
Ethereum's New Privacy Infrastructure: In-Depth Analysis of How Aztec Achieves "Programmable Privacy"
TechFlow Selected TechFlow Selected

Ethereum's New Privacy Infrastructure: In-Depth Analysis of How Aztec Achieves "Programmable Privacy"
From Noir language to Ignition Chain, a comprehensive breakdown of Ethereum's full-stack privacy architecture.
Author: ZHIXIONG PAN
In the second decade of blockchain technology's development, the industry faces a fundamental philosophical and technical paradox: while Ethereum has successfully established itself as a trustless value settlement layer—the "world computer"—its radical transparency is becoming a barrier to mass adoption. Today, every on-chain user interaction, asset allocation, salary transfer, and even social relationship is exposed within a permanent, immutable public panopticon. This "glass house" existence not only violates personal sovereignty but also excludes most institutional capital due to the lack of commercial confidentiality.
2025 marks a decisive turning point in industry consensus. Vitalik Buterin, co-founder of Ethereum, clearly stated that "privacy is not a feature, it's hygiene," defining it as a foundational element of freedom and a necessary condition for social order. Just as the internet evolved from plaintext HTTP to encrypted HTTPS—enabling the rise of e-commerce—Web3 is now reaching a similar inflection point. With approximately $119 million in funding support, Aztec Network (Ignition architecture) is advancing Ethereum’s infrastructure toward programmable privacy through Ignition Chain, the Noir language ecosystem, and exploration of Noir-based proof applications such as zkPassport.

Macro Narrative: From Single-Point Breakthroughs to Deep "Holistic Privacy" Defense
Ethereum’s understanding of privacy has moved beyond isolated mixing protocols, evolving into a "holistic privacy" architecture spanning network, hardware, and application layers. This paradigm shift became a focal point at the 2025 Devconnect conference, establishing that privacy protection must have full-stack defensive depth.
Redefining Software Standards: Kohaku and Stealth Meta-Addresses
The Kohaku reference implementation, developed by the Ethereum Foundation's Privacy & Scaling Exploration (PSE) team, marks the transition of privacy technology from "wild plugins" to formalized infrastructure. Kohaku is more than just a wallet SDK—it aims to fundamentally restructure the account system.
By introducing the "stealth meta-address" mechanism, Kohaku allows recipients to publish only a static meta-public key, while senders use elliptic curve cryptography to generate unique one-time on-chain addresses for each transaction.
To external observers, these transactions appear to be sent to random black holes, making it impossible to link them to users' real identities. Furthermore, Kohaku provides reusable integration components around mechanisms like stealth meta-addresses / stealth addresses, pushing privacy capabilities from add-ons toward standardized wallet infrastructure.
The Final Frontier of Hardware Security: ZKnox and Quantum Resistance
If Kohaku safeguards logic at the software level, then ZKnox—funded by the Ethereum Foundation (EF) to address hardware gaps in the ecosystem—focuses on deeper issues of key security and future threats. As ZK applications proliferate, increasingly sensitive witnesses (which may include key material, identity data, or transaction details) must participate in proof and signing processes on the client side, expanding the attack surface in case of device compromise. ZKnox concentrates on improving infrastructure so post-quantum (PQ) cryptography becomes both usable and affordable on Ethereum—for example, proposing precompiles to reduce lattice-based cryptographic computation costs—and paving the way for migration to PQ signature schemes.
Critically, with quantum computing potentially threatening traditional elliptic curve cryptography by the 2030s, ZKnox focuses on enabling "usable and affordable" post-quantum cryptography on Ethereum. For instance, EIP-7885 proposes adding an NTT precompile to lower the on-chain verification cost of lattice-based cryptography (including schemes like Falcon), preparing the network for future PQ transitions.
Aztec's Historical Significance and Technical Architecture: Defining the "Private World Computer"
Within the evolution of privacy technologies, Aztec occupies a unique niche. Unlike Bitcoin-era pseudonymity or the single-dimensional "transactional privacy" offered by Zcash or Tornado Cash, Aztec strives for Turing-complete "programmable privacy." Its core team includes co-inventors of the PLONK zero-knowledge proof system, giving Aztec deep roots in original cryptographic innovation.
Hybrid State Model: Breaking the Impossibility Triangle
The biggest challenge in building a private smart contract platform lies in state management. Traditional blockchains are either fully public (like Ethereum) or fully private (like Zcash). Aztec introduces a novel hybrid state model: at the private layer, it uses a Bitcoin-like UTXO model, storing user assets and data as encrypted "notes."
