Understanding the Rugpull Scheme Behind the $15 Million Loss
TechFlow Selected TechFlow Selected

Understanding the Rugpull Scheme Behind the $15 Million Loss
Stop stepping on landmines.
Author: Ada
TenArmor and GoPlus possess powerful Rugpull detection systems. Recently, the two have joined forces to conduct in-depth risk analysis and case studies on the growing severity of Rugpull incidents, revealing the latest tactics and trends in Rugpull attacks and providing users with effective security protection recommendations.
Rugpull Incident Statistics
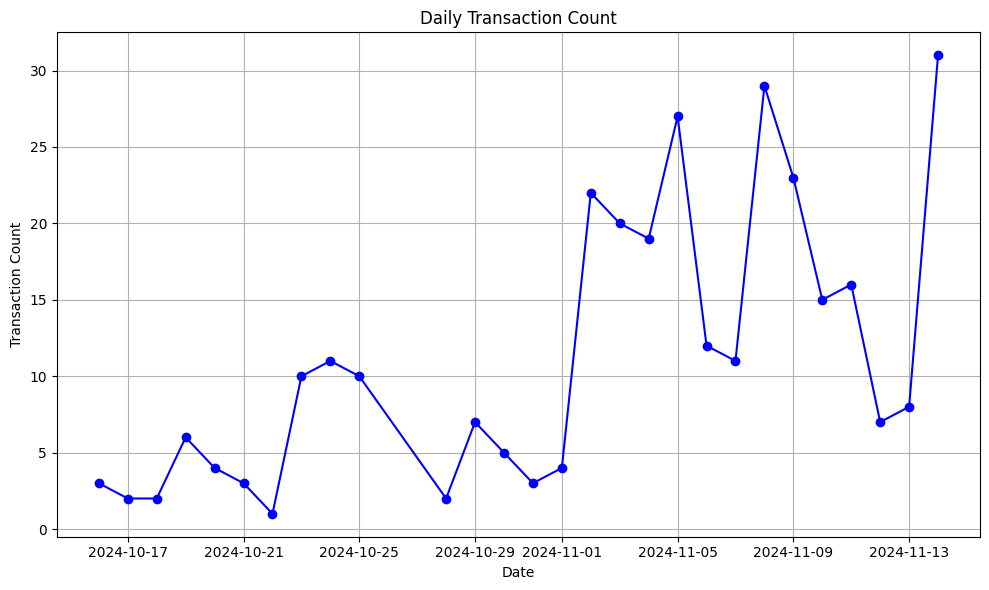
TenArmor's detection system identifies a large number of Rugpull incidents daily. Reviewing data from the past month, Rugpull incidents are on an upward trend—especially on November 14, when as many as 31 Rugpull events occurred in a single day. We believe it is necessary to expose this phenomenon to the community.
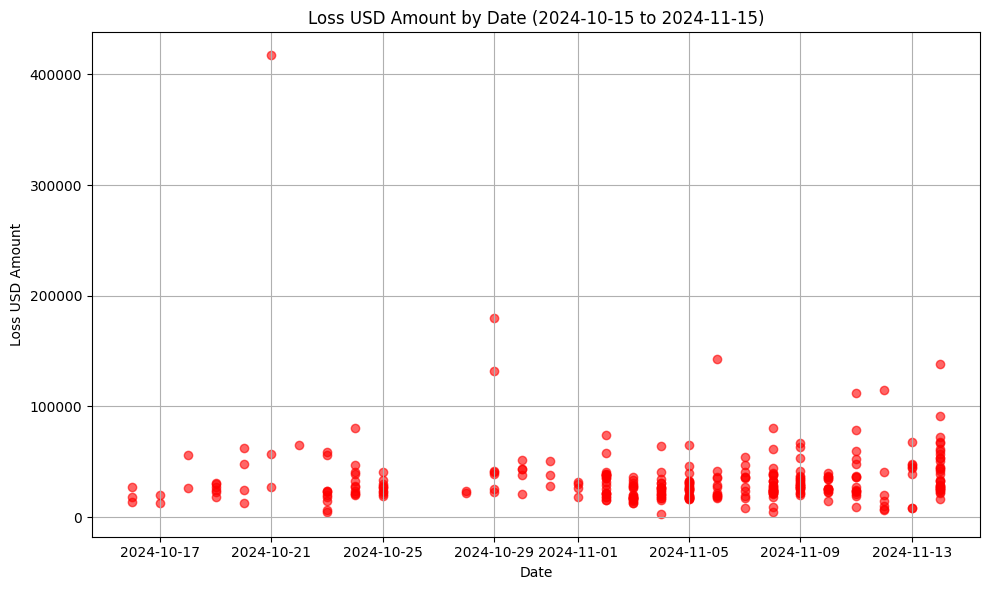
The financial losses from these Rugpull incidents mostly fall within the 0–100K range, with cumulative losses reaching $15 million.
