After the Run on Banks: Predictions and Reflections—Privacy, Credit, DID
TechFlow Selected TechFlow Selected

After the Run on Banks: Predictions and Reflections—Privacy, Credit, DID
Demand in the following sectors—privacy, credit, decentralized identity, and reputation systems—may grow as flaws exposed by bank runs become apparent.
Author: Raxy @Jsquare
Disclaimer: This article does not constitute any investment advice. All thoughts are the author's independent views and do not represent the position of their affiliated company.
✦ Introduction ✦
Recent market-wide liquidations have occurred in waves. I believe that several sectors—privacy, credit, decentralized identity (DID), and reputation systems—may see growing demand as flaws exposed during these panic-driven sell-offs become more apparent. This article attempts to explore narrative possibilities through specific projects. These are just fragmented thoughts; please correct me if there are obvious errors.
01 Whales being targeted at critical moments highlights the importance of on-chain privacy for institutional holders and users alike. Privacy may require a framework and ecosystem capable of delivering customized services based on user needs.
Although blockchain accounts are currently represented by complex strings of numbers and addresses, persistent tracking and analysis can still reveal the identities behind these accounts. Numerous data analytics tools already exist to help identify such whales.
Thus, to some extent, blockchains do not truly protect user privacy. Once your address is linked to your real-world identity, all transaction data becomes fully transparent. Even with multiple wallets prepared in advance, each new wallet still requires a gas fee to activate. Therefore, it’s worth exploring how the long-discussed privacy sector has evolved across multiple bull and bear cycles—what developments and changes have actually taken place?
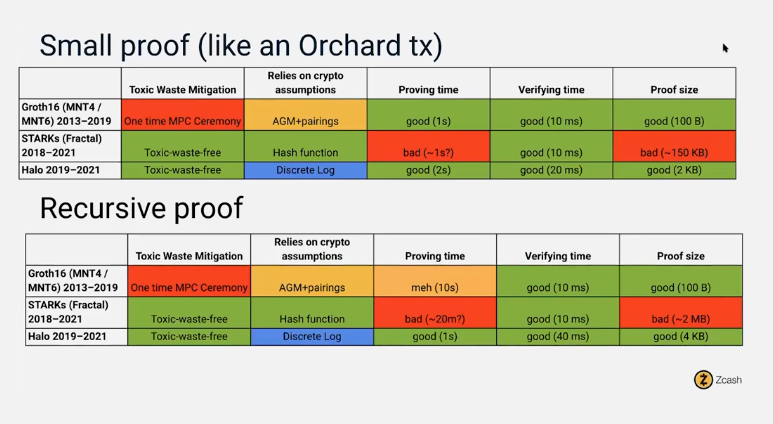
Zero-knowledge proof (ZKP) technology was first discovered in the 1980s but remained ineffective or inapplicable until Zcash emerged in 2016.
Zcash, using Groth16 technology, offers two types of addresses: shielded private addresses (Z) and transparent addresses (T). Transactions involving Z-addresses hide associated addresses, amounts, and encrypted notes, while T-address transactions are publicly visible via standard blockchain explorers.
Z-addresses and T-addresses on Zcash can transact with one another, enabling a process of free choice: you can de-anonymize assets by sending from a Z-address to a T-address, or anonymize them by moving from T to Z.
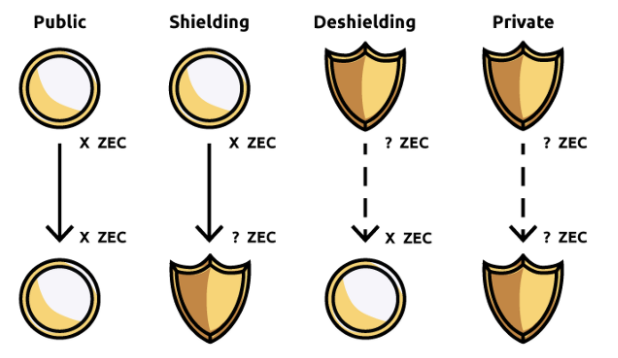
The above image illustrates the conversion process between Zcash’s Z and T addresses.
