
2024 Annual Report on the Security Landscape of Web3 Blockchain
TechFlow Selected TechFlow Selected

2024 Annual Report on the Security Landscape of Web3 Blockchain
Gain a comprehensive understanding of the dynamic evolution of Web3 blockchain security posture.
Author: Beosin
Introduction
This research report is initiated by the Blockchain Security Alliance and jointly authored by alliance members Beosin and Footprint Analytics, aiming to comprehensively explore the global blockchain security landscape in 2024. Through analysis and assessment of the current state of blockchain security worldwide, the report reveals existing security challenges and threats while offering solutions and best practices.
This report enables readers to gain a more comprehensive understanding of the dynamic evolution of Web3 blockchain security. It helps readers evaluate and respond to security challenges in the blockchain domain. Additionally, readers can obtain valuable insights on security measures and industry trends to make informed decisions and actions in this emerging field. Blockchain security and regulation are critical issues for the development of the Web3 era. Through in-depth research and discussion, we can better understand and address these challenges, promoting the safety and sustainable development of blockchain technology.
1. Overview of the 2024 Web3 Blockchain Security Landscape

According to monitoring from Alert, a platform under blockchain security firm Beosin, total losses in the Web3 sector due to hacking attacks, phishing scams, and project team rug pulls reached $2.513 billion in 2024. This includes 131 major attack incidents resulting in approximately $1.792 billion in losses; 68 rug pull incidents causing about $148 million in losses; and phishing scams leading to around $574 million in losses.
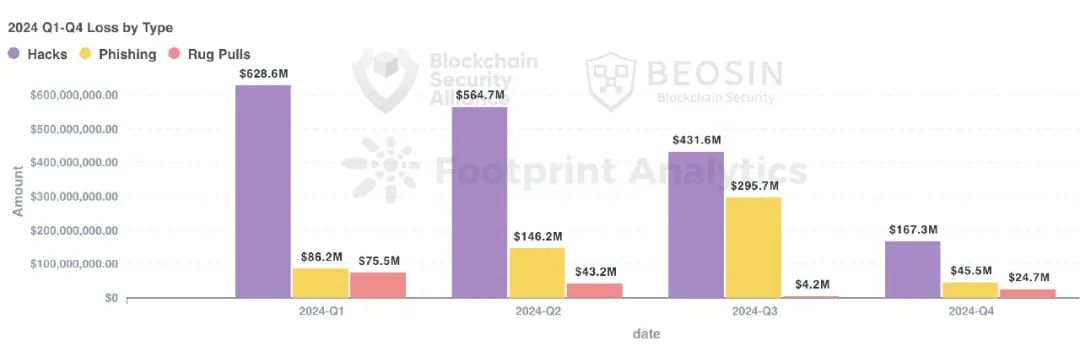
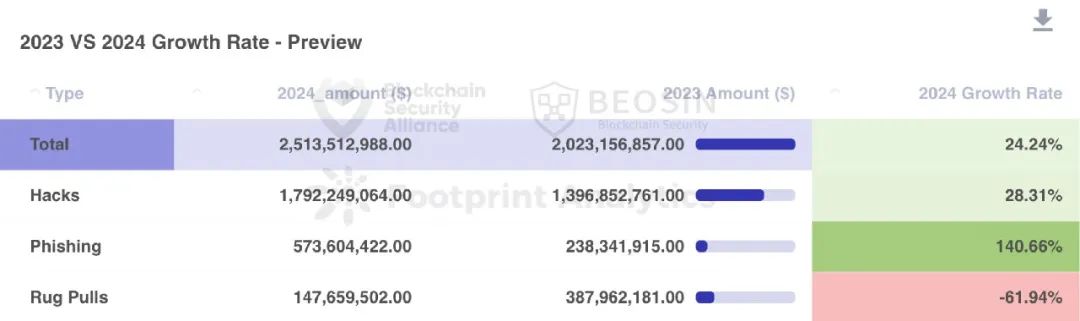
In 2024, both hacking attacks and phishing scam amounts increased significantly compared to 2023, with phishing scams surging 140.66% year-on-year. Losses from project team rug pulls dropped significantly, decreasing by approximately 61.94%.
In 2024, attacked projects included various types such as DeFi, CEXs, DEXs, public chains, cross-chain bridges, wallets, payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV bots, and Telegram bots. DeFi was the most frequently targeted type, with 75 attacks causing total losses of approximately $390 million. CEXs suffered the highest total financial loss, where 10 attacks resulted in about $724 million in losses.
In 2024, a wider range of public chains experienced security breaches, including multiple incidents across several blockchains. Ethereum remained the chain with the highest financial loss, with 66 attack events on Ethereum causing approximately $844 million in losses, accounting for 33.57% of annual total losses.
In terms of attack methods, private key leaks caused $1.306 billion in losses through 35 incidents, representing 51.96% of total losses and making it the most damaging attack method.
Smart contract vulnerability exploitation was the most frequent attack method, with 76 out of 131 attack incidents (58.02%) stemming from contract vulnerabilities.
Approximately $531 million in stolen funds were recovered during the year, accounting for about 21.13%. Around $109 million in stolen funds were sent to mixers, approximately 4.34% of total stolen assets, down about 66.97% compared to 2023.
2. Top 10 Web3 Security Incidents in 2024
In 2024, there were five attack incidents each exceeding $100 million in losses: DMM Bitcoin ($304 million), PlayDapp ($290 million), WazirX ($235 million), Gala Games ($216 million), and Chris Larsen theft ($112 million). The top 10 security incidents accounted for approximately $1.417 billion in total losses, about 79.07% of the annual total from attack events.
No.1 DMM Bitcoin
Loss Amount: $304 million
Attack Method: Private Key Leak
On May 31, 2024, Japanese cryptocurrency exchange DMM Bitcoin was attacked, resulting in over $300 million worth of Bitcoin being stolen. The hacker dispersed the stolen funds across more than ten addresses attempting to launder them.
No.2 PlayDapp
Loss Amount: $290 million
Attack Method: Private Key Leak
On February 9, 2024, blockchain gaming platform PlayDapp was attacked, with hackers minting 2 billion PLA tokens valued at $36.5 million. After failed negotiations with PlayDapp, on February 12, the hacker minted another 15.9 billion PLA tokens worth $253.9 million and transferred part of the funds to Gate.io. The PlayDapp team subsequently paused the PLA contract and migrated PLA tokens to PDA tokens.
