
Nillion: Leading a New Era of Secure Computing, Unlocking AI's Full Potential While Preserving Privacy
TechFlow Selected TechFlow Selected

Nillion: Leading a New Era of Secure Computing, Unlocking AI's Full Potential While Preserving Privacy
Nillion, a key enabler in the field of secure computing, is unlocking the potential of AI across industries.
Author: 3rd Street Capital
Translation: TechFlow
The Growing Importance of Secure Computation
In today’s increasingly digital world, the risks of data breaches and misuse of personal information have significantly increased. These threats not only harm businesses but also expose individuals to substantial risks. For example, in the Cambridge Analytica scandal, Facebook allowed a political consulting firm to obtain personal data from millions of users without their consent, influencing major political events. This incident revealed the dangers of centralized data control and highlighted the vulnerability of personal information in the current digital environment.
Beyond data misuse, large-scale data breaches further expose the inadequacies of existing data protection methods. Below are some notable recent incidents:
-
Ledger (2020): Personal information of 270,000 customers exposed
-
LinkedIn (2021): Data of 700 million users leaked
-
LastPass (2022): Hackers breached encrypted password vaults
-
Microsoft (2023): Data from 65,000 companies exposed
An increasing number of data breaches and misuse cases underscore the urgent need for stronger security measures. As artificial intelligence (AI) becomes more integrated into our daily lives, a critical question arises: How can we trust AI to protect our most sensitive information?
Secure computation technologies have the potential to revolutionize AI by enabling highly personalized and secure services while preserving privacy.
Unlocking AI's Potential Through Secure Computation
Even advanced AI tools like ChatGPT remind users not to share sensitive or personal information, highlighting the risks in data processing. Recent lawsuits against ChatGPT and Microsoft’s Copilot have amplified this warning, accusing them of using customer data without consent to train AI models. These cases raise serious concerns about data privacy and trust:
-
OpenAI and Microsoft sued for $3 billion over alleged ChatGPT "privacy violations"
-
OpenAI faces lawsuit over allegedly unauthorized use of data to train ChatGPT
Unfortunately, data privacy and security issues hinder AI’s immense potential. However, imagine a future where machine learning AI can securely process sensitive data through advanced encryption, ensuring information is never leaked or exposed. This would bring revolutionary changes across industries and improve people’s lives.
This is exactly where secure computation comes into play. It is the key to unlocking AI’s full potential—enabling AI to deliver personalized and customized services while ensuring data privacy and security remain uncompromised.
What Is Secure Computation?
To understand how Nillion drives this innovation, it’s essential first to grasp the concept of secure computation and how it works. Secure computation enables AI to perform machine learning operations on encrypted data, meaning even sensitive information can be processed without being exposed. For instance, tools like ChatGPT could process encrypted data just as they do regular text. The entire computation occurs within a secure environment, and the output remains encrypted until decrypted by the key holder—ensuring your data stays private throughout the process.
With secure computation, AI can provide powerful and personalized services without sacrificing data privacy and security, making it a pivotal technology for the future of machine learning.
How Does Secure Computation Work?
Imagine a group of friends, each possessing a secret ingredient from a special recipe, but none willing to reveal their ingredient to the others. They all want to know what the final dish would taste like if all ingredients were combined.
Here’s how they do it:
-
Secret Ingredients in Locked Boxes: Each friend places their secret ingredient into a locked box, with only they holding the key, so no one else can see inside.
-
Magic Chef (Secure Computation): They hand all the locked boxes to a magic chef who can cook using these ingredients without opening the boxes. The chef has special tools to mix, bake, or sauté the ingredients inside the boxes without unlocking or viewing the contents.
-
Final Dish in a Sealed Container: After cooking, the magic chef places the final dish into a sealed container that only the friends can open together.
-
Shared Enjoyment: When they open the container, they can taste the delicious result of combining all secret ingredients. They enjoy the meal and understand how their contributions synergized, but no one learns any individual’s secret ingredient.
