EVM to RISC-V? Discussing the Past and Present of RISC-V and Its Applications in Web3
TechFlow Selected TechFlow Selected

EVM to RISC-V? Discussing the Past and Present of RISC-V and Its Applications in Web3
Although the introduction of RISC-V faces challenges such as compatibility with existing ecosystems and balancing performance and security, it also provides infinite possibilities for future blockchain technologies.
1. Introduction
Blockchain, as a new type of distributed computing platform, is not merely based on data structures or cryptographic algorithms at its foundation—it represents a revolution in execution environments. From smart contract execution to cross-chain verification, from decentralized applications (DApps) to zero-knowledge proof (ZKP) generation, every on-chain action ultimately needs to be interpreted and executed by some form of virtual machine (VM). Underlying the VM's operation is a component often overlooked yet critically important: the hardware instruction set architecture (ISA).
In traditional blockchain systems, we habitually assume that "a virtual machine is a software issue", relating only to programming languages and runtime environments. Ethereum’s EVM is a stack-based VM customized for smart contracts, while Polkadot and Near use WebAssembly (WASM) as their runtime standard. However, as blockchains evolve toward higher performance, verifiability, and customizability, an undeniable trend is emerging: hardware ISA is re-emerging as a key component in the design of on-chain execution models.
1.1 The Connection Between Blockchain and Hardware Instruction Sets
In traditional operating systems, the instruction set serves as a bridge between the OS and hardware, abstracting the operations a processor can perform. In blockchain systems, due to their characteristics of “verifiable execution” and “cross-platform determinism,” VM behavior must not only be correct but also provable and reproducible. This requirement pushes VM instruction semantics to be clear, concise, and deterministic—qualities that align closely with the original design principles of RISC architectures.
More importantly, in scenarios involving zero-knowledge proofs (ZKP), trusted execution environments (TEE), and off-chain proofs, the instruction set architecture often needs to be "modeled into proof circuits," making the ISA’s verifiability, structural simplicity, standardization, and openness crucial attributes. A closed, complex, and ambiguous ISA is unsuitable as a long-term foundation for on-chain VMs.
1.2 The Role of Virtual Machines in Blockchain
In blockchain systems, the role of a virtual machine can be understood as the “CPU of a decentralized world.” Whether it's a contract deployed on Ethereum mainnet or a zkVM or MoveVM running on Rollups or AppChains, there is a shared fundamental question: how to determine code execution results within a globally consistent system.
Mainstream VM solutions include:
-
EVM (Ethereum Virtual Machine): A stack-based VM designed specifically for Ethereum, simple to operate and traceable;
-
WASM (WebAssembly): A general-purpose, high-performance VM standard driven by browsers and now adopted by multiple chains;
-
Move VM: Originating from the Libra project, emphasizing resource control and formal verification;
-
zkVM / RISC-V VM: Modeling execution as zk circuits or ISA execution models for efficient ZKP generation;
-
Solana BPF VM: A secure VM extended from Berkeley Packet Filter.
Despite architectural differences, these VMs face the same core challenge: how to unify “performance, verifiability, and cross-platform consistency” on-chain? On this front, the role of ISA becomes increasingly prominent—especially ISAs with modularity and open-source properties like RISC-V.
1.3 Why Focus on RISC-V: Openness, Lightweight, and Extensibility
Among various ISAs, RISC-V has rapidly risen in recent years because it addresses several longstanding issues:
-
Open-source and royalty-free: Avoids patent barriers and licensing risks, ideal for open-source chain projects and public tech stacks;
-
Simple instructions with clear semantics: Easy to model, formally verify, and convert into circuits;
-
Modular extensible design: Can build a VM using just a minimal subset (e.g., RV32I), or extend with SIMD, Crypto, and other instructions;
-
Vibrant ecosystem: Compiler toolchains like GCC/LLVM already offer full support; operating systems, simulators, and verification frameworks are steadily maturing;
-
Global neutrality: The foundation relocated outside the U.S., welcomed by regions including China and Europe, favorable for building international computing standards.
For blockchain, RISC-V offers a low-barrier, highly controllable execution platform capable of running on-chain contracts, embedding circuits for zk-proof generation, or executing sensitive logic in trusted hardware.
1.4 Objectives and Structure of This Article
This article systematically explores the potential of RISC-V in blockchain, particularly its value in VM architecture, execution environment design, and verifiable computing. We will proceed through the following sections:
-
About RISC-V: A brief introduction to the basic concepts of RISC-V;
-
The History of RISC-V: Tracing its evolution from academic origins to industrial adoption;
-
An Overview of RISC-V Instruction Set: Analyzing its modular instruction design and relevant subsets for VMs;
-
RISC-V Ecosystem and Development: Exploring current software/hardware support and community dynamics;
-
Applications in Blockchain Virtual Machines: Examining how major VMs integrate or could integrate with RISC-V;
-
Impact of Instruction Sets on VMs: Analyzing implementation complexity, performance, and circuit generation;
-
Implications of Ethereum's RISC-V Initiative: Reviewing proposed plans for an Ethereum RISC-V runtime;
-
Conclusion and Outlook: Summarizing possible pathways for RISC-V as a future on-chain execution platform.
In today’s rapidly evolving technological landscape with rising consensus costs, an open, universal, and verifiable-computing-oriented execution architecture may well be the “new infrastructure” urgently needed by blockchain systems. Whether RISC-V can fulfill this role will be explored step by step in this article.
2. About RISC-V
The core of modern computing systems lies in how the instruction set architecture (ISA) defines the interaction protocol between software and hardware. RISC-V represents a significant engineering effort to redesign and openly share this foundational layer. This chapter delves into the technical philosophy of RISC-V, its comparative advantages over mainstream ISAs, and the industrial significance of its “open ISA” status.
2.1 RISC Design Philosophy and Advantages of Simplified Instruction Sets
RISC-V is one of the representative architectures of Reduced Instruction Set Computing (RISC). The RISC design philosophy originated in the 1980s as a response to Complex Instruction Set Computers (CISC), based on the assumption that most programs use only a small number of simple instructions, with complex operations efficiently composed via compiler optimization.
