
Web3 Security Incidents in August: Total Losses of Approximately $316 Million
TechFlow Selected TechFlow Selected

Web3 Security Incidents in August: Total Losses of Approximately $316 Million
A total of 28 hacking incidents occurred, resulting in losses of approximately $253 million, with $13.58 million recovered. The causes involved smart contract vulnerabilities, compromised accounts, and front-end attacks.
Author: SlowMist Technology
Overview
In August 2024, Web3 security incidents resulted in total losses of approximately $316 million. According to statistics from the SlowMist Hacked Database (https://hacked.slowmist.io), there were 28 hacking incidents that caused losses of about $253 million, with $13.58 million recovered. The causes included smart contract vulnerabilities, account compromises, and front-end attacks. Additionally, according to Scam Sniffer, a Web3 anti-fraud platform, there were 9,145 phishing victims this month, resulting in total losses of $62.93 million.
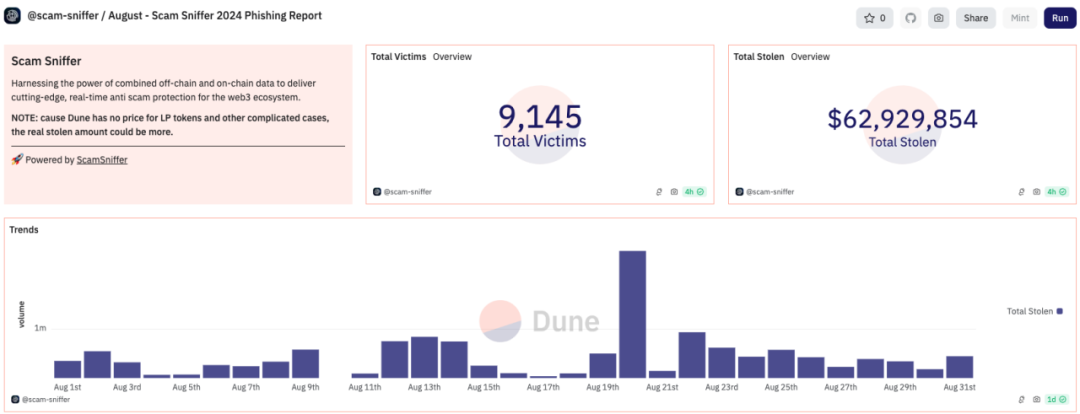
(https://dune.com/scam-sniffer/august-scam-sniffer-2024-phishing-report)
Major Incidents
Convergence Finance
On August 1, 2024, Convergence Finance was attacked. The attacker minted and sold 58 million CVG tokens—worth about $210,000, equivalent to the entire staking reward allocation—and also stole around $2,000 in unclaimed rewards from Convex. According to Convergence Finance’s post-mortem report, the root cause was the lack of input validation in the `claimMultipleStaking` function of the reward distribution contract.
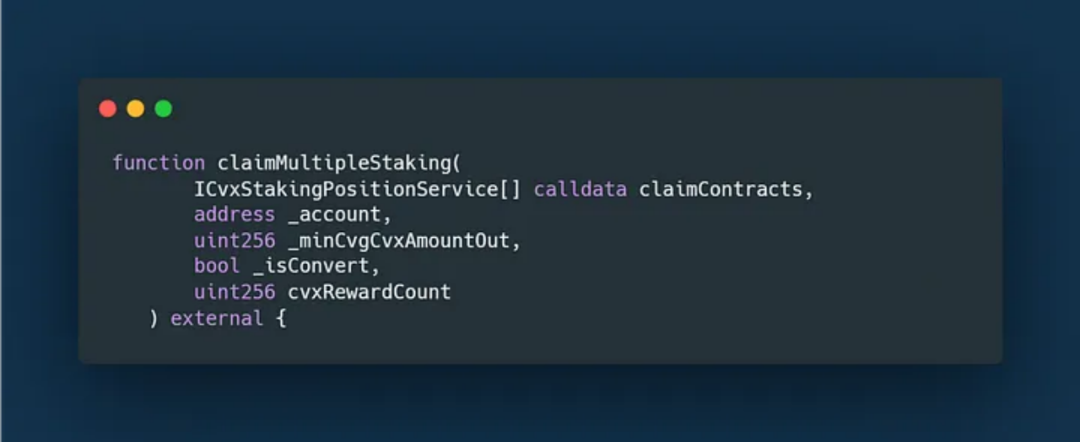
(https://medium.com/@cvg_wireshark/post-mortem-08-01-2024-e80a49d108a0)
Ronin
On August 6, 2024, the gaming blockchain Ronin suffered an attack, during which abnormal withdrawals of cross-chain assets occurred on the Ronin Bridge. According to analysis by the SlowMist security team, the attack happened because weights were modified to unexpected values, allowing funds to be withdrawn without any multi-signature threshold checks. The attacker withdrew approximately 4,000 ETH and 2 million USDC from the bridge, valued at around $12 million. By August 7, white-hat hackers had returned assets worth $12 million and received a $500,000 bug bounty.
