
Crypto Identity Crisis: The Bottleneck to Mass Consumer Adoption
TechFlow Selected TechFlow Selected

Crypto Identity Crisis: The Bottleneck to Mass Consumer Adoption
Although the application scenarios of cryptocurrency are becoming increasingly compelling, its identity issue remains underestimated and has become a bottleneck for the success of crypto consumers' applications.
Author: Natalie Mullins
Translation: Mars Finance, MK
In 2023, enthusiasm around "consumer crypto" resurged, partly due to the rise of products like friend.tech and a growing industry focus on infrastructure over end-user applications. Now, many predict 2024 will be the breakout year for crypto's application layer, as teams race to attract the next wave of users—from gaming and decentralized physical infrastructure networks (dePIN) to social experiences.
Yet despite increasingly compelling use cases for cryptocurrency, its identity problem—particularly the ability to defend against Sybil attacks—remains underestimated and poses a bottleneck to the success of consumer-facing crypto applications.
The Root of All Problems: Identity
The issue of on-chain identity is not new; despite years of development and private investment, it remains unresolved. In the previous cycle, even as transaction volumes and activity grew exponentially, many founders ran out of funds due to misjudging product-market fit, mistaking inorganic users for genuine demand. Without robust Sybil resistance, the 2024–2025 cycle risks repeating this pattern.
Proof of Personhood (PoP) is a mechanism to verify an individual’s humanity and uniqueness, seen as foundational for building digital identity. (Source: Worldcoin)
To date, most attention has focused on reputation, decentralized identity (DID), and privacy—important aspects, but ones that do not fundamentally solve the Proof of Personhood (PoP) challenge. Most PoP solutions available today aim to combat AI-driven misinformation and Sybil attacks, yet crypto may require uniquely tailored PoP solutions for similar but distinct reasons. The highly financialized nature of crypto creates strong incentives for fraud and adversarial behavior, most notably