Core principles of RISC architecture include:
-
Fixed-length instructions: Simplify decoding and execution logic, improving instruction throughput;
-
Register-centric: Most operations limited to registers, minimizing memory access;
-
Clear semantics with single-cycle execution: Reduces implementation complexity, beneficial for pipelining and out-of-order execution;
-
Compiler-friendly: Offloads complex instruction composition to compilers, enhancing hardware generality.
RISC-V inherits the above RISC principles and further emphasizes:
-
Modular design: Base instruction sets (e.g., RV32I) can be used independently, with advanced extensions like floating-point, vector, and compressed instructions added as needed;
-
Clean and formally modelable semantics: Especially suitable for integration into formal verification systems or zero-knowledge circuits;
-
Clear separation between user and privileged modes: Helps construct multi-level security environments and virtualization support;
-
Strong cross-platform consistency: Standardized instruction behavior avoids legacy baggage and undocumented features.
In short, RISC-V represents a “ground-up” attempt to reconstruct instruction sets, leveraging modern compilers, manufacturing processes, and system requirements to design a more open, simplified, and verifiable ISA.
2.2 Key Comparisons with x86, ARM, and Other ISAs
RISC-V's main competitors are the two dominant architectures in today's market: x86 and ARM, which lead in desktop/server and mobile/embedded markets respectively.
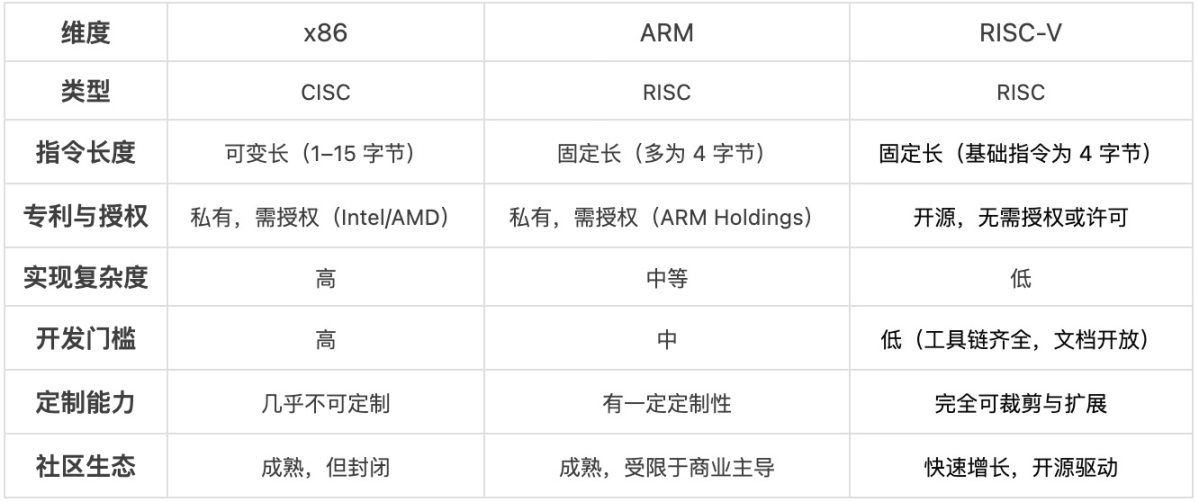
From a blockchain perspective, RISC-V holds natural advantages:
-
Simple structure, circuit-friendly: Highly suitable for systems requiring strong execution modeling such as zkVMs;
-
License freedom, no legal barriers: No concerns about patent disputes in execution environments, ideal for global deployment;
-
Highly customizable: Can build lightweight VMs using minimal instruction sets like RV32I;
-
Easy to implement: Simple to rebuild processors in Verilog or implement interpreters in software.
The complexity and closed nature of x86 make it unsuitable for modeling into on-chain environments; ARM, despite its technical strengths, faces severe licensing restrictions, making it difficult to serve as an “on-chain universal computing standard.” RISC-V, due to its openness, simplicity, and adaptability, emerges as a promising candidate for on-chain execution platforms.
2.3 Industrial Significance of Open-Source ISA
The most transformative aspect of RISC-V is its identity as an “open instruction set.” Similar to the open-source waves seen in operating systems, compilers, and databases, the open-sourcing of ISA is catalyzing a new round of hardware ecosystem restructuring.
Its industrial significance can be understood across several dimensions:
-
Avoids monopolies and lowers barriers: Small-to-medium chipmakers and national research institutions can legally develop compatible processors without paying high licensing fees;
-
Promotes innovation and differentiation: Allows enterprises to customize or extend ISAs according to business needs, enabling competitive differentiation beyond generic products;
-
Supply chain security: For nations and organizations prioritizing autonomy and control, RISC-V offers a more manageable software-hardware baseline;
-
Unified design of software and circuits: An open ISA facilitates co-optimization of hardware and software, especially in high-performance and verifiable computing domains;
-
Global collaboration platform: The RISC-V International Foundation brings together academia, industry, and open-source communities, serving as a bridge for cross-sector cooperation.
In blockchain, the benefits of this open architecture are even more pronounced. On-chain VMs require high transparency, customizability, and verifiability—requirements difficult to meet with traditional closed architectures. RISC-V provides foundational support for building “on-chain trusted hardware interfaces” and “provable computing layers.”
This chapter introduced the design philosophy behind RISC-V, its differences from mainstream ISAs, and the profound implications of its open-source identity. With these characteristics understood, the next chapter traces RISC-V’s historical development—from academic origin to global industrialization—laying solid groundwork for understanding its applicability in blockchain.
3. The History of RISC-V
The emergence of RISC-V was not accidental but the result of decades of accumulated reflection in computer architecture. Originating in academia, it quickly advanced to the forefront of industrial application. In emerging fields like blockchain, RISC-V’s “freedom to implement and customize designs” is gradually revealing far-reaching impacts. To better understand why it suits blockchain VMs and trusted computing, we must begin with its origins.
