
Russian service provider Aeza Group behind hackers, dark web, and drug markets sanctioned
TechFlow Selected TechFlow Selected

Russian service provider Aeza Group behind hackers, dark web, and drug markets sanctioned
Analyze the background and operational model of Aeza Group, and combine insights from blockchain anti-money laundering and tracking tool MistTrack to reconstruct its role within the criminal ecosystem.
Authors: Lisa&Liz
Editor: Liz
Background
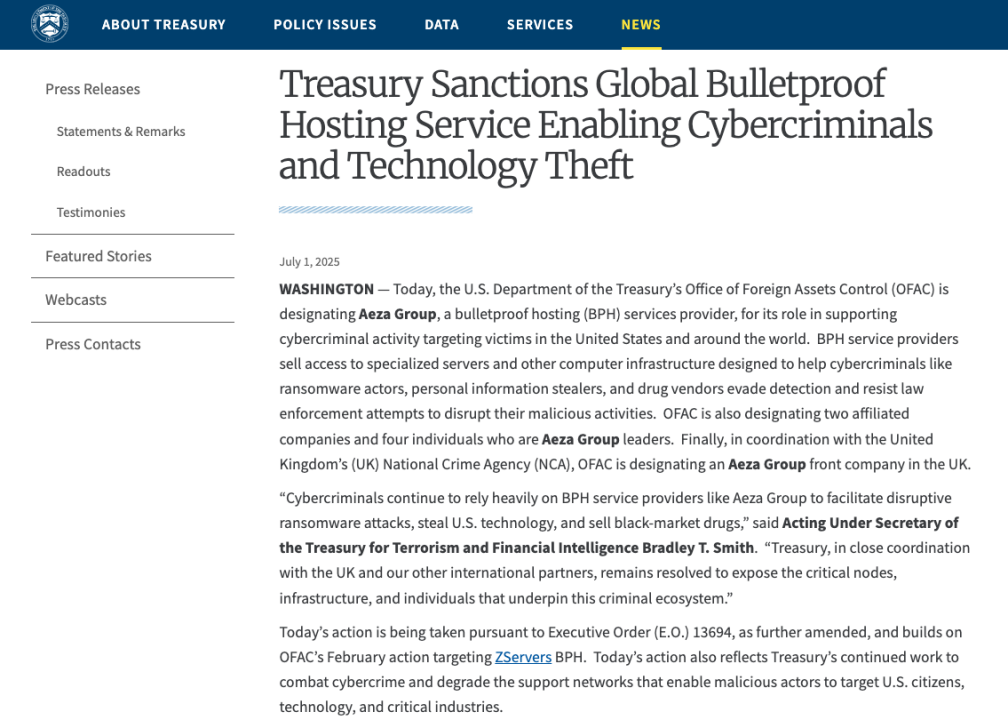
Recently, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) announced sanctions on Russia-based Aeza Group and its affiliated entities for providing hosting services to ransomware and information-stealing tools.
(https://home.treasury.gov/news/press-releases/sb0185)
The sanctions cover Aeza Group, its UK front company Aeza International Ltd., two Russian subsidiaries (Aeza Logistic LLC and Cloud Solutions LLC), four executives (CEO Arsenii Penzev, Director Yurii Bozoyan, Technical Director Vladimir Gast, and manager Igor Knyazev), and one cryptocurrency wallet (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F).
"Cybercriminals continue to heavily rely on bulletproof hosting providers like Aeza Group to launch destructive ransomware attacks, steal American technology, and sell illicit drugs on black markets," said Bradley T. Smith, Acting Under Secretary for Terrorism and Financial Intelligence at the U.S. Department of the Treasury. "The Treasury will continue working closely with the United Kingdom and other international partners to steadfastly expose critical nodes, infrastructure, and individuals underpinning this criminal ecosystem."
This sanctioning marks a shift in focus by international law enforcement from targeting attackers directly to dismantling their underlying technical infrastructure and service providers. This article outlines the background and operational model of Aeza Group and uses chain analysis from anti-money laundering and tracking tool MistTrack to reconstruct its role within the criminal ecosystem.
Who is Aeza Group?
