SlowMist: Old Wine in a New Bottle — Analysis of the Arbitrage MEV Bot Scam
TechFlow Selected TechFlow Selected

SlowMist: Old Wine in a New Bottle — Analysis of the Arbitrage MEV Bot Scam
This article will analyze the tactics of arbitrage MEV bot scams and the fund transfer patterns used by scammers.
Author: Liz, SlowMist
Background
Earlier this year, SlowMist founder Cos warned users on X about fraudulent arbitrage MEV bot scams. Today, hacker groups continue to follow trends closely—the scam has simply rebranded from a "simple-to-use Uniswap arbitrage MEV bot" into the "ChatGPT Arbitrage MEV Bot: How to Use Slippage Bots to Earn $2,000 Daily with Zero Effort." The SlowMist security team has observed an increasing number of victims affected by such scams recently. This article will explain how these scams operate and analyze the fraudsters’ fund movement patterns to help users avoid falling victim.
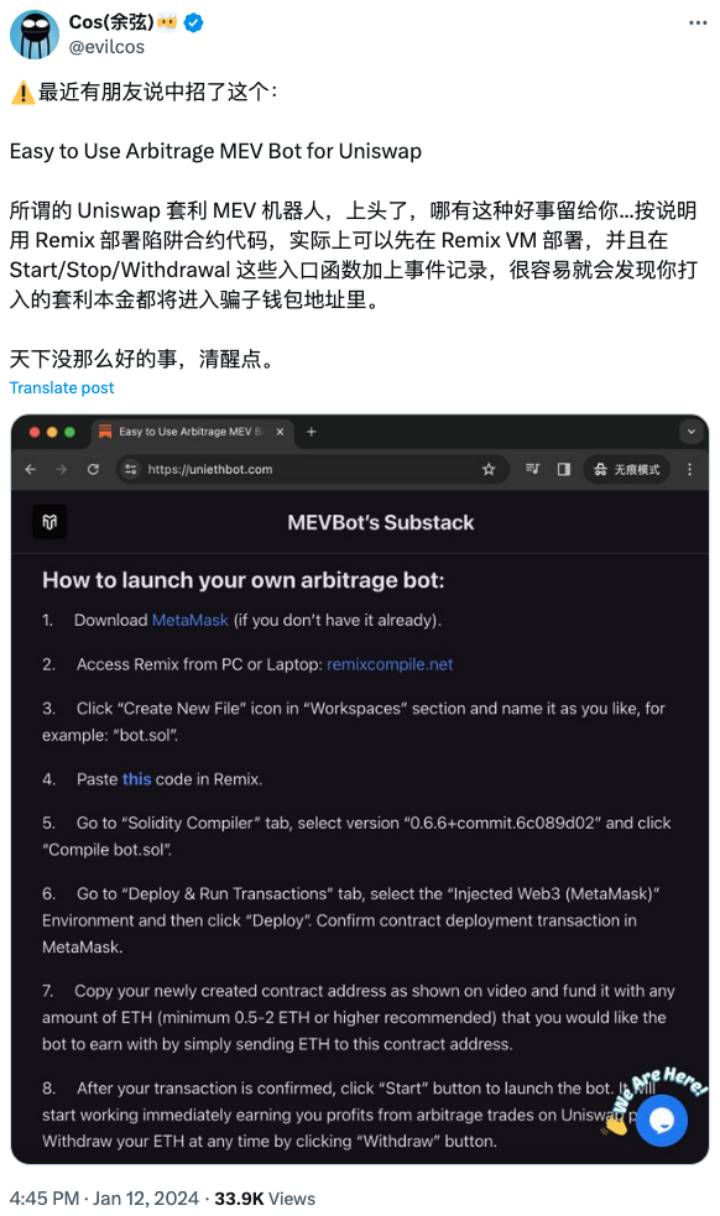
(https://x.com/evilcos/status/1745728599171457120)
Falling for the Scam While Chasing Arbitrage
AI tools like ChatGPT have become widely used for boosting productivity—and scammers are well aware of this. By associating their scams with ChatGPT, they gain attention and appear more credible and sophisticated. However, ChatGPT only briefly appears in the scammer’s tutorial video: the fraudster claims the arbitrage bot code was generated using ChatGPT, thereby reducing suspicion around potentially malicious code.