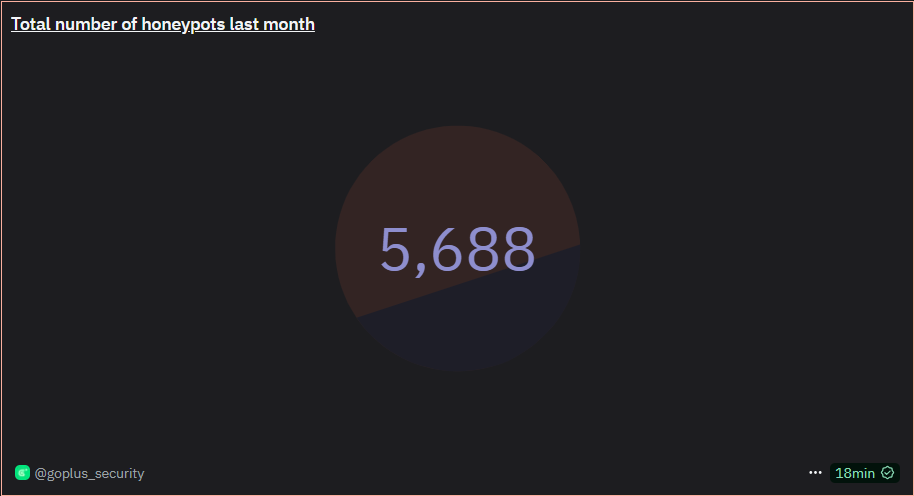
The most typical form of Rugpull in the Web3 space is the "Pixon" scam (a type of honeypot token). GoPlus’s Token Security Detection Tool can identify whether a token is a Pixon scam. Over the past month, GoPlus has detected 5,688 such Pixon tokens. For more security-related data, visit GoPlus’s data dashboard on DUNE.
TL;DR
Based on current characteristics of Rugpull incidents, we summarize the key preventive measures below:
1. Avoid blindly following trends. When purchasing popular tokens, verify that the token address is genuine to prevent falling for counterfeit tokens and scams.
2. Conduct due diligence when participating in new launches ("fair launches"). Check whether early trading volume originates from addresses linked to the contract deployer. If so, it may indicate a scam—avoid such projects.
3. Review the contract source code, especially the implementation of transfer/transferFrom functions, to ensure normal buying and selling capabilities. Avoid contracts with obfuscated code.
4. Before investing, examine the holder distribution. Avoid tokens where holdings are heavily concentrated in a few addresses.
5. Investigate the funding sources of the contract creator. Trace back up to 10 hops if possible to determine whether funds originate from suspicious exchanges.
6. Follow TenArmor’s early warnings to minimize losses. TenArmor has the capability to detect scam tokens in advance. Follow TenArmor’s X account for real-time alerts.
7. The TenTrace system has accumulated scam/phishing/exploit address databases from multiple platforms and can effectively identify inflows and outflows of blacklisted funds. TenArmor is committed to improving community security and welcomes collaboration with interested partners.
Characteristics of RugPull Incidents
Through extensive analysis of Rugpull incidents, we have identified the following recent patterns.
Impersonating Well-Known Tokens
Since November 1, TenArmor’s detection system has identified five Rugpull incidents impersonating the PNUT token. According to this post, PNUT launched on November 1 and surged 161x within seven days, capturing investor attention. The timing of PNUT’s rise aligns closely with when scammers began impersonating it, indicating that fraudsters exploit popularity to lure unsuspecting investors.