However, Zcash has a flaw: everyone uses a specific key to verify proofs. If someone gains access to the corresponding private key, they could spoof proofs. Thus, the master key introduces a significant trust issue.
At the time, Zcash sparked extensive debate among thinkers and also faced pressure from anti-money laundering regulations.
Therefore, today we need to define a clear small panel for privacy demands. On-chain dApps consist of interactions—of varying complexity—between users and smart contracts. Any privacy solution must ensure both of these atomic components—users and smart contracts—are private and secure.
Privacy isn’t just about anonymizing simple transactions or certain actions—it requires building a broader ecosystem comprising various privacy-focused applications to serve users. For example, a whale or market maker executing real trades may employ multiple strategies to manage risk exposure, yet current solutions cannot adequately meet their privacy needs.
Hence, privacy needs a comprehensive framework and system upon which developers can build and create applications.
Building on Zcash, Aleo enables not only anonymous asset transfers but also private payments, liquidity provision, governance voting, and identity verification. Only the interacting parties know the details; malicious third parties cannot learn anything or exploit the information in any way.
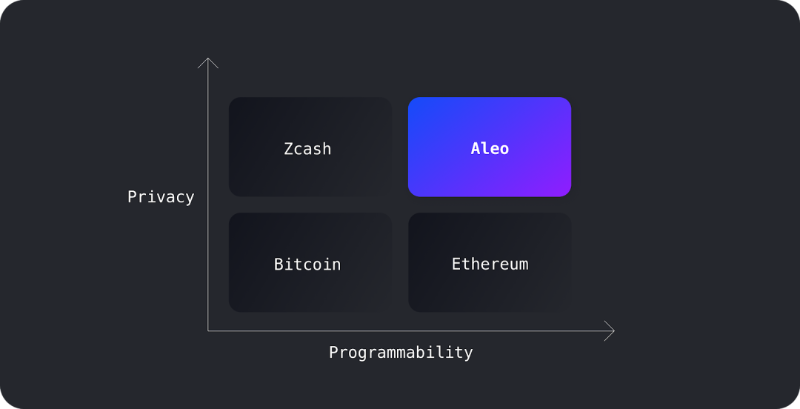
Aleo is a platform for fully private applications. Its core remains ZKP, but Aleo provides a full-stack solution allowing ZK programmability at every layer of the stack, enabling large-scale decentralized private computation. For both users and transactions—the two atomic components—Aleo ensures no identifying information is leaked.
Aleo supports composable and private applications and provides a new programming language framework called "Leo." Leo emphasizes readability and ease of use, resembling traditional programming frameworks, abstracting away low-level cryptographic concepts, and offering a developer-friendly experience.
Aleo employs a system called ZEXE (Zero-Knowledge EXecution). During state transitions, it generates a proof bundled into an on-chain transaction. The transaction updates the system state by creating an on-chain record, so the final transaction contains only the proof—not the inputs used to generate it. Aleo refers to this concealed process as "zkCloud," a component within its tech stack.
"zkCloud" enables programmable interactions between protected identities—such as users, organizations, DAOs, etc. This computational model can run locally or be delegated to specialized validators.
In addition, other ZKP-based projects like Aztec are also promising. Aztec aims to fulfill Ethereum’s unmet privacy needs, while Secret Network uses Trusted Execution Environments (TEE). Since ZKP requires less trust, TEE-based projects might develop faster relatively speaking.
The above outlines Aleo’s basic architecture. In future research, I will delve deeper into Aleo’s ecosystem development and write a dedicated piece exploring how the aforementioned Aleo functionalities meet privacy demands.
02 Whale credit played a crucial role in this debt crisis. Credit requires multiple middleware and infrastructure layers to mature, with the core being an on-chain and off-chain credit evaluation system. On-chain credit is still searching for product-market fit (PMF).