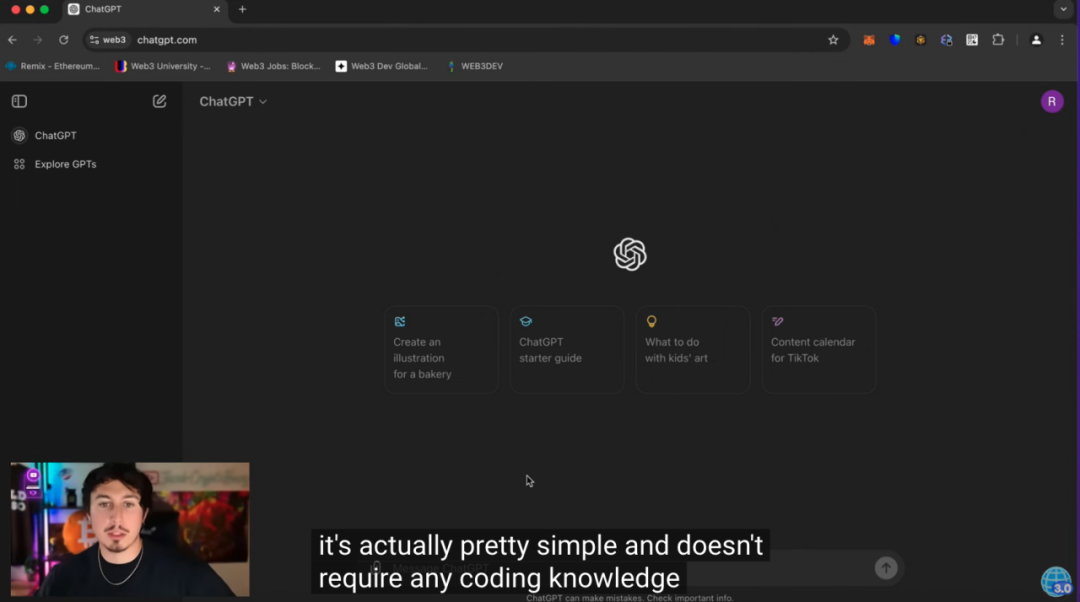
(https://www.youtube.com/watch?v=Z32hH3eLK-c)
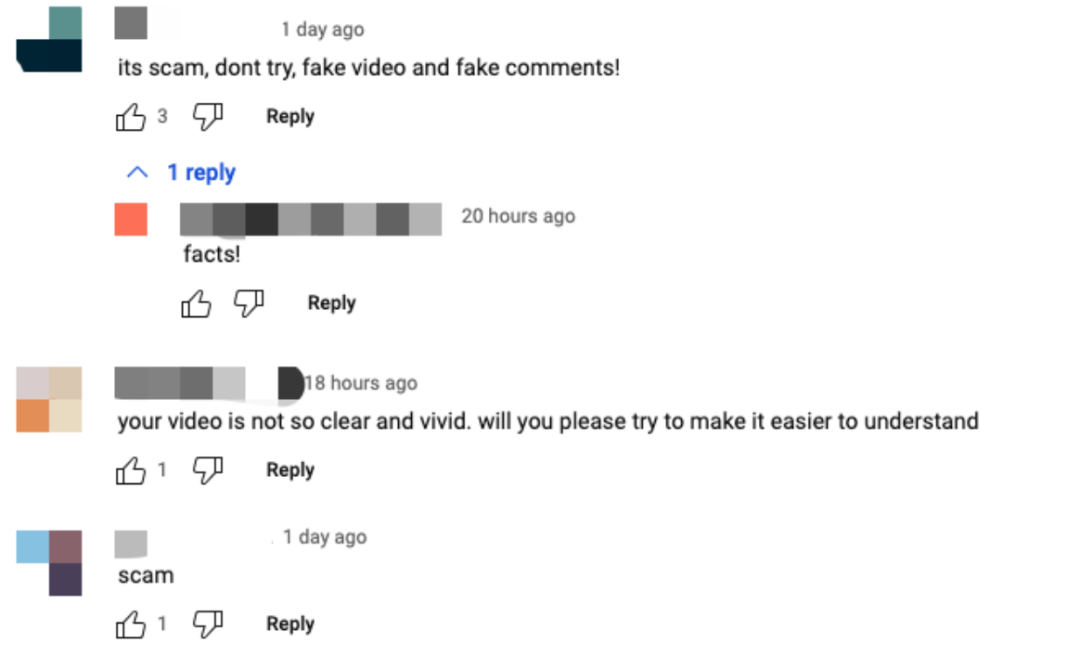
In reality, a closer look at the scammer's YouTube video reveals obvious signs of manipulation—audio and visuals are out of sync, previous videos appear fabricated, and the account was likely purchased. All evidence suggests this YouTuber is untrustworthy. Although the comment section is flooded with praise and gratitude, scrolling further down reveals warnings and alerts posted by actual victims.