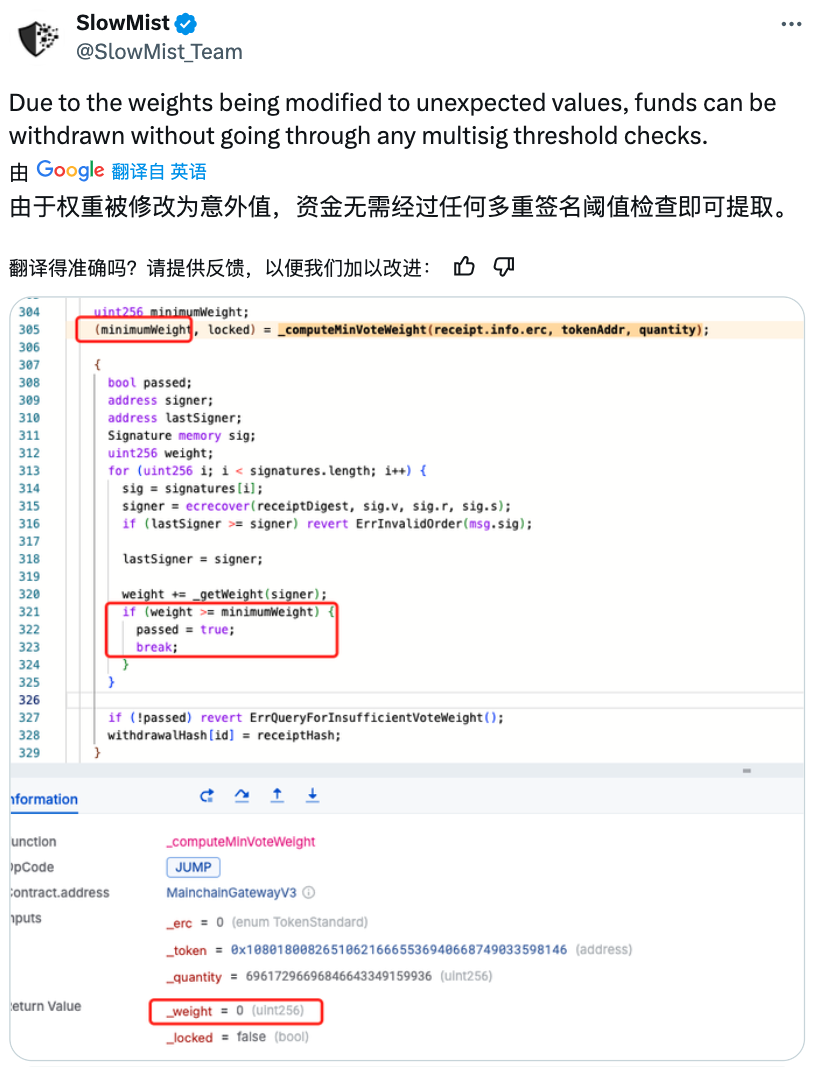
(https://x.com/slowmist_team/status/1820783952145355247?s=46&t=DLwbX9Nw4QECiyZQ0av-fg)
Nexera
On August 7, 2024, an external attacker obtained credentials to manage the Nexera Fundrs platform's smart contract. Using these credentials, the attacker transferred NXRA tokens from the Fundrs staking contract on Ethereum, causing losses of approximately $1.83 million. Of the 47.24 million NXRA tokens stolen, the attacker only sold 14.75 million (worth about $449,000). Nexera successfully removed the remaining balance of 32.5 million NXRA tokens from the attacker’s wallet, preventing further losses.