hacking and Sybil farming. As we shift from Web2’s ad-subsidized model to Web3’s user-owned paradigm, centralized value-extraction platforms will give way to more open networks and protocols that continuously distribute rewards and ownership to end users. Without strong identity solutions, crypto teams will find themselves locked in endless battles defending their products and treasuries from malicious actors—undermining crypto’s core value proposition of scaling incentive alignment.

Early DeFi projects like Uniswap and dYdX set an unsustainable industry standard by rewarding users thousands or even tens of thousands of dollars simply for using their products. Today, many crypto natives expect substantial airdrops from minimal product engagement—even if passive or one-time. As a result, many teams are adopting stricter eligibility criteria and strategically reducing activity from bots and multi-wallet human farmers.
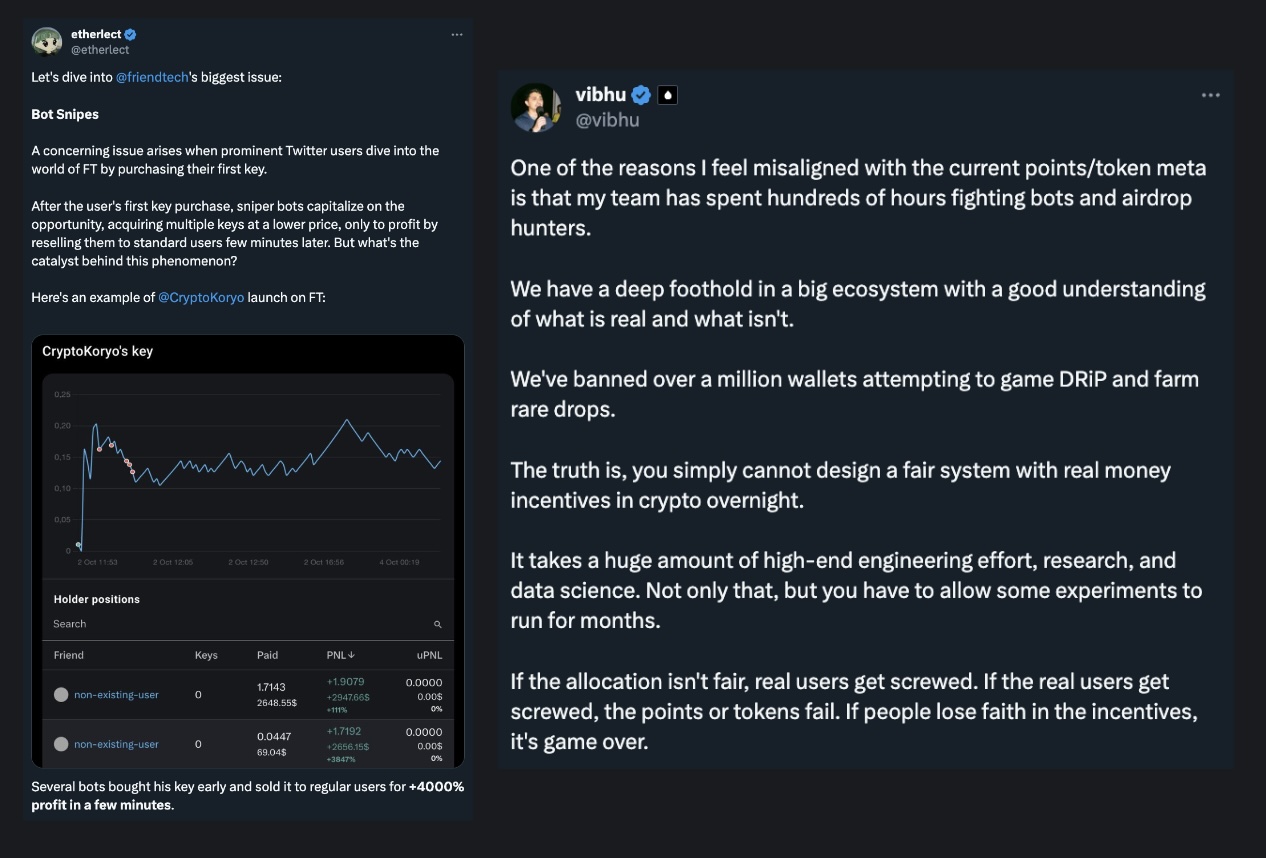
Anyone who has spent significant time on Sybil resistance in crypto knows it’s an endless game of cat and mouse. As crypto teams become more sophisticated in risk mitigation, so too do Sybil farmers evolve. 2023 became a pivotal year, with YouTube content uploads and searches related to “airdrops” reaching record highs, alongside increasingly advanced farming tools entering the market. Articles such as Kerman Kohli’s exposed extreme examples, including products that automatically deploy wallets and execute various on-chain actions while offering countermeasures against any Sybil resistance techniques crypto teams might employ.
This dynamic harms not only most startups but also degrades the quality of on-chain data signals. While blockchains are often praised for their “openness” and “transparency,” the financial incentives to manipulate key metrics—such as active wallets or trading volume—are so high that much of the on-chain user activity data becomes functionally useless. This presents a major challenge for crypto founders striving to establish truthful baselines for fundamental metrics like unique human users, customer acquisition cost (CAC), or customer lifetime value (LTV).