These notes are marked as "spent/expired" via nullifiers, preventing double-spending while preserving privacy of note contents and ownership relationships. At the public layer, Aztec maintains publicly verifiable states updated by public functions executed in a public execution environment on the network.
This architecture enables developers to mix private and public functions within the same smart contract. For example, a decentralized voting app can publicly expose the "total vote count" as global state, while strictly keeping "who voted" and "what they voted for" confidential via private state.
Dual Execution Model: The Harmony of PXE and AVM
Aztec splits execution between client and network layers: private functions run in the client-side Private Execution Environment (PXE), generating proofs and commitments related to private state; public state transitions are processed by the sequencer (running the public execution environment/VM), which generates—or delegates to a prover network—the validity proof that can be verified on Ethereum.
-
Client-Side Proving: All private data processing occurs locally within the user’s "Private Execution Environment (PXE)." Whether generating transactions or computing logic, private keys and plaintext data never leave the user’s device. The PXE runs circuits locally and produces a zero-knowledge proof.
-
Public Execution and Verification (AVM): Users submit only the generated proof to the network. The sequencer or block committee verifies private proofs and re-executes public components during block construction. Public contract logic runs in the AVM and is included in the final validity proof verifiable on Ethereum. This split—private inputs handled client-side, public state transitions provably verified—contains the tension between privacy and verifiability within a formally defined interface boundary, without requiring all nodes to see plaintext data.
Interoperability and Cross-Layer Communication: Portals and Asynchronous Messaging
Under the Ignition architecture, Aztec does not treat Ethereum as a back-end engine to proxy DeFi instructions. Instead, it establishes L1↔L2 communication abstractions through Portals. Since private execution requires clients to "prepare and prove" ahead of time, while public state changes must be executed by the sequencer on-chain, cross-domain calls in Aztec follow a unidirectional, asynchronous message-passing model: L2 contracts can initiate call intents to an L1 portal (or vice versa), with messages becoming consumable in subsequent blocks via rollup mechanisms. Applications must explicitly handle failure and rollback scenarios.
The rollup contract plays a critical role in maintaining state roots, verifying state transition proofs, and managing message queue states—enabling composable interactions with Ethereum while preserving privacy constraints.
Strategic Engine: The Noir Language and Democratizing Zero-Knowledge Development
If Ignition Chain is Aztec’s body, then Noir is its soul. For a long time, developing zero-knowledge applications was hindered by the "dual-brain problem": developers had to be both expert cryptographers and skilled engineers, manually translating business logic into low-level arithmetic circuits and polynomial constraints—an inefficient process prone to security vulnerabilities.
The Power of Abstraction and Backend Agnosticism
Noir emerged to end this "Tower of Babel" era. As an open-source domain-specific language (DSL), Noir features modern syntax similar to Rust, supporting loops, structs, function calls, and other high-level constructs. According to Electric Capital’s developer report, writing complex logic in Noir requires only one-tenth the code volume compared to traditional circuit languages like Halo2 or Circom. For example, the Payy privacy payment network reduced its core codebase from thousands of lines to about 250 after migrating to Noir.
Even more strategically significant is Noir’s "backend agnosticism." Noir compiles to an intermediate representation (ACIR), which can interface with any proof system supporting the standard.
By decoupling circuit expressions from specific proof systems via ACIR, Noir defaults to Barretenberg within the Aztec protocol stack, but ACIR can also be converted or adapted to other backends like Groth16 off-chain or in different systems. This flexibility positions Noir as a universal standard across the ZK landscape, breaking down barriers between ecosystems.
Ecosystem Explosion and Developer Moats
Data confirms Noir’s strategic success. In Electric Capital’s annual reports, the Aztec/Noir ecosystem has ranked among the top five fastest-growing developer ecosystems for two consecutive years. Over 600 projects on GitHub now use Noir, spanning identity verification (zkEmail), gaming, and complex DeFi protocols.
By hosting the global NoirCon developer conference, Aztec not only strengthens its technical moat but also fosters an active ecosystem of privacy-native applications—heralding a Cambrian explosion of privacy apps.
Network Foundation: Decentralized Practice of Ignition Chain
In November 2025, Aztec launched Ignition Chain on the Ethereum mainnet—a milestone focused initially on decentralized block production and proof workflows, with transaction and contract execution expected to gradually open in early 2026. This is not just a technical achievement, but a bold realization of Layer 2 decentralization promises.