3.1 Origins at UC Berkeley
The RISC-V project began in 2010, initiated by the Computer Science Department at the University of California, Berkeley. It wasn’t the first “RISC” architecture—the concept of RISC itself was pioneered jointly by researchers at Berkeley and Stanford in the early 1980s, aiming to improve pipeline efficiency and reduce implementation cost through simplified instructions. Early notable RISC architectures included SPARC, MIPS, and PowerPC.
However, although widely studied in academia, these early architectures generally faced challenges such as “licensing restrictions,” closed designs, and commercial failures. By the 21st century, processor architectures had become dominated by the ARM-x86 duopoly, leaving academia struggling to find a truly open, modern, and extensible instruction set for teaching and research.
RISC-V emerged precisely under these conditions: designed from scratch to become an open, modular, and sustainably maintained general-purpose ISA, suitable both for education and industry. The “V” in its name stands for “fifth-generation Berkeley RISC design.”
3.2 The RISC-V Foundation and Open-Source Movement
As academic interest in RISC-V grew, more labs, researchers, and engineers began developing related toolchains and processor implementations. To coordinate standard evolution and promote industrialization, the RISC-V Foundation was officially established in 2015, with initial members including Google, NVIDIA, Western Digital, IBM, SiFive, and Berkeley.
The Foundation declared that RISC-V’s architectural specifications would be permanently open, license-free, and freely implementable, drawing massive attention in the commercial world. It became a rare “open-source infrastructure” in the processor domain, similar to Linux, LLVM, and OpenCL, offering businesses a controlled path avoiding patent lock-in.
In 2019, concerned about U.S. export control policies, the RISC-V Foundation relocated its headquarters to Switzerland, demonstrating its commitment to neutrality and global open collaboration. This move further enhanced its credibility and influence internationally.
The RISC-V open-source wave has also spurred numerous open-source cores (e.g., Rocket, BOOM, PicoRV, CV32E40P) and SoC projects (e.g., OpenPiton, OpenTitan, CHIPS Alliance), spanning embedded microcontrollers to data-center-grade processors.
3.3 Standardization Progress: From Base to Extension Modules
RISC-V’s architectural specification emphasizes “minimal starting point” and “composability.” Its standard evolution follows several levels:
-
Base integer instruction set: RV32I and RV64I, covering core instructions like logic, arithmetic, jumps, load/store;
-
Standard extension modules: M (multiply/divide), A (atomics), F/D (floating-point), C (compressed), V (vector), etc.;
-
Domain-specific extensions: T (trusted execution), P (DSP signal processing), Zks (zero-knowledge acceleration), currently in development;
-
Privilege level specifications: Defining Machine/Supervisor/User privilege levels, supporting OS and virtualization;
-
Debugging and binary interface: Debug protocols, ABI, calling conventions, etc.
This modular approach—breaking the ISA into independent components with separate versioning and flexible combination—grants exceptional freedom to software and hardware systems. Developers can tailor functionality to target platforms, greatly reducing chip design complexity and enabling co-evolution of hardware and software.
In blockchain systems, especially in resource-constrained or auditable execution-path VMs, this ability to precisely control system capabilities at the instruction level is particularly valuable.
3.4 Adoption by Enterprises and Academia
Since 2018, industrial applications of RISC-V have entered a period of rapid growth. Today, hundreds of companies and institutions have adopted or experimented with RISC-V, including:
-
Processor startups: SiFive, Tenstorrent, Esperanto, StarFive, focusing on high performance and low power;
-
Traditional semiconductor firms: Intel (investing in RISC-V startups), Qualcomm, Samsung, Microchip;
-
Storage and embedded sectors: Western Digital announced future chips will mostly be RISC-V based; ESP32-C series shifting to RISC-V;
-
OS and toolchain support: Full compatibility with Linux, Zephyr, FreeRTOS, Rust, GCC, LLVM;
-
Universities and research institutes: MIT, Tsinghua, Zhejiang University, ETH Zurich, IIT, widely using it in teaching and experiments;
Particularly in China, RISC-V has received strong policy and industrial support, leading to projects from Alibaba T-Head, CAS, and Zhongwei. Its open architecture is seen as a strategic choice to reduce dependence on foreign IP.
In blockchain, increasing numbers of teams are experimenting with RISC-V-based VMs or on-chain execution environments, such as:
-
ZKWasm + RISC-V: Compiling zkVM to RISC-V target architecture, leveraging ISA composability to compress circuit complexity;
-
Ethereum EVM Object Format (EOF) and RISC-V: Discussing conversion of EVM bytecode to RISC-V IR for improved efficiency;
-
OpenZKP + RISC-V: Embedding RISC-V compilation paths into ZKP circuits to boost proof and verification performance.
Summary
The history of RISC-V is a journey from academic inception to global industrial revolution. It is not only a challenge to closed architectures but also a victory of open-source thinking in computing platforms. For blockchain systems, RISC-V is more than just a processor architecture—it may become the foundational bedrock for future trusted computing, open VMs, and on-chain execution models.
4. Introduction to the RISC-V Instruction Set
As an open-source instruction set architecture (ISA), one of RISC-V’s core characteristics is simplification and modular design. These traits have made it popular in both academic and industrial circles, granting it inherent flexibility and adaptability—especially valuable in highly customized scenarios like blockchain VMs. This chapter systematically introduces the composition, extension modules, customization mechanisms, and potential value of the RISC-V instruction set for blockchain.
4.1 Base Instruction Set (RV32I / RV64I)
RISC-V begins with a minimal viable base—the so-called RV32I and RV64I, corresponding to 32-bit and 64-bit integer architectures. “I” stands for Integer, meaning integer operations, covering fundamental building blocks of program execution: arithmetic, logic, conditional branches, memory access, and jumps.
RV32I includes approximately 47 base instructions, encoded in fixed length—typically 32 bits—making instruction decoding logic simple and hardware implementation inexpensive. RV64I extends this with 64-bit integer support, suitable for higher-performance applications with larger memory addressing needs.
All RISC-V implementations must support a minimal subset—either RV32I or RV64I—providing a clear starting point for software and hardware developers.