Exploring the Design Space
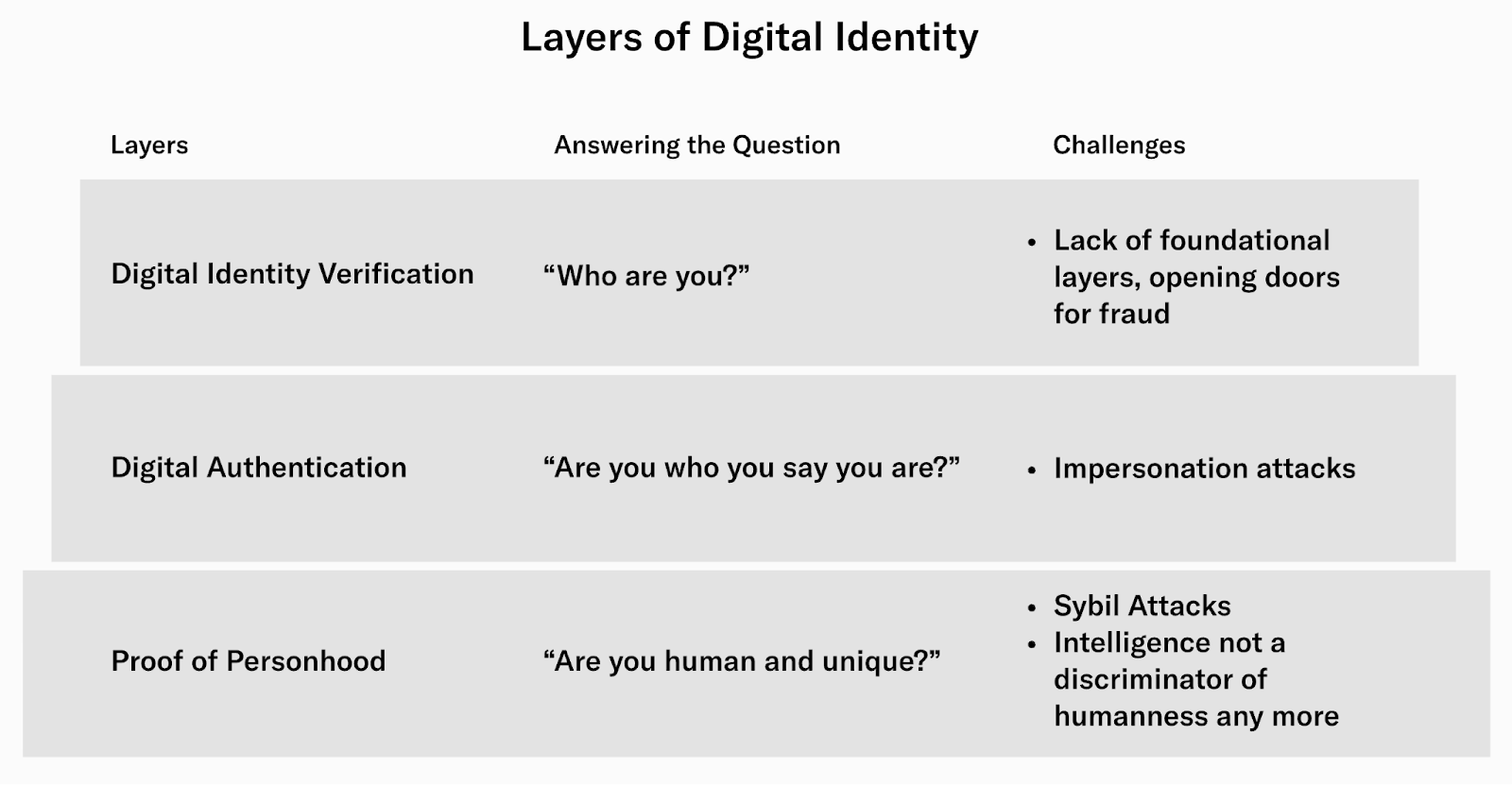
Within the context of Proof of Personhood, there are two primary ways to think about identity: uniqueness and humanness.
Uniqueness refers to whether an account interacting with an application represents a single, distinct human or multiple accounts operated by one individual. Many founders view one wallet per unique human user as the ideal standard, though crypto wallets currently aren’t designed to enforce this. Some projects may lean toward mature solutions like KYC, but these come with significant trade-offs.
