
11 million in cryptocurrency stolen as physical attacks become a growing threat
TechFlow Selected TechFlow Selected

11 million in cryptocurrency stolen as physical attacks become a growing threat
A fake delivery driver stole $11 million worth of cryptocurrency this weekend, as break-in incidents are also on the rise.
By: Liam Akiba Wright
Translated by: Saoirse, Foresight News
According to the San Francisco Chronicle, around 6:45 a.m. on November 22, a suspect disguised as a delivery worker entered a residence near the "Mission Dolores" neighborhood at 18th Street and Dolores Street, took control of the occupants, and stole a mobile phone, a laptop, and approximately $11 million worth of cryptocurrency.
As of Sunday, San Francisco police have not announced any arrests or provided specific details about the stolen assets, nor have they disclosed which blockchain network or token types were involved in the stolen cryptocurrency.
Physical attacks targeting cryptocurrency holders are not isolated incidents—there is a growing and concerning trend emerging.
Prior cases we've reported include a $4.3 million home invasion robbery in the UK; a kidnapping and torture case in New York's SoHo district aimed at forcing victims to grant access to their Bitcoin wallets; a surge in France of cryptocurrency-related kidnappings and government responses; extreme security measures taken by prominent crypto holders (such as the "Bitcoin family") who distribute wallet recovery phrases across multiple continents; the widespread practice among high-net-worth crypto investors of hiring personal security; and analyses of the rising trend of "wrench attacks" (violent coercion to extract cryptocurrency) and the risks and benefits of self-custody.
On-chain tracking begins immediately after the robbery
Even though a robbery may begin at someone's front door, the stolen funds often continue moving across public blockchain ledgers—making tracking possible and turning it into a race: one side involves money laundering channels shifting assets, while the other includes increasingly sophisticated freezing and tracking tools that have matured by 2025. USDT on TRON remains a key factor in this race.
This year, collaboration between token issuers, blockchain networks, and data analytics firms has enhanced the industry’s ability to freeze illicit assets. According to the T3 Financial Crime Unit, hundreds of millions of dollars in illegally transacted tokens have been frozen since late 2024.
The possibility of halting fund flows in the short term increases significantly if stablecoins are involved—because major stablecoin issuers cooperate with law enforcement and data partners, blacklisting wallet addresses linked to crimes upon notification.
Broad data also supports the view that stablecoins are the preferred tool for illegal fund flows. Chainalysis’ 2025 Crime Report shows that stablecoins accounted for about 63% of total illicit transaction volume in 2024, marking a significant shift from previous years when BTC and ETH dominated money laundering channels.
This shift is critical for asset recovery: centralized stablecoin issuers can block transactions at the token level, and when intermediary funds enter stages requiring KYC procedures, centralized platforms such as exchanges become additional "interception points."
Meanwhile, Europol warns that organized crime groups are leveraging artificial intelligence to upgrade their tactics—shortening money laundering cycles and enabling automated splitting of funds across blockchain networks and service platforms. If the destination address of stolen funds can be identified, the key action is to notify token issuers and exchanges as early as possible.
On a macro level, victim losses continue to worsen
Data from the FBI’s Internet Crime Complaint Center (IC3) shows that cybercrime and fraud caused $16.6 billion in losses in 2024, with cryptocurrency investment scams increasing 66% year-on-year. From 2024 to 2025, physical coercion targeting cryptocurrency holders—sometimes referred to as "wrench attacks"—has drawn greater attention. These cases often combine home invasions, SIM-swapping (fraudulently gaining control of someone’s SIM card), and social engineering. TRM Labs (a blockchain security firm) has documented trends related to these coercive thefts.
Although this San Francisco incident involved only a single residence, its attack pattern is representative: device intrusion → forcing victims to transfer funds or export private keys → rapid on-chain fund dispersal → testing withdrawal pathways.
New regulatory policies in California add another variable to this case. The state’s Digital Financial Assets Law, effective July 2025, grants the Department of Financial Protection and Innovation authority to license and enforce compliance for certain cryptocurrency exchanges and custodians.
If any off-ramp (channels converting cryptocurrency into fiat), OTC broker, or storage provider with business ties to California comes into contact with the stolen funds, the regulatory framework under the Digital Financial Assets Law could facilitate cooperation with law enforcement. While not a direct method for recovering self-custodied assets, it impacts the counterparties thieves typically rely on to convert crypto into cash.
Policy changes elsewhere will also affect how this case unfolds
According to legal analysis by Vinson & Elkins, the U.S. Treasury removed the mixer Tornado Cash from the Specially Designated Nationals List (SDN list) on March 21, 2025, altering compliance requirements for interacting with its codebase.
However, this change does not legalize money laundering, nor does it reduce the analyzability of on-chain transactions.
Still, it weakens the prior deterrent that pushed some participants toward alternative mixers or cross-chain bridges. If stolen funds use traditional mixers or cross-chain bridges to move into stablecoins before cashing out, tracing the origin and identifying the first point where KYC is triggered will remain pivotal.