4.2 Modular Extension Design
Unlike traditional closed ISAs, RISC-V uses a modular architecture allowing selective addition of functional modules atop the base instruction set. These modules are named with single letters and can be combined into complete ISA configurations. For example, RV64IMAC denotes a 64-bit architecture supporting integer multiply/divide (M), atomics (A), and compressed instructions (C).
Common extensions include:
M Extension (Integer Multiply/Divide)
The M extension adds hardware support for multiplication and division, especially significant for multi-precision integer operations. In blockchain contexts—such as hash computation and big integer operations—this capability offers tangible benefits.
A Extension (Atomic Operations)
The A extension provides atomic read-modify-write instructions like LR/SC (Load-Reserved/Store-Conditional), critical for implementing multithreaded synchronization and concurrent computing. This is especially important in on-chain multicore execution or trusted execution environments.
F/D Extension (Floating-Point Arithmetic)
The F extension supports single-precision floating-point operations; D supports double precision. While currently less used in mainstream blockchain VMs, they hold potential in economic modeling simulations and on-chain scientific computing.
C Extension (Compressed Instructions)
The C extension allows compressing some 32-bit instructions into 16-bit forms, significantly improving code density. This is crucial for memory-constrained embedded devices, edge nodes, or lightweight blockchain clients.
V Extension (Vector Computing)
The V extension gives RISC-V vector processing capabilities, supporting large-scale parallel data operations—ideal for cryptography and zero-knowledge proofs (ZKP). Similar to SIMD, the V extension shows great promise in elliptic curve operations, parallel hashing, and SNARK/ZK-STARK preprocessing.
4.3 Support for Custom Instructions
Another key feature of RISC-V is open extensibility. Users or enterprises can add custom instructions while maintaining compatibility with the standard ISA. This mechanism not only aids specialized hardware optimization but is also ideal for blockchain scenarios involving frequent calls to specific algorithms, such as:
-
BLS signature verification instructions (custom accelerators);
-
Hash instructions like SHA-256, Keccak;
-
Precompiled instruction sets for zero-knowledge proof circuits;
-
Instruction optimizations for proof-carrying code.
This way, developers can achieve hardware-software co-acceleration without breaking ecosystem unity.
4.4 Instruction Set Specifications and Version Control
RISC-V standards are defined and maintained by RISC-V International, using a modular version control system. Each extension module has its own independent version number, helping different vendors and developers maintain compatibility during implementation.
The current mainstream version is the 2.x series, such as RV64GC v2.2 (where G denotes a combination of general-purpose instructions: IMAFD). This structure facilitates version upgrades and enables flexible configuration tailoring for different application scenarios.
4.5 Toolchain and Debugging Ecosystem
Thanks to active open-source community development, RISC-V enjoys comprehensive toolchain support:
-
Compilers: GCC and LLVM/Clang provide full RISC-V support;
-
Simulators: Spike (official ISA reference model), QEMU (user/system-level simulation), Renode (hardware-cooperative simulation);
-
Debugging tools: GDB supports RISC-V debugging; OpenOCD and others support JTAG interfaces;
-
Language support: Rust compiler now supports RISC-V, facilitating secure, trustworthy execution environments on-chain.
These tools collectively form the infrastructure for building RISC-V blockchain VMs or hardware-software cooperative platforms.
Summary
With its simplification, modularity, extensibility, and open licensing, the RISC-V instruction set is gradually reshaping the landscape of underlying computing platforms. For blockchain systems seeking balanced security, determinism, flexibility, and performance, RISC-V opens new possibilities: not only can we design custom instruction sets for specific VMs, but we can also deeply integrate hardware with blockchain systems, innovating freely without licensing constraints. This may represent a crucial step in the evolution of blockchain computing paradigms.
5. RISC-V Ecosystem and Development
An ISA’s vitality depends not only on its technology but also on the surrounding ecosystem. As a relatively “young” ISA, RISC-V has developed a vast upstream-downstream system in under fifteen years since its formal proposal in 2010. This chapter comprehensively analyzes RISC-V’s ecosystem and development status from four perspectives: chip implementations, development toolchains, OS and simulator support, and international policy.
5.1 Current State of Chip and SoC Implementations
One of RISC-V’s greatest successes lies in its “speed of adoption.” Compared to the historically rich but closed x86 and ARM, RISC-V’s modular, open, and easy-to-implement nature has attracted numerous companies to processor design, accelerating the evolution from embedded SoCs to general-purpose processors.
Representative players in the chip and SoC space include:
-
SiFive (USA): Co-founded by Krste Asanović, one of RISC-V’s initiators, currently the most representative commercial RISC-V company. Has launched multiple 64-bit processor IPs (e.g., U7, U8 series) and participated in high-performance platform designs.
-
StarFive (China): Focused on open-source SoC chips and boards (e.g., VisionFive series), promoting RISC-V adoption in domestic embedded development and edge AI scenarios.
-
Alibaba T-Head (China): Launched multiple XuanTie series processors, widely deployed in IoT and edge applications, with partial IP implementations open-sourced to foster developer ecosystems.
-
Andes, Codasip, GreenWaves, etc.: Active in niche markets like IoT, audio recognition, and smart vision, showcasing RISC-V’s flexible adaptability.
In addition, startups like Esperanto (thousands of cores for AI acceleration), Tenstorrent, Vitesse, MetaX are building high-performance processors—even GPUs—based on RISC-V. Such vibrancy is extremely rare in the histories of x86 and ARM.
5.2 Development Toolchains: GCC, LLVM, QEMU, Rust Support
An ISA’s vitality largely depends on whether its toolchain support is complete. RISC-V has made significant progress here:
-
GCC support: Official GCC support began in 2015, now covering full RV32/RV64 instruction sets and mainstream extensions;
-
LLVM/Clang support: Enhanced continuously under initiatives by Google, SiFive, becoming the preferred compiler for modern systems and blockchain projects;
-
QEMU simulator: Supports user-mode and system-mode simulation of RISC-V, enabling quick validation of programs or OS;
-
Rust support: RISC-V is now officially part of the Rust compiler backend, supporting no_std mode and embedded development, with active community maintenance of multiple HAL crates;
-
Debugger support: Tools like GDB, OpenOCD, J-Link are widely adapted to RISC-V, supporting breakpoints, register monitoring, etc.;
-
Build systems and SDKs: PlatformIO, Yocto, Zephyr SDK, etc. all support RISC-V, enabling direct construction of embedded systems or custom images.
