From Cure to Poison: Why Has Permit Become a Source of Risk?
TechFlow Selected TechFlow Selected

From Cure to Poison: Why Has Permit Become a Source of Risk?
We cannot deny the value brought by Permit, but the increasing number of recent theft incidents also suggests that the harm it brings seems to be even greater.
Author: Keystone
1. One-Minute Guide to Understanding What Permit Is
Let's start with a small story about borrowing money:
I want to borrow 1 million from my good friend Jack Ma. Without hesitation, Jack Ma picks up the phone and calls the bank, confirms his identity, then tells the bank: "I authorize XXX to withdraw up to 1 million." The bank acknowledges and records this authorization.
Next, I simply go to the bank and tell the counter I’d like to withdraw the 1 million that Jack Ma authorized for me. The bank checks whether there’s an existing authorization record, verifies that I am indeed XXX, and then hands over the 1 million.
This little story is a tangible analogy of the Approve authorization mechanism on Ethereum. In this process, only Jack Ma (the asset owner) can initiate the authorization by calling the bank (i.e., sending a transaction on-chain), which is then recorded and managed by the bank (the token contract). Only after that can I (the authorized party) transfer funds up to the authorized amount. If the bank finds no such authorization, my withdrawal request will be rejected outright.
Now, what if we use a different authorization method—Permit—to borrow from Jack Ma? How would the process change?
This time, when I ask again to borrow 1 million, the generous Jack Ma doesn’t bother calling. Instead, he pulls out a checkbook, fills in the amount, signs it, and hands it to me. I take this check to the bank for redemption. Even though the bank has no prior authorization record, it verifies the authenticity of the check through Jack Ma’s signature and pays me the specified amount.
You’ve probably already noticed the difference between these two processes. Approve, as a key feature of ERC-20, has been widely used since Ethereum launched. So why did we later introduce the Permit method via ERC-2612 to achieve the same purpose?
2. Why Do We Need Permit?
The ERC-2612 proposal was first introduced in March 2019 and wasn't finalized until October 2022. Its emergence is closely tied to the multiple spikes in gas prices on the Ethereum mainnet during that period.
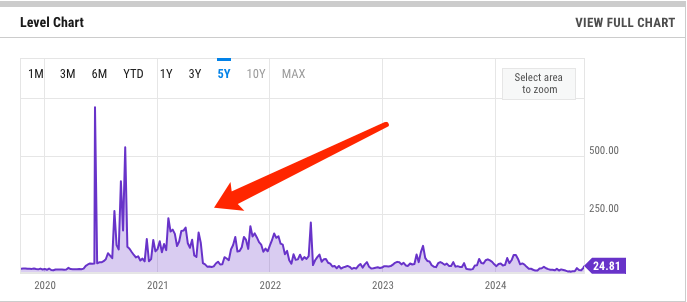
Figure: ETH mainnet gas prices remained high between 2020–2022
A raging bull market combined with the wealth effect of new on-chain projects led to extremely high trading enthusiasm. Users were willing to pay higher fees to get their transactions confirmed faster—sometimes, being included just one block earlier could mean exponentially higher profits.
However, the downside was that users often had to endure exorbitant gas costs. Under the traditional Approve workflow, completing a token swap required two separate transactions (TXs). For users with smaller capital, these transaction fees became a nightmare.
ERC-2612’s introduction of Permit changed authorization into an off-chain signing process. It doesn’t need to be submitted on-chain immediately. Instead, the signature can be provided later when transferring tokens—just like how I only present Jack Ma’s signed check to the bank at the time of withdrawal.
Busy Jack Ma saves a phone call, and users seemingly save one TX. During periods of high gas prices, the cost savings are significant—appearing to be a win-win situation. But unbeknownst to many, Pandora’s box was quietly opening...

3. Explosive and Uncontrolled Growth
Prior to Permit, one common tactic hackers used to phish users was tricking them into signing Approve transactions. Since these transactions required gas fees, users were more alert, making successful attacks harder. Even if a user accidentally clicked through, they could usually recover in time by submitting a replacement transaction with the same nonce before the original was confirmed. Thus, hackers didn’t always succeed.
With the arrival of Permit, however, it was like hitting the jackpot for hackers. Compared to Approve, Permit requires no gas—only a signature—lowering users’ guard significantly. Due to its off-chain nature, attackers gained full control: users couldn’t undo their consent, and hackers could choose the optimal moment to exploit the authorization, maximizing their gains.