No.3 WazirX
Loss Amount: $235 million
Attack Method: Cyberattack and Phishing
On July 18, 2024, India's cryptocurrency exchange WazirX lost over $230 million from its multisig wallet, which used the Safe Wallet smart contract. Attackers tricked multisig signers into approving a contract upgrade transaction, allowing them to directly transfer assets from the upgraded contract, ultimately withdrawing all assets totaling over $230 million.
No.4 Gala Games
Loss Amount: $216 million
Attack Method: Access Control Vulnerability
On May 20, 2024, a privileged address of Gala Games was compromised. The attacker called the token mint function via this address to directly mint 5 billion GALA tokens valued at approximately $216 million, then gradually exchanged the newly issued tokens for ETH. Subsequently, the Gala Games team used blacklist functionality to block the hacker and recover some losses.
No.5 Chris Larsen (Ripple's co-founder)
Loss Amount: $112 million
Attack Method: Private Key Leak
On January 31, 2024, Ripple co-founder Chris Larsen reported that four of his wallets had been breached, resulting in total losses of about $112 million. Binance successfully froze $4.2 million worth of stolen XRP tokens.
No.6 Munchables
Loss Amount: $62.5 million
Attack Method: Social Engineering Attack
On March 26, 2024, Blast-based Web3 gaming platform Munchables was attacked, suffering losses of about $62.5 million. The breach occurred because the project hired North Korean hackers as developers. All stolen funds were eventually returned by the hackers.
No.7 BTCTurk
Loss Amount: $55 million
Attack Method: Private Key Leak
On June 22, 2024, Turkish cryptocurrency exchange BTCTurk was attacked, losing about $55 million. Binance assisted in freezing over $5.3 million worth of stolen funds.
No.8 Radiant Capital
Loss Amount: $53 million
Attack Method: Private Key Leak
On October 17, 2024, multi-chain lending protocol Radiant Capital was attacked. Attackers illegally obtained permissions from three owners within Radiant Capital’s multisig wallet. Since the multisig wallet used a 3/11 signature verification model, attackers used these three private keys to conduct off-chain signatures, then initiated on-chain transactions to transfer ownership of the Radiant Capital contract to a malicious contract controlled by the attackers, causing losses exceeding $53 million.
No.9 Hedgey Finance
Loss Amount: $44.7 million
Attack Method: Contract Vulnerability
On April 19, 2024, Hedgey Finance suffered multiple attacks. Exploiting a token approval vulnerability, attackers stole large quantities of tokens from the ClaimCampaigns contract—over $2.1 million worth on Ethereum and about $42.6 million on Arbitrum.
No.10 BingX
Loss Amount: $44.7 million
Attack Method: Private Key Leak
On September 19, 2024, BingX exchange’s hot wallet was hacked. Although BingX activated emergency protocols including urgent asset transfers and withdrawal suspension, according to Beosin statistics, abnormal outflows from the hot wallet led to total losses reaching $44.7 million. Stolen assets spanned multiple blockchains including Ethereum, BNB Chain, Tron, Polygon, Avalanche, and Base.
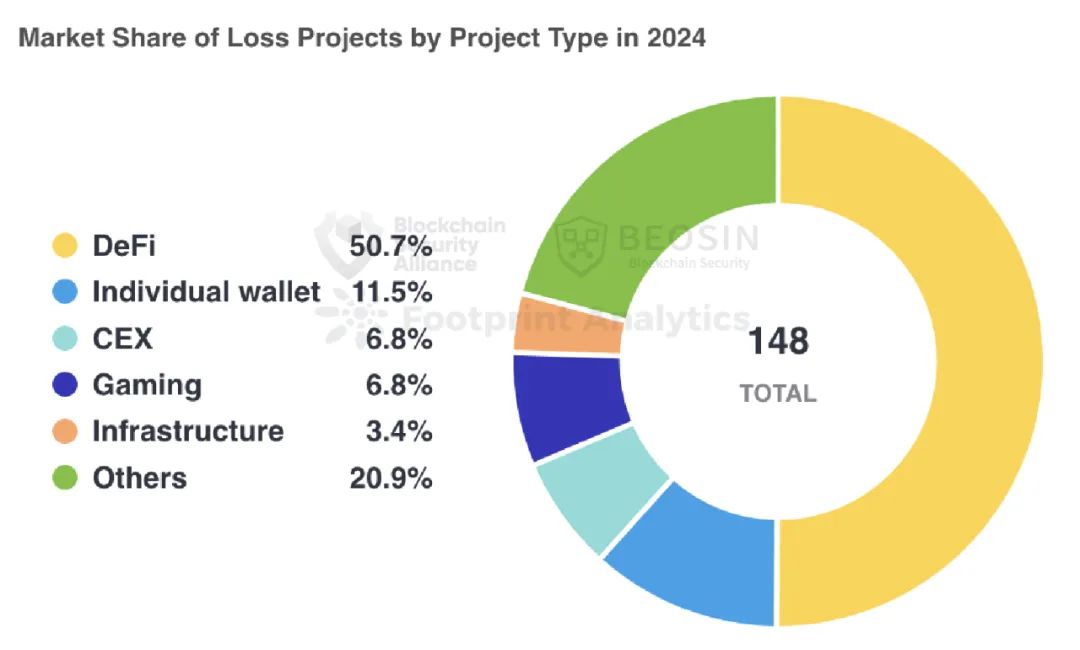
3. Types of Attacked Projects
Besides common categories like DeFi, CEXs, DEXs, public chains, cross-chain bridges, and wallets, attacked projects in 2024 also included payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV bots, and Telegram bots.
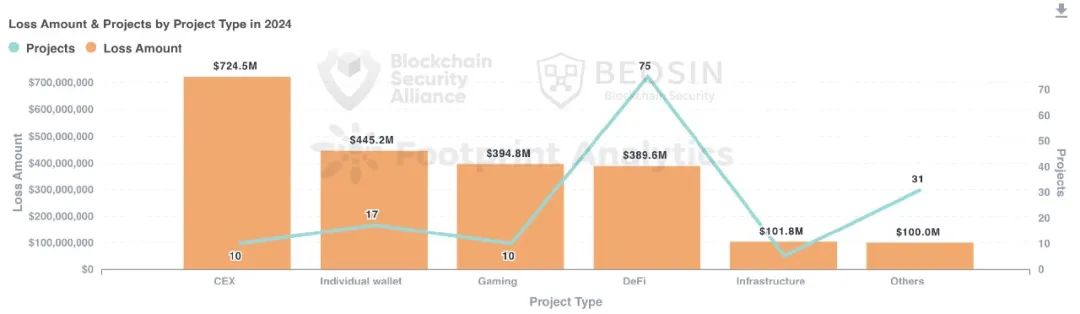
In 2024, DeFi projects faced 75 attack incidents—the highest number (about 50.70%) among all project types. Total losses from DeFi attacks amounted to approximately $390 million, roughly 15.50% of all losses, ranking fourth in terms of financial impact.