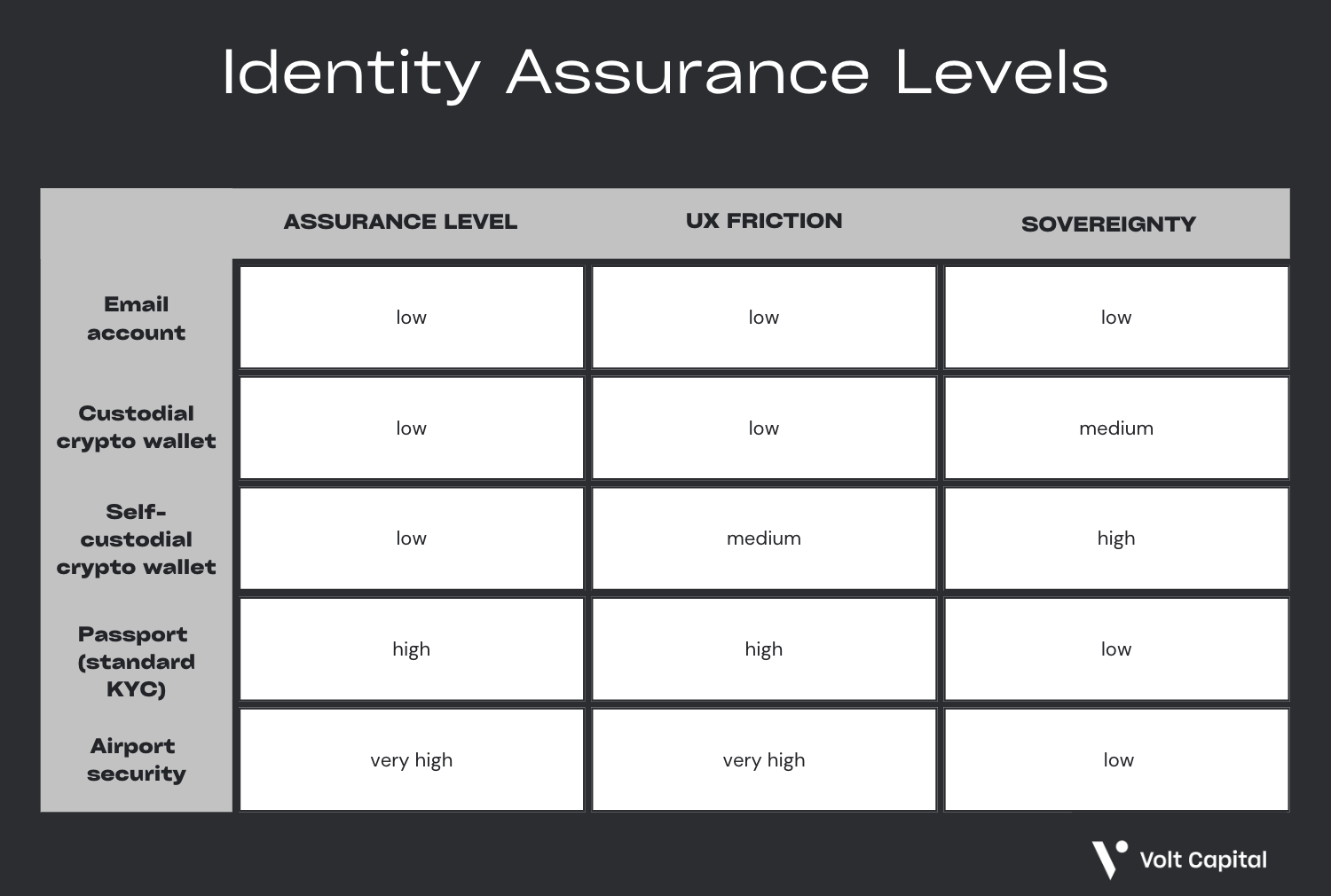
For those unfamiliar with the concept of Identity Assurance Levels (IAL), defined by the National Institute of Standards and Technology, IAL conveys “the degree of confidence that an asserted identity is the individual’s true identity.” Identity solutions typically fall into three categories:
1. Some confidence (Level 1) – Identity is self-asserted; no verification required (e.g., email accounts).
2. High confidence (Level 2) – Identity is verified by a third party; requires in-person or remote verification (e.g., government-issued ID, credential documents, address verification).