This story vividly illustrates secure computation:
-
Locked Boxes (Data Encryption): Secret ingredients represent encrypted data—protected and inaccessible to others.
-
Magic Chef (Secure Computation Algorithms): The magic chef symbolizes algorithms capable of computing on encrypted data without decryption.
-
Final Dish (Computation Result): The final dish in the sealed container represents the encrypted computation result, accessible only to authorized parties upon decryption.
-
Privacy Preserved Throughout: At every stage, each friend’s secret ingredient remains confidential, yet all benefit from the combined outcome.
In simple terms:
Secure computation allows computers to perform calculations on encrypted data, meaning the data appears as meaningless characters to the system. Computers can process and combine this encrypted data to generate useful results without knowing the actual content. Only those with the correct “key” can unlock and interpret the final result, thus ensuring everyone’s privacy is protected.
Is Secure Computation the Same as Zero-Knowledge Proofs (ZK)?
When discussing secure computation, a common question is whether it’s similar to zero-knowledge proofs (ZK). While both ZK and secure multi-party computation (sMPC) enhance privacy, they serve different purposes.
Zero-knowledge proofs allow one party to prove the truth of a statement to another without revealing any additional information. For example, you can prove you have sufficient account balance without disclosing the exact amount. In contrast, secure computation enables multiple participants to jointly compute a function over their combined data without revealing their individual inputs.
In short, ZK focuses on securely proving facts, whereas MPC—like the magic chef example—focuses on secure collaborative computation without exposing individual inputs. Although both ZK and MPC are powerful privacy-preserving tools, their applications differ: ZK emphasizes securely verifying facts, while MPC enables secure collaborative data processing.
The Mathematics Behind MPC
In the magic chef analogy, we saw how multiple participants can contribute data without revealing it, yet still produce meaningful results. This is precisely how multi-party computation (MPC) works: it uses clever mathematical techniques to securely process hidden data.
If you're interested in the mathematics behind MPC, watch the video series "MPC Explained", which intuitively explains these concepts in an accessible way—even for those without a cryptography background.
Transforming Industries Through Secure Computation
The principles of secure computation go beyond theory—they hold transformative potential across various industries. Below are real-world examples of how secure computation could revolutionize healthcare, finance, and personal data management:
Healthcare Applications:
Hospitals can securely share encrypted genetic data from millions of patients worldwide using secure computation. AI can then analyze this data to identify new genetic markers for diseases like Alzheimer’s and develop predictive models. This would significantly improve early detection and prevention, while ensuring complete confidentiality of patient data.
Financial Services Applications:
Financial institutions can collaborate with regulators using secure computation to analyze encrypted transaction data, enhancing fraud detection and compliance monitoring. For example, banks can securely share encrypted large-scale transaction patterns with an AI-driven central regulatory platform. The platform can analyze aggregated encrypted data from multiple banks to identify systemic risks, detect fraudulent activities such as money laundering, and monitor regulatory compliance.
By using secure computation, banks can collectively strengthen the financial system’s resilience against fraud and systemic risks, while protecting customer privacy and commercial secrets.
Personal Use Case 1 (Health & Wellness):
Individuals can securely share their encrypted genetic data with AI-powered platforms to receive highly personalized health plans. These may include nutrition and fitness regimens tailored to predict and prevent chronic diseases—even before symptoms appear—while ensuring complete confidentiality of sensitive health data.
Personal Use Case 2 (Tax Audits):
Individuals and businesses can securely share their encrypted financial data with AI-powered audit platforms. These platforms use secure computation to conduct comprehensive tax audits without exposing sensitive financial information.
For example, taxpayers can upload encrypted financial records to the platform, which analyzes the data for tax law compliance, identifies discrepancies, and provides optimization suggestions for tax filings. The platform generates detailed reports and recommendations while ensuring the actual financial data remains private and invisible to auditors or third parties. This reduces the need for manual audits, saves time and cost, improves accuracy, and ensures privacy.