CEXs ranked first in financial losses, with 10 attacks causing about $724 million in total losses, making them the costliest target type. Overall, exchanges continued to face frequent security incidents in 2024, indicating exchange security remains the biggest challenge in the Web3 ecosystem.
Personal wallets ranked second in financial losses, totaling about $445 million. Twelve attacks targeting crypto whales combined with numerous phishing and social engineering attacks against regular users caused personal wallet losses to surge 464.72% compared to 2023, making it the second-largest security challenge after exchange security.
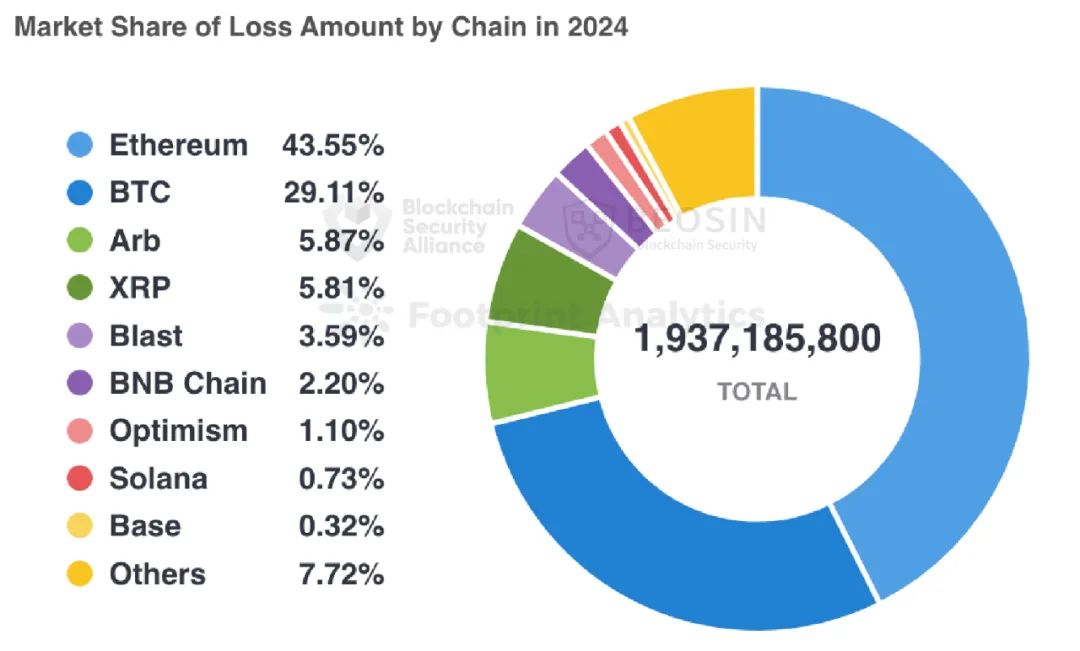
4. Losses Across Blockchains
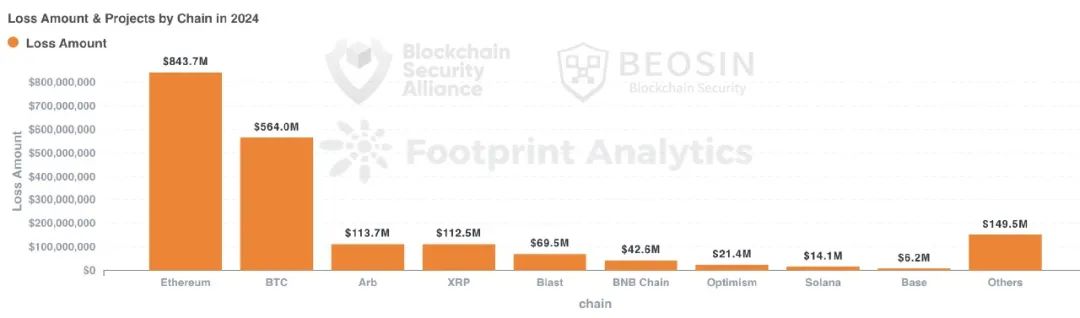
Compared to 2023, a broader variety of public chains experienced attacks in 2024. The top five chains by loss amount were Ethereum, Bitcoin, Arbitrum, Ripple, and Blast:
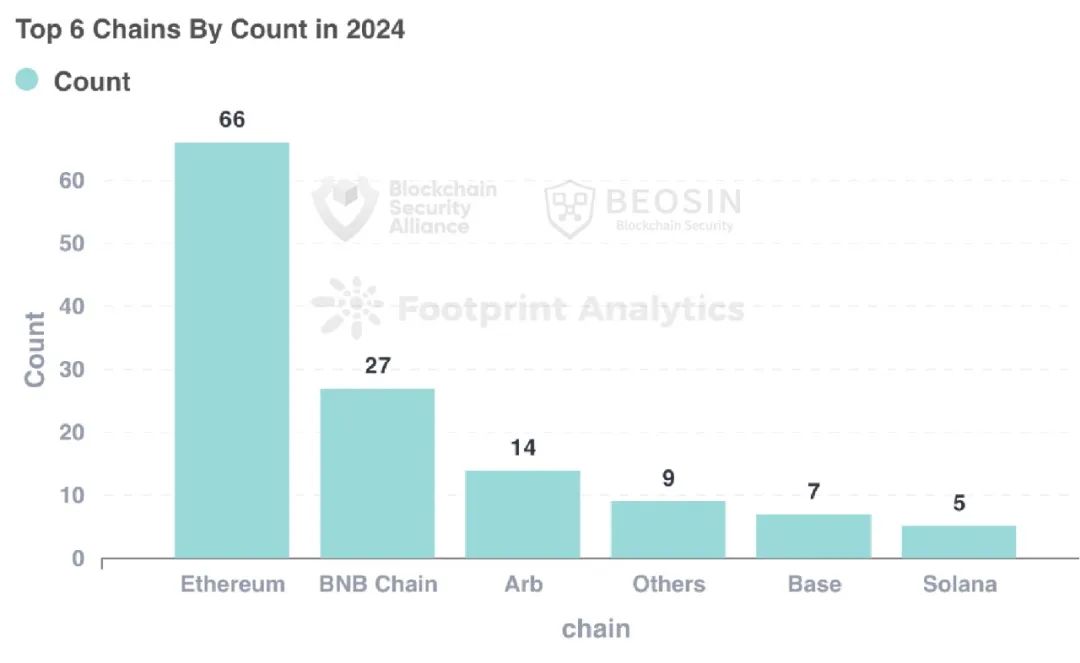
The top six chains by number of attack incidents were Ethereum, BNB Chain, Arbitrum, Others, Base, and Solana:
Similar to 2023, Ethereum remained the chain with the highest financial loss. Sixty-six attack events on Ethereum caused approximately $844 million in losses, accounting for 33.59% of annual total losses.