3. Very high confidence (Level 3) – Identity is verified by a third party using biometric data; requires in-person verification (e.g., TSA agent verifying photo ID or fingerprints).
Humanness relates to whether account activity is generated by bots or real humans. Currently, detecting humanness is easier than verifying uniqueness, primarily because human users tend to exhibit more complex behavior than bots. Teams investing in honeypot technologies and data-driven monitoring and detection infrastructures can usually mitigate large-scale bot-driven activity, although multi-wallet human farmers present a different kind of challenge.
Long-term, distinguishing humanness may become more challenging and ambiguous, especially as some accounts oscillate between bot-generated and human-generated activity. This dynamic will intensify as humans deploy bots (“agents”) to traverse the internet and transact on their behalf. Some more ambitious (and controversial) identity solutions, such as Worldcoin, are attempting to tackle this Proof of Personhood problem—often relying on various forms of KYC or biometric data.
Crucially, continuous identity verification is essential when validating uniqueness and/or humanness. Solutions that verify identity only at creation are particularly vulnerable to Sybil attacks and fraudulent behaviors, which could range from selling access to self-custodied wallets (e.g., OTC trades) to more organized attacks (e.g., reverse-engineering identity and/or reward systems).
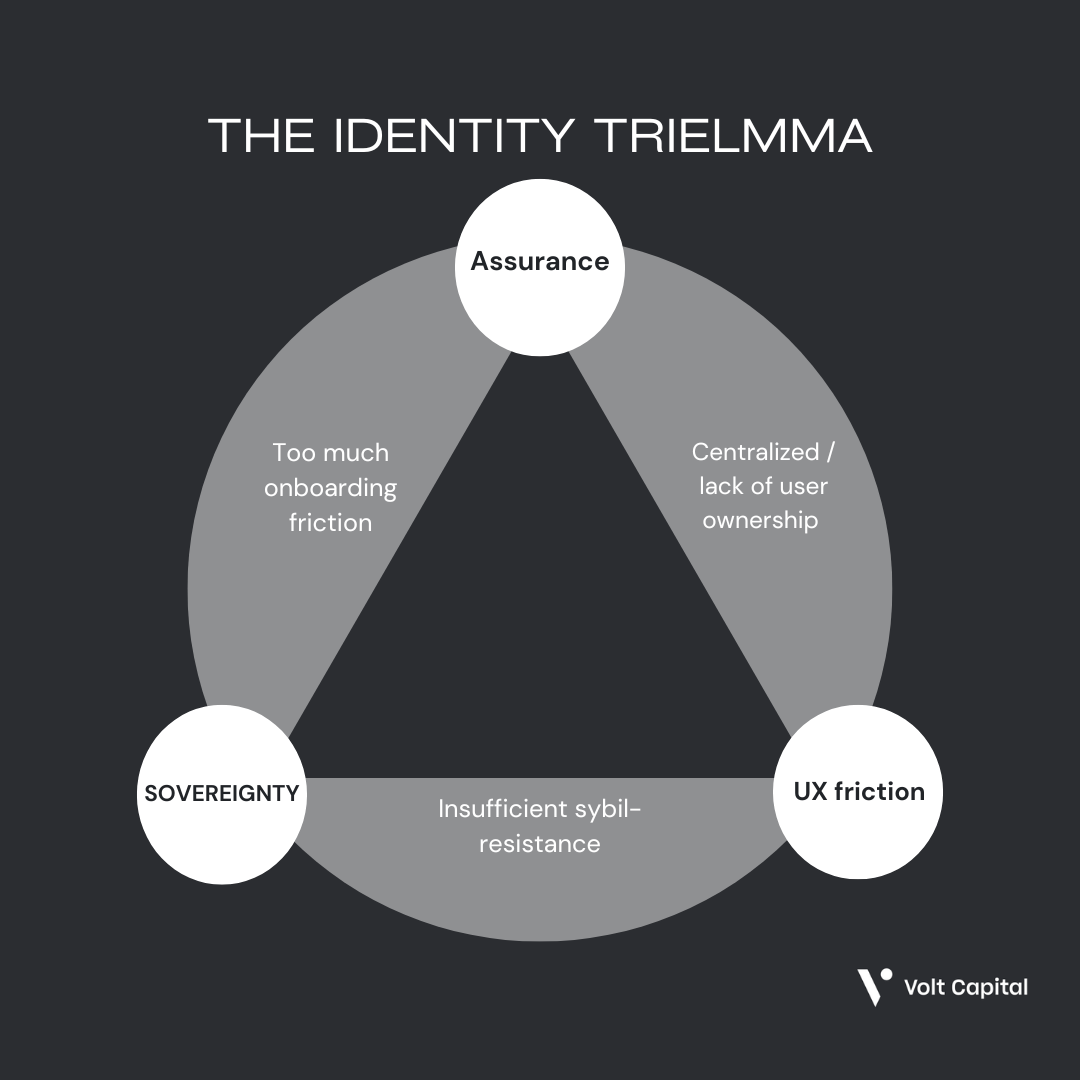
The ideal identity solution would provide the highest level of assurance without introducing excessive user friction or compromising sovereignty. However, since such a solution does not yet exist, crypto founders are forced to make trade-offs best suited to their specific use cases.
Promising Solutions
1. Proofs
Cryptographic signature statements made by one party about themselves or others.
While not typically applicable to PoP, proofs are fundamental primitives of cryptographic identity. They rightly treat identity as a collection of reputational credentials, where different aspects of identity hold relevance or value depending on context (e.g., local vs. national, official vs. informal). An open and composable standard for creating proofs and schemas—such as Ethereum Attestation Service—could greatly expand the on-chain identity space and eliminate the need for “identity providers” to constantly reinvent proprietary wheels.