These examples demonstrate how secure computation unlocks AI’s potential, delivering powerful solutions across industries while maintaining the highest standards of privacy and security.
Real-World Applications of Privacy-Enhancing Technologies
Secure computation may sound futuristic, but some of the world’s largest organizations already use privacy-enhancing technologies (PETs) in practice. For example, JP Morgan uses multi-party computation (MPC) in its dark pool trading system, allowing parties to conduct private trades without revealing sensitive information like inventory positions. Similarly, Meta uses MPC in its ad technology for private performance measurement, enabling advertisers to evaluate campaign effectiveness without accessing users’ private data.
These examples highlight how the principles behind secure computation are already successfully applied to solve real-world privacy challenges, demonstrating the feasibility and impact of PETs in modern industries.

Nillion: Ushering in a New Era of Secure Computation
Introducing Nillion: A New Era of Secure Computation
Nillion, as a key enabler in the field of secure computation, is unlocking AI’s potential across industries. While Nillion is not the only secure computation solution, it stands out with its decentralized network powered by Petnet. This network leverages secure multi-party computation (sMPC) for private data processing and combines it with Nil Message Compute (nMC) for high efficiency and scalability.
Core Components of Nillion’s Architecture
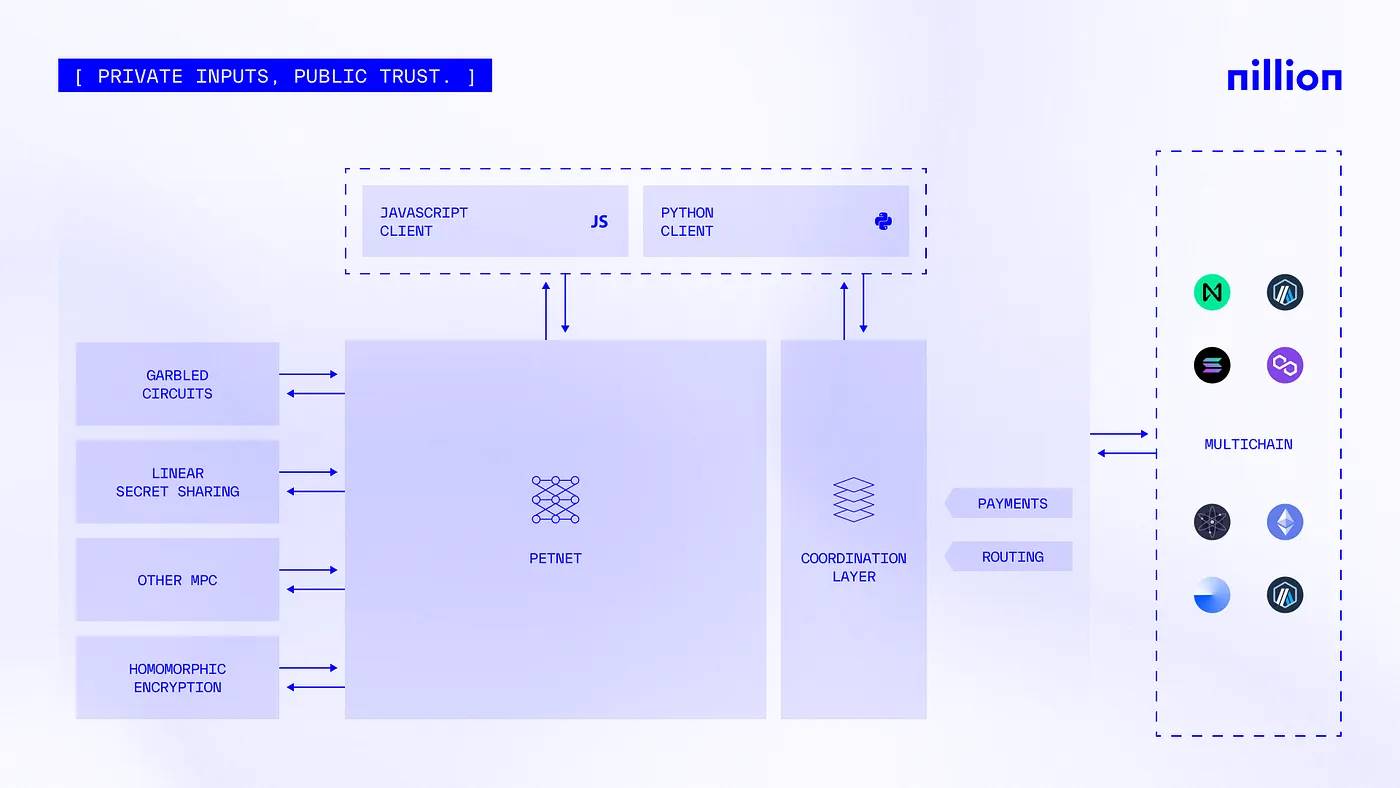
Overview of Nillion’s Architecture
Petnet — The Privacy-Enhancing Technology Network
At the heart of Nillion’s infrastructure lies Petnet, a decentralized network that securely connects nodes in the system. Petnet enables distributed data processing, using sMPC to allow multiple parties to jointly compute without exposing private data. nMC further optimizes this process by reducing communication between nodes, improving efficiency and scalability.
Petnet also employs data sharding, breaking high-value data (HVD)—such as personal identities, medical records, proprietary algorithms, and financial transactions—into smaller encrypted fragments distributed across different nodes. This ensures no single node can access the complete dataset, greatly enhancing both security and performance.
Dual-Network System — Coordination Layer and Orchestration Layer
Built atop Petnet are the coordination layer and orchestration layer:
-