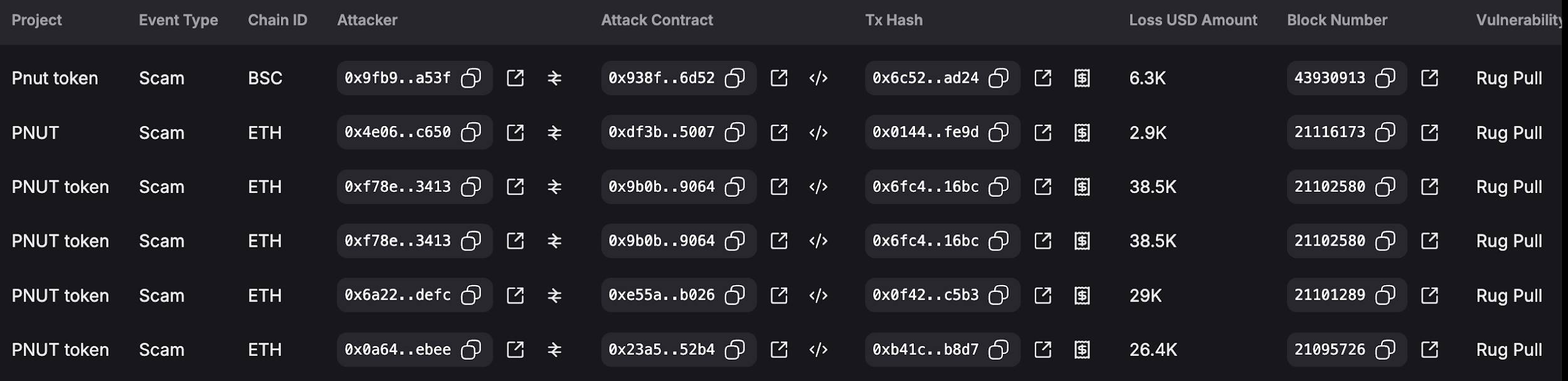
These PNUT-impersonating Rugpulls have collectively defrauded victims of 103.1K USD. TenArmor reminds users not to follow trends blindly—always verify the authenticity of a token’s address before purchasing.
Targeting New-Token Launch Bots
New token or project launches often attract significant market interest. During initial trading, prices can fluctuate drastically—even between seconds—making speed crucial for profit. Trading bots far surpass human traders in speed and responsiveness, making them highly popular for launching into new markets.
However, scammers have also recognized the prevalence of launch bots and now set traps specifically designed to catch them. For example, since October 2024, the address 0xC757349c0787F087b4a2565Cd49318af2DE0d0d7 has initiated over 200 scam campaigns, each completing from contract deployment to rugpull within just a few hours.
Take this recent scam incident as an example: the attacker first used 0xCd93 to create the FLIGHT token and then established a FLIGHT/ETH liquidity pair.
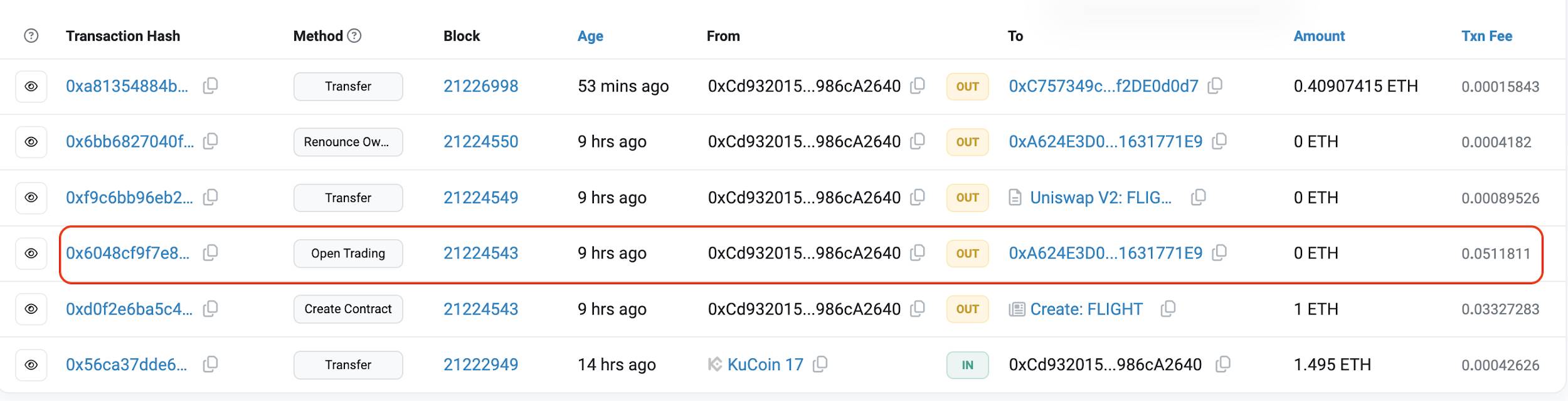
Immediately after the trading pair was created, numerous Banana Gun launch bot transactions appeared, exchanging small amounts for tokens. Further analysis reveals these bots were controlled by the scammer to fabricate trading volume.