Vow
On August 13, 2024, Vow was hacked due to a contract vulnerability, resulting in losses of approximately $1.2 million. According to VOW, the team was testing the USD exchange rate setting feature of the v$ contract to prepare for new lending pools and oracle functionality. The attacker exploited a brief time window and exchange rate fluctuation by purchasing and sending large amounts of VOW tokens to the contract, generating nearly 2 billion v$ tokens, which were then sold back into the Uniswap pool for profit.
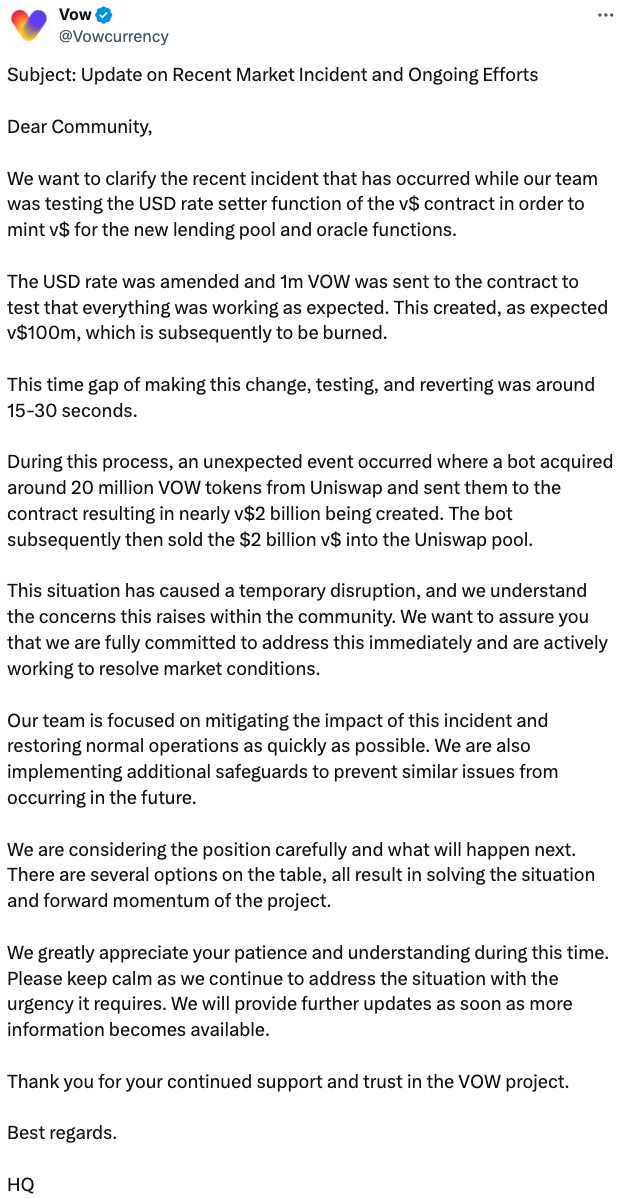
(https://x.com/Vowcurrency/status/1823407231658025300)
User
On August 19, 2024, according to on-chain investigator ZachXBT, a suspicious transfer involving 4,064 BTC (worth approximately $238 million) may have originated from a potential victim. The funds were quickly transferred to ThorChain, eXch, Kucoin, ChangeNow, Railgun, and Avalanche Bridge. As of August 27, $205,000 had been recovered.