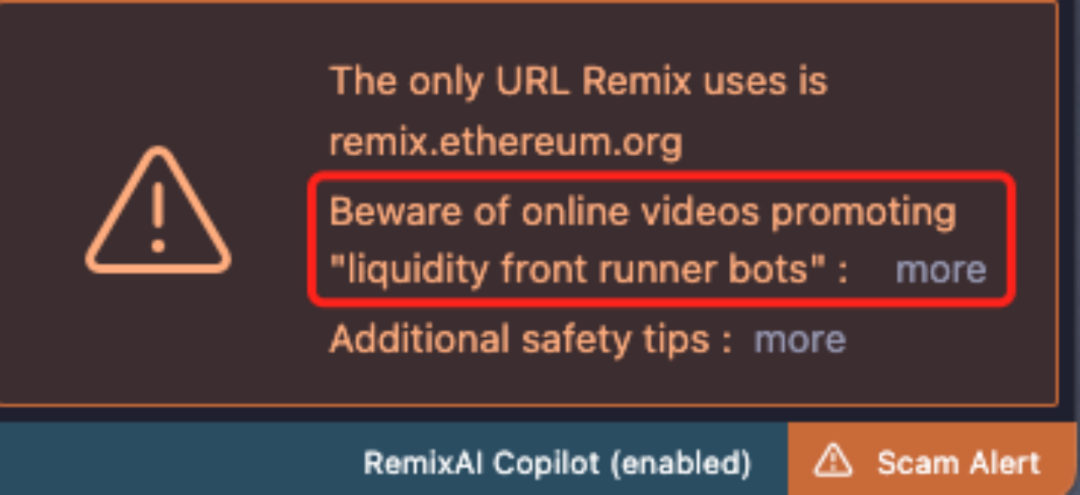
The scammer claims that their bot monitors new tokens and significant price changes on Ethereum to identify arbitrage opportunities, allowing users to earn passive income effortlessly. First, users need a MetaMask wallet and must open a provided Remix link (a fake version of Remix).
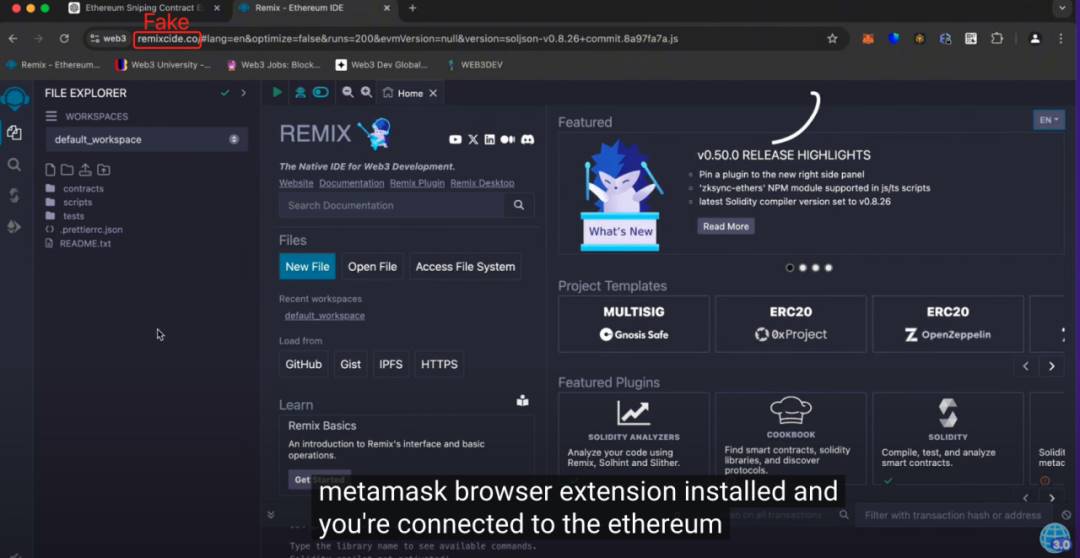
Next, users are instructed to paste the scammer-provided code, compile it, and deploy the smart contract. At this stage, the scammer insists users must deposit initial funds into the contract, claiming higher ETH deposits yield greater profits. Once users complete these steps and click “start,” their money disappears—the deposited capital is immediately transferred to the scammer’s wallet due to backdoor code.