The Courage to Be Decentralized from Day One
In today’s Layer 2 scaling race, most networks (e.g., Optimism, Arbitrum) rely on a single centralized sequencer at launch to ensure performance, postponing decentralization indefinitely.
Aztec chose a radically different path: Ignition Chain operates from inception under a decentralized validator/sequencer committee structure, proactively delegating key permissions to an open set of validators. The network triggered genesis block production once the validator queue reached a threshold of 500, attracting over 600 validators in its early stages to participate in block production and endorsement.
This design is not redundant—it is the survival baseline for a privacy network. If the sequencer were centralized, regulators or powerful entities could easily pressure it to censor or reject privacy transactions from specific addresses, rendering the entire privacy network ineffective. A decentralized sequencer/committee eliminates single-point censorship risks and significantly enhances resistance against transaction suppression, assuming honest participants exist and protocol assumptions hold.
Performance Roadmap
While decentralization ensures security, it poses performance challenges. Currently, Ignition Chain generates blocks every 36–72 seconds. Aztec’s roadmap aims to compress this interval down to around 3–4 seconds by the end of 2026 through parallelized proof generation and network-layer optimizations—approaching Ethereum mainnet’s interactive experience. This marks the shift of privacy networks from merely "usable" to "high-performance."
Killer Application: zkPassport and the Paradigm Shift in Compliance
Technology remains cold until it solves real human problems. zkPassport—more accurately described as one of several identity proof/compliance signaling tools in the Noir ecosystem—is adopted by Aztec in its own context to perform minimal-disclosure compliance checks (e.g., sanctions list screening), exploring a middle ground between privacy and regulatory requirements.
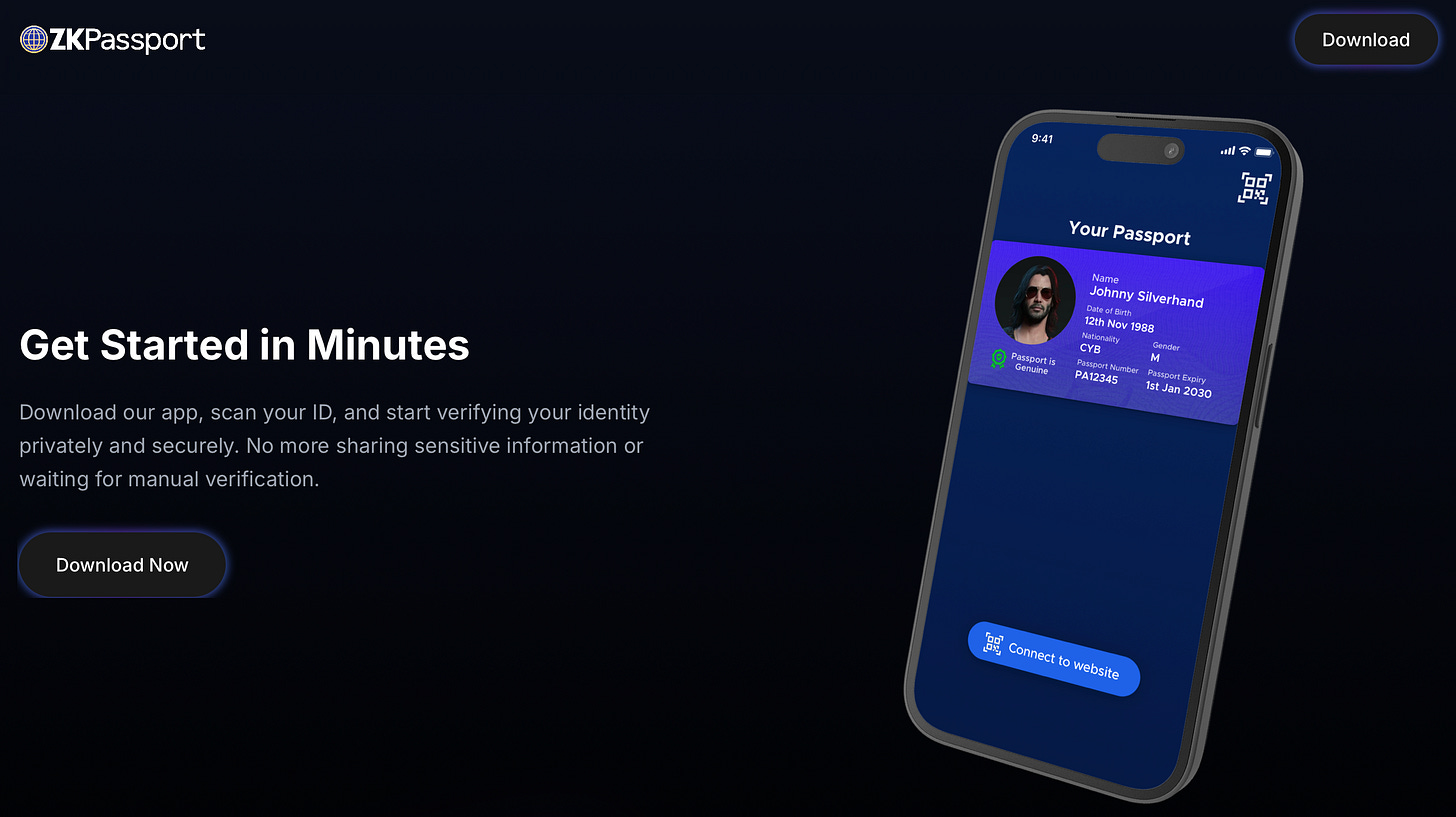
From Data Collection to Fact Verification