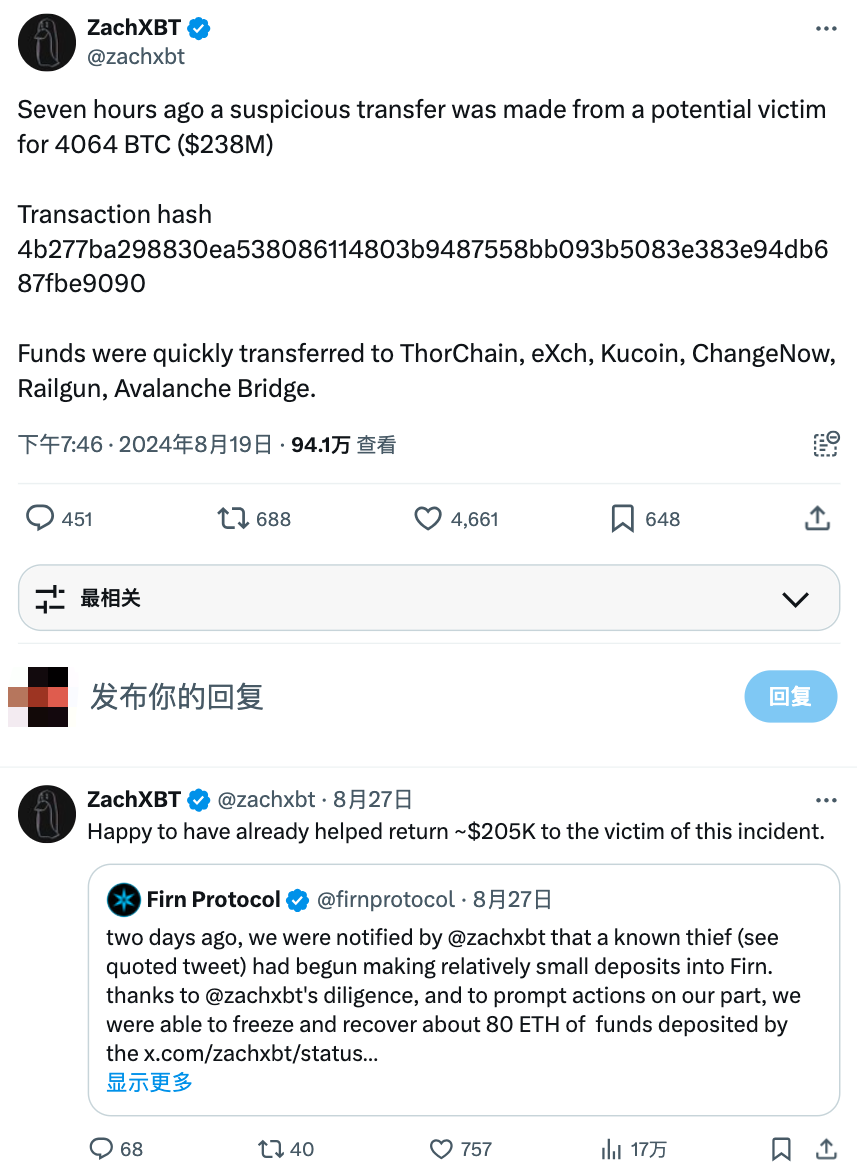
(https://x.com/zachxbt/status/1825499490956231021)
User
On August 21, 2024, according to monitoring by Scam Sniffer, a victim lost DAI worth $55.43 million after signing a phishing transaction targeting their DeFi Saver Proxy. According to MistTrack analysis, the funds were sent to multiple addresses and most were subsequently converted into ETH.