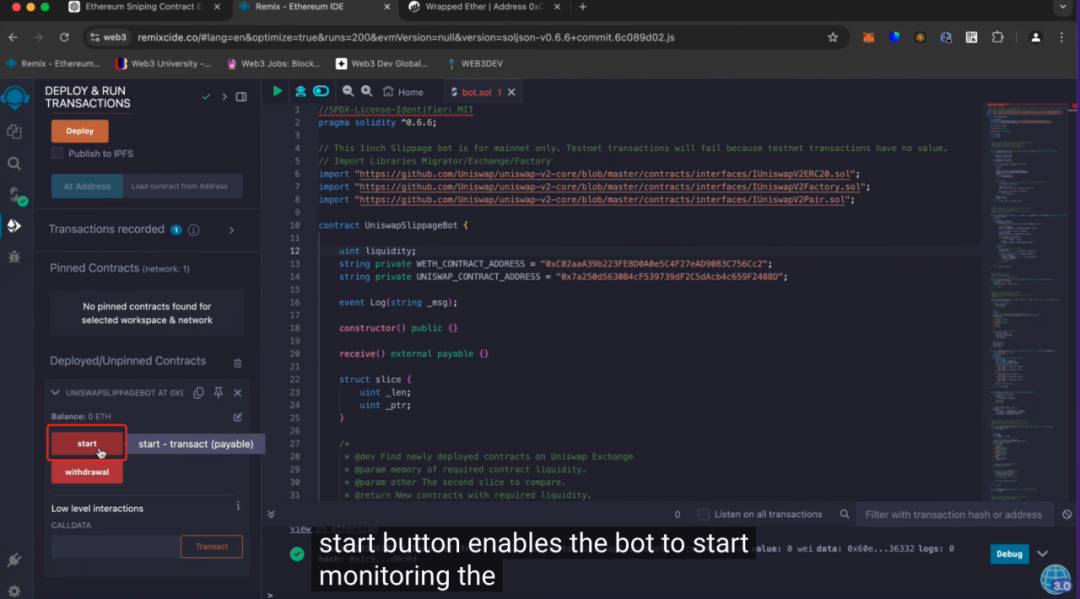
We take the scam incident reported by Web3 anti-fraud platform Scam Sniffer as an example to analyze the fund transfer patterns commonly used by such scammers.

(https://x.com/realScamSniffer/status/1828364436241031669)
Using the chain analysis and anti-money laundering platform MistTrack to investigate the scammer’s address (0xAEF35f154C318c87744913f38A6d357691258122), we find that since late August, this single address has already profited approximately 30 ETH, with over 100 victims.