 Note: This total loss data does not include on-chain phishing losses or partial CEX hot wallet losses
Note: This total loss data does not include on-chain phishing losses or partial CEX hot wallet losses
Bitcoin network ranked second in losses, with a single incident causing $238 million in losses. Third place went to Arbitrum, with total losses of about $114 million.
5. Analysis of Attack Methods
Attack methods in 2024 were highly diverse, extending beyond common contract vulnerabilities to include: supply chain attacks, third-party service provider attacks, man-in-the-middle attacks, DNS attacks, front-end attacks, etc.
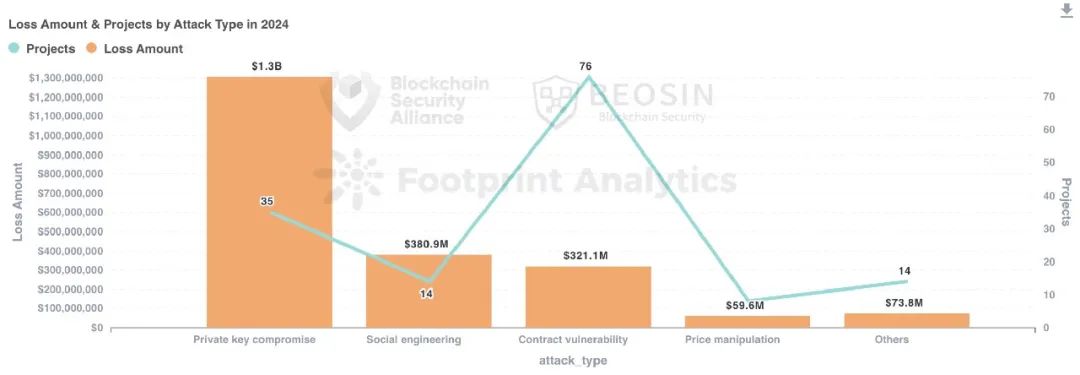
In 2024, 35 private key leak incidents caused $1.306 billion in losses, accounting for 51.96% of total losses, making it the most financially damaging attack method. Major private key leak incidents included: DMM Bitcoin ($304 million), PlayDapp ($290 million), Ripple co-founder Chris Larsen ($112 million), BTCTurk ($55 million), Radiant Capital ($53 million), BingX ($44.7 million), DEXX ($21 million).
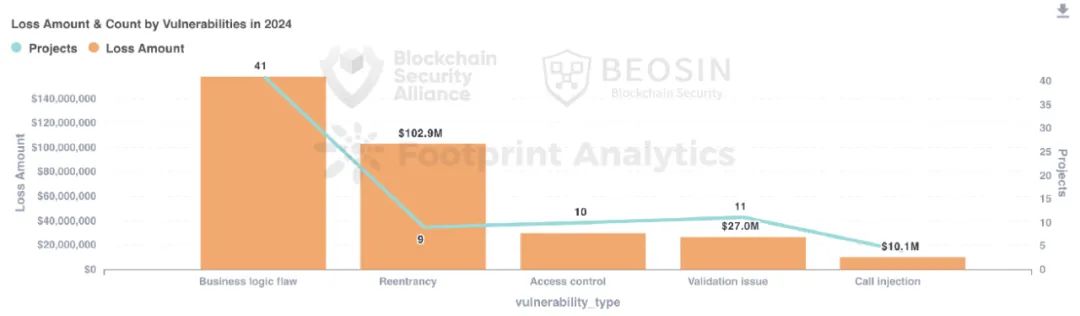
Contract vulnerability exploitation was the most frequent attack method, with 76 out of 131 attack incidents (58.02%) originating from contract vulnerabilities. Total losses from contract vulnerabilities were approximately $321 million, ranking third in financial impact.
Breaking down contract vulnerabilities further, business logic flaws were the most frequent and costly, accounting for about 53.95% of losses from contract vulnerabilities, totaling approximately $158 million.
6. Case Studies on Anti-Money Laundering Incidents
6.1 Polter Finance Security Incident
Incident Summary
On November 17, 2024, Beosin Alert monitoring detected an attack on the FTM-chain lending protocol Polter Finance, where attackers manipulated token prices within the project's contract using flash loans for profit.