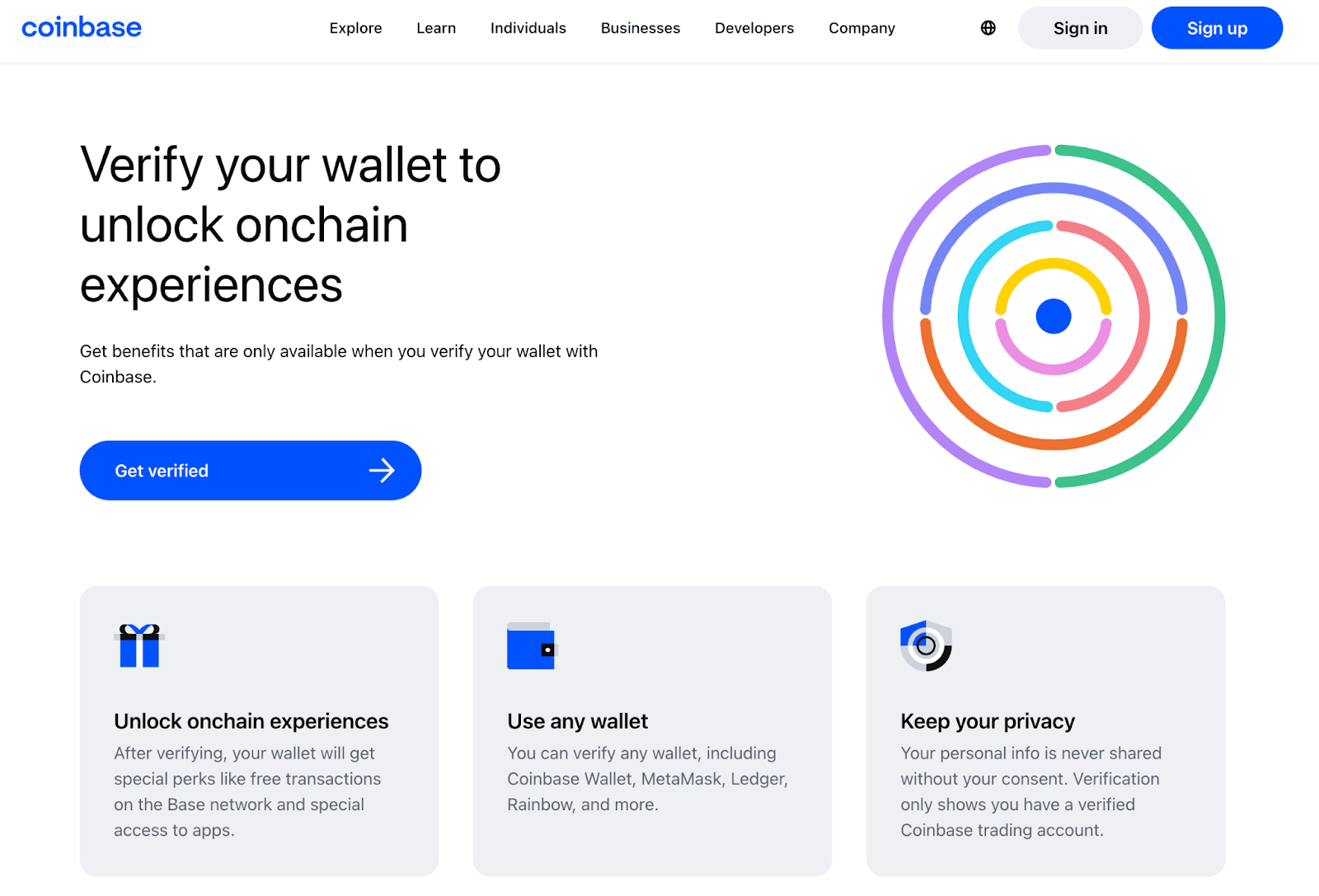
For example, Coinbase’s “Verification” product uses the Ethereum Attestation Service to issue on-chain attestations verified by Coinbase, including KYC proof. Users opt into verification through exclusive incentive perks. (Source: Coinbase)
2. Progressive Proof of Personhood
Rewarding users over time based on demonstrated uniqueness.
While no solution is entirely foolproof, KYC and biometrics are undoubtedly among the highest-assurance identity tools currently available. Yet certain characteristics of crypto reduce the feasibility of these solutions:
-
Industry-wide resistance to KYC / emphasis on privacy and sovereign identity.
-
Biometrics are rarely used or adopted in consumer applications (except health and fitness apps).
-
Need for continuous and dynamic identity assurance.
The main goal of progressive PoP is to design systems that reward users over time based on behaviors that demonstrate their uniqueness/humanness. The other challenge lies in avoiding incentives for wasteful resource consumption and ensuring rewarded actions genuinely correlate with uniqueness.