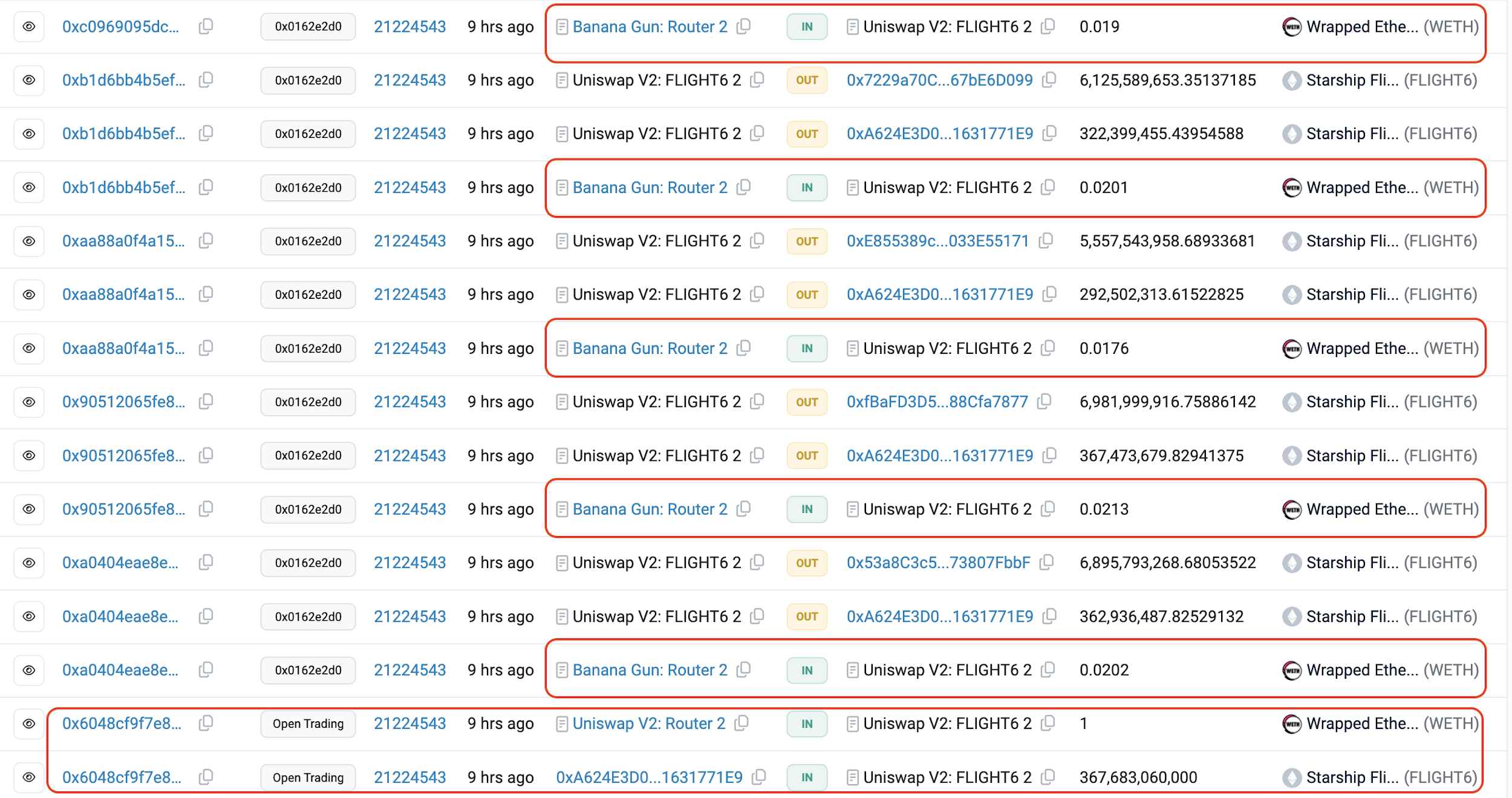
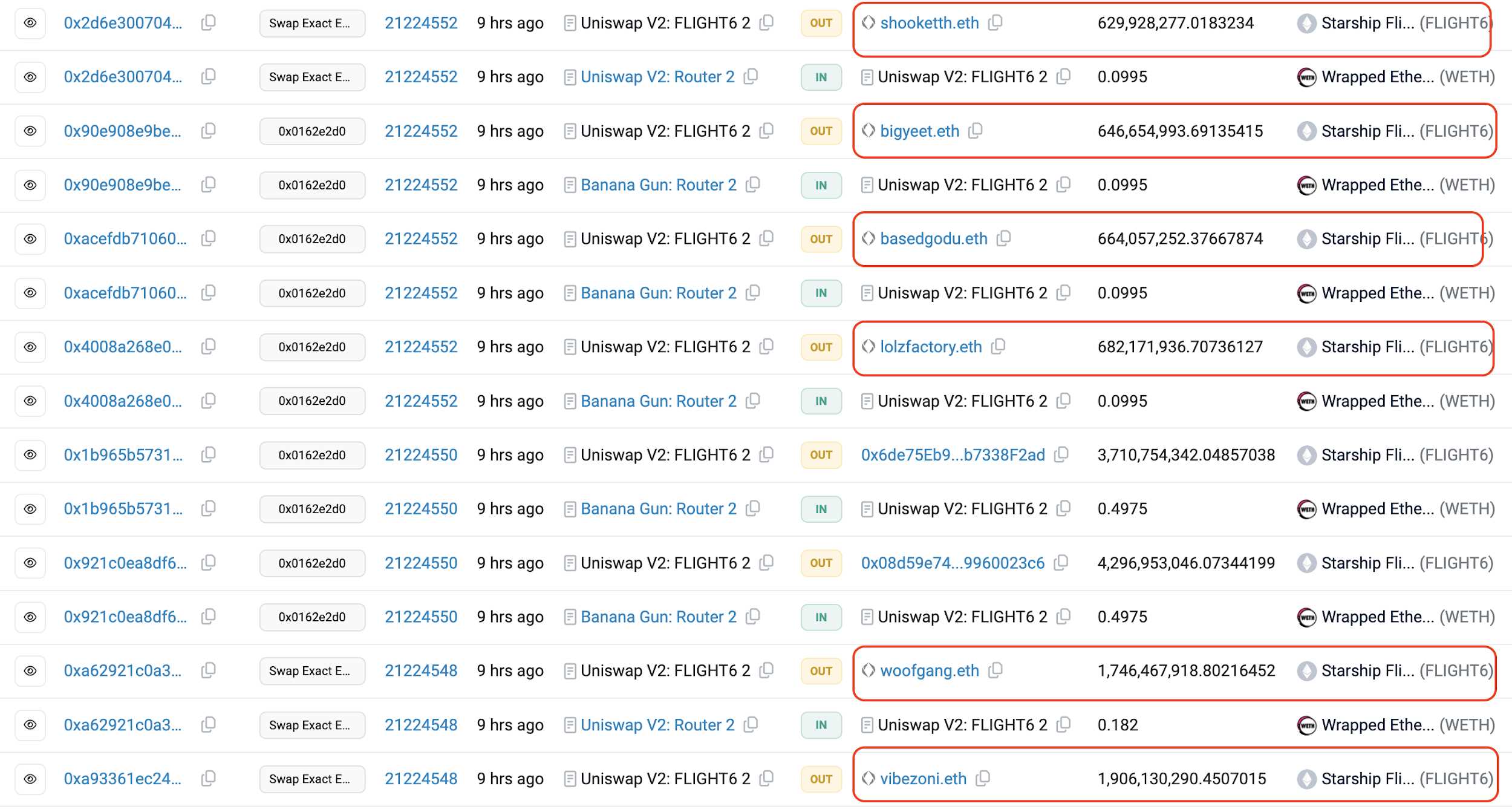
After about 50 small transactions created artificial traffic, real investors were attracted—many using Banana Gun launch bots themselves.
After trading continued for some time, the scammer deployed a dedicated Rugpull contract funded from address 0xC757. Just 1 hour and 42 minutes later, they executed the rugpull, draining the entire liquidity pool and profiting 27 ETH.
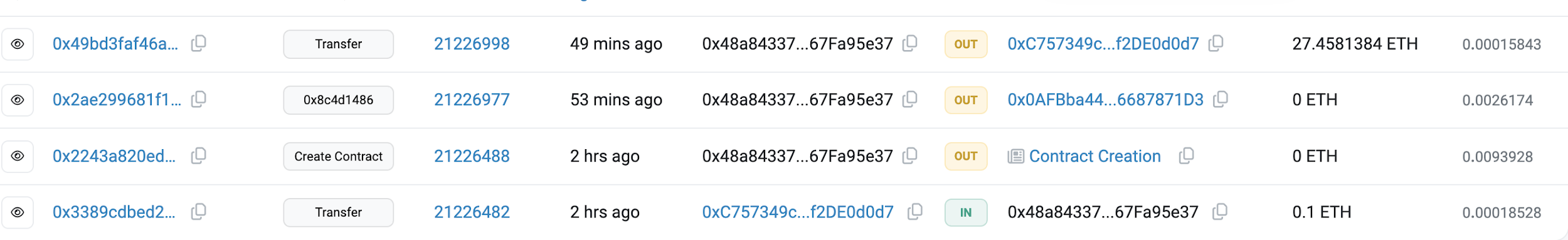
Analyzing this method reveals a clear pattern: the scammer generates fake volume via micro-transactions to attract launch bots, then executes the rug once sufficient liquidity is drawn in. While launch bots offer speed advantages, users must remain vigilant against such scams. Always perform due diligence—check whether early volume comes from deployer-linked addresses—and avoid suspicious launches.
Hidden Code Manipulations
Tax on Transactions
The image below shows the transfer function code of the FLIGHT token. It clearly deviates significantly from standard implementations. Each transfer incurs conditional taxes, severely restricting both buying and selling—a strong indicator of a scam token.