Traditional KYC ("Know Your Customer") processes require users to upload passport photos and ID documents to centralized servers—cumbersome and creating numerous vulnerable data honeypots. zkPassport completely overturns this logic: leveraging NFC chips and government digital signatures embedded in modern e-passports, it enables local reading and verification of identity information through physical contact between phone and passport.
Subsequently, a Noir circuit running on the user’s phone generates a zero-knowledge proof. Users can prove facts such as "I am over 18," "My nationality is on the permitted list / not in a restricted jurisdiction," or "I do not appear on sanction lists," without revealing exact birth dates, passport numbers, or other detailed fields.
Sybil Resistance and Institutional Access
The significance of zkPassport extends far beyond identity verification. By generating anonymous identifiers based on passports, it offers a robust "Sybil resistance" tool for DAO governance and airdrop distribution, ensuring "one person, one vote" fairness while eliminating the possibility of reverse-tracking real identities.
In practice, such verifiable, minimally-disclosing compliance signals could reduce institutional friction in participating in on-chain finance. While not equivalent to full KYC/AML procedures, institutions can use zkPassport to demonstrate compliance eligibility and engage in on-chain financial activities without exposing trading strategies or fund sizes. Through this application, Aztec demonstrates that compliance does not require building a panopticon—technology can simultaneously satisfy regulatory demands and protect individual privacy.
Economic Model: Continuous Clearing Auction (CCA) and Fair Distribution
As the native fuel of a decentralized network, the issuance mechanism of the AZTEC token reflects the project’s extreme commitment to fairness. Aztec abandoned traditional models prone to bot sniping and gas fee wars, partnering with Uniswap Labs to introduce the innovative "Continuous Clearing Auction (CCA)."
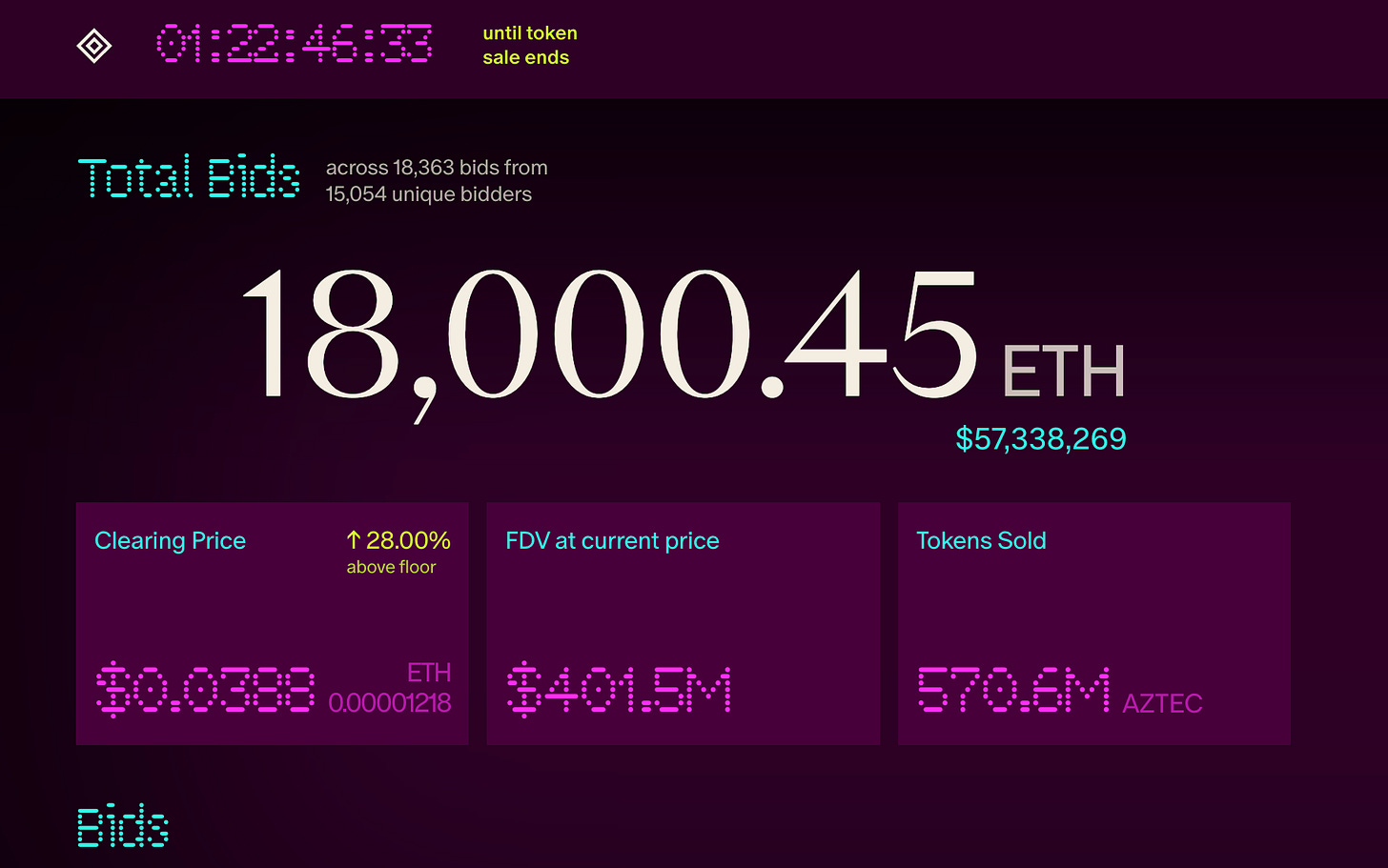
Price Discovery and MEV Resistance