The completeness of these tools allows developers to seamlessly integrate RISC-V into existing workflows—a critical advantage for migrating blockchain VMs or launching on-chain WASM/zkVM projects.
5.3 Operating System and Simulator Support
From bare-metal execution to full-featured OS, RISC-V is gradually establishing comprehensive operational environment support:
-
Linux: Mainline kernel has supported RISC-V since 2018; general distributions like Debian, Fedora, Arch Linux are now available;
-
Embedded RTOS: Zephyr, FreeRTOS, NuttX, RT-Thread all offer RISC-V ports, widely used in low-power devices;
-
Simulation and verification tools:
-
Spike: Golden reference simulator from UC Berkeley, supporting RV32/RV64 user and privilege modes;
-
FireSim: Open-source full-system FPGA-based simulation platform capable of running Linux and conducting microarchitectural performance tests;
-
Renode: Programmable simulation environment supporting multiple architectures, suitable for building virtual blockchain testnets;
-
gem5: Partially supports RISC-V, useful for architecture research;
-
Verilator: For RTL verification, compatible with RISC-V soft cores like PicoRV, VexRiscv.
These simulators and system supports provide strong backing for VM development, on-chain verification logic, and cross-architecture testing.
5.4 RISC-V Internationalization and Policy Support (Especially in China)
As an open standard, RISC-V has received high attention and support from governments and industry organizations worldwide:
-
RISC-V International: Registered in Switzerland, uniting 300+ members to drive standard evolution and international collaboration;
-
European RISC-V Strategy: EU views RISC-V as central to its “digital sovereignty,” funding multiple high-performance open-source SoC projects;
-
U.S. DARPA and NASA: Support research on verifiable chip platforms based on RISC-V;
-
China’s policy focus and strategic layout:
• MIIT and local governments promoting “open-source alternatives”;
• Universities and research institutions (e.g., CAS, Tsinghua) actively participating in RISC-V standardization;
• Dozens of domestic companies (Alibaba, BLUESKYCHIP, T-Head, Zillionics, etc.) investing continuously in chip design and IP ecosystems;
• Local development boards (e.g., VisionFive, Milk-V) accelerating domestic developer ecosystem formation;
• China RISC-V Industry Alliance (CRVA) bridging technology and commercialization.
China has become a global hub for RISC-V development, ranking among the top globally in scale and activity.
This chapter comprehensively demonstrated RISC-V’s ecosystem prosperity—from chip implementation and toolchain maturity to OS support and global policy-industry dynamics. For blockchain systems, this ecosystem completeness means: on-chain VMs can rapidly deploy using existing software-hardware ecosystems, rather than fighting a lonely “from-zero” battle.
6. Applications in Blockchain Virtual Machines
Virtual machines are foundational infrastructure in modern blockchain systems, analogous to runtime environments in traditional operating systems—they execute smart contracts, process user-submitted transactions, and ensure verifiability, determinism, and security of on-chain code. The choice and design of a VM not only shape developer experience but also profoundly impact chain execution efficiency and scalability.
This chapter discusses blockchain platforms’ requirements for VMs, reviews current mainstream VM architectures, introduces RISC-V’s emerging role, and analyzes representative pioneering practices.
6.1 Requirements for VMs in Blockchain Platforms
Unlike traditional computing platforms, blockchain VMs operate in a distributed, trustless, and auditable execution environment. This context leads to several distinct requirements:
-
Determinism: Identical inputs must produce identical outputs on any node, ensuring consensus consistency;
-
Security: Prevent malicious contracts from abusing system resources, guarding against buffer overflows, infinite loops, etc.;
-
Resource metering (Gas system): Enable fine-grained resource consumption tracking to limit execution time, memory usage, etc.;
-
Performance and scalability: Maximize execution efficiency without sacrificing determinism, supporting more complex business logic;
-
Auditability and verifiability: Support on- or off-chain execution tracing for auditing and dispute resolution.
The VM’s underlying design—including its chosen instruction set—directly determines the implementation cost and capability boundaries of these features.
6.2 Overview of Current Mainstream VMs
In actual blockchain platforms, current mainstream VM systems include:
1. EVM (Ethereum Virtual Machine)
• Native VM of Ethereum, based on a 256-bit stack architecture;
• Advantages: Simple, mature, robust tooling ecosystem;
• Disadvantages: Poor performance, instruction semantics mismatched with modern CPUs,不利于parallel execution and optimization.
2. WASM (WebAssembly)
• Proposed by W3C, originally for browsers, now gaining popularity across multi-chain platforms;
• Representative platforms: Polkadot, NEAR, Cosmos (CosmWasm);
• Advantages: Close to modern hardware, fine-grained instructions, good performance;
• Disadvantages: Not designed for on-chain use, requires additional implementation for resource metering and sandbox isolation.
3. Move VM
• Resource-oriented language and VM proposed by Libra/Diem (now Aptos/Sui);
• Features: Based on linear types, ensures non-duplicability and safe transfer of resources;
• Targets high-security smart asset logic, though adaptation to on-chain execution still needs optimization.
Beyond these, VMs like Solana’s BPF VM, FuelVM, and zkVM focus on high-performance or zero-knowledge proof scenarios. But a common issue is that most do not directly design or bind to a low-level hardware ISA.
This raises a new question: What new possibilities arise if a lightweight, verifiable real instruction set were directly used to build on-chain VMs?