(https://www.pcmag.com/news/us-sanctions-russian-web-hosting-provider-aeza-for-fueling-malware)
Aeza Group is a Saint Petersburg, Russia-based bulletproof hosting (BPH) provider that has long supplied dedicated servers and anonymous hosting services to ransomware groups, infostealer operators, and illegal drug trading platforms.
Its clients include notorious infostealer operators such as Lumma and Meduza, which have previously attacked U.S. defense industrial base organizations and global tech companies; ransomware and data theft groups BianLian and RedLine; and Russia’s prominent darknet drug marketplace Blacksprut. Aeza not only hosted Blacksprut but also participated in building its technical architecture. According to OFAC, Blacksprut has been widely used for the global distribution of fentanyl and other synthetic drugs, posing a serious threat to public safety.
MistTrack Analysis
According to analysis by blockchain anti-money laundering and tracking platform MistTrack, the sanctioned address (TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F) has been active since 2023 and has received over $350,000 in USDT to date.
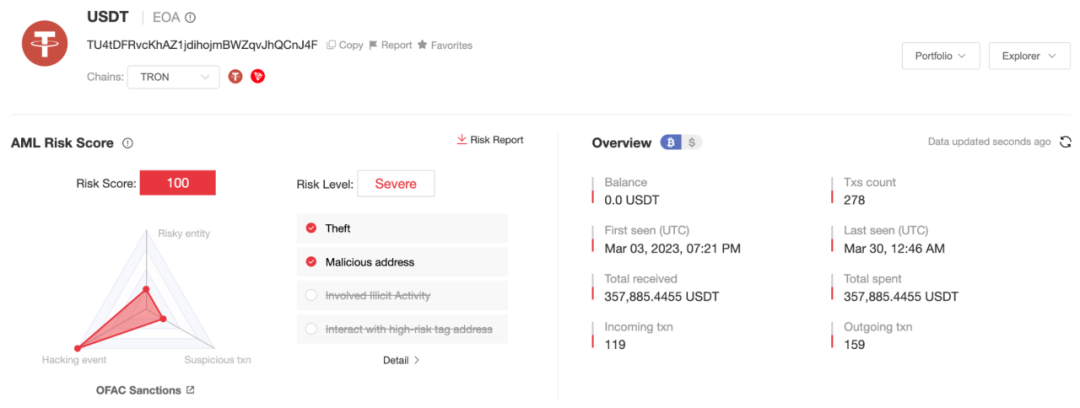
MistTrack analysis shows that this address has interacted with the following:
-
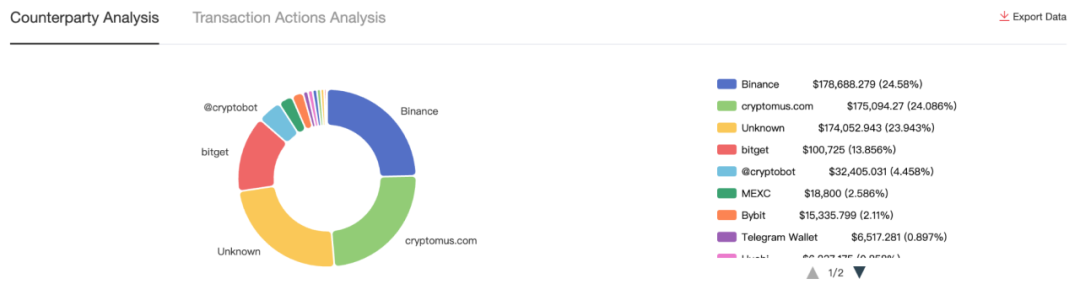
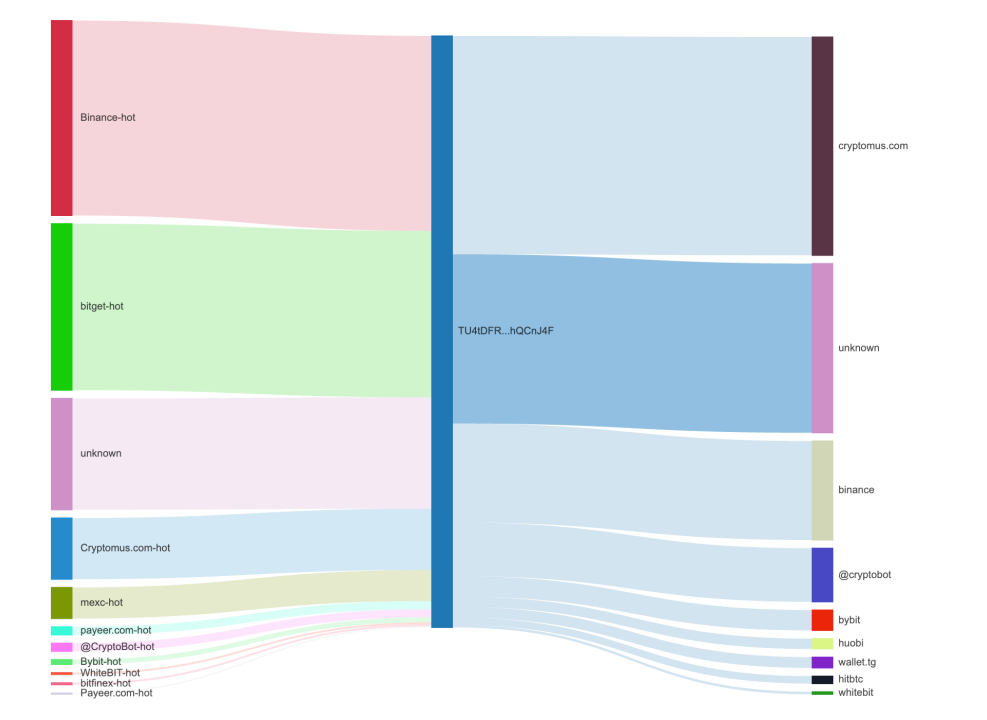
Sent funds to multiple well-known exchanges/OTC platforms such as Cryptomus and WhiteBIT for money laundering;
-
Linked to previously sanctioned entities including Garantex and Lumma;
-
Connected to Telegram-promoted Stealer-as-a-Service (StaaS) platforms;
-
Associated with addresses linked to the darknet drug market Blacksprut.
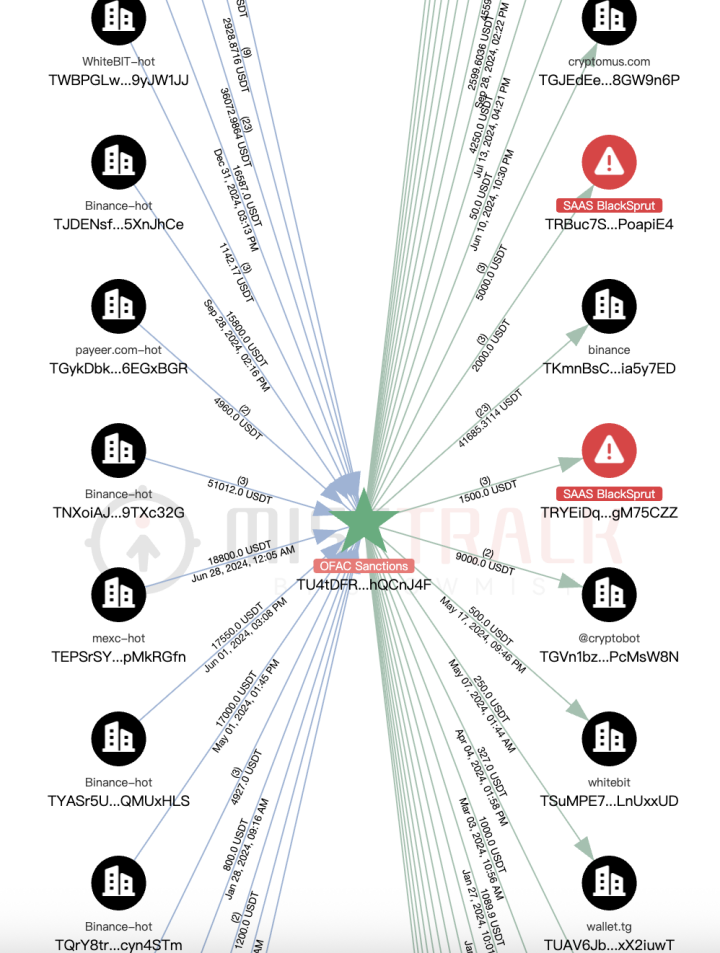
Based on MistTrack's counterparty transaction analysis, the breakdown of counterparties interacting with this address is as follows:
In addition, we found that Aeza's Telegram channel remained active on July 2, when administrators posted backup URLs in case users could not access the main site:
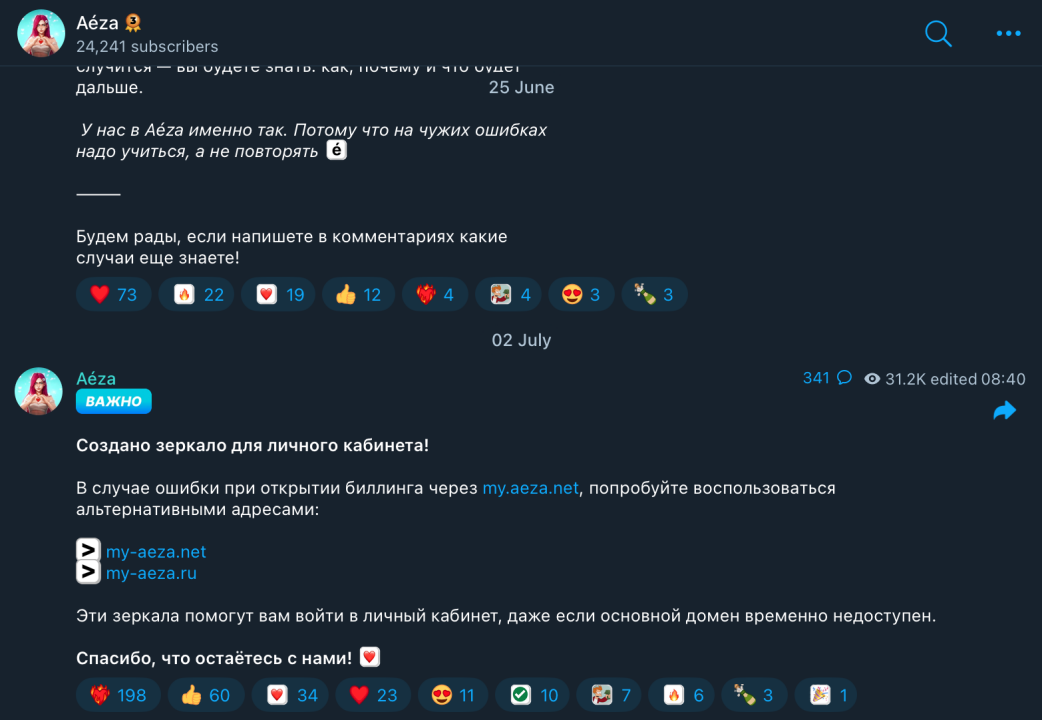
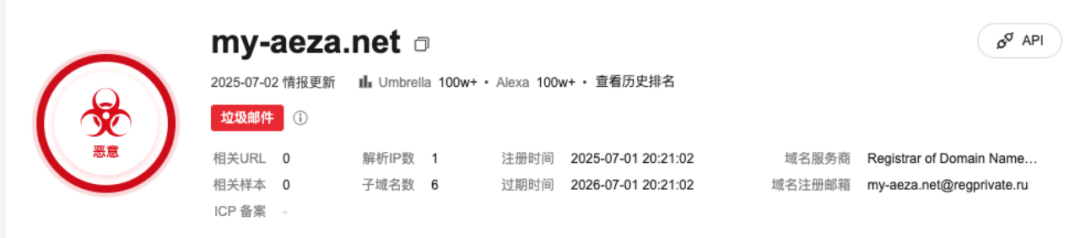
Upon investigation, it was discovered that these two backup URLs were created on the same day OFAC announced sanctions against Aeza.
Conclusion
The sanctions against Aeza Group signal that global regulators are expanding their enforcement scope from direct cyber attackers to the technical service networks supporting them. Hosting providers, anonymous communication tools, and payment channels are becoming new focal points for compliance actions. For enterprises, exchanges, and service providers, KYC/KYT is no longer an optional measure—engaging in business relationships with high-risk entities could result in secondary sanctions risks.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News
















