
Security Insights Behind the $1.4 Billion Heist
TechFlow Selected TechFlow Selected

Security Insights Behind the $1.4 Billion Heist
The golden age of the Web3.0 world should not be a hackers' carnival.
By Certik
Recently, Jason Jiang, Chief Business Officer of CertiK, appeared on Cointelegraph's podcast "The Agenda," discussing Web3.0 security in depth following the Bybit incident. When $1.4 billion in assets vanished overnight, it shocked not only the industry but every user concerned about digital asset safety. This wasn't just the largest theft in crypto history—it also exposed hidden risks lurking beneath the sector’s rapid growth.
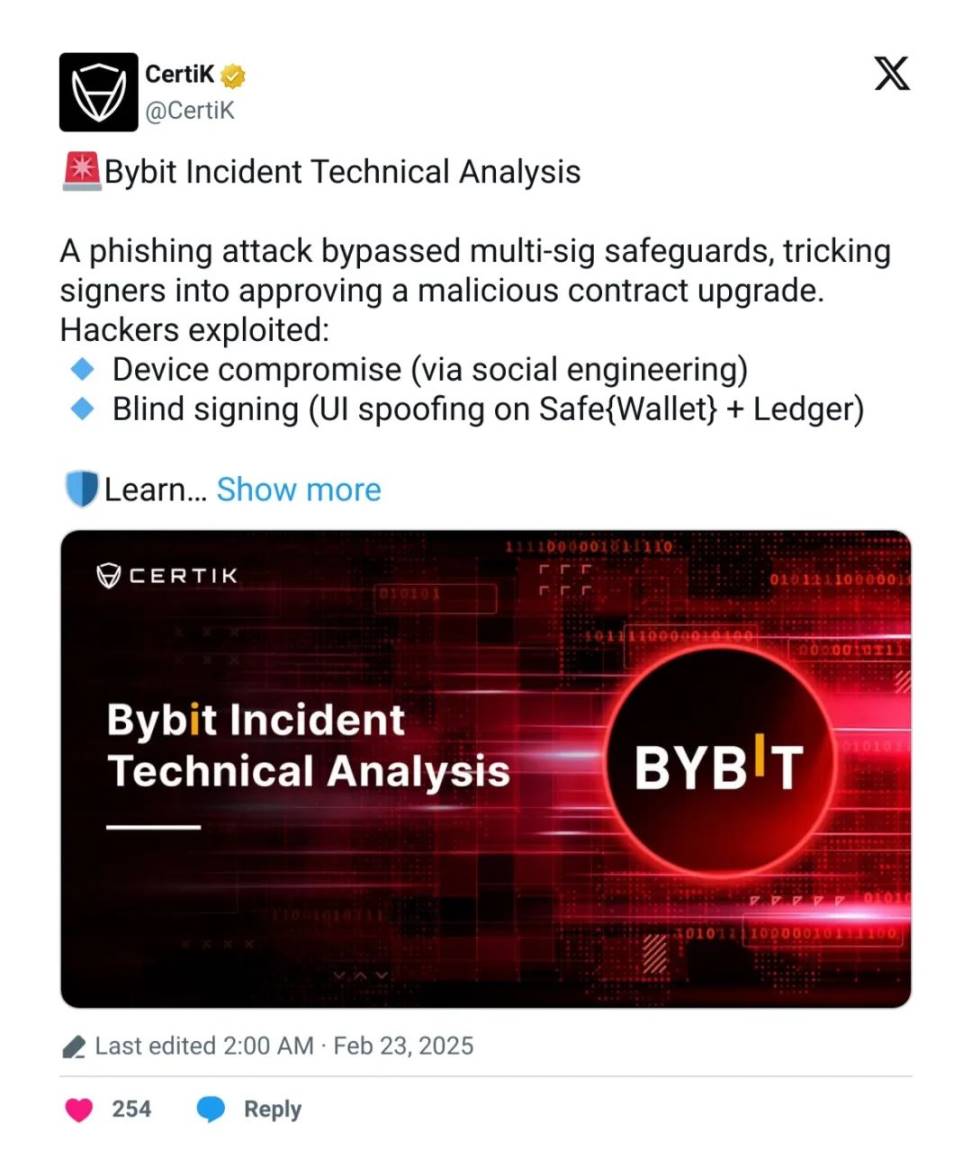
As a leader in blockchain security, CertiK has never stopped analyzing such threats. After the Bybit incident, CertiK quickly conducted technical analysis and highlighted the existence of the “blind signing” issue. In the discussion, Jason explained the causes of blind signing and advised users to verify transaction addresses at least three times.