Coordination Layer (NilChain): Responsible for task allocation across the network, ensuring each node knows its role in computations and coordinating storage operations and payments for blind computation. This layer aligns economic incentives with efficient network resource management.
-
Orchestration Layer: Coordinates and integrates multiple privacy-enhancing technologies (PETs) to enable complex, secure computations. It acts as a “conductor,” managing and harmonizing different cryptographic techniques.
NilVM — The Nillion Virtual Machine
NilVM is the execution environment for blind computation programs written in Nillion’s programming language, Nada. It ensures these programs run efficiently and securely within the Nillion network and optimizes the application of various PETs via the orchestration layer.
The NIL Token
The NIL token is the native utility token of the Nillion network. Its uses include:
-
Security and Coordination: By staking NIL tokens, users gain voting rights to secure the network through a delegated proof-of-stake mechanism and help select active validators.
-
Network Resource Management: Users pay in NIL tokens to access the coordination layer or initiate blind computation requests, effectively managing network resources.
-
Petnet Cluster Economy: Infrastructure providers join clusters to support blind computation and earn NIL token rewards for contributing network resources.
-
Network Governance: NIL holders can stake tokens to vote on on-chain proposals or delegate their voting power to others.
A New Era for AI: Nillion’s Transformation in Secure Data Processing
Nillion is leading a revolution in data security by integrating advanced privacy-enhancing technologies (PETs) like secure multi-party computation (sMPC) and fully homomorphic encryption (FHE) through its innovative orchestration layer. Below are two examples illustrating the profound impact of Nillion’s technology across different domains.
-
Healthcare Use Case: Accelerating Development of a Common Cold Vaccine
The Challenge
New strains of the common cold virus emerge annually, complicating vaccine development. Researchers need access to large, diverse datasets to analyze these evolving viruses. However, privacy laws only permit access to patient data with explicit consent, limiting sample size and slowing vaccine development.
Nillion’s Solution
Nillion’s secure computation technology eliminates trust barriers in data sharing through orchestrated coordination. By integrating sMPC and FHE, Nillion enables hospitals to securely share encrypted patient data. Researchers can analyze this data without exposing personal information, enabling safe and private collaboration at scale.
