Groom Lake: A Private Security Firm in the Lawless World of DeFi
TechFlow Selected TechFlow Selected

Groom Lake: A Private Security Firm in the Lawless World of DeFi
In today's Web3, we need our own Pinkertons.
Written by: Lewy
Compiled by: TechFlow
Since 2014, an estimated $80 billion has been stolen due to hacks and exploits. Last year alone, around $10 billion was lost, with $4 billion coming from cryptocurrency. In the second quarter of this year, crypto losses exceeded $300 million. Ethereum itself lost nearly $65 million across 55 incidents.
DeFi lacks sufficient security, and FDR, founder of Groom Lake, aims to improve it—whether in response to current market demands for leverage and incident response planning or in operational monitoring to prevent vulnerabilities.
Right now, DeFi is like the wild west.
In the real Wild West, there were times when local sheriffs or federal agents couldn't help, so people turned to the Pinkertons—a private security/detective agency founded around 1850.
In today's Web3, we need our own Pinkertons. Protocols and individuals are constantly losing funds to hackers and exploits, naively begging attackers to return stolen money.

Earlier this month, we witnessed the unexpected Vyper/Curve exploit, through which hackers obtained $69 million.
As we've seen, protocols focused on launching quickly in a volatile environment don't necessarily spend extra time on security operations.
When responding to exploits, time isn't just critical—it’s also about leverage. In active situations, protocols or individuals need rapid escalation to gain the upper hand.
FDR shared a story where they limited all communications to reduce the exploiter’s influence. As a result, there was no noise on Twitter—no messages, nothing.
Later, the attacker sent an email via a temporary Protonmail address—and just like that, the attacker lost control, leading to the hacker's downfall.
Through carefully orchestrated psychological warfare, his team professionally took control of the situation.
What is Groom Lake?
As FDR puts it, "Groom Lake is the private military company of DeFi."
Groom Lake is a specialized cybersecurity and intelligence operations firm. They provide everything from structure, frameworks, crisis response plans, to compliance—delivering both proactive and reactive security measures that protocols need. FDR said he wants to build Groom Lake into an agile team, similar to light infantry.

Based on current metrics, Groom Lake can deploy an agent globally for real-time, on-site operations within 24–48 hours.
Compared to Web2, where teams typically have 72 hours to resolve issues during active incidents—not to mention access to virtually unlimited resources—in the crypto space, attackers can drain funds in just a few hours. There's no time to mobilize.
In today's environment, cybersecurity consulting firms often extort protocols, taking advantage of projects’ willingness to pay large sums for security services. And audits aren’t cheap either—they can range from thousands to hundreds of thousands of dollars.
Groom Lake offers both proactive and reactive security services at a cost lower than hiring a single internal cybersecurity employee, covering all domains: psychological operations, offensive hacking, defensive security, forensics, and even human intelligence. Groom Lake leverages a global network embedded within governments and institutions across six continents.
Best and Worst Security Practices
When asked about best and worst security practices for users and founders, FDR had a lot to say.
If you use a VPN to enhance privacy, choose one with locally developed proprietary software that fully utilizes advanced settings. Be aware that the "Fourteen Eyes" alliance consists of 14 countries—including the U.S., Germany, and the U.K.—that share surveillance data among members. For maximum privacy, select a VPN provider headquartered outside these nations. As FDR said, "Once your data leaves your control, it becomes a public target…"
Another example of poor security practice is using SMS for 2FA... FDR put it best: "Like what? Why?" While something is better than nothing, there's no reason to use SMS-based 2FA anymore. People can easily switch to virtual authenticators instead of text messages. FDR prefers VA apps (like Google Authenticator, Authy) because they’re convenient, secure, and easy to use. YubiKeys are another solid choice—slightly paranoid but extremely secure.
Beyond these "lower-level" security practices, FDR emphasizes that protocols must establish a Crisis Response Plan (CRP). In the U.S. military, clear communication is essential for effective coordination and successful outcomes. If a security breach occurs, everyone knows their role thanks to a pre-defined Crisis Response Plan (CRP). Community managers prepare templated messages and work shifts during the first 48 hours. An incident response manager acts as a central hub, coordinating actions to keep everyone aligned. Legal, PR, and media teams stand ready to draft negotiation emails. Proactivity is key—everyone knows their responsibilities and executes them efficiently. Following FDR’s advice, CRP drills should be conducted at least annually, much like fire drills. These measures ensure both individuals and entire protocols are prepared for worst-case scenarios like hacks or exploits.
What is Drosera?
Drosera is the world’s first Decentralized Autonomous Response Collective (DARC), a set of smart contracts built on EigenLayer that enables consensus-layer ETH operators to mitigate hacks.
Drosera provides round-the-clock monitoring and incident response capabilities.
Protocols benefit from reduced gas costs, as advanced validation checks are performed off-chain. Drosera uses proprietary technology to conceal protocol security configurations—even from the operators themselves.