When THORChain validators refused to roll back transactions, Jason bluntly stated, “We’re like in the Wild West,” while emphasizing that only by embracing regulation can the Web3.0 industry mature. Faced with billion-dollar cyberattacks, a mere $4,000 bug bounty feels insignificant—highlighting the urgent need for the industry to address its underinvestment in security. After all, the golden age of Web3.0 should not be a hacker’s carnival.
After Bybit’s $1.4 Billion Hack, CertiK Executive Explains How to Enhance Crypto Asset Security
In February this year, the hacker attack on Bybit sent shockwaves through the industry. According to reports, the North Korean hacking group Lazarus stole Ethereum-related tokens worth $1.4 billion from the centralized exchange, making it the most costly cryptocurrency heist in history.
The aftermath of this attack raised many questions: Where did things go wrong? Is my money safe? What measures can be taken to prevent similar incidents in the future?
Data from blockchain security firm CertiK shows that this massive theft accounted for approximately 92% of all losses in February. As a result, total crypto losses in February surged nearly 1,500% compared to January.
In Episode 57 of Cointelegraph’s “The Agenda” podcast, hosts Jonathan DeYoung and Ray Salmond spoke with CertiK Chief Business Officer Jason Jiang, diving into how the Bybit hack unfolded, the consequences of the exploit, and what steps users and exchanges can take to secure their cryptocurrencies.
Are crypto wallets still safe after the Bybit breach?
In short, Jason believes the Lazarus group was able to successfully carry out the large-scale attack on Bybit because they managed to compromise the devices of all signers—three individuals managing the multi-signature SafeWallet used by Bybit. The group then tricked them into signing malicious transactions they believed were legitimate.
Does this mean SafeWallet is no longer trustworthy? Jason says it's not that simple. "If the developer's computer at Safe was hacked, there might have been more information leaked from that machine. But I think for individual users, the likelihood of such an event is extremely low."
He noted that ordinary users can significantly improve their cryptocurrency security through several methods, including storing assets in cold wallets and being vigilant against potential phishing attacks on social media.
When asked whether hardware wallets like Ledger or Trezor could be exploited in a similar way, Jason again said the risk for average users is minimal—as long as they perform due diligence and remain cautious during transactions.
"One reason this incident occurred is that the signers blindly approved transaction instructions without seeing the full address," he added. "Always make sure the address you're sending to is exactly the one you intend to send to—especially for large transactions, double and triple check."
"I believe the industry will attempt self-correction and improvement after this event, pushing for greater transparency and recognizability in the signing process. Of course, there are many other lessons to learn, but this is certainly one of them."
How to Prevent the Next Billion-Dollar Exchange Hack?
Jason pointed out that the lack of comprehensive regulation and security safeguards may have contributed to the escalation of this hack. Previously, some validators of the cross-chain protocol THORChain refused to roll back or block Lazarus Group’s use of the protocol to convert stolen funds into Bitcoin, further fueling debate over decentralization boundaries.
"Welcome to the Wild West," Jason said. "That's the reality we’re living in right now."
"In our view, if cryptocurrency is going to thrive, it needs to embrace regulation," he said. "To gain broader acceptance, we must proactively engage with regulators and find ways to enhance industry security."
Jason praised Bybit CEO Ben Zhou for his response following the incident, but also noted that Bybit’s bug bounty program, launched before the hack, offered only a $4,000 reward. While most cybersecurity professionals aren’t solely motivated by money, increasing bounty amounts would still help exchanges maintain higher security standards.
When asked how exchanges and protocols can incentivize and retain top talent to safeguard their systems, Jason observed that security engineers don’t always receive the recognition they deserve.
"Many people think top-tier talent goes to development roles because that’s where they get the most rewards," he said. "But it also comes down to whether we value security engineers enough. They carry immense responsibility."
"Help reduce their stress and give them more recognition and incentives. Whether through financial rewards or honors, offer fair compensation within our means."
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