The negative consequences are evident: the number of phishing victims and total stolen amounts have surged dramatically. According to @ScamSniffer statistics:
In 2023, phishing attacks resulted in losses totaling $295 million.
In the first half of 2024 alone, losses exceeded $314 million.
By the end of Q3 2024, a major incident occurred: a wallet address believed to belong to Shen Yu suffered a Permit-based phishing attack, losing 12,000 $spWETH—worth around 200 million RMB.
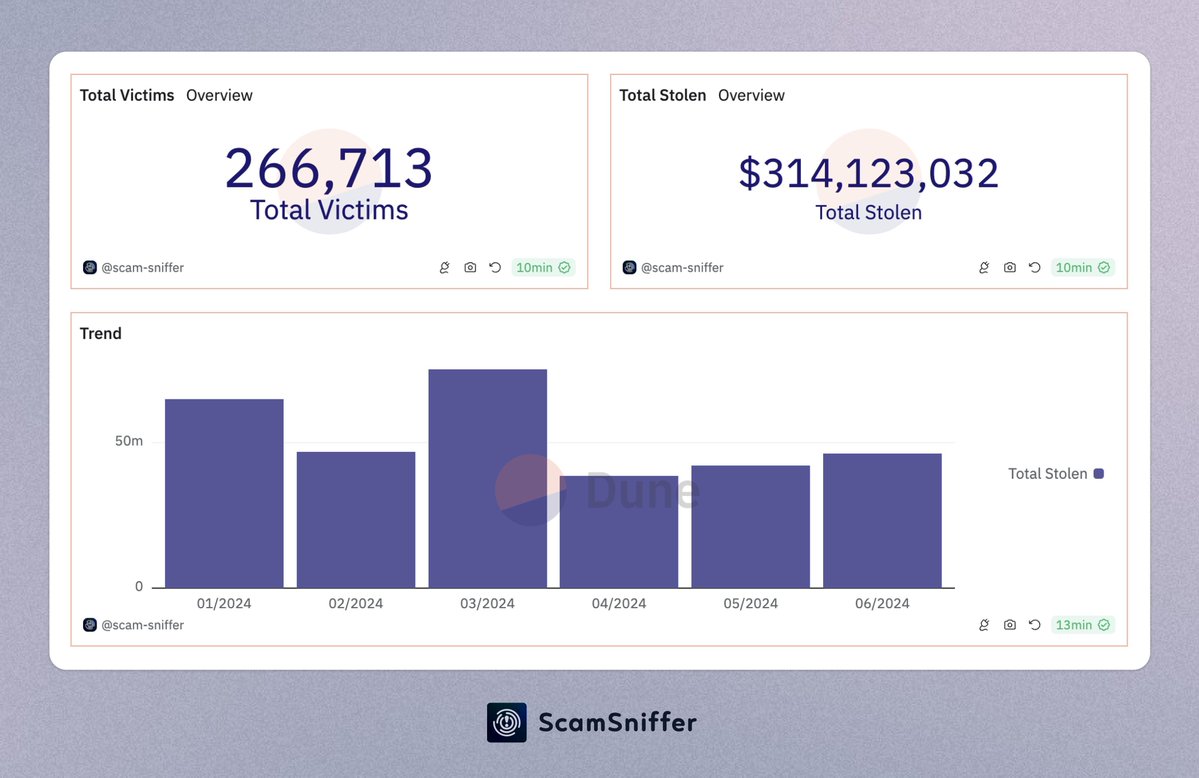
Figure: ScamSniffer’s Phishing Attack Statistics Report for H1 2024
This state of affairs was likely unforeseen by the original proposers. The intention behind Permit was to reduce gas costs and improve user experience and efficiency. They thought it was a double-edged sword—gains came with risks—but instead, it turned out to be a giant kitchen knife: one side extremely sharp, slicing open a massive hole in the shield protecting user asset security.
There are several similar signature-based authorization methods. For example, Uniswap’s later introduction of Permit2 enables offline signing for all ERC-20 tokens. As the No.1 DEX, Uniswap’s adoption further increased user reliance on offline signatures, thereby amplifying phishing risks.
4. How to Protect Yourself?
So, as ordinary users facing this Damoclean... kitchen knife hanging over our heads, what preventive measures can we take to avoid losses?
1. Raise Awareness
Stay Calm Amid Airdrop Temptations
Crypto project airdrops can be very attractive, but most are actually phishing attacks disguised under fake airdrop names. When encountering such offers, never rush to “claim” them. Verify the legitimacy of the airdrop and the official website through multiple trusted sources to avoid landing on phishing sites.