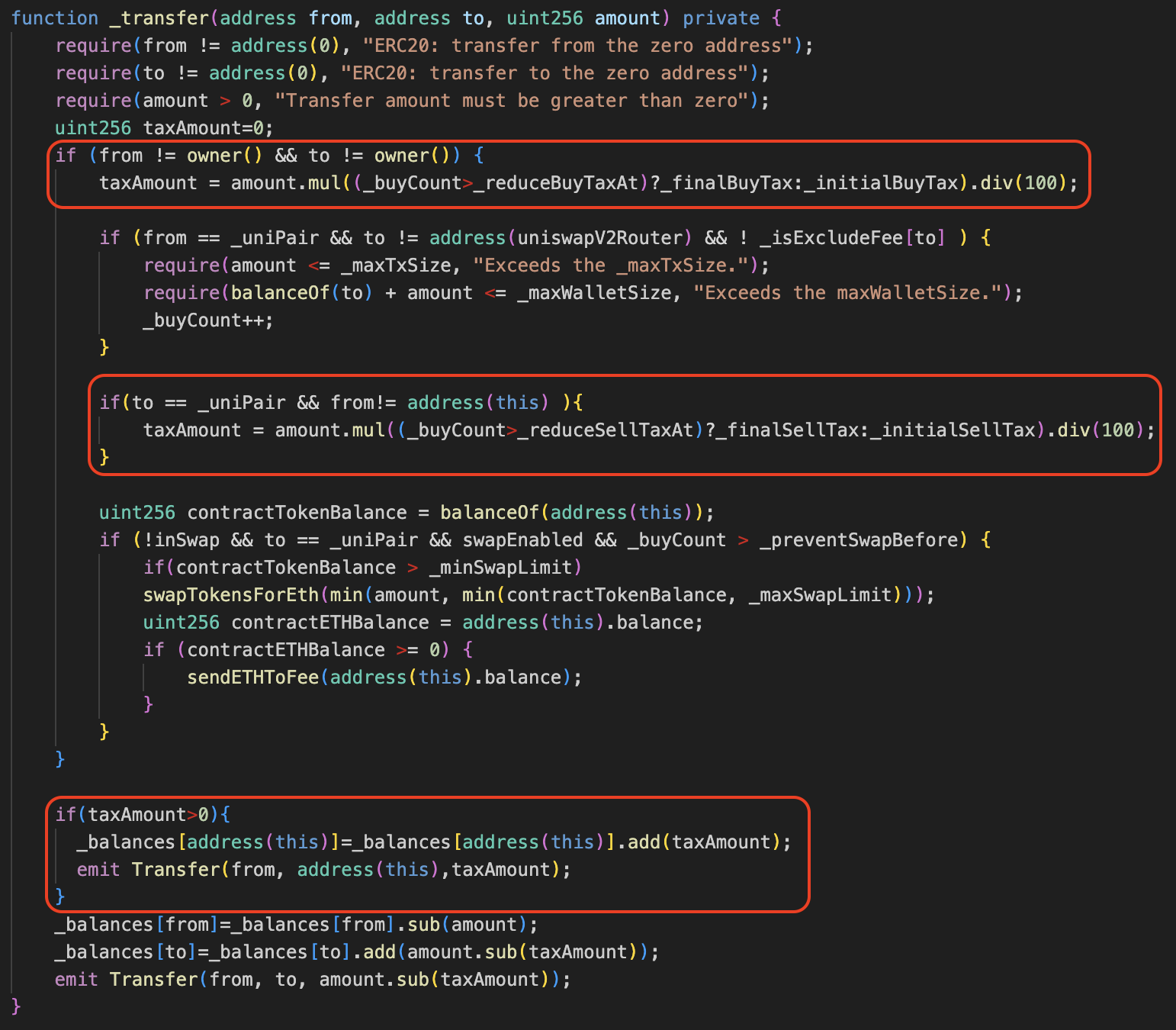
In such cases, simply reviewing the token’s source code allows users to spot red flags and avoid traps.
Code Obfuscation
As mentioned in TenArmor’s latest review of major Rug Pull incidents, some scammers deliberately obfuscate their source code to obscure malicious intent and reduce readability. Encountering such code should be a clear signal to stay away.
Blatant rugApproved Functions
Among the many Rugpull incidents detected by TenArmor, some are brazenly obvious. For instance, this transaction explicitly declares its malicious intent.