Vulnerability and Fund Analysis
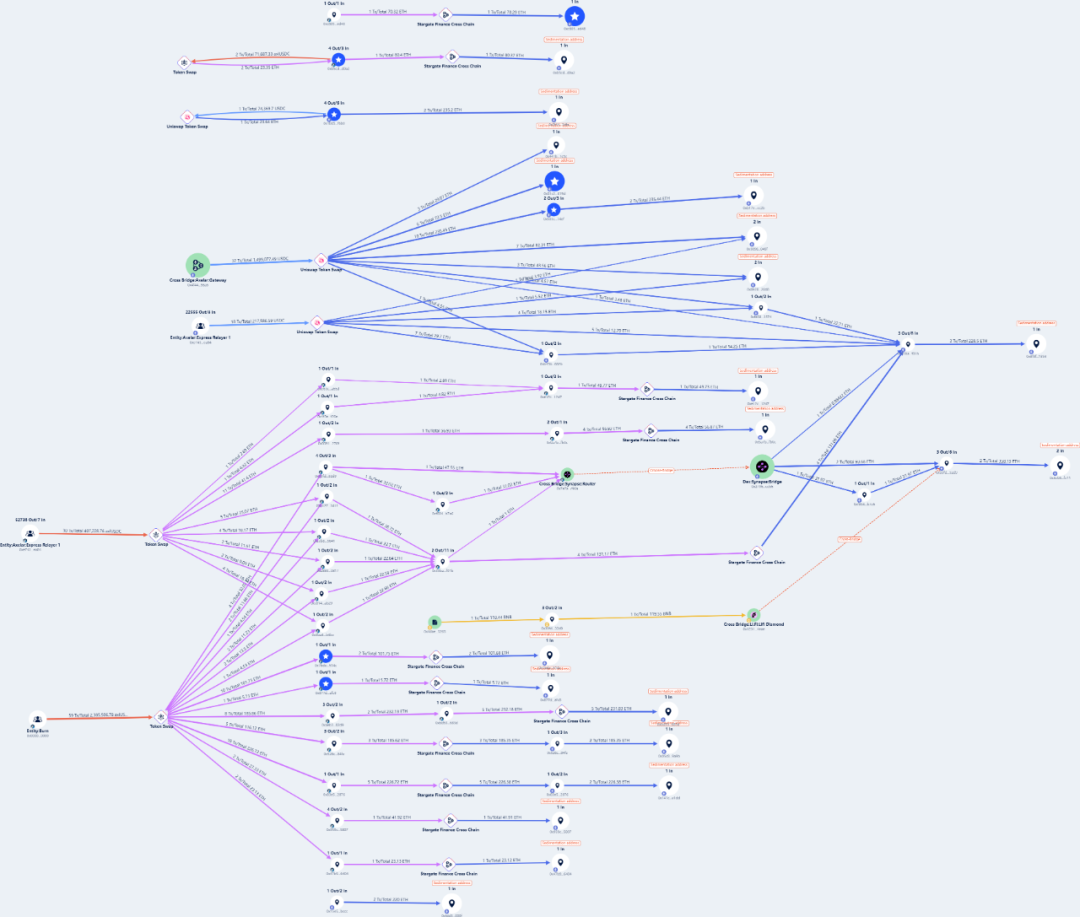
The attacked LendingPool contract (0xd47ae558623638f676c1e38dad71b53054f54273) used 0x6808b5ce79d44e89883c5393b487c4296abb69fe as oracle, which relied on a recently deployed price feed contract (0x80663edff11e99e8e0b34cb9c3e1ff32e82a80fe). This price feed contract calculated prices using token reserves from uniswapV2_pair (0xEc71), which could be exploited via flash loans, thus exposing a price manipulation vulnerability.
Attackers used flash loans to artificially inflate the value of $BOO tokens, borrowing other crypto assets. Subsequently, stolen funds were converted into FTM tokens, bridged to the ETH chain, and stored entirely on Ethereum. Below is a diagram showing fund flows on ARB and ETH chains:
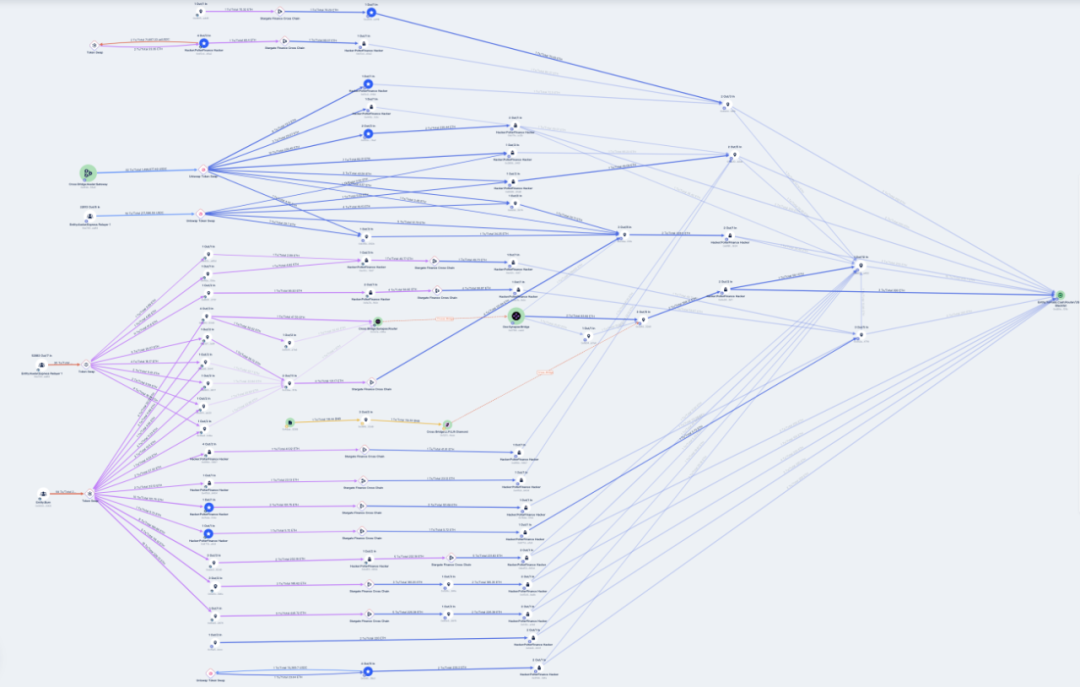
On November 20, attackers continuously transferred over 2,625 ETH to Tornado Cash, as shown below:
6.2 BitForex Security Incident
Incident Summary
On February 23, 2024, renowned on-chain investigator ZachXBT disclosed via his analytical tools that BitForex’s hot wallet experienced outflows of approximately $56.5 million, during which the platform suspended withdrawals.