On-chain credit is still in early market stages, lacking abundant middleware and infrastructure, and some issues may need modular solutions—such as regulatory licenses, mature DID systems, and sound on-chain credit algorithms.
Had 3AC’s wallet assets been valued at peak prices, I believe credit platforms would have given them perfect scores. So before discussing credit products, we must recognize that credit fundamentally depends on creditworthiness assessment and borrowers’ ability to pay interest and meet qualification criteria.
Let’s start with credit systems. Building credit systems inevitably involves the question of how on-chain and off-chain elements should coexist.
DID products continue exploring ways to integrate or balance on-chain and off-chain data, striving to make identities increasingly datafied and structured. However, due to limited existing benchmarks and standards, no high-adoption DID product has emerged yet.
Thus, current credit systems rely mostly on off-chain evaluations. Off-chain assessment implies a black-box evaluation model, making crypto lending remain a fragile business line.
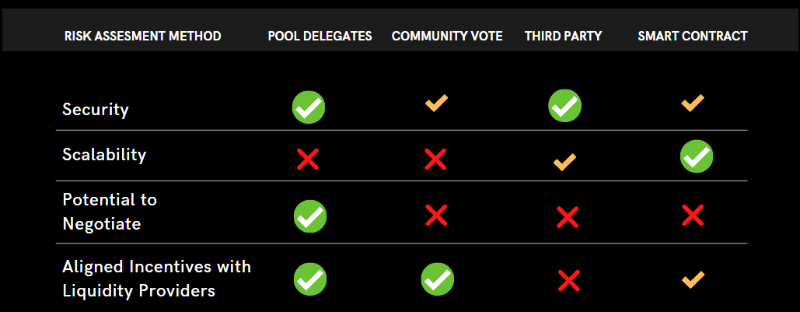
Comparison of different risk assessment methods
We’ll compare Maple Finance, TrueFi, and Goldfinch to distinguish their credit assessment approaches.