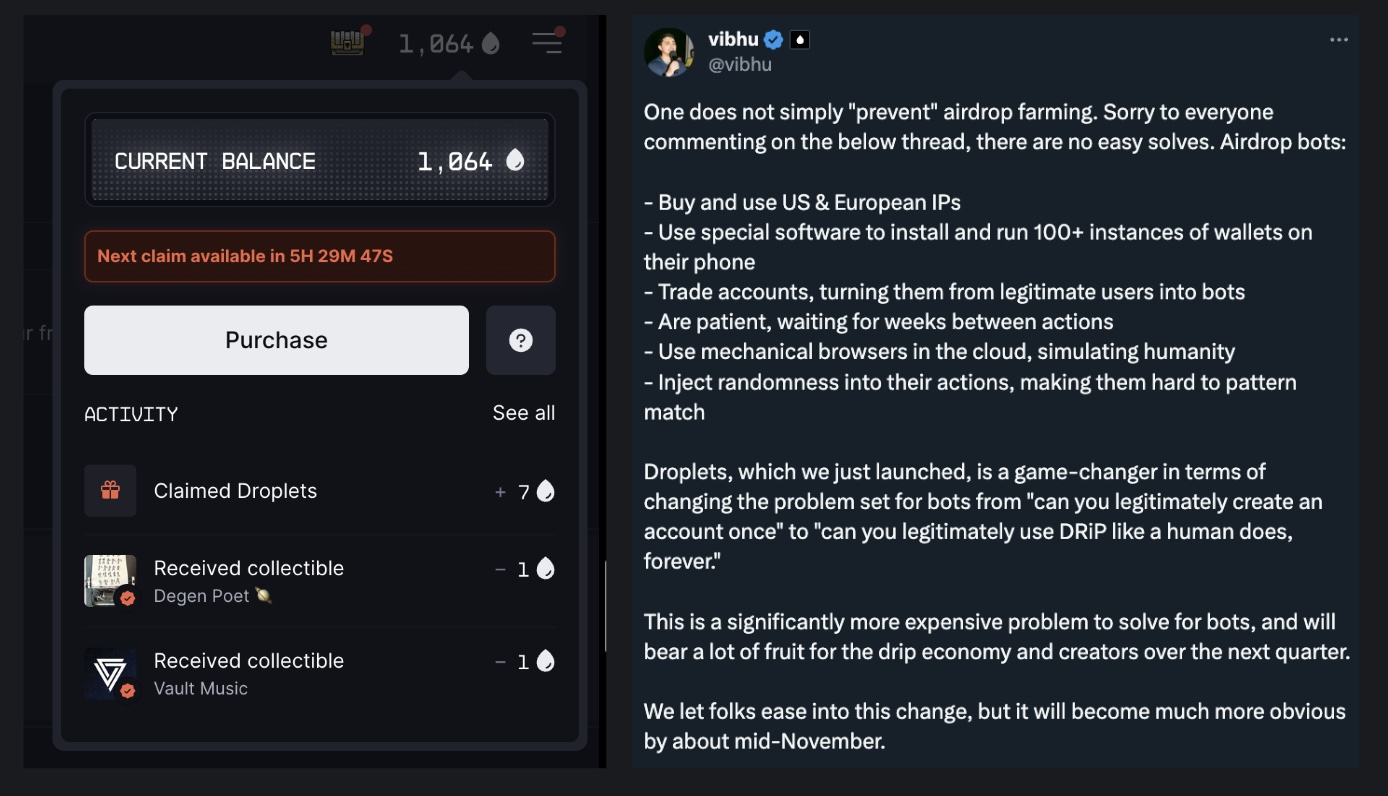
For instance, DRiP, a creator-centric content distribution platform, recently launched its Droplets feature, rewarding users for logging in daily and engaging meaningfully with the product. Each collectible received deducts 1 drip automatically from the user’s total balance. Only users with enough Droplets to receive collectibles are considered “active,” helping the DRiP team build more accurate daily active user (DAU) and engagement metrics.
Conclusion
In many ways, online identity primitives have never truly moved beyond low-assurance solutions like email accounts. Without crypto’s financial incentives or the rise of generative AI, these solutions might never have needed to change. Yet while these technologies will bring innovation in the coming years, they also make the identity problem harder and more complex for the foreseeable future. That’s precisely why the identity issue in crypto isn’t just about decentralized identifiers (DID) or privacy mixers—the very viability of cryptoeconomic incentives is at stake.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News