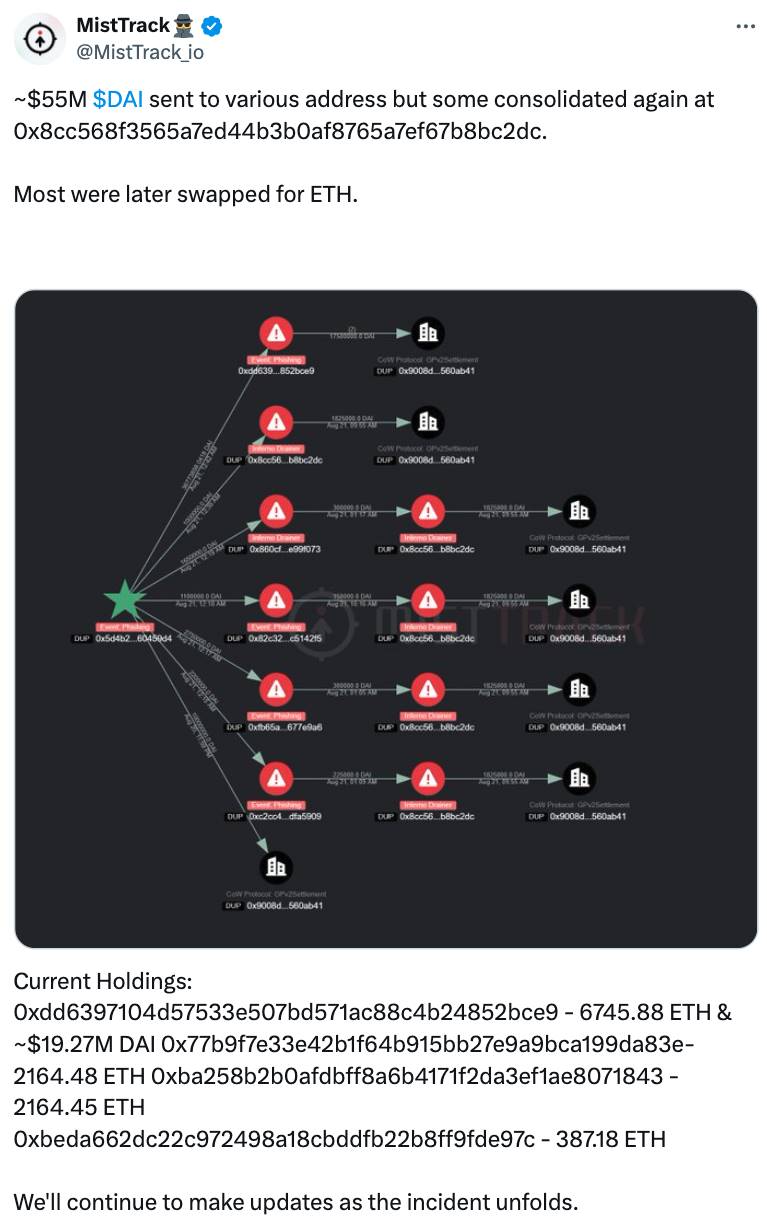
(https://x.com/MistTrack_io/status/1826273448626356697)
Aave
On August 28, 2024, a peripheral contract of the DeFi lending platform Aave was exploited via an arbitrary call vulnerability, resulting in losses of approximately $56,000. The affected contract, ParaSwapRepayAdapter, is not part of Aave’s core protocol. It allows users to repay loans using existing collateral through asset swaps on the decentralized exchange ParaSwap. Although the contract was not designed to hold user funds, small residual token balances accumulated over time due to positive slippage in transactions. Aave representatives emphasized that this incident did not threaten user funds or compromise the security of the core Aave protocol.