Maple Finance introduced Pool Delegates to source and evaluate loans. Each lending pool can be managed by different delegates who assess borrowers. They offer collateral ratios ranging from 0–50%, primarily serving crypto-native institutions.
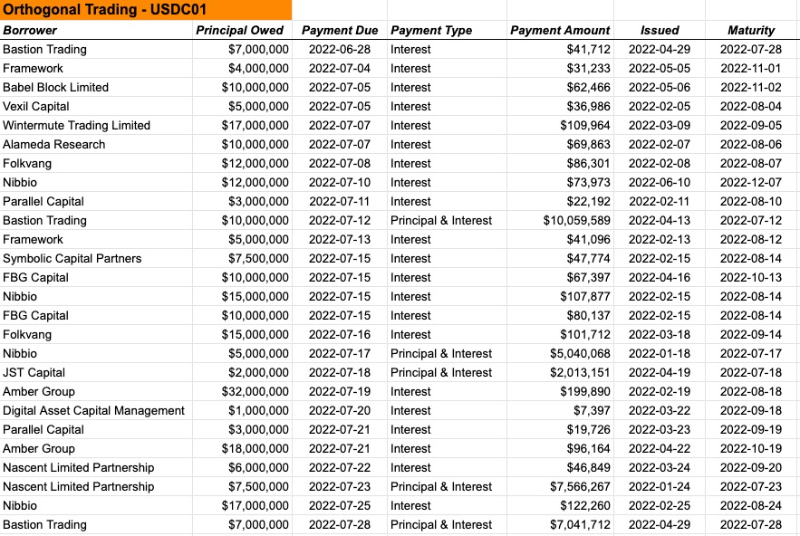
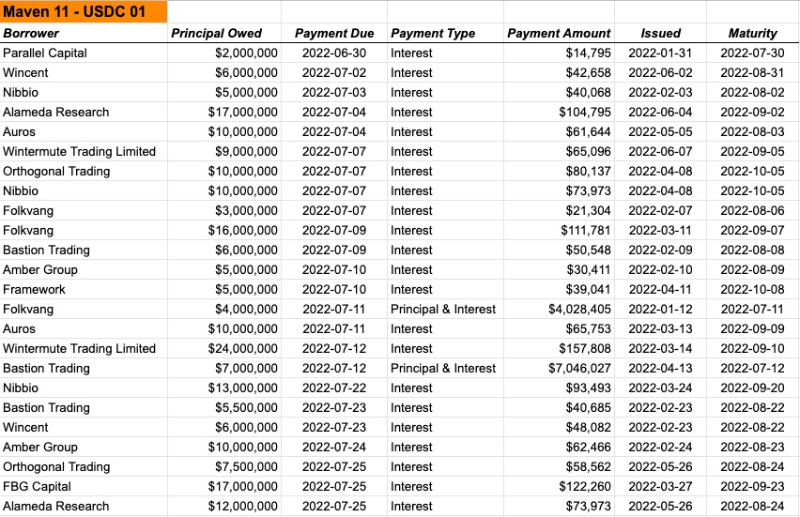
Orthogonal Trading and Maven11 are two major Pool Delegates
Maple Finance allows Pool Delegates to negotiate loan terms with borrowers—including interest rates, maturity dates, and collateral ratios.
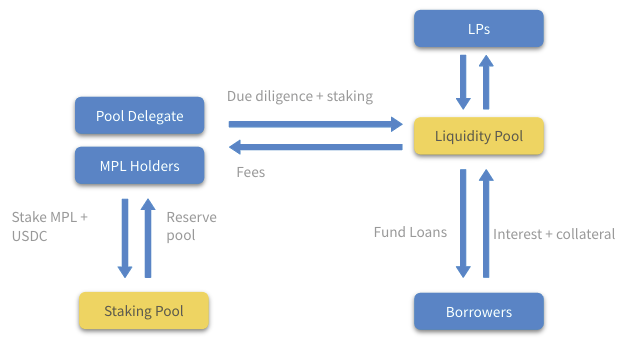
How Maple Finance operates
TrueFi, on the other hand, centers its model around a DAO vote. The community initially sets all loan terms, and borrowers must additionally gain approval from individuals holding $stkTRU. Each loan request requires over 80% approval.
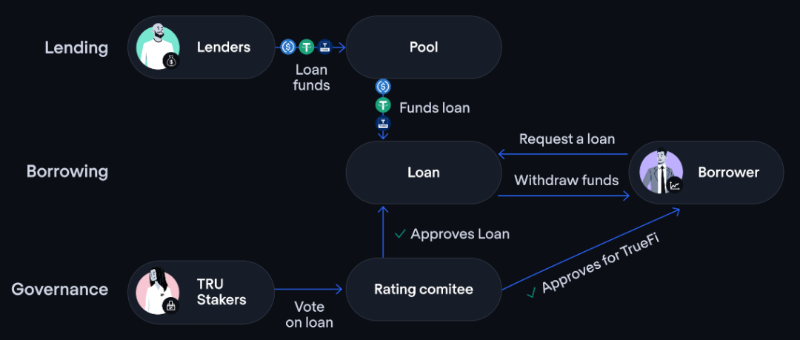
How TrueFi operates
Goldfinch relies on third-party partner teams (Personal or Parallel Markets) for audits. Borrowers must stake $GFI tokens—roughly twice the loan amount—and submit institutional credit and financial statements to the team. Upon successful review, the borrower receives a non-transferable, unique identity (UID) NFT linked to their designated wallet to prevent Sybil attacks. Then, the system randomly selects 6 out of 9 auditors to approve the loan. (This is somewhat similar to TrueFi, where native token holders act as voters.)