The CCA mechanism allows the market to fully negotiate and discover true prices within a defined time window. Within each clearing cycle, trades settle at a uniform clearing price, reducing incentives for frontrunning and gas bidding. This effectively eliminates profit opportunities for snipers, placing retail investors on equal footing with whales.
Protocol-Owned Liquidity
More innovatively, CCA automates the closed loop between issuance and liquidity creation. The auction contract can automatically inject a portion of proceeds and tokens into a Uniswap v4 liquidity pool according to publicly disclosed parameters, forming a blockchain-verifiable "issuance → liquidity" cycle.
This means AZTEC tokens enjoy deep on-chain liquidity from day one, avoiding the typical volatility seen in new token launches and protecting early community participants. This more DeFi-native approach to issuance and liquidity seeding exemplifies how AMMs can evolve from mere "trading infrastructure" into "issuance infrastructure."
Conclusion: Building Web3’s "HTTPS Era"
Aztec Network’s ecosystem—from the foundational Noir language standard to upper-layer applications like zkPassport, and the network backbone of Ignition Chain—is transforming the Ethereum community’s long-held vision of an "HTTPS upgrade" into an engineering reality. This is not an isolated technical experiment, but part of a broader movement aligned with native Ethereum initiatives like Kohaku and ZKnox, collectively building a layered privacy defense system spanning hardware to applications.
If the early phase of blockchain development established trustless value settlement, the next central theme will be asserting data autonomy and confidentiality. In this journey, Aztec plays a vital infrastructural role—not seeking to replace Ethereum’s transparency, but complementing it with "programmable privacy" to complete the missing half. As technology matures and compliance frameworks evolve, we can look forward to a future where privacy is no longer an "add-on feature" but a "default property"—a "private world computer" that preserves the verifiability of public ledgers while respecting individual digital boundaries.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News