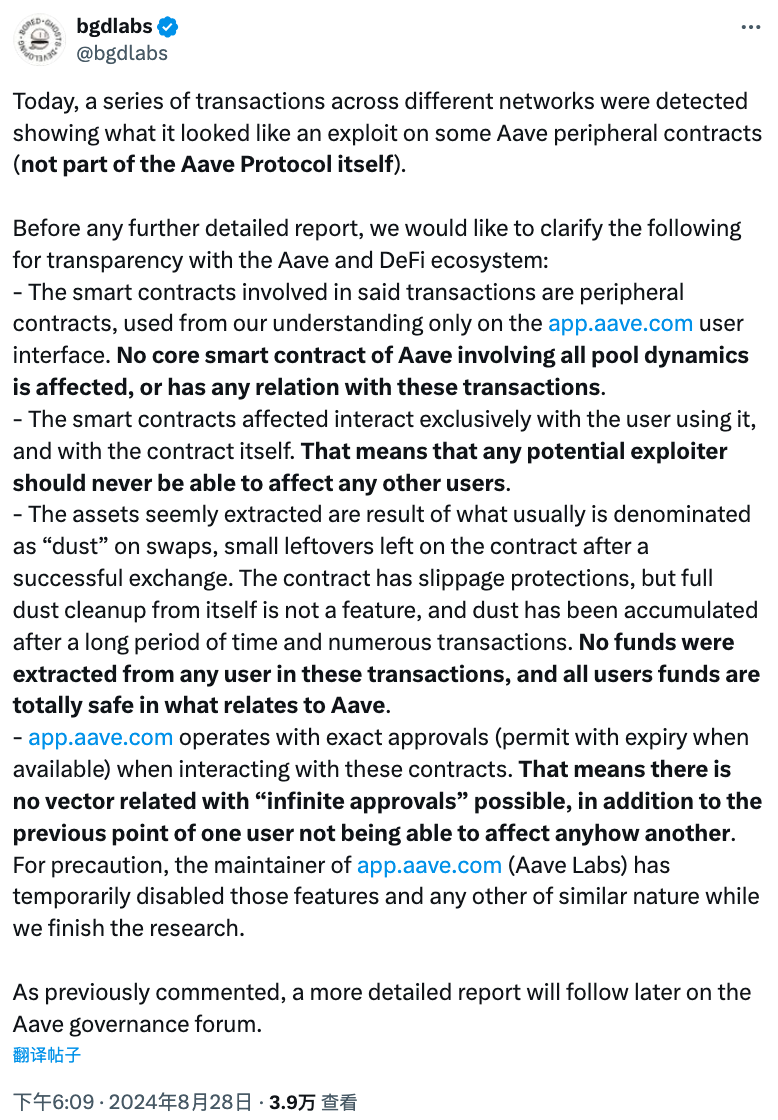
(https://x.com/bgdlabs/status/1828736554262470792)
Summary
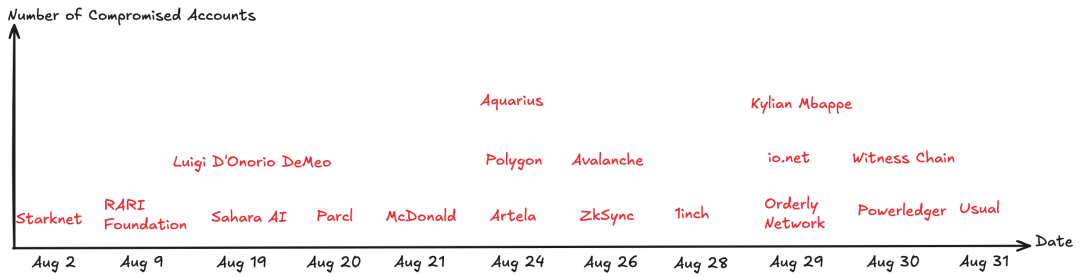
This month, account security emerged as a major risk area, with account breaches accounting for 64.3% of all hacking incidents. Notably, attackers targeted not only well-known blockchain projects and individuals but also celebrities and established brands from traditional industries, such as football star Kylian Mbappe and McDonald's. After compromising high-profile accounts, hackers often posted messages containing phishing links or promoted specific tokens. The SlowMist security team urges users to remain vigilant against phishing attacks, verify information from multiple sources, and exercise caution when investing. Most of the account breaches this month occurred on Discord. Previously, we explained the Discord token mechanism in our article SlowMist: Exposing How Malicious Browser Bookmarks Steal Your Discord Token; click the link to read more.
Finally, the incidents covered in this article represent the major security events of the month. For more blockchain security incidents, visit the SlowMist Hacked Database (https://hacked.slowmist.io/); clicking "Read Original" will take you directly there.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