The Impact
With Nillion, researchers can access vast amounts of encrypted patient data, significantly accelerating vaccine development. Safely leveraging nearly unlimited datasets enables rapid identification of vaccine targets and better responses to new strains, all while protecting patient privacy.
Why Existing AI Models Can’t Achieve This
Current AI models rely on trust, requiring patients to consent to sharing raw data—limiting participation and sample size. Data breaches and privacy concerns remain major challenges for platforms like ChatGPT and other large language models (LLMs). Without secure computation, these models cannot ensure sensitive information is neither leaked nor misused, hindering collaborative research under strict privacy protection.
-
Personal Use Case: Secure Personal AI Writing Assistant
The Challenge
Many people often need AI assistance when drafting emails, editing sensitive reports, or summarizing personal documents. However, privacy concerns and data breach risks make users hesitant to entrust confidential information to AI platforms. Current AI systems require access to raw data, raising fears that personal files might be stored, leaked, or misused.
Nillion’s Solution
Nillion offers a secure AI writing assistant that ensures user privacy at every step through its orchestration layer:
-
Orchestrated File Submission: Users securely submit files through Nillion’s orchestration layer, which handles encryption to keep content confidential—even the AI service itself cannot view it.
-
Secure Computation: Supported by the Nillion network, AI processes documents using sMPC and FHE. The orchestration layer coordinates these technologies, enabling AI to edit, summarize, and improve content without decrypting the original document.
-
Private Delivery of Results: The AI-generated output is returned to the user in encrypted form. Only the user can unlock and view the final result using their private decryption key.
The Impact
This approach allows users to confidently use AI for writing tasks while protecting sensitive information. Nillion enables AI to handle tasks previously inaccessible due to privacy concerns—such as processing legal documents or confidential business reports—without compromising trust or data security.
Why Existing AI Models Can’t Achieve This
Existing AI models require access to raw textual data, posing significant privacy risks. Users must trust platforms not to misuse or leak their sensitive files. Nillion eliminates this need for trust by allowing AI to directly process encrypted data, ensuring privacy and confidentiality throughout the entire process.
Conclusion: Nillion Leading the Future of Secure Computation
As the digital world continues to evolve, so do the risks of data breaches and misuse of sensitive information. Escalating data privacy concerns indicate an urgent need for stronger protective measures. Meanwhile, AI holds immense potential to transform industries, yet its full potential remains untapped due to privacy issues and vulnerabilities in current data handling practices.
Currently, AI is limited by privacy concerns and restricted mostly to non-critical applications. However, breakthroughs in secure computation will enable AI to safely process sensitive data, unlocking its true potential. This will be a turning point—AI will integrate deeply into all aspects of our lives, fundamentally transforming industries and how we interact with technology.
Nillion is leading this transformation. With its ability to perform secure computations on encrypted data, Nillion addresses the challenges blocking widespread AI adoption. By leveraging advanced PETs such as secure multi-party computation (sMPC) and fully homomorphic encryption (FHE), Nillion ensures sensitive information remains protected throughout. From enabling secure global collaboration in healthcare to delivering more personalized and secure financial services, Nillion unlocks AI’s full potential while safeguarding privacy and security.
Join Nillion, explore their website, read detailed documentation about their groundbreaking technology, and follow them on X for the latest updates—together, let’s shape the future of secure computation:
Together, we can create a digital world where privacy and innovation coexist.
Acknowledgments
I extend my sincere gratitude to the Nillion team for providing visuals and valuable feedback. I also thank the teams at 3rd St Capital and uDAO for their insightful contributions and support in shaping this article. To learn more about 3rd St Capital, please visit our website:
For more information about uDAO, please visit:
Disclaimer
This document is for informational purposes only. The views expressed herein should not be construed as investment advice or recommendations. Recipients of this document should conduct their own due diligence based on their specific financial situation, investment goals, and risk tolerance (not covered herein) before making any investment decisions. This document does not constitute an offer or solicitation to buy or sell any assets mentioned herein.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News