6.3 RISC-V’s Role in VMs: Host Platform or Guest Architecture?
RISC-V’s introduction offers two complementary entry points for blockchain VM architecture design:
1. As a host platform (Host ISA)
• Blockchain nodes run directly on RISC-V processors (e.g., RISC-V SBCs), while VMs continue using EVM/WASM;
• Benefits include deployment of lightweight nodes, offline wallets, or trusted execution environments (TEE);
• Typical use cases: hardware wallets, IoT blockchain terminals, etc.
2. As a guest architecture (Guest ISA)
• Use RISC-V as the target ISA for VM execution—i.e., compile smart contracts into RISC-V instructions for on-chain execution;
• This design can reuse existing compiler toolchains (e.g., GCC, LLVM), simplifying multi-language contract deployment;
• Determinism and security achieved by restricting instruction sets, introducing gas models, and sandboxing.
The latter is the most watched innovation direction recently, blurring the boundary between software VMs and real CPUs by introducing “hardware-level instruction sets” into virtual execution environments.
6.4 Precedents Using RISC-V as a Blockchain VM Instruction Set
The following projects represent current efforts using RISC-V in blockchain VMs or on-chain execution models:
1. Cartesi
• Pioneered the use of a “RISC-V Linux VM” as a smart contract execution environment;
• Developers can write contracts using standard Linux toolchains, greatly enhancing programming freedom;
• VM implemented via RISC-V user-mode simulation, combined with on-chain verification to ensure determinism.
2. Sonic (proposed by Fuel Labs)
• Proposes building a “RISC-V zero-knowledge VM” as the execution engine for zk-rollups;
• Compiles contract logic into RISC-V instructions, then generates STARK proofs for high-performance off-chain execution + on-chain verification;
• Advantages: hardware proximity, cross-language compilation compatibility, and verifiability.
3. Polyjuice (Godwoken)
• Not fully based on RISC-V, but runs on CKB-VM whose original design was inspired by RISC-V;
• Offers EVM compatibility, combining RISC-V-style resource models for seamless integration with Nervos Layer 1.
4. Golem
• Decentralized computing platform supporting multiple task architectures;
• New versions considering RISC-V as a standardized runtime ISA to enhance task portability and lightness;
• Particularly suitable for heterogeneous devices (e.g., mobile, embedded) joining computation tasks.
The consensus among these projects is: RISC-V’s open-source, modular, and verifiable characteristics are well-suited for the high-security, high-constraint on-chain execution environment.
RISC-V’s emergence in blockchain VMs isn’t blind replacement of traditional architectures, but an opportunity to rethink “trusted computing.” In the following chapters, we will analyze how RISC-V’s instruction set affects VM implementation and performance, and examine its strategic significance and future potential from an Ethereum perspective.
7. Impact of Instruction Sets on Virtual Machines
A VM’s underlying execution model relies heavily on instruction set support. The ISA not only determines contract execution efficiency but also profoundly influences the VM’s implementation complexity, scalability, execution security, and even ecological sustainability. In blockchain environments—where determinism and resource management are extremely sensitive—ISA selection is particularly critical.
This chapter examines four core dimensions to explore how different ISAs affect VM design and deployment, further evaluating RISC-V’s unique advantages.
7.1 Implementation Difficulty: Custom vs. General-Purpose Architectures
In VM design, one approach is a fully custom instruction set, such as Ethereum’s EVM; another is reusing existing general-purpose ISAs like WASM or RISC-V.
Pros and cons of custom instruction sets:
•Advantages: Structurally simple, tailored for blockchain (e.g., EVM’s 256-bit word operations);
•Disadvantages: Cannot reuse existing compilers/toolchains, closed ecosystem, high maintenance cost;
•High debugging difficulty: Lacks ready-made debuggers, simulators, or performance analysis tools.
General-purpose ISAs offer the following advantages:
• Direct reuse of mature toolchains (e.g., LLVM, GCC, GDB, QEMU);
• Broad multi-language compiler support (C, C++, Rust, Go, Zig);
• Easier integration of standard sandboxing and OS-level isolation.
RISC-V, as an open general-purpose ISA, is more suitable for embedding into VM systems than traditional x86/ARM due to its extreme simplicity—reducing implementation and maintenance difficulty while retaining toolchain maturity.
7.2 Performance: Execution Acceleration vs. Decoding Complexity
An ISA’s structure determines decoding and execution efficiency, affecting overall VM performance.
• EVM, designed as a bytecode stack machine, has a simple execution model but is hard to optimize; modern processors struggle to efficiently execute its 256-bit stack operations;
• WASM, closer to register architectures, better utilizes modern CPU pipelines and SIMD instructions, achieving high execution efficiency;
• RISC-V emphasizes pipeline-friendliness and low-overhead decoding paths from the start; its fixed-length instructions (mostly 32-bit) enable fast parsing, translation, or JIT compilation, suitable for high-performance scenarios;
• Compiling contracts directly to RISC-V instructions can significantly boost execution speed and allow native hardware acceleration (e.g., FPGA/ASIC).
Additionally, optional RISC-V extensions (e.g., vector, compressed instructions) allow further performance improvements while maintaining compatibility.
7.3 Scalability: How Modular ISAs Help Support New Features
Another critical issue in VM architecture is scalability—whether it can painlessly support new languages, type systems, or resource models in the future.
One of RISC-V’s core strengths is its modular design: beyond base instruction sets (RV32I/RV64I), it allows standardized extensions (M/A/F/D/V) or custom instructions:
• Blockchain platforms can build minimal VMs based on RV32I, enabling only essential instructions to reduce attack surface;
• For specific scenarios (e.g., zkVM, AI computing), hardware vector extensions or custom arithmetic instructions can be introduced to create specialized VMs;
• Custom instructions, when paired with gas mechanisms, can still maintain resource meterability and determinism.
In contrast, extending EVM/WASM typically relies on bytecode-layer modifications or version switches, which are costly and weak in compatibility.
7.4 Security and Verifiability: Deterministic Execution and Sandboxing Strategies
Security is paramount in blockchain VMs—and closely tied to ISA characteristics.
Determinism: Blockchains require identical outputs from any node given identical inputs; any behavior dependent on platform, time, or hardware state risks breaking consensus.