Fund Analysis
Beosin security team conducted deep tracking and analysis of the BitForex incident via Trace:
Ethereum
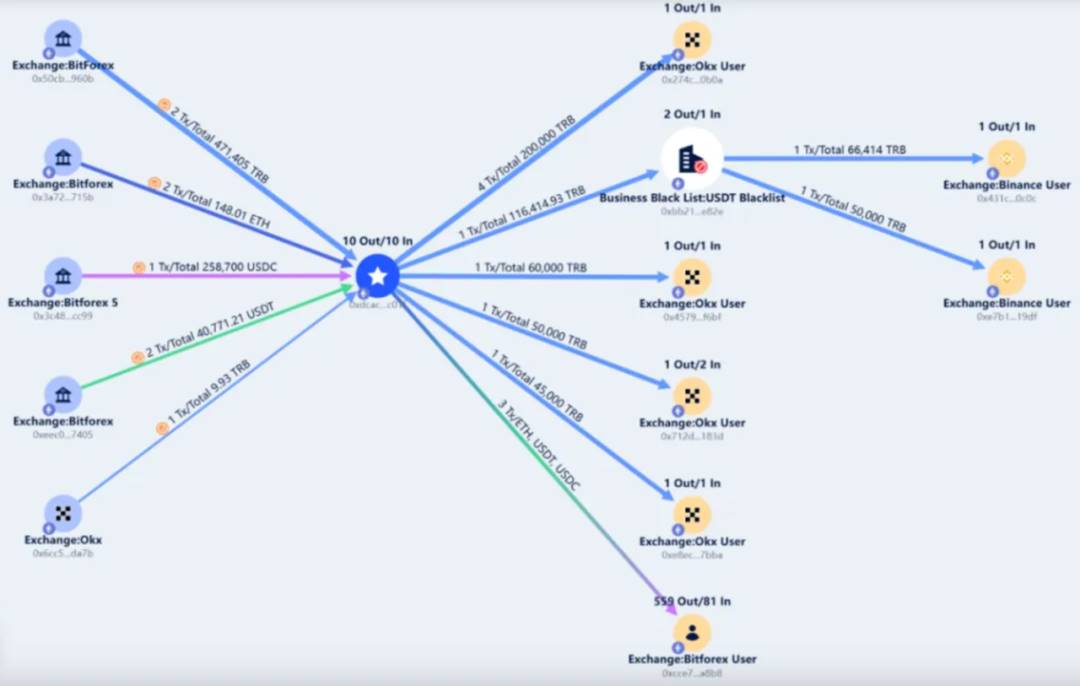
Starting at 6:11 AM (UTC+8) on February 24, 2024, BitForex began transferring 40,771 USDT, 258,700 USDC, 148.01 ETH, and 471,405 TRB into an Ethereum escape address (0xdcacd7eb6692b816b6957f8898c1c4b63d1fc01f).
Then on August 9 (Beijing time), the escape address returned all tokens except TRB—including 147.9 ETH, 40,771 USDT, and 258,700 USDC—back to BitForex’s exchange account (0xcce7300829f49b8f2e4aee6123b12da64662a8b8).
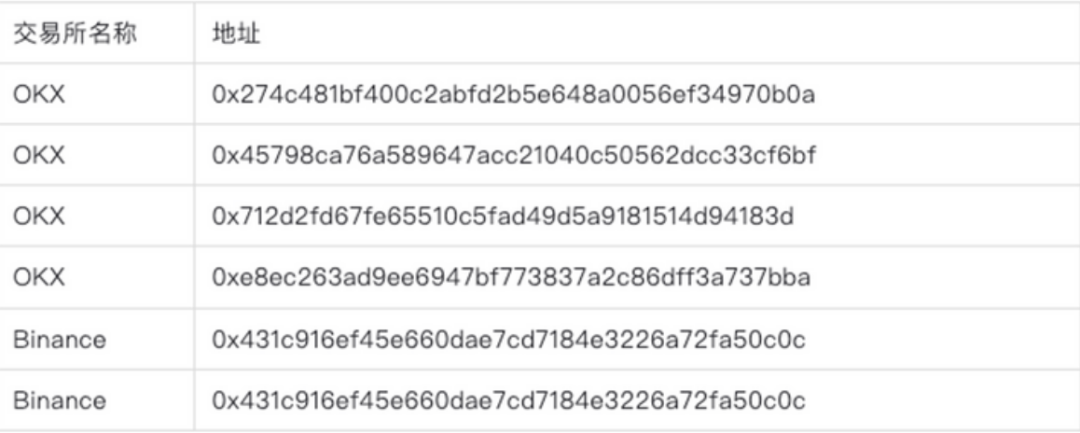
From November 9 to 10 (Beijing time), the escape address transferred 355,000 TRB via seven transactions into four different OKX exchange user addresses:
0x274c481bf400c2abfd2b5e648a0056ef34970b0a
0x45798ca76a589647acc21040c50562dcc33cf6bf
0x712d2fd67fe65510c5fad49d5a9181514d94183d
0xe8ec263ad9ee6947bf773837a2c86dff3a737bba
The escape address then transferred the remaining 116,414.93 TRB to an intermediary address (0xbb217bd37c6bf76c6d9a50fefc21caa8e2f2e82e), which split the entire TRB balance into two transactions sent to two different Binance users:
0x431c916ef45e660dae7cd7184e3226a72fa50c0c
0xe7b1fb77baaa3bba9326af2af3cd5857256519df
BNB Chain
On February 24, BitForex withdrew 166 ETH, 46,905 USDT, and 57,810 USDC to a BNB Chain address (0xdcacd7eb6692b816b6957f8898c1c4b63d1fc01f), where they remain.

Polygon
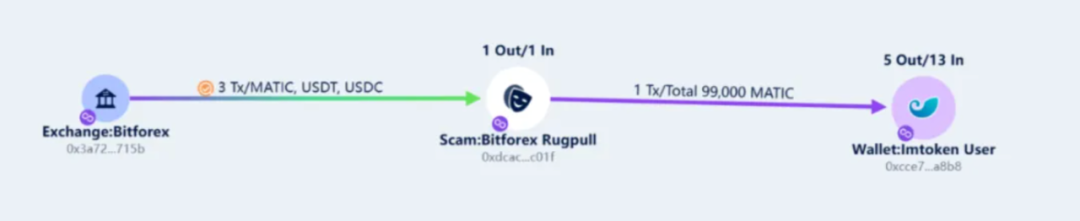
On February 24 (Beijing time), BitForex withdrew 99,000 MATIC, 20,300 USDT, and 1,700 USDC to a Polygon chain address: 0xdcacd7eb6692b816b6957f8898c1c4b63d1fc01f.
Of this, 99,000 MATIC was transferred on August 9 to address 0xcce7300829f49b8f2e4aee6123b12da64662a8b8 and has since remained idle, while the USDT and USDC tokens remain in the original address.
TRON
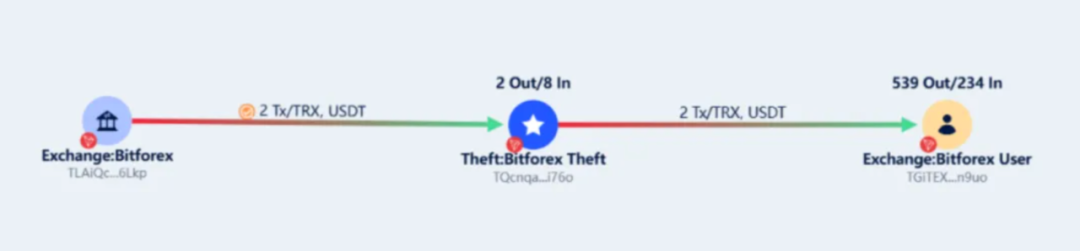
On February 24, BitForex withdrew 44,000 TRX and 657,698 USDT to TRON chain address TQcnqaU4NDTR86eA4FZneeKfJMiQi7i76o. On August 9, all aforementioned tokens were transferred back to BitForex user address: TGiTEXjqx1C2Y2ywp7gTR8aYGv8rztn9uo.