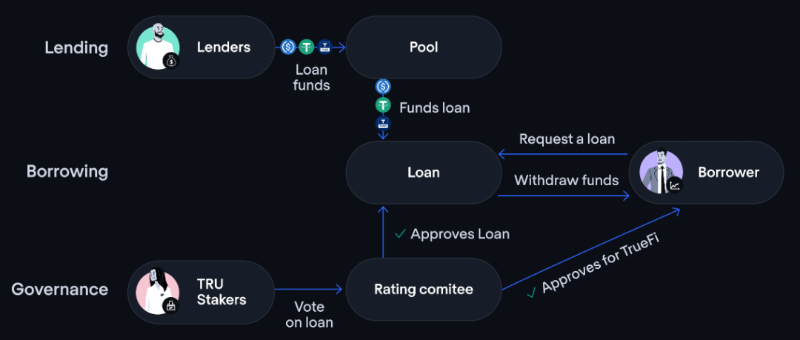
How Goldfinch operates
From an overall design perspective, the biggest difference among the three lies in their loan evaluation mechanisms.
However, they share one commonality: centralized individuals or teams conduct credit assessments. Even though these include stakeholders who hold platform tokens, I believe they still feel uncertain and confused when assessing debts of super-whales.
Then we return to our earlier question:
“If 3AC’s wallet value were at its peak, what score would Maple, TrueFi, and Goldfinch’s evaluation models assign to 3AC?”
On-chain reputation and credit risk scoring remain major challenges. Credit requires backing from authoritative entities—governments, state machinery, or legal frameworks. Credit doesn’t emerge out of thin air.
What backs the credibility of Maven11 and Orthogonal Trading? Is it merely the assets they’ve deposited into pools? UST was a good attempt. Before LFG purchased BTC, I was a Terra believer. But later I realized the leverage built upon such credit kept increasing. Credit inherently takes time to establish and requires continuous trial and error.
Why then does the crypto market keep spawning countless collateral ratio models and credit evaluation frameworks, resulting in such chaos?
The root cause may lie in the fact that no one can guarantee consequences for defaulting, nor dare speculate rewards for repayment.
Meanwhile, because of the large interest rate gap between DeFi and traditional banking, borrowers are reluctant to pay high rates (those willing to pay high rates often lack qualifications, introducing inherent risks), forcing platforms like Maple and TrueFi to subsidize borrowing with their own tokens. Thus, institutional lending in DeFi remains in a phase of actively seeking PMF.
But debts can be restructured, and new cycles will emerge. Credit remains one of the indispensable engines of DeFi.
Earlier, we mentioned the large yield spread between DeFi and traditional finance, which creates borrowing demand.
But borrowing assets means you’re short—more precisely, you implicitly hold a bearish view or expect prices to remain range-bound in the short term.
In TradFi, this is known as carry trade. When carry trade experiences massive volatility, TradFi yields drop, causing interest rates on major DeFi lending platforms like Aave and Compound to fall. Moreover, stablecoins in DeFi face depeg risks due to currently limited use cases.
Therefore, during liquidity crunches, users may increasingly price their lives in fiat. Even if they borrow DAI or other stablecoins, they may still exchange them for USDC or fiat on CEXs. Hence, we observe more traditional giants and whales attempting to short stablecoins to trigger depegs—a profitable arbitrage opportunity.
Precisely because credit-related credit algorithm models are still imperfect, among other factors, overcollateralization has become the dominant model in DeFi, ensuring platform security and treasury liquidity to better control risk.
Overcollateralization isn’t flawless. Risks include:
-
In public chains with limited liquidity, the overcollateralized model acts like a vampire. When you borrow large amounts of ETH, BTC, or USDC using native protocol assets for liquidity, you effectively drain non-native asset liquidity from the chain. This leads to high TVL on certain chains dominated by illiquid native assets (unless you’re willing to endure extremely high slippage on DEXs).
-
The overcollateralized model introduces Debt Ceilings (debt ceiling constraints).