• EVM is inherently deterministic, but often introduces non-deterministic risks when interfacing with platforms (JIT, floating-point, time calls);
• WASM natively allows non-deterministic behaviors (e.g., NaN representations, threads), requiring additional restrictions;
• RISC-V, as a contract execution ISA, can naturally support deterministic control by explicitly restricting floating-point/system instructions and enforcing sandbox execution.
Sandboxing and Formal Verification:
• RISC-V’s transparent, clean specifications are conducive to formal modeling and execution path verification;
• Projects like Cartesi and Sonic build VMs on RISC-V, enabling off-chain execution and on-chain generation of verifiable proofs;
• This opens new paths for “provable execution”: not only are smart contract results trustworthy, but their entire execution process can be zero-knowledge verified.
In summary, RISC-V’s transparency and controllability give it advantages in security and auditability.
Summary:
A suitable instruction set can greatly expand a VM’s design space and execution efficiency. As an open, simple, customizable general-purpose ISA, RISC-V shows high adaptability in blockchain VM architectures. It reduces implementation costs, enables future expansion via modularity, enhances on-chain trustworthiness through verifiable execution, and is emerging as a potential core for a new class of VM architectures.
8. Implications of Ethereum’s RISC-V Initiative
Ethereum, as one of the most influential smart contract platforms globally, keeps VM architecture at the heart of its technical evolution. From early EVM to eWASM and current Layer 2 explorations, the Ethereum community consistently pursues higher performance, stronger security, and broader language support. Throughout this process, RISC-V—as an open, verifiable, modular instruction set architecture—has been incorporated into experimental paths of multiple projects.
This chapter reviews the Ethereum community’s evolutionary attempts in VMs, especially those related to RISC-V and their implications.
8.1 ewasm and Early RISC-V VM Experiments
Around 2018, the Ethereum Foundation launched the ewasm (Ethereum-flavored WebAssembly) project, aiming to replace EVM with WASM for better language support and execution efficiency. However, ewasm ultimately failed to fully replace EVM, mainly due to:
•WASM itself wasn’t designed for deterministic environments, requiring extensive restrictions;
• Security sandbox models were overly complex, increasing node execution and verification burden;
• Poor compatibility with blockchain VM gas models.
During ewasm experimentation, developers proposed using RISC-V as the VM’s underlying ISA, arguing that:
• RISC-V ISA better fits “deterministic execution” models;
• Facilitates static analysis and gas metering;
• Open architecture helps build lightweight, specialized VMs.
Though these early ideas weren’t adopted into the mainline, they inspired later Layer 2 and verifiable computing projects.
8.2 Exploration in Rollup Technologies
With the rise of Layer 2 technologies, the Ethereum ecosystem split into two main directions: Optimistic Rollups and ZK Rollups. Both execute smart contract logic off-chain, submitting only results and proofs to the main chain, drastically reducing costs.
RISC-V’s role in Rollup scenarios mainly appears in:
• Fraud proofs in Optimistic Rollups: Simulate contract execution using RISC-V, validating disputed executions on-chain (e.g., Cartesi);
•Circuit generation in ZK Rollups: Convert RISC-V programs into proof circuits to generate STARK/SNARK proofs, enhancing contract verifiability (e.g., RISC Zero);
These designs share a common trait: using RISC-V as a unified instruction layer to bridge on- and off-chain execution, with formal modeling and zero-knowledge verification capabilities.
8.3 Design and Deployment of Cartesi Machine
Cartesi is the most representative RISC-V VM project in the Ethereum ecosystem. Its core is the Cartesi Machine execution environment, using precisely simulated RISC-V architecture to balance performance and security via off-chain execution and on-chain validation.
Key features of Cartesi include:
•Full Linux system support: Enables native development in Rust, C, C++, offering better dev experience than traditional contract development;
•Deterministic execution: Sandboxes Linux calls, file systems, etc., ensuring consistent results across nodes;
•Interactive fraud proofs: Secures safety by on-chain validation of RISC-V step-by-step simulation;
•Already deployed multiple DApps, including games, data markets, AI inference services.
Cartesi is not just a VM, but an exploration of a “Layer 2 operating system” merging general computing with blockchain environments.
8.4 Implications for Ethereum and Layer 2 Evolution
Open ISAs like RISC-V unleash enormous potential in Rollups and verifiable computing:
•Shift from contract language to computational architecture abstraction: Moving beyond Solidity/EVM, building VMs based on hardware instructions;
•Promotion of verifiable computing models: Off-chain execution with on-chain validation naturally suits precisely defined instruction sets;
•Reduced on-chain cost and complexity: Develop using general RISC-V toolchains; on-chain only verifies or schedules key steps;
•Facilitating heterogeneous development of “app-specific chains (AppChains)”: Each chain can customize its VM while sharing a common verification layer.
In the longer term, Ethereum’s exploration of RISC-V prompts us to reconsider the foundational design of smart contract platforms: Can we build a new paradigm where “instruction set is the platform”?
Summary:
RISC-V’s application in Ethereum and Layer 2 scenarios demonstrates its unique advantages in deterministic computing, verifiability, and developer experience. Though not yet a mainnet standard, it plays a key role in multiple subsystems and projects, influencing future approaches to VM and blockchain system design.
9. Challenges and Future Outlook
RISC-V’s potential in blockchain is evident, but widespread adoption still faces many challenges. Overcoming these and driving deeper integration between RISC-V and blockchain technology will be key to future technical development. Meanwhile, RISC-V shows unique promise in future on-chain computing paradigms—especially in conjunction with zero-knowledge proofs, decentralization, and open-source chips.
This chapter discusses RISC-V’s challenges in blockchain and outlines future technical trends and potential applications.
9.1 Compatibility Issues with Existing Ecosystems (EVM/WASM vs RISC-V)
Existing blockchain ecosystems, especially Ethereum, are deeply entrenched in EVM and WASM as smart contract execution environments. While these technologies enjoy strong ecosystem support and compatibility, they also face performance bottlenecks, scalability limits, and security challenges. Introducing a new ISA like RISC-V inevitably raises compatibility issues:
• Transition in languages and toolchains: EVM and WASM already have mature developer tools, debuggers, IDEs, etc. Although RISC-V has strong toolchain support (e.g., GCC, LLVM), rapid adoption in existing blockchain development workflows requires overcoming technical hurdles in language support and compiler toolchains.