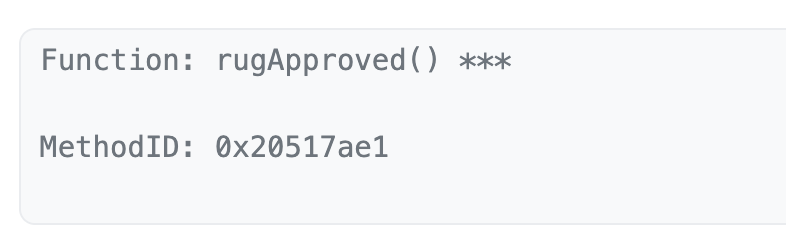
There is typically a time window between the deployment of a Rugpull contract and the actual execution—around three hours in this case. To guard against such attacks, follow TenArmor’s X account for timely alerts about high-risk contract deployments, enabling users to withdraw funds promptly.
In addition, functions like rescueEth and recoverStuckETH are commonly used for Rugpulls. While presence alone doesn’t confirm a scam, they should raise suspicion when combined with other warning signs.
Concentrated Holders
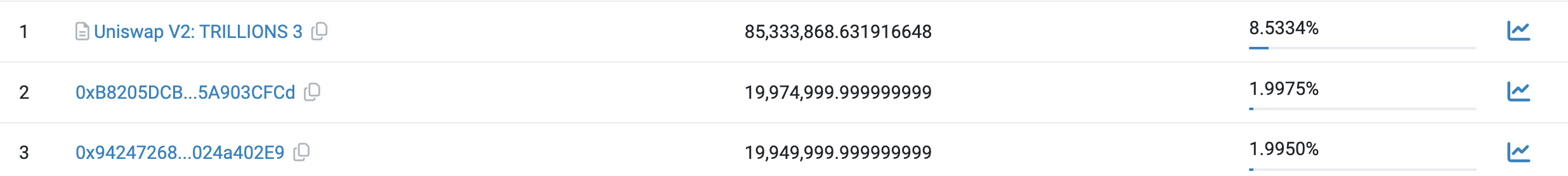
In recent Rugpull incidents detected by TenArmor, token holder distributions exhibit distinctive patterns. We randomly selected three affected tokens to examine their holder distribution:
0x5b226bdc6b625910961bdaa72befa059be829dbf5d4470adabd7e3108a32cc1a
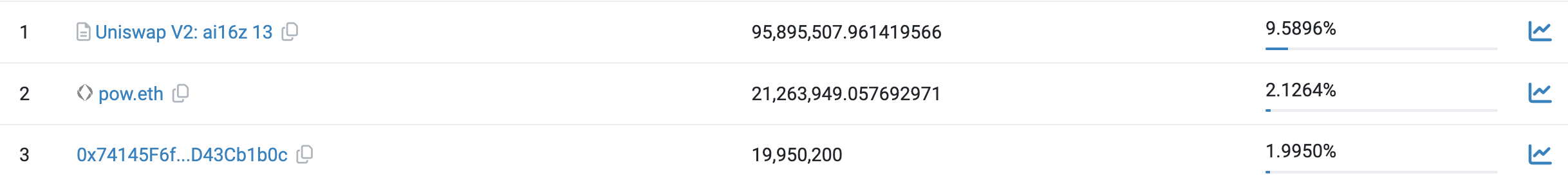
0x9841cba0af59a9622df4c0e95f68a369f32fbdf6cabc73757e7e1d2762e37115
0x8339e5ff85402f24f35ccf3b7b32221c408680421f34e1be1007c0de31b95f23
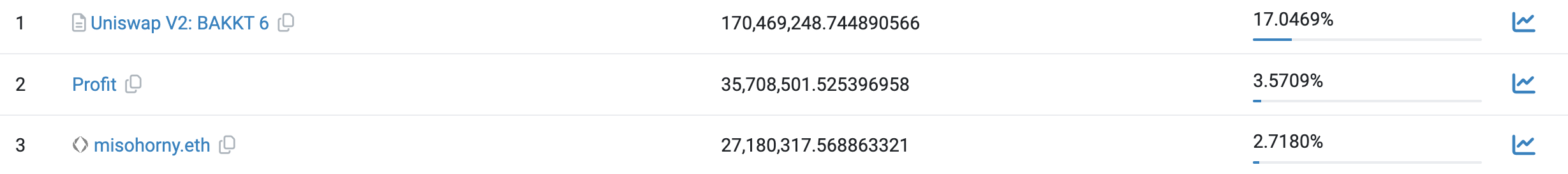
In all three cases, Uniswap V2 pairs dominate as top holders, holding overwhelmingly large shares. TenArmor warns users: if you notice a token’s holdings are heavily concentrated in a single address—such as a Uniswap V2 pair—exercise extreme caution before trading.
Funding Sources
We randomly selected three Rugpull incidents detected by TenArmor to analyze funding origins.
Case 1
tx: 0x0f4b9eea1dd24f1230f9d388422cfccf65f45cf79807805504417c11cf12a291
Tracing back six hops reveals incoming funds from FixedFloat.