Drosera is a spin-off of Groom Lake. FDR realized that in Web3, highly agile teams operate within an unstructured industry and environment, with little regulatory consideration, rushing products to market. Often, projects don’t have time to focus on security operations or ensure everything is secure. That’s how Drosera came to be…
During Drosera’s development, FDR prioritized user-friendly access, recognizing that DeFi and crypto often lack friendliness toward users and founders. Drosera is designed to offer accessible services at a lower cost than bug bounties and audits. FDR envisions a simplified user experience where customers can easily access Drosera’s features by visiting a website and clicking a button.
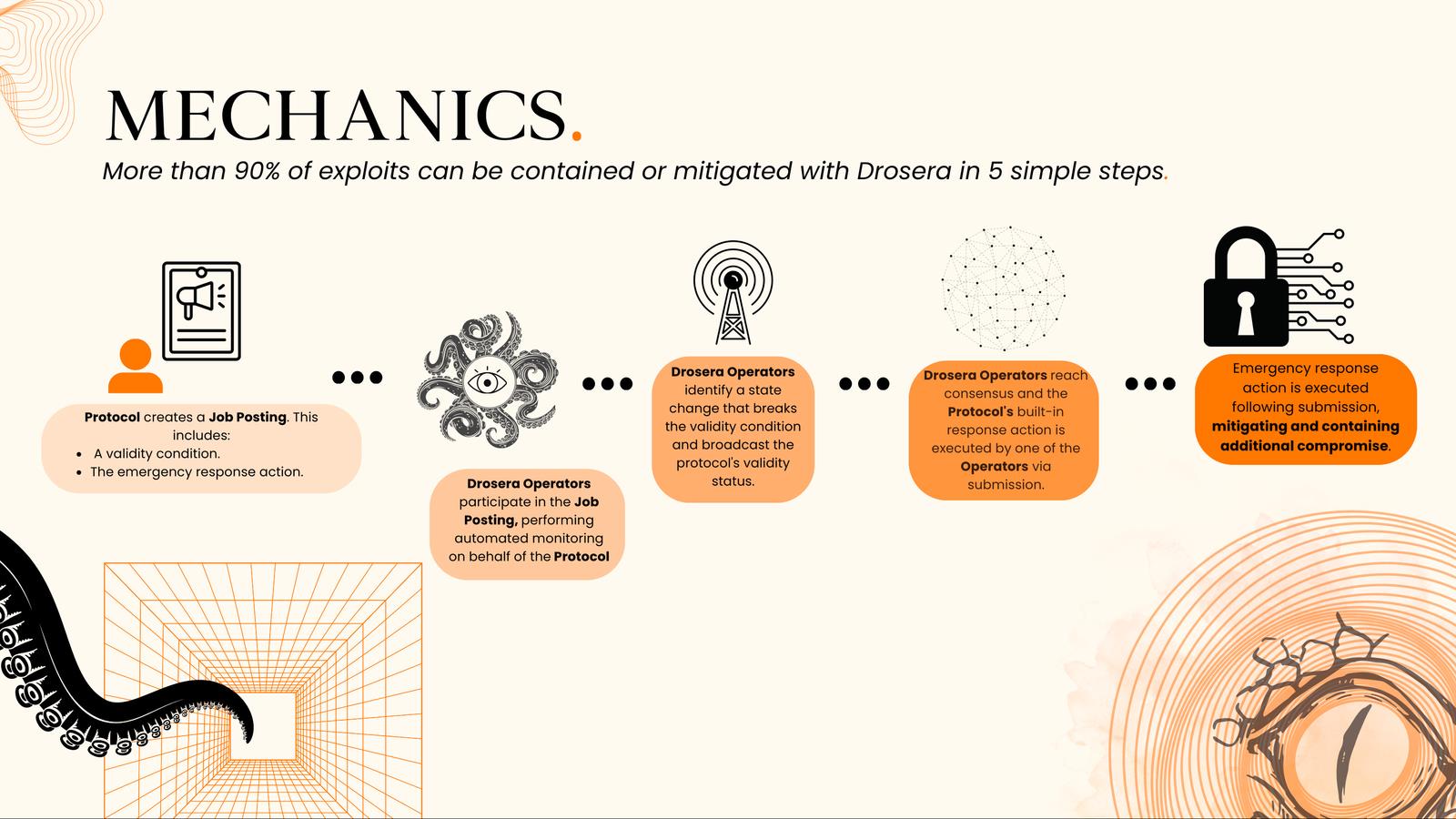
Drosera mitigates the impact of security vulnerabilities through a five-step process. First, a protocol posts a "mission" outlining specific validity conditions and emergency response actions. Second, Drosera operators join the mission and conduct automated monitoring on behalf of the protocol. Third, these operators detect any state changes violating the validity conditions and immediately broadcast the status. Fourth, operators reach consensus and activate the protocol’s preset emergency action via one operator’s submission. Finally, this action effectively contains and mitigates further risk to the protocol. FDR guarantees that within a 24–48 hour window, Drosera can move swiftly from detection to deployment—even directly engaging the attacker.
Compared to fully programmable approaches, Drosera simplifies security by reducing the need for complex structures, saving developers time and lowering additional costs. As the first platform offering accessible security solutions, Drosera strengthens network security block by block.

Regarding its development timeline, Drosera is being built on EigenLayer as an Active Validation Service (AVS). Its minimum viable product (MVP) is awaiting deployment to collect initial real-world data and establish itself as a "security AVS." In phase two, the focus will shift to B2B business development with key partners as an entry point into the broader EVM ecosystem. By Q1 2026, Drosera aims to complete its Series A funding and evolve into a fully democratized and decentralized security marketplace.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News