-
Crypto asset prices may remain highly volatile for extended periods. Overcollateralization can easily trigger panic-driven liquidation cascades. To safeguard their liquidation thresholds, whales may dump altcoins to consolidate liquidity and replenish collateral.
Relatively speaking, for the crypto market—which remains in an extreme dark forest phase—overcollateralization is indeed a better way to manage risk. For crypto-native liquidity, the most suitable instrument may well be overcollateralized stablecoins. Perhaps cascading liquidations are crypto’s best evolutionary path. Whether collateral can uphold this banner matters greatly.
Recently, Aave announced its overcollateralized stablecoin (GHO), which could capture part of the stablecoin market share. It will be important to watch whether GHO can leverage Aave’s credibility to quickly establish use cases across several DeFi protocols. Until now, I’ve wondered what a true on-chain bank might look like—perhaps the answer is near.
03 Flaws in credit evaluation systems highlight the importance of native DeFi authentication and decentralized reputation scoring systems.
Here, I’d like to introduce ARCx. At the slogan level, it addresses my confusion about overcollateralization, privacy, and credit scoring systems. Yet, adoption rates remain to be observed.
Moreover, we must evaluate whether its designed credit scoring system can genuinely solve the aforementioned problems in practice.
ARCx has created a DeFi Passport (scored 0–999), generating a credit score based on users’ past wallet interactions with various DeFi protocols. Evaluation criteria include many variables such as loans, liquidations, airdrops, and user behaviors.
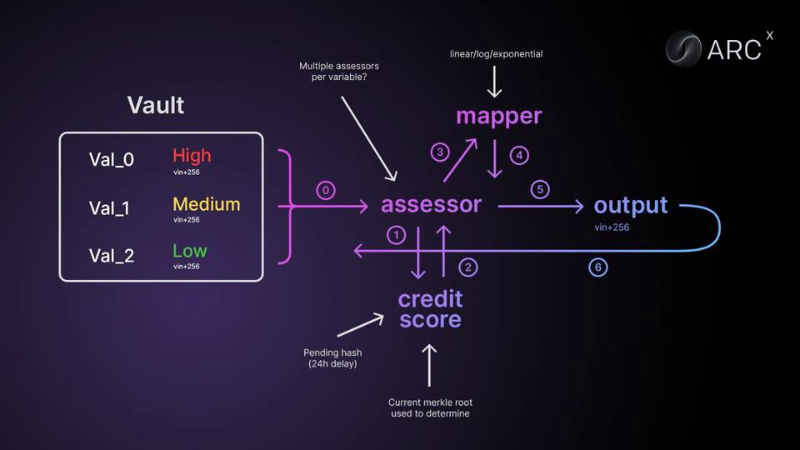
As Andrew Beal noted in his recent post:
“The DeFi ecosystem represents a new quadrant of the financial system, but from a reputational standpoint, it’s an island separated from the mainland. Why?
No identity.
All the work you’ve done to build reputation in traditional finance doesn’t apply because the DeFi ecosystem doesn’t know who you are. It’s like transferring schools halfway through junior year. Everything you did in the first two years is gone—you must start over.”
04 By decomposing and datafying the concept of “identity,” making user identities and data unique and composable, we need a minimal viable “DID protocol.”
When placing the word “identity” online, we seem able to break it down into compositional frameworks like storing, managing, and retrieving information.
Yet “identity” touches upon the “philosophy of self.” When discussing the “self,” we should regard humans as holistic beings. Identity reflects social attributes and, to some degree, personal value.
Voltaire wrote in his *Philosophical Dictionary* regarding “identity”:
“Only memory can establish identity, i.e., personal sameness.”
“My identity today clearly stems from yesterday’s experiences and the traces they left in my body and consciousness.”
Once, our identities were shaped by religion and authoritarianism. Now, without faith or emperors, we face numerous ratings and evaluation systems.
These have become invisible shackles controlling us. Can we now deconstruct the term “identity” to liberate the real-world “self”? Can we entrust recognition of social attributes to network identities that are constructible and decomposable?
