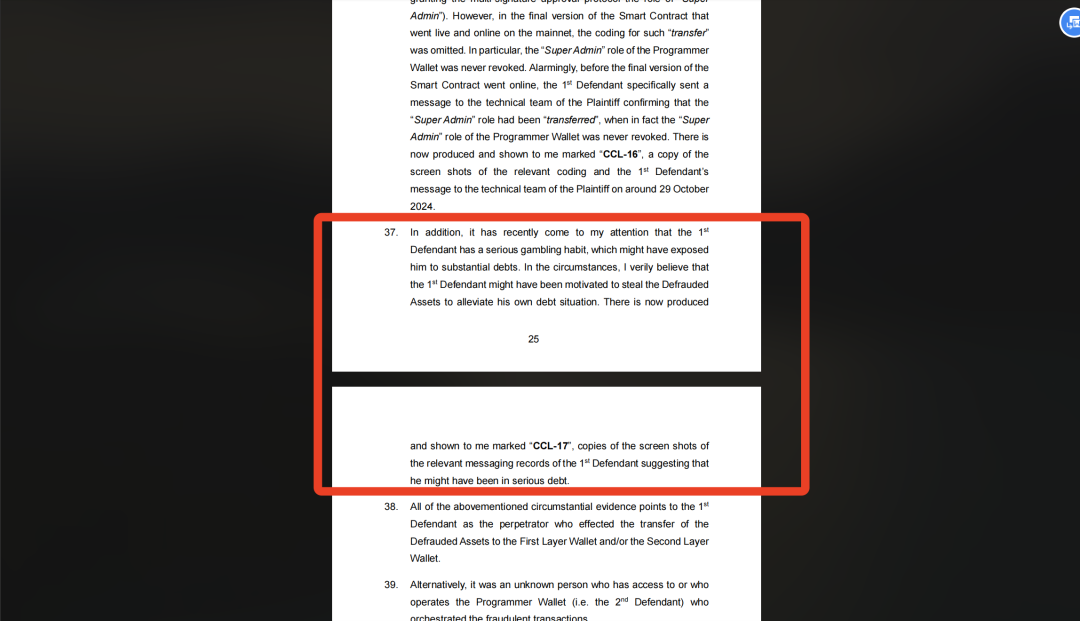
According to the affidavit, the first defendant borrowed money from various sources over a relatively short period and may have even contacted underground lenders or loan sharks, facing high interest rates and constant debt collection calls. Exhibit CCL-17 references conversations in which he pleaded for help, stating he was paying interest to multiple lenders and repeatedly asking whether more loans could be arranged or requesting introductions to new funding sources.
Shortly before the incident, the first defendant hinted in work group chats and private conversations with colleagues and friends that his financial situation was extremely tight, even expressing anxiety about "something bad happening" if he couldn't secure more funds. These statements closely coincide with the unauthorized transfer of company crypto assets, reinforcing the plaintiff’s belief about the defendant’s motive: resorting to theft under pressure from overwhelming debt.
According to the plaintiff, whenever questioned about his personal finances or gambling habits, the first defendant repeatedly evaded the topic or gave vague answers, never clearly disclosing how much he owed or whether he continued gambling. The affidavit notes that from late October until the incident, he consistently claimed there were "no big issues," yet his private chat content directly contradicted this.
The plaintiff fears that if the first defendant urgently needs to repay gambling debts or chase losses, he may quickly move the stolen digital assets to other wallets or cash out off-chain, making recovery even more difficult. Hence, the urgent application to the court for a worldwide asset freeze order, demanding the first defendant and other unidentified wallet holders disclose and return the涉案 crypto assets.
Bane, partner at Kronos Research, stated that the team holds many additional outrageous personal materials not included in the court filings, though they are not directly relevant to the case. The focus remains on recovering the funds. "When all evidence points to someone once deeply trusted within the team, everyone was shocked. But motive is not proof—everything must be grounded in facts. We believe the law will deliver a fair outcome. Until judgment, he remains a suspect."
Bane added: "We all believed the super admin privileges had been handed over to the multi-sig. But he used OpenZeppelin’s permission library, which supports multiple admins by default. So the original dev wallet never actually relinquished its privileges. Typically, teams deploy using an EOA (externally owned account), then transfer permissions to a multi-sig afterward. His dev wallet, controlling the contract, by default held super admin[0] rights under OpenZeppelin’s initial setup. He later 'transferred' super admin rights to the multi-sig and falsely claimed in chat logs that he had renounced his EOA privileges—but the revoke transaction was never actually broadcast. Later, he claimed he misunderstood the system, thinking it was one-to-one rather than many-to-many—implying he believed that granting permissions to the multi-sig automatically revoked his own. Due to trust, no one double-checked the contract state, leading to this tragedy."
After the incident, the defendant reportedly said: "My mistake. I forgot to revoke the permissions—an extremely basic error."
The case has not yet been adjudicated. The submitted litigation documents include extensive chat logs from the first defendant. Interested readers may download the full file:
Link: https://howsewilliams-my.sharepoint.com/:f:/p/regulatory/EtrvPWcvev1An5eEDMRNoRgBc1Ih7x0l6dR-Cf-0E-rC8Q?e=1g9OPJ
Password: D1234@5##
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News