Since the involved wallet addresses have not been made public, exchanges can plan response strategies over the next 14 to 90 days based on three core pathways. The table below outlines, based on 2025 market structure and regulatory conditions, a "primary fund transfer model," key monitoring indicators, and probability ranges for fund freezing and recovery:
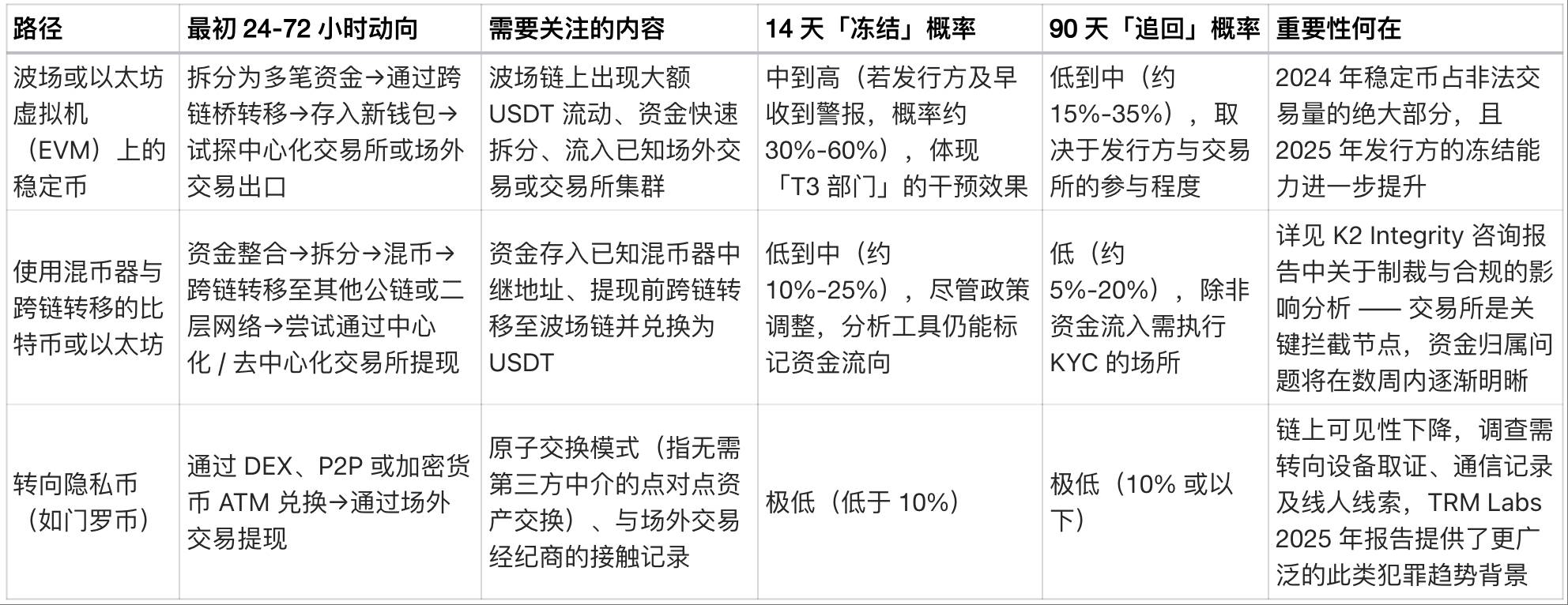
The timeline of the case can be inferred using the above model.
In the initial 24–72 hours, focus should be on fund consolidation and early transfers. If the addresses are exposed and funds include stablecoins, issuers should be notified immediately to initiate blacklisting; if funds are in Bitcoin or Ethereum, monitoring should focus on mixers, cross-chain bridges, and whether funds shift toward USDT before fiat conversion.
Per IC3 collaboration protocols, if funds flow into KYC-required venues, asset preservation notices are typically issued within 7–14 days, leading to exchange account freezes.
Within 30–90 days, if privacy coin transaction paths emerge, investigative focus will shift to off-chain clues—including device forensics, communication records, and traces of the "fake delivery" scam—while TRM Labs and similar organizations advance their fund-tracing efforts during this phase.
Wallet design continues evolving to counter physical coercion risks
In 2025, the adoption of multi-party computation (MPC) wallets and account abstraction wallets has expanded, introducing features like policy controls, seedless recovery, daily transfer limits, and multi-factor approval processes—designs that reduce the risk of "single-point exposure" of private keys during physical coercion (i.e., private keys are not leaked through a single device or step).
Contract-level "time locks" (mechanisms that delay transaction execution) and "spending caps" can slow down the movement of high-value funds and create a time window to alert issuers or exchanges in case of account compromise.
These protective measures cannot replace basic security practices related to device usage and home safety, but they do reduce the likelihood of successful fund theft when thieves gain access to phones or laptops.
The San Francisco Chronicle report provides core facts of the case, but the San Francisco Police Department website has not yet published a dedicated bulletin on this incident.
The case’s progression will depend on two key factors: whether the involved target addresses will be made public, and whether stablecoin issuers or exchanges have received review or intervention requests.
Join TechFlow official community to stay tuned
Telegram:https://t.me/TechFlowDaily
X (Twitter):https://x.com/TechFlowPost
X (Twitter) EN:https://x.com/BlockFlow_News