Web3 empowers every user and builder to control their own data, value, relationships, and information. Every user will become a unified discovery point of their own data, experiencing composability across apps and interactions.
This could create compound experiences akin to shared network effects, whereas isolated systems manipulating user privacy and data will become islands. Decentralized identity systems relying solely on addresses and NFTs as foundations will face severe limitations.
“A subjective feeling, and observable qualities of personal similarity and continuity, combined with a certain belief in the similarity and continuity of some shared worldview. As an unconscious quality of life, this is especially evident in young people discovering themselves and their communities. Within it, we witness the irreversible emergence of unique unity—body type and temperament, talents and vulnerabilities, childhood patterns and acquired ideals—revealing available roles, career possibilities, choices of values. Offers, mentors appear, friendships form, and initial sexual contacts occur.” (Erikson, 1970)
0xBcfd stated in his post that we can learn from the flaws of primitive cryptographic identity systems to understand what’s needed for more reliable decentralized identity systems. Clearly, a single registry (index), identifier standard, or data structure standard is too rigid.
It must work with various identifiers. It must be open to flexible, extensible data models and structures. It must operate across network environments. Its design should follow the principle that identity is about managing and discovering information—thus, data must come first.
This suggests a simple design: each identifier maintains a table containing its own data. Collectively, these identity-centric user tables form a distributed user table for the internet.
This distributed user table isn’t a physical table but a virtual one, composed of several components analogous to parts of a traditional user table:
Identifier: Decentralized identifiers shouldn’t be mere entries in application databases but provably unique and cryptographically controlled. Accessibility must support various forms of identifiers across networks—similar to the decentralized DID standard.
Data Structures: Just as app developers define their own data structures, a decentralized data layer must enable developers to define custom data models while ensuring reusability and public storage.
Index: Users bring their identifiers when defining data models in apps. Standard indexing can combine these elements into a user table (or app table), so when users interact with apps (creating data), the information is properly cataloged for future routing. This creates easily discoverable user data records—mapped to data models and cryptographically linked to identifiers.
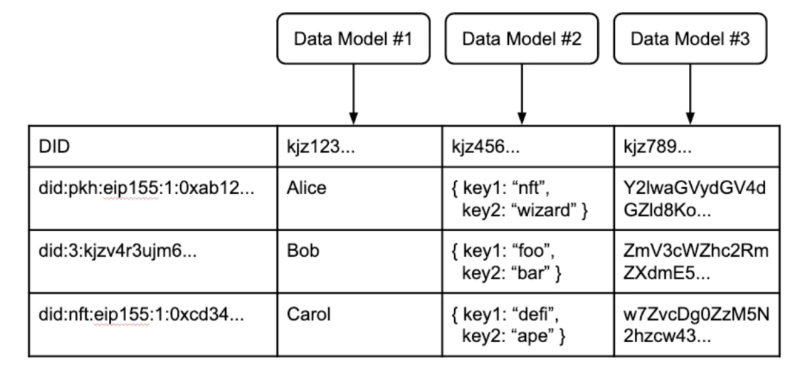
A distributed virtual user table featuring various DIDs from different networks, developer-defined data models, and related records
Therefore, a reasonable decentralized identity system should meet three criteria:
-
Trustless (Dependable): Operates on public network ensembles where anyone can participate, including partitioned or local networks.
-
Flexible: Supports any data structure definable by developers.
-
Highly Accessible: Works across any open network and unique identifier.
And can be enhanced by additional complex factors such as:
-
Pseudonymous-first: No account creation or verification required to begin. Users (or other entities) simply carry a cryptographic key pair and start accumulating information around it.
-
Generative: Information accumulates over time, forming an emergent holistic identity.
-
Composable: Information can be discovered and shared across contexts without predefined integration or portability standards.
-
Separable and Selective: Data sets can be encrypted, obfuscated, split across multiple identifiers, or otherwise segmented according to the controller’s preferences.