Avoid Blind Signing
If you accidentally land on a phishing site and your wallet pops up a transaction request, carefully review the content. If you see terms like Permit, Permit2, Approve, or IncreaseAllowance, be cautious—this means the transaction is attempting to obtain token authorization. Normal airdrop procedures don’t require this. Keystone implements transaction parsing and display at the hardware level. Users can leverage such tools to avoid blind signing and prevent serious consequences caused by impulsive actions.
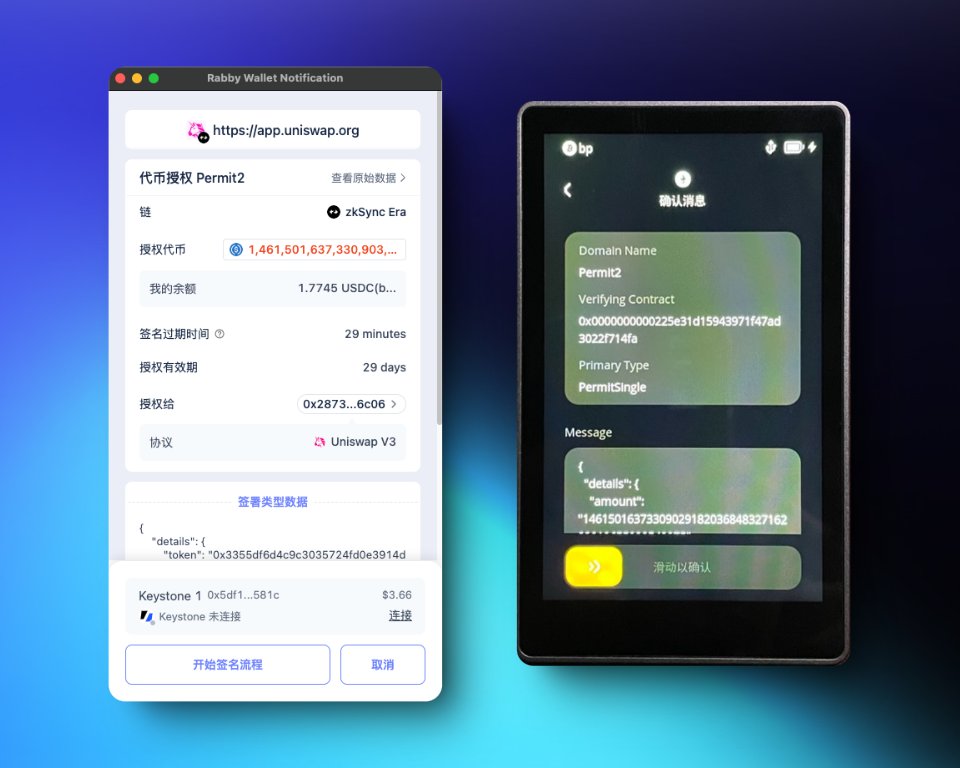
Figure: Keystone hardware wallet and Rabby Wallet parsing and displaying a Permit2 signature transaction
2. Use Protective Tools
ScamSniffer
For average users, accurately identifying phishing URLs is extremely difficult, and some threats inevitably slip through. By using the ScamSniffer browser extension, you’ll receive warnings when visiting suspected phishing websites, allowing you to stop interaction in time.
Revoke.cash
Revoke.cash displays all token authorization records in your wallet. We recommend revoking any suspicious or unlimited authorizations. Develop the habit of regularly cleaning up authorizations and minimize unnecessary approvals.
3. Asset Segregation and Multi-Signature Wallets
As the saying goes: don’t put all your eggs in one basket—and this applies perfectly to crypto assets. For instance, store large holdings in cold wallets like Keystone, while using small-balance hot wallets for daily interactions. Even if compromised, your major assets remain safe.
For even higher security needs, consider using multi-signature (multi-sig) wallets. With multi-sig, assets can only be moved when a threshold number of signers approve. If a single wallet is hacked, the attacker still cannot access the funds without meeting the approval threshold.
5. Conclusion
We can’t deny the value Permit brings. However, the growing number of theft incidents suggests its risks may now outweigh its benefits. Much like the once-popular eth_sign method—which was notorious for poor readability and high risk and thus favored by hackers—it eventually got blacklisted and deprecated by most wallet providers. Its functionality has since been replaced by safer alternatives.
Now, is Permit standing at the same crossroads that eth_sign once faced? Should it be improved and upgraded—or abandoned altogether? This is a question Ethereum developers must now seriously consider and discuss.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News