Bitcoin
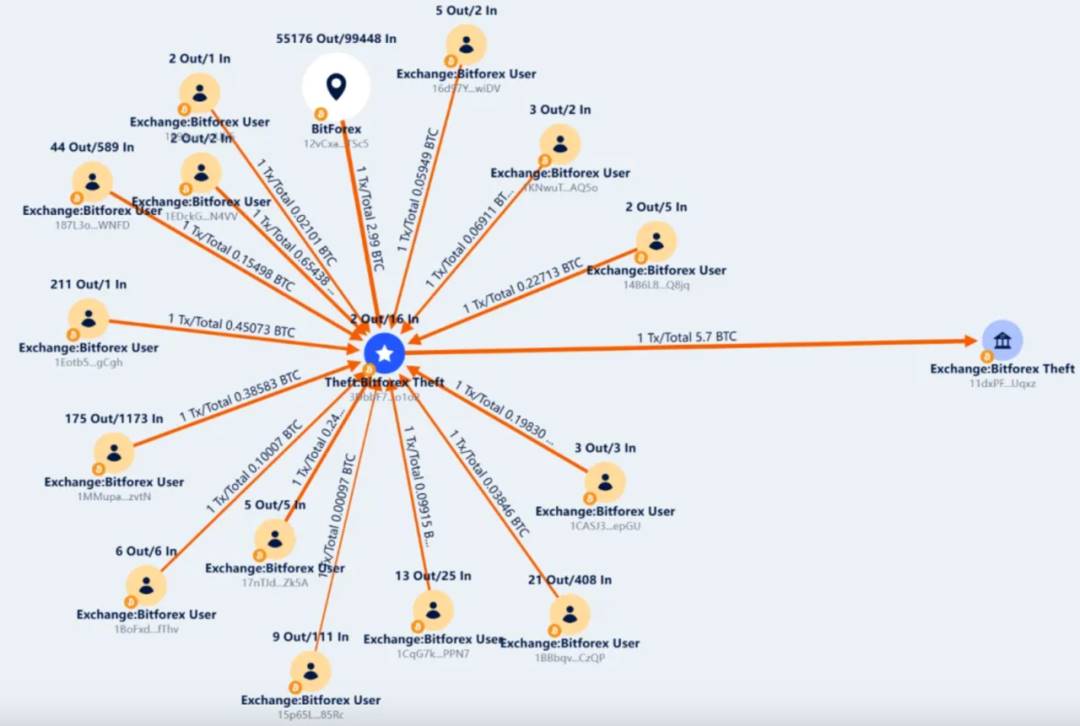
Starting February 24, 16 BitForex addresses collectively transferred 5.7 BTC to BTC chain address 3DbbF7yxCR7ni94ANrRkfV12rJoxrmo1o2. On August 9, this address returned all 5.7 BTC to BitForex’s exchange address: 11dxPFQ8K9pJefffHE4HUwb2aprzLUqxz.
In summary, on February 24, BitForex transferred 40,771 USDT, 258,700 USDC, 148.01 ETH, and 471,405 TRB to Ethereum; 44,000 TRX and 657,698 USDT to TRON; 5.7 BTC to Bitcoin; 166 ETH, 46,905 USDT, and 57,810 USDC to BNB Chain; and 99,000 MATIC, 20,300 USDT, and 1,700 USDC to Polygon. On August 9, all tokens on BTC, TRON, and all except TRB on Ethereum were returned to BitForex accounts. From November 9–10, all 471,405 TRB were transferred to four OKX and two Binance accounts. All tokens on Ethereum, TRON, and BTC have now been moved, while 166 ETH, 46,905 USDT, and 57,810 USDC remain on BSC, and 99,000 MATIC, 20,300 USDT, and 1,700 USDC remain on POL.
Exchange deposit addresses for TRB:
7. Fund Flow Analysis of Stolen Assets
Throughout 2024, approximately $1.312 billion in stolen funds remained in hacker addresses (including cases involving cross-chain transfers and dispersion across multiple addresses), accounting for 52.20% of total stolen funds. Compared to last year, hackers increasingly prefer conducting money laundering through multiple cross-chain movements and dispersing stolen funds across many addresses rather than directly using mixers. Increased addresses and complex laundering paths undoubtedly increase investigation difficulty for project teams and regulators.
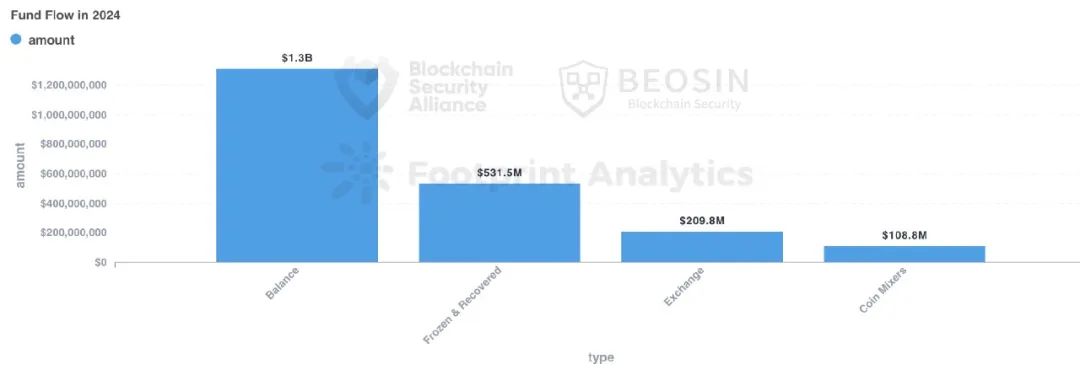
Approximately $531 million in stolen funds were recovered, accounting for about 21.13%. In 2023, recovered funds totaled approximately $295 million.
About $109 million in stolen funds were sent to mixers, approximately 4.34% of total stolen assets. Since the U.S. OFAC sanctioned Tornado Cash in August 2022, the amount of stolen funds flowing into Tornado Cash has significantly decreased.