• Smart contract migration: Existing blockchain smart contracts are typically optimized for EVM or WASM. Migrating them to RISC-V without rewriting large amounts of code or compromising compatibility is a pressing issue.
• Multi-layer support: To ensure smooth transition of on-chain apps, blockchain networks might need to simultaneously support multiple VMs (e.g., EVM, WASM, RISC-V), increasing node complexity and maintenance costs.
These challenges require gradual community-led transitions, balancing compatibility and innovation for a smooth ecosystem evolution.
9.2 Balancing Performance, Security, and Decentralization
One core characteristic of blockchain technology is decentralization, demanding high fault tolerance and transparency. On this foundation, balancing performance and security is critically important.
•Conflict between performance and decentralization: Transaction throughput and TPS in modern blockchains are often constrained by VM execution efficiency. RISC-V offers lightweight, scalable architecture to optimize VM speed, but performance gains may compromise decentralization, e.g., hardware-accelerated VMs could create dependency on a few high-performance hardware vendors.
•Trade-off between security and performance: Introducing dedicated instruction sets or hardware accelerators in RISC-V can boost performance but increases node security risks and verification complexity. For example, how to ensure hardware acceleration doesn’t introduce unverified vulnerabilities, or how to guarantee secure sandboxing to prevent attack vectors via RISC-V extensions.
•Decentralization vs. hardware dependency: Adding hardware acceleration or custom chips may increase centralization risk, especially under heavy reliance on specific hardware (e.g., dedicated RISC-V chips). Preserving the core principle of decentralization remains a critical consideration.
Therefore, balancing these three aspects—achieving efficiency and security while preserving decentralization—is a key challenge for RISC-V’s future blockchain applications.
9.3 Convergence Trend of Open-Source Chips + Blockchain
As blockchain technology evolves, deep integration of hardware and software becomes an important future trend. RISC-V, as an open-source ISA, is leading this transformation.
• Proliferation of open-source chips: As an open ISA, RISC-V not only provides a research platform for academia but also flexible, customizable opportunities for hardware manufacturers. More hardware makers (e.g., SiFive, StarFive) are releasing open-source RISC-V chips, finding applications in IoT, smart terminals, and increasingly in blockchain.
• Integration of blockchain with specialized hardware: In the future, blockchain networks may combine with specialized open-source hardware devices to form dedicated blockchain nodes or mining equipment. This hardware-software fusion could improve network efficiency and lower hardware development barriers, enabling more participants to join the blockchain ecosystem at low cost.
9.4 Potential in Zero-Knowledge Proofs (ZK-RISC-V?)
Zero-knowledge proofs (ZK Proofs) are key technologies enhancing privacy and scalability in blockchain. They allow proving correctness of computations without revealing data—crucial for privacy-preserving applications (e.g., privacy coins, private smart contracts).
RISC-V’s potential in ZK proofs lies in:
•Precise control over computation: RISC-V’s simple, efficient ISA is ideal for building verifiable ZK proof circuits, especially when hardware-supported ZK-RISC-V circuits accelerate proof generation and verification.
•Reduced computational overhead: Traditional ZK proofs demand substantial resources; RISC-V can improve proof efficiency through simplified instructions and dedicated hardware, lowering computational burden on blockchain networks.
•Composable ZK-RISC-V circuits: Combining RISC-V’s ISA with ZK technology enables composable ZK-RISC-V circuits, unlocking complex applications like cross-chain transactions and privacy-preserving smart contracts.
Thus, ZK-RISC-V, as a novel integration of blockchain and ZK proofs, could become a vital technical pillar for future DeFi and privacy-preserving domains.
9.5 Impact on Future On-Chain Computing Paradigms
RISC-V’s emergence may drive a transformation in on-chain computing paradigms:
•From VMs to hardware support: RISC-V’s openness and hardware-friendliness offer a new computing architecture—not limited to VM simulation, but integrating hardware resources into dedicated computing networks.
•Popularization of decentralized hardware: Blockchain’s decentralization ethos may push hardware toward decentralization, with more open-source hardware projects joining the ecosystem, greatly lowering entry barriers and costs.
•A new era of smart contracts integrated with hardware: Contract execution no longer confined to traditional VMs, but accelerated directly via hardware—leveraging RISC-V’s ISA advantages to boost efficiency and security.
In the future, RISC-V’s role in blockchain may extend beyond smart contract execution, potentially becoming part of the entire blockchain infrastructure, enabling more efficient, flexible, and secure on-chain computing.
Summary:
While RISC-V faces challenges in ecosystem compatibility and balancing performance with security, it unlocks boundless possibilities for future blockchain technology. As hardware and blockchain further converge, RISC-V may play an increasingly important role—especially in zero-knowledge proofs and specialized hardware—offering immense potential. Facing these challenges and opportunities, RISC-V could not only enhance blockchain performance and security but possibly transform the entire on-chain computing paradigm.
To conclude, our discussion has covered RISC-V’s applications and future outlook in blockchain, highlighting its enormous potential as an innovative technology in cryptocurrency, smart contracts, and Layer 2 solutions.
References
[1] Full text of the long-term L1 execution layer proposal suggesting replacing EVM with RISC-V: https://d.foresightnews.pro/article/detail/82938
[2] Awesome ZKVM: https://github.com/rkdud007/awesome-zkvm
Disclaimer
This article was compiled and summarized with assistance from ChatGPT. The entire text has been reviewed and proofread solely by the author. If there are inaccuracies or omissions regarding technical implementations or product descriptions, readers are welcome to point them out—your feedback is appreciated.
This article aims to provide technical education and discussion on RISC-V and its applications in blockchain, and does not constitute any investment advice. Readers should independently research any blockchain-related projects, technologies, or products mentioned herein. The author assumes no responsibility for any consequences arising from the use of this content.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News