FixedFloat is an automated cryptocurrency exchange that requires no user registration or KYC verification. Scammers use FixedFloat to maintain anonymity when introducing funds.
Case 2
tx: 0x52b6ddf2f57f2c4f0bd4cc7d3d3b4196d316d5e0a4fb749ed29e53e874e36725
Five hops back show fund inflows from MEXC 1.
On March 15, 2024, the Hong Kong Securities and Futures Commission (SFC) issued a warning about MEXC, noting that MEXC actively promotes its services to Hong Kong investors without being licensed or having applied for a license from the SFC. As of March 15, 2024, MEXC and its website were added to the SFC’s list of suspected unlicensed virtual asset trading platforms.
Case 3
tx: 0x8339e5ff85402f24f35ccf3b7b32221c408680421f34e1be1007c0de31b95f23
Five hops back reveal incoming funds from Disperse.app.
Disperse.app is used to distribute ETH or tokens across multiple addresses.
Transaction analysis shows the caller of Disperse.app was 0x511E04C8f3F88541d0D7DFB662d71790A419a039, and tracing two hops further reveals another Disperse.app fund inflow.
Further analysis shows another Disperse.app caller at 0x97e8B942e91275E0f9a841962865cE0B889F83ac, and two hops prior, funds originated from MEXC 1.
Analyzing these three cases reveals that scammers frequently use non-KYC, unlicensed exchanges to fund their operations. TenArmor advises users to scrutinize the funding sources of contract creators when investing in new tokens.
Preventive Measures
Basing on aggregated data from TenArmor and GoPlus, this article comprehensively outlines the technical characteristics of Rugpulls and presents representative cases. In response to the above patterns, we summarize the following preventive actions:
1. Avoid blindly following trends. When purchasing popular tokens, verify that the token address is authentic to avoid counterfeit scams.
2. Perform due diligence during new launches. Check whether early trading volume comes from addresses associated with the contract deployer—if so, avoid the project.
3. Examine the contract source code, particularly the transfer/transferFrom functions, ensuring normal buy/sell functionality. Avoid contracts with obfuscated code.
4. Before investing, review holder distribution. Avoid tokens with highly concentrated ownership.
5. Investigate the contract creator’s funding sources. Trace back up to 10 hops to check whether funds originate from suspicious exchanges.
6. Monitor TenArmor’s early warnings to cut losses quickly. TenArmor can detect scam tokens in advance—follow TenArmor’s X account for real-time alerts.
All malicious addresses involved in these Rugpull incidents are continuously updated in the TenTrace system. TenTrace is TenArmor’s proprietary anti-money laundering (AML) system, applicable to AML, anti-fraud, and attacker identity tracking scenarios. It has accumulated scam/phishing/exploit address databases across multiple platforms, capable of effectively identifying blacklisted fund inflows and accurately monitoring their outflows. TenArmor is committed to enhancing community security and welcomes cooperation with interested parties.
About TenArmor
TenArmor is your first line of defense in the Web3 world. We provide advanced security solutions focused on addressing the unique challenges posed by blockchain technology. Through our innovative products ArgusAlert and VulcanShield, we ensure real-time threat protection and rapid response. Our expert team specializes in everything from smart contract audits to cryptocurrency tracking, making us the go-to partner for any organization seeking to safeguard its digital assets in the decentralized space.
Follow us on @TenArmorAlert for the latest Web3 security alerts.
Contact us:
X: @TenArmor
Mail: team@tenarmor.com
Telegram: TenArmorTeam
Medium: TenArmor
About GoPlus
GoPlus, as the first on-chain security protection network, aims to provide every user with the most accessible and comprehensive on-chain security safeguards to protect every transaction and asset.
The security service architecture primarily consists of the GoPlus APP (web and browser extension) for direct C-end users, and GoPlus Intelligence, which indirectly serves end-users through B-end integrations. Covering the broadest spectrum of Web3 users and transaction scenarios, GoPlus is building an open, user-driven on-chain security network:
Projects can independently integrate GoPlus to provide on-chain security for their users, while developers are encouraged to leverage their strengths by deploying innovative security products onto the GoPlus Security Marketplace. Users can then freely select and configure convenient, personalized security services, fostering a collaborative, open, decentralized security ecosystem between developers and users.
Today, GoPlus has become the preferred security partner for Web3 builders. Its on-chain security services are widely adopted and integrated by Trust Wallet, CoinMarketCap, OKX, Bybit, DexScreener, SushiSwap, and others, averaging over 34 million API calls per day and exceeding 4 billion cumulative calls. It covers over 90% of users’ on-chain transactions, and its open security application platform has already served more than 12 million on-chain users.
Our community:
Discord: GoPlusSecurity
Medium: GoPlusSecurity
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News