We need a minimal protocol establishing management and routing to trusted data. Everything else should be left to developers’ creativity, enabling uniqueness and diversity.
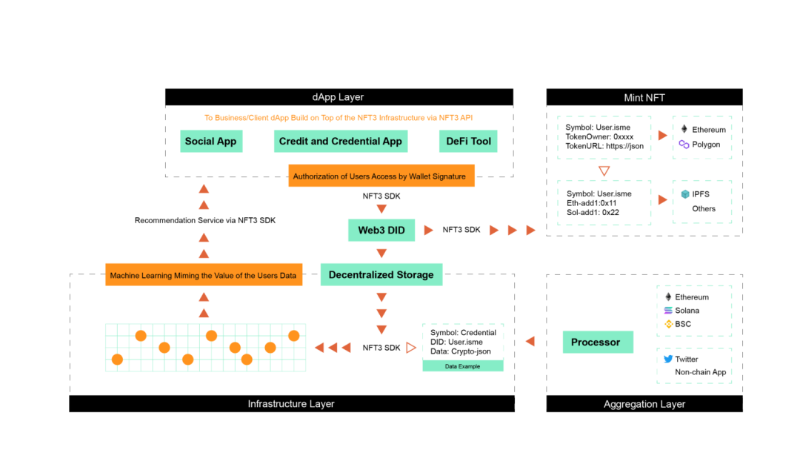
NFT3 enables users to access protocols easily and build their own identity systems while preserving personal privacy and sovereignty.
It builds a credit scoring system called “NCredit,” where higher scores grant benefits such as increased on-chain governance voting power, lower borrowing interest rates, reduced collateral ratios (similar to ARCx), and larger allocations in IDOs.
It provides an SDK for project developers to integrate, with NFT3 acting as the DID gateway. Users can choose to share data under their own conditions, so any dApp integrated with the NFT3 SDK can access data per user preference.
At the base layer, NFT3 integrates a storage system and applies machine learning to simulate user data, eventually transmitting it to apps willing to adopt the SDK—leaving uniqueness and diversity to developers and users, realizing a truly minimal identity protocol.
Regarding the recent market-wide deleveraging and mass liquidations, I’ve organized my thoughts on the market landscape.
Returning to the beginning of this article: why does CeFi still occupy such a large market space?
Clearly, CeFi has its strengths. I don’t believe DeFi will completely replace CeFi in the future.
Its faster customer acquisition, quicker decision-making, and specialized customization better meet ordinary users’ needs.
Additionally, its low slippage suits users with shallow understanding of crypto liquidity landscapes.
The above constitutes Part 1. I boldly predict these sectors will experience solid demand-side growth. But market validation is needed—to confirm whether this demand is real and how adoption curves evolve.
In Part 2, I will elaborate on my understanding of the following questions with examples, particularly focusing on protocol liquidity health.
Key questions include:
-
Which sectors and specific projects can expand Web3 use cases?
-
How should we educate the market and users? (This is a criterion I’ve recently emphasized in early-stage investing: does the team show awareness of market and user education? What’s their plan for doing so?)
-
How can we provide developers with a better environment?
-
How can Web3 products achieve better retention? How can we change user behavior and ensure product sustainability?
Markets need self-healing, and we need to gather ourselves and keep building.
Traditional financial systems took over a century of trial and error, surviving countless black swans, to reach today’s order.
Projecting final forms from current states is inherently flawed. DeFi still has a long journey ahead.
“Trust takes time. This transparency will be invaluable.
It should manifest as code accessible to all, not decisions made behind closed doors.”
Reference:
1. Identity as Information
2. Zero-knowledge-enabled Cooperation: Halo 2 & Aleo | Zooko Wilcox, ECC, Howard Wu, Aleo
3. NFT3 Tech Update
4. ARCX's DeFi Passport Makes It All Possible
5. The Crypto Loan Economy
6. Zero Knowledge Primitives by Aleo
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News