8. Project Audit Status Analysis
Among 131 attack incidents, 42 involved projects that had not undergone audits, 78 involved audited projects, and audit status could not be confirmed for 11 projects.
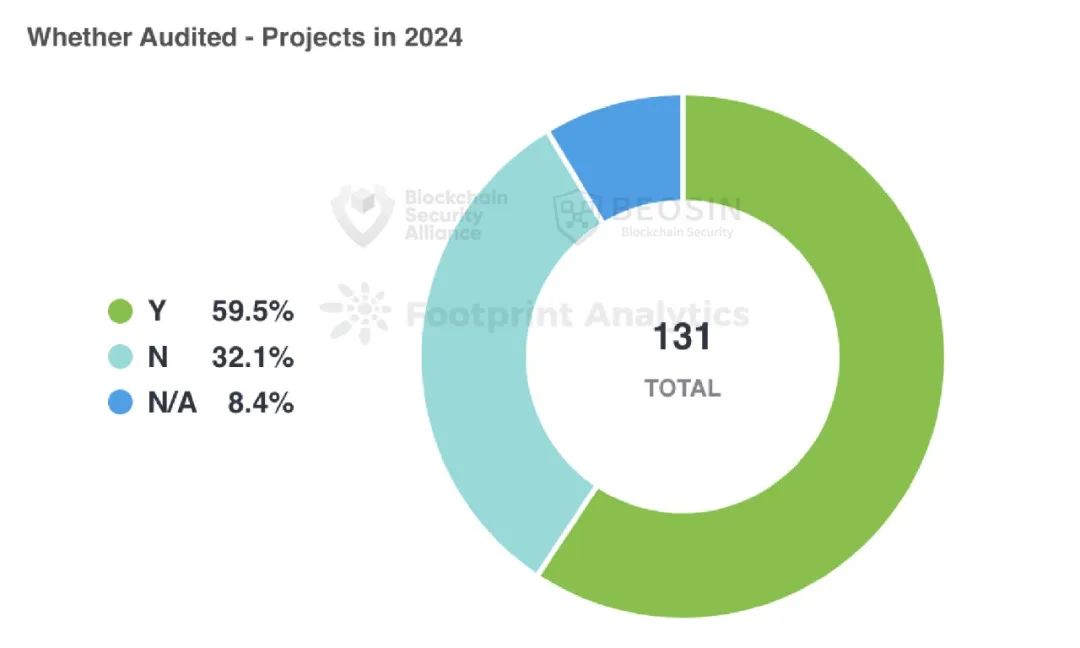
Among the 42 unaudited projects, 30 incidents (about 71.43%) stemmed from contract vulnerabilities. This indicates that unaudited projects are more likely to harbor potential security risks. In contrast, among the 78 audited projects, 49 incidents (about 62.82%) involved contract vulnerabilities, showing that audits can improve project security to some extent.
However, due to the lack of standardized norms in the Web3 market, audit quality varies widely, falling short of expectations. To effectively safeguard assets, it is recommended that projects seek professional security firms for audits before launch.
9. Rug Pull Analysis
In 2024, Beosin Alert platform monitored a total of 68 major rug pull incidents in the Web3 ecosystem, involving approximately $148 million, a significant decrease from $388 million in 2023.
In terms of amounts, among the 68 rug pull incidents, nine projects exceeded $1 million in losses: Essence Finance ($20 million), Shido Global ($2.4 million), ETHTrustFund ($2.2 million), Nexera ($1.8 million), Grand Base ($1.7 million), SAGA Token ($1.6 million), OrdiZK ($1.4 million), MangoFarmSOL ($1.29 million), and RiskOnBlast ($1.25 million), totaling $33.64 million in losses, accounting for 22.73% of all rug pull losses.
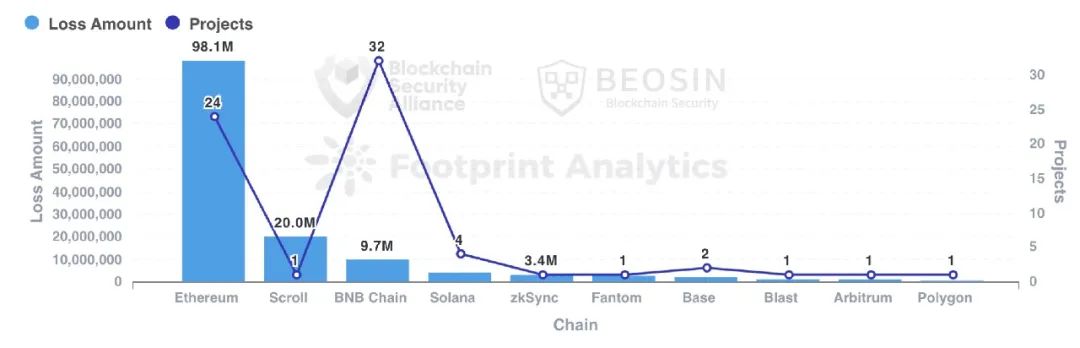
Rug pull projects on Ethereum and BNB Chain accounted for 82.35% of total incidents, with 24 and 32 incidents respectively. One rug pull exceeding $20 million occurred on Scroll. Other chains saw smaller numbers of rug pulls, including Polygon, BASE, and Solana.
10. Summary of the 2024 Web3 Blockchain Security Landscape
In 2024, the number of on-chain hacking incidents and project rug pulls declined noticeably compared to 2023, yet total losses continued to rise, with phishing attacks becoming more rampant. The most damaging attack method remained private key leaks. Key reasons behind this shift include:
Following rampant hacking activities last year, the entire Web3 ecosystem placed greater emphasis on security in 2024. Efforts from both project teams and security companies—including real-time on-chain monitoring, stronger focus on security audits, and learning from past contract exploitation incidents—made it harder for hackers to steal funds via contract vulnerabilities compared to the previous year. However, project teams still need to strengthen awareness regarding private key management and operational security.
As crypto markets integrate with traditional finance, hackers are no longer limited to attacking DeFi, cross-chain bridges, and exchanges but have expanded targets to payment platforms, gambling platforms, crypto brokers, infrastructure, password managers, development tools, MEV bots, and Telegram bots.
From 2024 to 2025, the crypto market is entering a bull phase with active on-chain capital, which will likely attract more hacking attempts. Meanwhile, regulatory policies targeting crypto assets are gradually improving globally to combat crimes involving digital assets. Under these trends, hacking activities are expected to remain high in 2025, posing ongoing serious challenges for global law enforcement and regulatory bodies.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