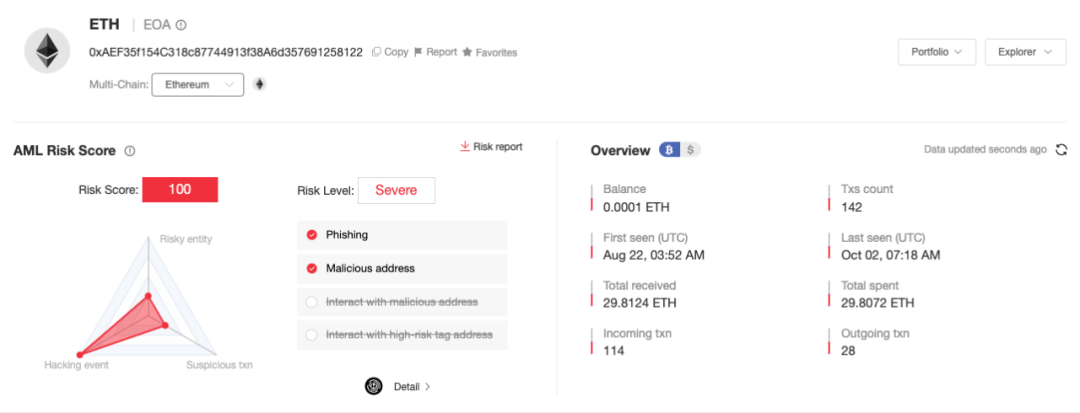
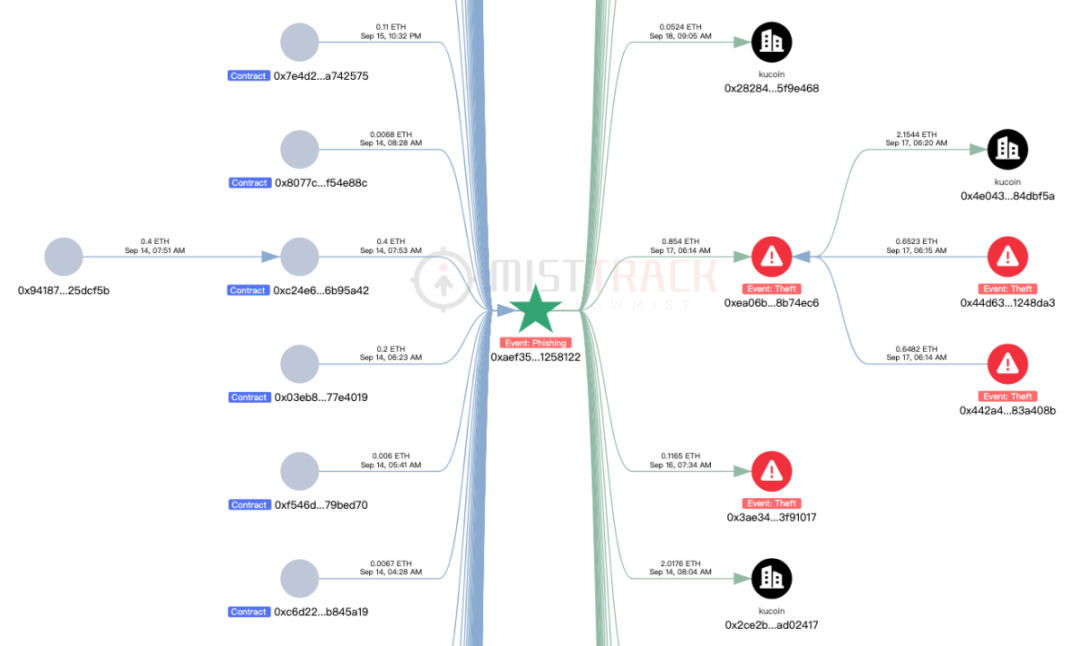
The funding pattern into this address is consistent: victims follow the scam process described above, transferring ETH into the contract, which is then stolen by the scammer. Outflows either go directly to exchanges or are first routed through intermediate holding addresses (e.g., 0xea06b983e144432919779b236ba28ece28b74ec6) before being sent to exchanges.
The addresses 0x442a4960c783affe2b6d9884f32d7cf2683a408b and 0x44d63ce270637553f89f3c2706869d98d1248da3 in the image below are also used by the scammer to collect victim funds directly. These two addresses were created in late August and have since stolen about 20 ETH from approximately 93 victims.
Since scammers adopt a broad, low-yield approach—collecting small amounts from many victims—it becomes impractical for most victims to pursue legal action due to relatively minor losses. As a result, these scammers can operate with impunity for long periods, simply repackaging their scams under new themes to continue defrauding others. Remix has issued warnings on its website about such scams. In the comment section of its Medium article analyzing such frauds, users have been reporting incidents dating back two years up to the present, sharing links to fraudulent videos and urging others to stay vigilant—highlighting just how widespread these scams have become.
Conclusion
The SlowMist security team urges all users to avoid clicking suspicious links or executing unknown code. Since scammers claim their code is generated by ChatGPT, users should at least verify the code using tools like ChatGPT or Claude to check for malicious behavior. Many users initially seek only passive income and are willing to invest capital, but following the scammer’s instructions leads not to profit—but total loss of principal. Ironically, it is the scammer who ends up earning truly passive income, as victims continuously send money into their wallets. Stay alert: always double-check whether an opportunity is a windfall or a trap, and protect your assets accordingly.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News